Encryption mechanisms in modern ransomware
 Extortionists are a major threat to PC users, whose activity is increasing over time. According to a recent semiannual report by Cisco, extortionists dominate the malware market and are the most profitable type of malware for intruders ever. Much has already been written about extortionists, and most people understand what they are. Extortionists use various methods to block access to the victim’s computer or its files, and then demand a ransom for restoring access to them. Recently, we have seen a significant increase in the activity of extortionists, cryptographers who specialize in encrypting user files. Consider the encryption methods they use.
Extortionists are a major threat to PC users, whose activity is increasing over time. According to a recent semiannual report by Cisco, extortionists dominate the malware market and are the most profitable type of malware for intruders ever. Much has already been written about extortionists, and most people understand what they are. Extortionists use various methods to block access to the victim’s computer or its files, and then demand a ransom for restoring access to them. Recently, we have seen a significant increase in the activity of extortionists, cryptographers who specialize in encrypting user files. Consider the encryption methods they use.General information
Encryption is an essential element of encryptors, since the entire success of such a “business” depends on how successfully it is used to block access to user files. Encryption itself is not a malicious method or operation. It is a powerful and legitimate tool used by ordinary users, corporate and government to protect data from unauthorized access.
Cipher operators are designed to “steal” user data. For this purpose, they use encryption, which gives them the opportunity to prevent access to the data of their rightful owner, since he does not know the encryption key. Data can be accessed only by attackers who know this key.
After its launch in the system, the cryptographer begins to modify the files or critical service data of the file system so that they can only be read by restoring them to their original state. In turn, this operation requires the use of a file decryption key, which is known only to attackers. Obviously, in this case, encryption and reverse decryption are used for malicious purposes.
')
In addition, encryption is used by the authors of the malware to securely interact with the malware of its managing C & C server, which, in turn, stores the key needed to decrypt the data. Using this key, the file system data or the files themselves can be restored to their original state.
The authors of cryptographers take advantage of both types of encryption, both symmetric and asymmetric. This gives them optimal performance and convenience when encrypting data. In the case of a symmetric encryption scheme, the same secret key is used for both data encryption and decryption. For asymmetric encryption, two keys are used: closed and open. The first is known only to attackers and is used to decrypt data, and the second is public and is used to encrypt data.
Symmetric encryption is useful for encryption in terms of convenience and performance, allowing a malicious program to encrypt data in a reasonable amount of time. Asymmetric encryption, on the other hand, is used to encrypt a symmetric key that can be changed. Thus, attackers can maintain one decryption key for all of their victims, instead of storing the key in each specific case of infection.
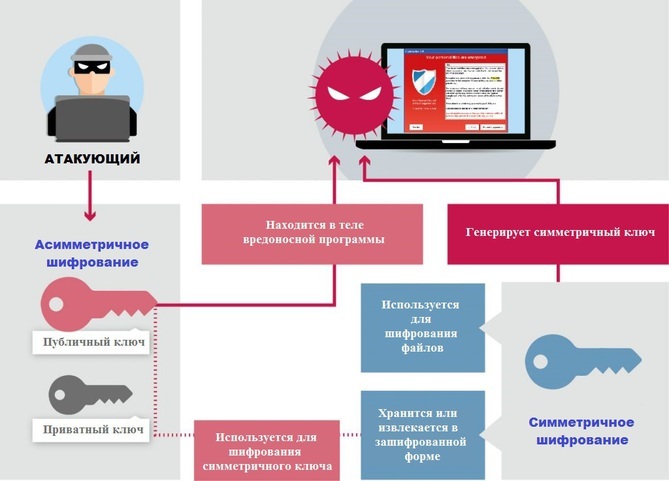
Fig. 1. The scheme of the work of symmetric and asymmetric encryption, which is used in cryptographers.
The protection mechanism of the symmetric key can be changed, but, as a rule, the public key is used for this, which is located in the body of the malicious program or extracted from the manager of the C & C server and then used to encrypt it. After the end of the encryption process, the symmetric key is often transferred to the server or stored in the victim's system.
Interaction with the C & C Server Manager
Cryptographers use cryptography when working with their C & C server to preserve the confidentiality of the transmitted data, as well as to hide malicious activity. Earlier families and versions of cryptographers paid special attention to confidentiality when working with C & C. Newer families and modifications use such proven encryption standards for their protocols as TLS .
Encrypting traffic between a compromised system and a server makes it more difficult to detect malicious activity, since it is difficult to distinguish it from the encryption protocol used in legitimate operations, such as online banking.
In order to inspect encrypted traffic, network security tools require additional capabilities from the intended victim of the network. For example, to check TLS-encrypted traffic, an IDS / IPS solution can be used, which is located on the data path between the internal network computers and remote servers. TLS traffic checking is also possible at the level of the computer itself, depending on the capabilities of the anti-virus tool used.
If the internal network does not have the ability to track traffic, the malware uses encryption to connect to C & C, which will remain undetected until C & C addresses are found and added to the black list of malicious IP addresses and domains. Thus, this method of protection is more reactive.
Errors in the implementation of encryption
ESET experts have already published a report on the evolution of encryption, which clearly indicated their growing prevalence. The number of families and modifications of cryptographers has increased significantly since 2011. In addition, the number of platforms for which extortioners are calculated has increased.
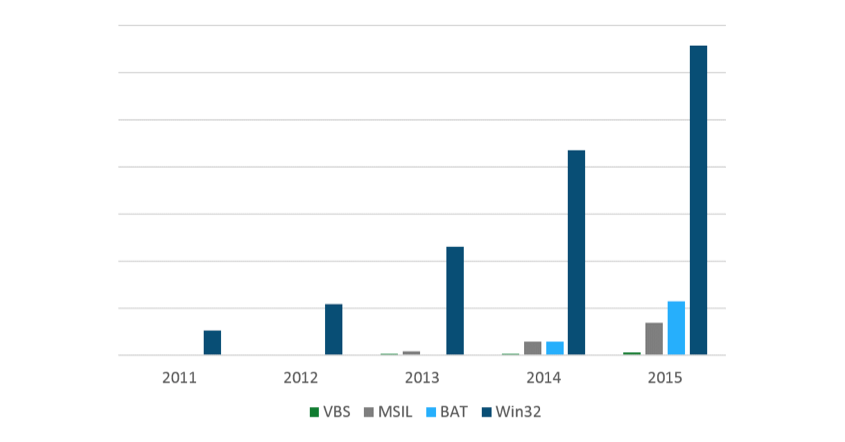
Fig. 2. The prevalence of cryptographers for the period from 2011 to 2015.
The rest of our analysis will be devoted to how encryption is implemented in four families of cryptographers at different stages of their evolution: CryptoDefense (2014), TorrentLocker (2014), as well as those that became popular TeslaCrypt (2015) and Petya (2016).
The purpose of our research is to show how cipher developers evolved over time and analyze the mistakes of their authors, from the silliest to the more complex.
When the extortionist CryptoDefense was first seen in the use of attackers, his research showed that he was very similar to CryptoLocker. The latter was one of the first of its kind cryptographer. It is noteworthy that CryptoDefense had serious flaws in the implementation of the mechanism of its interaction with the C & C server manager, as well as in the process of encrypting files.
The protocol for working with C & C is based on the use of HTTP HTTP POST requests sent by malware from an infected host. To ensure security when working with C & C, CryptoDefense used URL obfuscation in HTTP POST requests. In this way, the encryption key that was used to encrypt the message was hidden. The body of the POST request contained the C & C protocol message, encrypted using the RC4 algorithm and the private key from the POST URL.
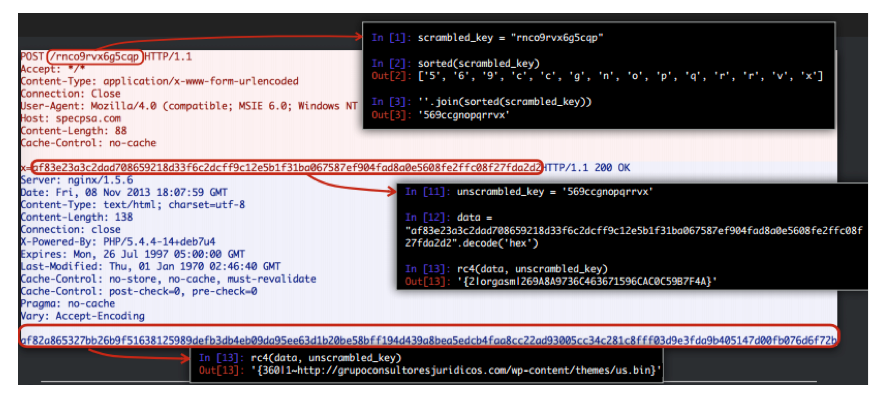
Fig. 3. Deciphering the CryptoDefense encryption protocol C & C.
In the case of intercepting an encrypted CryptoDefense message, it can be easily decrypted. The POST request itself contains all the information necessary to recover the encryption key and disclose the mechanisms of the interaction protocol with C & C. This, in turn, allows you to create a network signature to detect the activity of the extortioner and block its malicious actions, in particular, the correct operation of the payload.
In the case of file encryption, the error in the implementation of the algorithm is surprisingly similar to the previous one. In order to understand it, consider the algorithm for performing actions of the extortioner CryptoLocker.
- After the victim is compromised, the extortionist notifies his C & C server about this and indicates the campaign ID as well as the unique system ID.
- The managing C & C server responds with an OK message for confirmation.
- The client accesses the server again, specifying the campaign identifier and the unique system identifier.
- The server provides the ransomware with a ransom request message and the RSA-2048 public key from the key pair that was generated for the given campaign ID / victim system ID combination. The private key from this pair never leaves the C & C server.
- The extortionist confirms to the C & C server the successful acceptance of the message requesting redemption and the public key. It also confirms the end of the file encryption process.
A weak spot in the CryptoLocker mechanism is the presence of steps 3 and 4, since in this case, the files are encrypted from the user only if the extortioner successfully communicates with the C & C server. These steps have been removed in the CryptoDefense algorithm, which generates a pair of keys on the victim’s system itself.
However, the authors of CryptoDefense overlooked a small detail, which is that the extortioner forgets to remove the RSA private key from the system. This key can be used to decrypt encrypted files and can be found in the system. After that, it is enough to use one of the Windows API functions to decrypt files.
Thus, the authors of CryptoDefense corrected one mistake in the work of the extortioner, but immediately made the second one.
Torrentlocker
Early versions of TorrentLocker also contained errors in the implementation of encryption, but relied on a very secure encryption algorithm for AES files in CTR mode. However, the way this algorithm was implemented led to the presence of weak points in the overall encryption scheme.
The AES algorithm is a block cipher , that is, it implies data encryption in fixed-size blocks (16 bytes). AES in CTR mode accepts an initial value as an input, known as an initialization vector or Initialization Vector (IV) to expand a key value (which can be 128, 192 or 256 bits) to the size of the data to be encrypted, which is called key stream (keystream). After that, an XOR operation on the original message data is applied to the key stream, simulating the concept of a stream cipher.
The exploitation of the vulnerability in the TorrentLocker encryption implementation was quite simple: on a compromised system, the extortioner generates a 2MB keystream and encrypts the first 2MB of each file. In the case when the file size is less than 2MB, it is fully encrypted by this method.
Nevertheless, the use of AES-CTR was completely analogous to the method of reusing the initialization vector and the stream cipher key, which is a common mistake among beginners in cryptography. Having at least one encrypted file and its original original content available, it is quite simple to restore the key stream and decrypt the remaining files. In later versions of TorrentLocker, the authors corrected this error by replacing the AES CTR mode of operation with CBC, which will be described in the next section on TeslaCrypt.

Fig. 4. CTR encryption scheme.
Petya
Petya cipher uses a different approach to other ransomware to perform its malicious functions. Instead of encrypting each file separately, it aims to compromise the data structures of the disk or file system. Petya's goal is the master boot record (MBR) sector of the victim system, which is used to boot the OS.
The authors of Petya have chosen the Salsa20 encryption algorithm, which belongs to the eSTREAM new stream cipher project. This initiative is a project to promote the development of new streaming fonts to replace the already obsolete type RC4. Petya’s use of the Salsa20 cipher signifies the evolution of ciphers, which now use new and more reliable ciphers.
When Petya is launched for execution, it begins the process of infecting the system, which consists of two stages . The MBR encryption process is fairly well implemented. It begins with a modification of the MBR, and then calls the BSOD in order to force the user to reboot the system. After the reboot, the user is shown the fake screen of the well-known tool CHKDSK, while Petya performs additional operations on encrypting the MBR. After that, it reboots the system again and shows the intimidating image to the user with the text of the ransom request.

Fig. 5. A user’s frightening picture of a Petya coder with ransom demand.
Despite the awesome message with a ransom demand, there is a way to decipher the MBR, since the authors made annoying errors in the extortioner's code. The most important flaw that the MBR can decrypt without addressing the attackers is the way the cryptographer uses to get the recovery key.
In order to understand the essence of this flaw, consider the situation of encryption from the other side. We begin by examining the process in which the recovery key, which is provided to the victim’s attackers, is used to decrypt the files. After that, we will explain how this implementation bug can be used to decrypt the MBR without knowing the whole key.
The field for the decryption key character set is limited to 54 characters, and its length is fixed and is 16 characters. As soon as the user enters the key in the redemption message field, it is verified. During the verification process, the entered recovery key is expanded to 32 bytes of the encryption key using a special algorithm and compared with the verification buffer in the sequence. If the encoded key corresponds to the verification buffer, it enters the input of the implementation function of the Salsa20 encryption algorithm (in fact, Salsa10 ), after which the disk sector data is decrypted.
Although the key expansion method runs exactly on the recovery key, which doubles its size, it does not add any additional key entropy , since the extension algorithm is deterministic. Thus, its security, in this case, is limited by the number of 54 ^ 16 different keys, which corresponds to the security level of 92 bits, (i.e., log2 (54 ^ 16) = 92.07) and is beyond the possible successful use of the coarse Forces to search for a key, for example, the NSA has the ability to iterate over keys up to 80 bits long.
The authors of Petya made a mistake in the implementation of the main function Salsa20, which creates an array of 16 words containing constants and a key from the so-called main table, which is used in the encryption process. The authors of the cryptographer fixed the existing Salsa20 implementation to support its 16-bit architecture, but they missed a key part. The reason why we are so attentive to the implementation of Salsa20 is the execution mode of the ransomware code. Since Petya is designed to work as a loader, which is executed in 16-bit real mode x86 microprocessors.
To create the above array, two copies of the main table are created in direct byte order format (little-endian). The authors of the cryptographer changed the variables of the uint32_t type to uint16_t, in order to adapt the code to a 16-bit architecture. Nevertheless, they neglected the adaptation of the new bit to perform the cycle when working with the main table in the main function Salsa20. Due to this error, after reading two bytes, the offset for the next data read operation is increased not by two, but by four bytes.

Fig. 6. Error in the implementation of Salsa20 for 16-bit architecture.
For this reason, in fact, only half of the key is involved in the Salsa20 encryption operation. This reduces the security level of the entire Petya encryption scheme from 92 bits to 46 bits. In this case, the key can be picked up within seconds using the brute force method even on ordinary computers.
TeslaCrypt
It is not accidental that TeslaCrypt is considered to be one of the most successful families of extortionists. Encryption mechanisms in TeslaCrypt are implemented very carefully, and the choice of algorithms for this purpose indicates that the authors have some training in the field of cryptography.
TeslaCrypt uses the AES-256 algorithm to encrypt files; however, unlike the vulnerable version of TorrentLocker, it uses CBC as its cipher mode. In this mode, each block of encrypted data (part of the encrypted message of a fixed size) acts as an IV initialization vector when encrypting the next block, with all blocks being encrypted with the same key. This fact shows that this is not a stream or another code similar to it, which makes the key search procedure used against TorrentLocker useless in this case.

Fig. 7. CBC encryption mode diagram.
The AES key itself, in the case of TeslaCrypt, is encrypted using an algorithm similar to the El-Gamal scheme , and then sent to the C & C server. Instead of RSA, the authors chose the Elliptic Curve Cryptography (ECC) algorithm for elliptic cryptography because of the convenience for evading detection, since ECC reduces the amount of ciphertext and takes less time to execute.
Nevertheless, the authors of TeslaCrypt v2.2.0 (aka TeslaCrypt v8) made one mistake, which is less trivial than previous ones. As stated on the BleepingComputer website and in the Talos study, a data recovery key (RK) designed to protect the encryption key is generated as a result of multiplying the shared secret key (C2K) specified by the C & C control server and the secret key used for file encryption (FK).
RK = C2K * FK
The recovery key is stored on the compromised system and allows you to carry out the FK recovery process in the event that C2K is known. However, the authors of TeslaCrypt v2.2.0 mistakenly suggested that they could use the factorization mechanism underlying RSA.
Even decades later, the researchers could not find an effective algorithm for calculating prime factors of a given number (as large as those used in RSA). However, this does not mean that the problem of factorization cannot be solved in the future.
The length of the data recovery key is not so long in order to make the task of factorization impracticable. Therefore, a brute force attack is a method that can be used to search for an encryption key and then decrypt files.
Can encryption be used against cryptographers?
The question arises, do coders really not specialize in encrypting already encrypted files? The answer is both yes and no.
Obviously, you can encrypt any encrypted data again. In fact, this fact underlies the idea of onion routing. In short, onion routing is designed to ensure the confidentiality of data and its transfer through nodes or routing nodes. Imagine a three-node scheme, so when a user wants to access a website, the request will be encrypted three times. For the first time by node 3, then by node 2, then by node 1. When a request passes through each node, it will be encrypted with the key of the current node, thus only node 3 will have original data at the input even before it passes through the route. Node 3 performs the request on behalf of the user and sends the response back using the same encryption scheme that applies to the request.
To ensure the efficiency and accuracy of file encryption, encryption programs usually filter files by their extensions; For example, the list of TorrentLocker files in 2014 looked like this . If a file extension gets into the list, it is encrypted, otherwise, it is discarded.
On the other hand, encryption tools often add some predetermined extension to the names of encrypted files. This is an interesting fact, since we did not observe examples of encryptors that would target file encryption tools. It follows from this that if one of such tools is used on a computer that has been compromised by the cryptographer, the data on it will not be encrypted by the extortionist.
Preventive measures
Preventive measures to protect against extortionists have already been published in various sources. In general, the following recommendations will be helpful to users.
- You should use a good antivirus product with HIPS proactive protection and phishing protection.
- Pay attention to hidden file extensions and do not follow links in messages received from unknown sources.
- Use file backup and do it as often as possible.
- Avoid mounting backup file directories on your computer. The extortioner may encrypt files placed on removable media in the cloud and other places that can be accessed from the OS file system.
If the encryption system has already compromised the system, you can try to decrypt the files using the decryption tools that were developed by security researchers. ESET has several such tools available to decrypt some families of extortionists and their modifications, which allows the user to access files without paying a ransom.
In addition, the National Police Office of the Dutch Police and the Europol European Cybercrime Center, in cooperation with security companies, also provide tools to assist the cryptographer’s victims.
Source: https://habr.com/ru/post/310536/
All Articles