Security Week 37: Windows patches will become more cumulative, Google vs. HTTP, vulnerability in MySQL
 Since October, Microsoft has been changing the update delivery policy for a number of operating systems ( news , post on Technet). In order to simplify the update process (and, probably, according to numerous applications of workers), Windows 7 and 8.1, as well as Windows Server 2008 and 2012, will be updated with one large patch once a month. The advantages of this approach are obvious: just look at the date of the last update in order to understand the relevance of installed patches.
Since October, Microsoft has been changing the update delivery policy for a number of operating systems ( news , post on Technet). In order to simplify the update process (and, probably, according to numerous applications of workers), Windows 7 and 8.1, as well as Windows Server 2008 and 2012, will be updated with one large patch once a month. The advantages of this approach are obvious: just look at the date of the last update in order to understand the relevance of installed patches.The drawbacks are also obvious: the option to install patches will no longer be available, everything will be loaded and put in one piece. If a patch turns out to be incompatible with the installed software or certain system settings, you can only refuse the entire monthly update immediately. It is with the installation of choice that Microsoft plans to fight: after all, in fact, this approach leads to fragmentation, instead of one version of Windows, we have to deal with a dozen, which complicates both support and testing.
However, one loophole remains: a cumulative patch includes both security updates and updates aimed at improving reliability. You can select and install only security fixes and nothing else, but this option is designed for clients from large companies. The new policy can go sideways when using specialized software with strict requirements for compatibility. There are a lot of examples when the release of the patch broke: you can recall problems with the software from Citrix after the update of Windows 10, or say the configuration system crashes through Powershell (here's an interesting point - the Microsoft left-hand link complains about the bugs of the right).
Changes to the Microsoft update policy reflect the current state of the battle between reliability and security. The most reliable software that is not updated over the years, it is also the most insecure. In a situation where the discovery of new vulnerabilities (and just bugs) is inevitable, you have to make a choice, and Microsoft makes a choice in favor of protection against hacking. This is commendable, but after all, a curious situation turns out: every month a new set of patches for Android once again brings up the topic of fragmentation, and yet on desktops, this is a much more serious problem. From a security point of view, the ideal scenario is the delivery of updates (at least patches) at the time they are ready (well, like in Gentoo ). It is this strategy, with regular explosions of user discontent, that Facebook is using, for example. Both ideal scenarios (maximum reliability or maximum safety) are unattainable, but the right balance must be sought. It is not excluded that the experience of vendors of security software is useful here: due to the nature of their work, they have been sending updates several times a day for many years.
')
Discloses critical vulnerability information in Oracle MySQL and compatible products.
News Legal Hackers research .
Researcher David Golunski from the Legal Hackers creative association this week partially revealed information about a serious vulnerability in Oracle MySQL, which also affects dependent products, in particular MariaDB and PerconaDB. This news is a good supplement to the previous one and also raises the question of the need for a standard for both patch delivery and vulnerability disclosure. MySQL bug (CVE-2016-6662, versions 5.7.14, 5.6.32 and 5.5.51 and earlier are subject to UPDATE: in versions 5.7.15, 5.6.33 and 5.5.52, the problem seems to have been quietly solved) allows you to embed bookmarks in the DBMS configuration files, which in turn can lead to the execution of arbitrary code during the next restart. Vulnerability can be exploited both when there is access to the server or remotely, in the case of an insecure system configuration (write access to configs by the user mysql).

More information about the scenario (rather nontrivial) exploitation of the vulnerability can be found at the link above. The important point is that the software already has patches, but for MySQL itself
40 days is in this case definitely not an argument, but the release of patches of one hole by different vendors at odds seems to be really a problem. It turns out that everyone is good. Welcome to the wondrous new, highly irregular world of software security. By the way, Oracle does not have a public reward program for the found vulnerabilities, and last year, CSO Oracle didn’t speak well of wythets at all - they say, there’s nothing to break our products without permission. The post was quickly removed, but the sediment remained.
Google Chrome will mark HTTP-only sites as unsafe
News Post in a google blog.
From January 2017, Google Chrome will begin to mark sites that provide connections only over an unsecure HTTP protocol as potentially unsafe. Chrome now marks these sites as neutral (as opposed to secure, trusted connections using HTTPS), but Google rightly believes the situation should change. The transition will be carried out in several stages, and in January only those sites that transmit HTTP passwords or credit card data (plain text!) Will become unsafe, which, of course, is very much beyond good and evil.
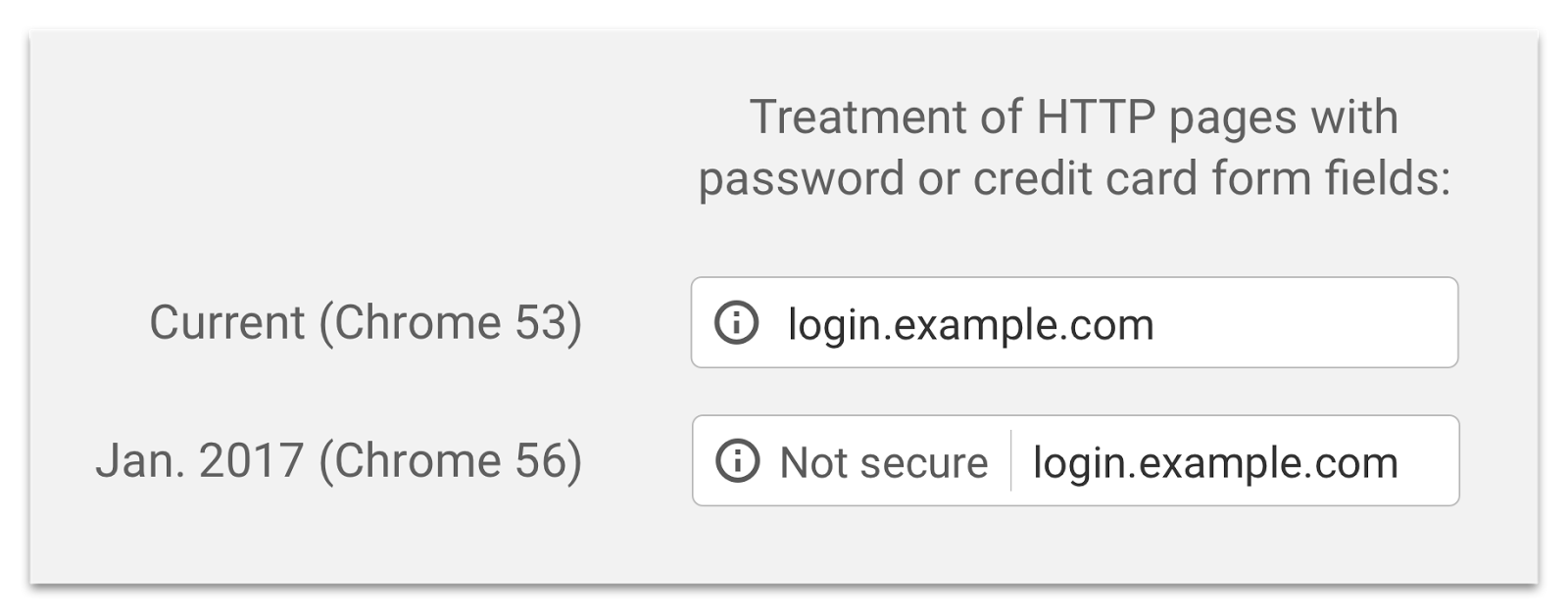
The following is interesting in the post of the Google team: the reaction of users to various methods of sorting websites was checked by research, and, as expected, they only pay attention to the explicit message about the problem. All the rest "you know, there may not be all good" are ignored. I wonder how often explicit messages about insecurity are ignored? Browser developers are thus face to face with an army of users, which is not at all required to understand the intricacies of network protocols. As a result, it is necessary to reduce the long-term experience of protecting information in the network to something very simple and understandable:
The next stage of the attack on the playtext Internet will be a warning about all HTTP sites in incognito mode, in which users, in theory, should care more about privacy. And finally, Google plans to extend the policy to all HTTP connections for all users.
What else happened:
Meanwhile, Microsoft held the last weekly patch according to the old rules .
Troyan, disguised as a guide for Pokemon Go, dragged into Google Play. 500,000 downloads .
And for a snack - password leakage from QIP plaintext.
Antiquities
"V-707"
 Resident is not a dangerous virus. It affects .COM files when they are loaded into memory. Changes the first 5 bytes of the file (MOV AX, Start_Virus; PUSH AX; RET near ) and appends to its end.
Resident is not a dangerous virus. It affects .COM files when they are loaded into memory. Changes the first 5 bytes of the file (MOV AX, Start_Virus; PUSH AX; RET near ) and appends to its end.It is activated only in DOS 3.30, determines (by scanning memory) the entry points of the handlers of the 13th and 21st interrupt in DOS and actively uses them when infecting files. Located in the highest memory addresses, adjusting the last MCB and reducing the size of available memory (word at address 0000: 0413).
When infecting, it counts the already infected files, and as soon as the 30th infected file is found, it sets interrupt 8h to the subroutine of the sound signal generation. Intercepts int 8 and int 21h.
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 89.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/310128/
All Articles