New tricks Locky cipher

In this article we will look at the techniques of one of the most well-known families of cryptographers: Locky .
Recently (our colleagues from Avira reported this in July), the cryptographer’s authors added a new feature that includes offline mode, and therefore now the malware can encrypt files without connecting to the server. In this case, the weak point is the key, which is the same for each computer where files are encrypted, but the single key is used only if, for some reason, the C & C server is unavailable to the cryptographer.
')
But now the authors have changed the way they infect computers. Typically, such attacks use a small Trojan downloader that downloads and launches the cryptographer. For example, when an attack uses a javascript file, it usually downloads a small executable file, which is needed only to get the encryption tool and launch it. As I wrote earlier , cyber criminals are constantly making various changes to try to avoid detection by security solutions.
Spread New Attack
In this case, when the attack was spread via e-mail, we saw a number of samples in the form of a zip-file, which contained inside a javascript file called “utility_bills_copies .js”. However, there are different versions using different file names and types, for example:

And inside was the following file:

They missed the part with the Trojan loader, and the script received the Locky version in the DLL format (when using the loader, in most cases the downloaded file was an EXE), which is executed when using Windows rundll32.exe. The first meeting with this option was on August 22 and the authors still use this strategy. As you can see, cyber criminals launch a new wave of attacks every week:
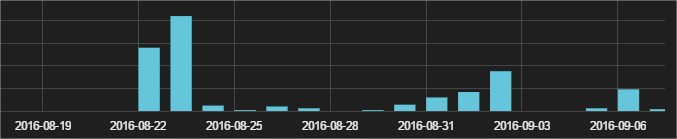
Most heavily affected countries
We have seen only a few hundred attempts at infection, mainly in North and South America and Europe, although they also occurred in Africa and Asia. In the event that such attacks are highly effective, then perhaps we will see an increase in their number in the coming weeks. Below you can find a list with some hashes of this version of Locky:
ransomware_list3 (3)
Article author: Louis Corrons
Source: https://habr.com/ru/post/309732/
All Articles