Plug-and-Get-Security I, TLS Security in the Grove of Domains

Secure TLS has always been a headache. Both for owners of small resources, and for companies whose infrastructure can reach several hundred or even thousands of domains. Problems with TLS \ SSL appear constantly - vulnerabilities in the protocols themselves, crypto-algorithms or their implementation. From the well-known Poodle and HeartBleed, to quite exotic and fresh (CVE-2016-2107) problems with AES-NI .
And what are the problems with TLS?
Stealing user accounts, administrators, embedding malicious content into traffic, advertising, or, as was the case with HeartBleed, even direct memory access to the server.
Let's take a look at the big picture.
For July 2016, according to the SSL Pulse project, which analyzes the settings of Alexa Top 200k domains:
- 40% of them have configuration errors or use insufficiently strong sets of encryption algorithms
- 25% have serious problems leading to the actual implementation of attacks on resource users or on the resources themselves
So, we all have problems!
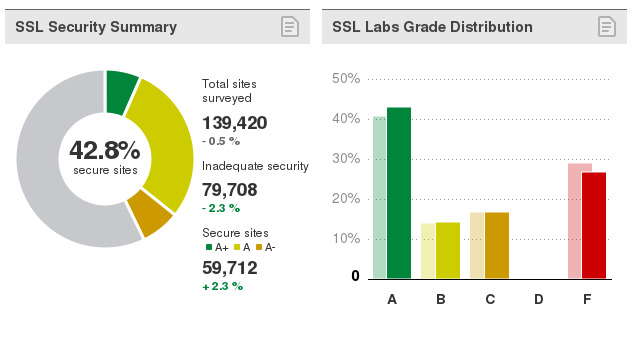
Who is guilty ?
It seems to us that this is largely due to the fact that TLS \ SSL is quite a complicated thing and it’s not easy to figure out how to prepare it safely. Fortunately, we have several services at our disposal that greatly facilitate this task:
» Qualis SSL Labs
» Comodo SSL Analyzer
» Mozilla SSL configuration Generator
And what exactly do we want to know when we set ourselves the task of checking the TLS settings:
- Are there any vulnerabilities in the version of the library we use?
- Is the reliability of the algorithms and key lengths used by us sufficient?
- Do we support TLS accelerating mechanisms that make our site faster for users?
- When will the expiration of certificates for our domains be suitable?
As well as other important things - the presence of PFS, Secure Renegotiation, HSTS, Key Pinning, Session Resumption, etc. These terms will be enough for five separate articles, so we will not delve into the wilds.
Let's see how this looks like on the example of Qualys SSL Labs: the service is excellent and gives out almost all the information we need:
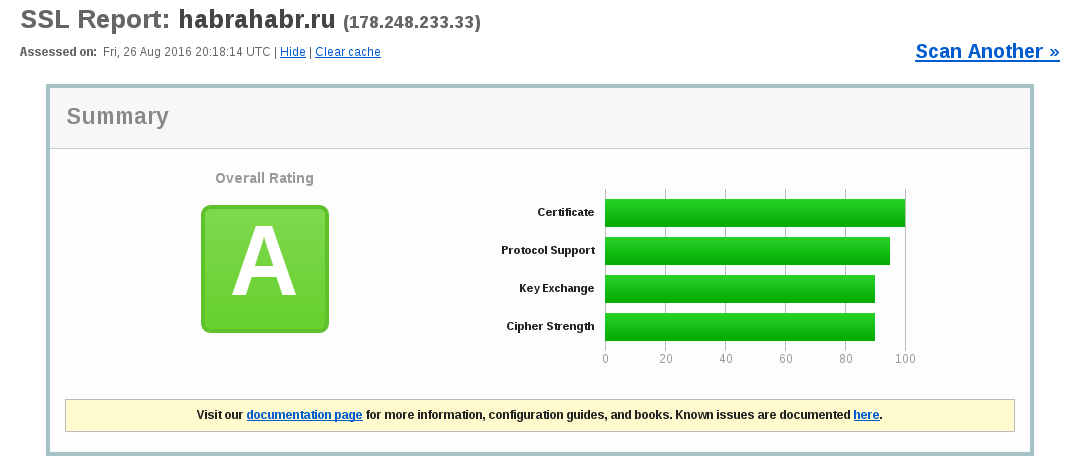
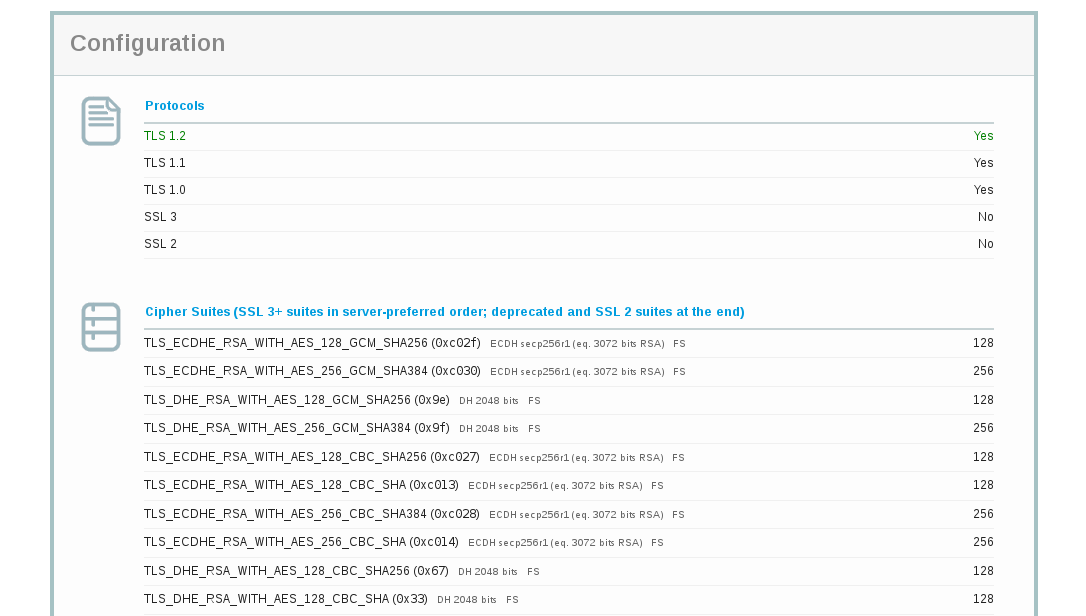

What to do?
At one time, we c Crait thought about monitoring SSL / TLS with us. I must say that despite the fact that public SSL verification services already existed, we could not benefit from this, because the size of our infrastructure was very large. And these are separated by several DCs in different cities, managed by different systems of configuration files, not connected to each other servers, which made manual analysis or any personalized approach impossible.
We needed a tool that would allow us to conveniently collect information about all the observed domains in one place. Highlight configuration problems and vulnerabilities, sort servers by criteria that interest us, build a convenient infographic, and keep information current. You probably already guessed that we are talking about Elastic + Kibana. Let's get started.
Create solution
First we need a functional that will allow us to collect information about domains. Qualys SSL Labs has an API and a console client for it . Unfortunately, it works slowly, but for us the time to bypass the servers was critical + the client has certain bugs, such as the ability to go into an endless sleep, if too many API requests are sent at the same time.
We c you after all fashionable guys? Fashionable, so we will do not just a clipper for cli, but a microservice! Rather a few. Why so - it will be clear further. Many thanks for Mikhail Aksenov Crait for writing and packaging.
A script was written that implements multi-threaded requests to ssllabs using their cli, which is able to collect data in JSON, send it to Elastic, write logs and bypass existing api problems after the execution of the request. The code is available on github , we will be glad to any contribution to the project!
What else do we need? Raise Elastic, Kibana and make friends all this with each other. Of course, we don’t want to do it all by hand, but use Docker. We remove containers and launch them with Compose.
We will have the following interaction scheme:
+--------------+ |tls-monitoring| ------> Internet +--------------+ | | Post data to Elastic REST api at port 9200 | +--------------+ |Elasticsearch | +--------------+ | | Get data from Elastic REST api at port 9200 | +---------------+ | Kibana | -----> UI localhost:5601 +---------------+ Previously, you can organize the collection of information about your (or foreign) domains, using (for example) unloading zones from DNS servers.
Docker-Compose is better to install from pip, because the versions of some distributions available in the repositories are so fresh that they cannot satisfy the Compose dependencies to Python.
pip3 install docker-compose wget https://raw.githubusercontent.com/dordyan/tls-monitoring/master/docker-compose.yml # ./all_domains docker-compose up What happened
In a few minutes you will receive the results of the first scans. The currently implemented dashboard is informative enough to build on its basis the processes of monitoring and controlling the state of the infrastructure.
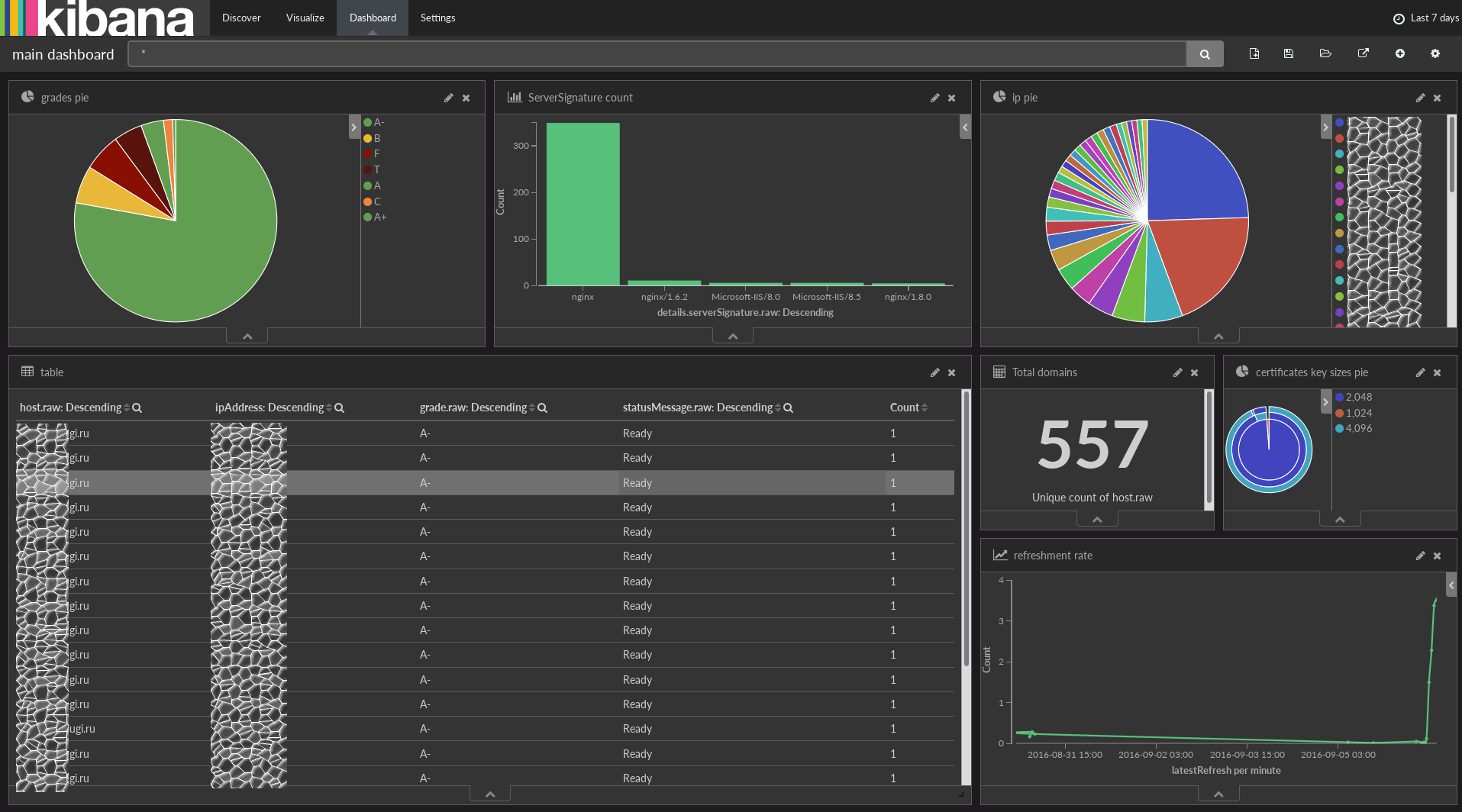
You can sort dashboards by rating to see which servers need attention first.
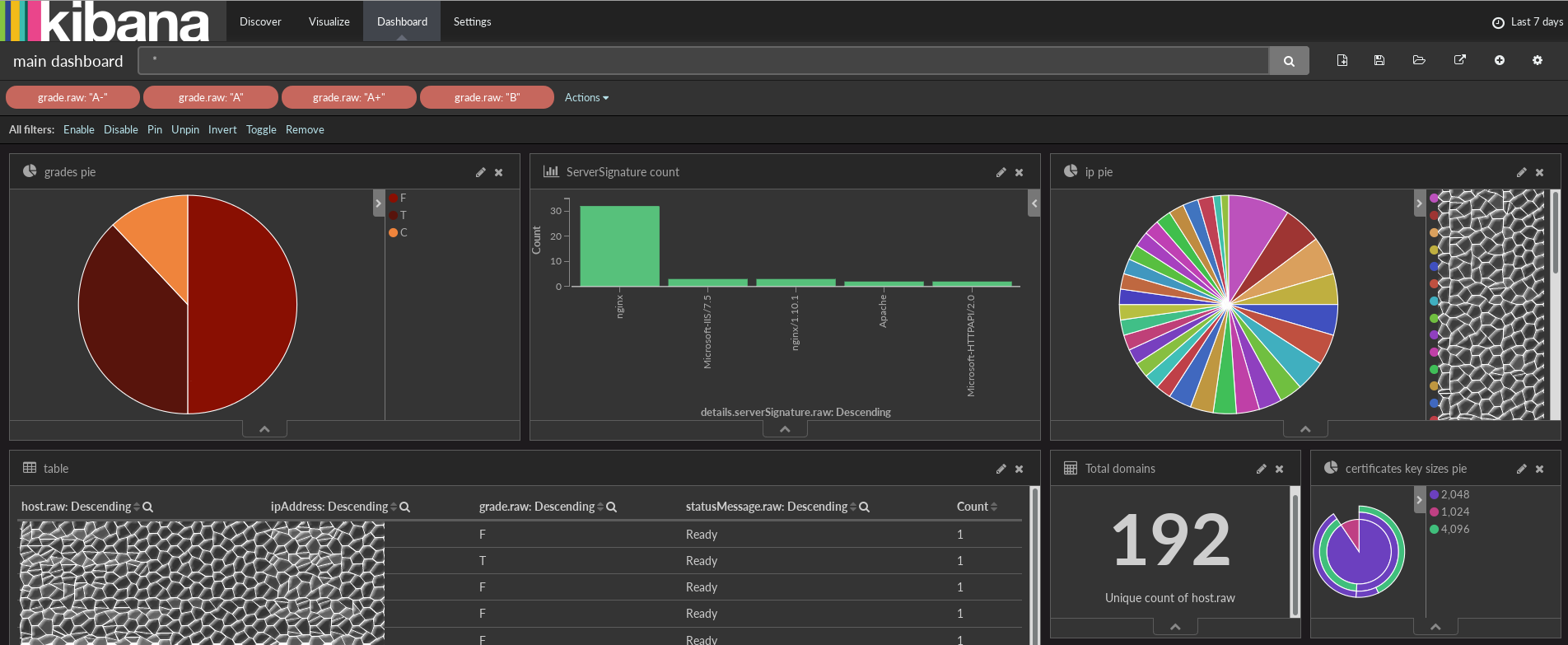
And add your own visualizations, for example, by vulnerability to POODLE, Heartbleed or any other data that the script provides. To see what else is in the database, open the Discover tab and expand JSON. If something is missing for you, simply add the necessary checks to the scan script.
Now, after we have identified the problem areas, the service for generating secure settings from Mozilla will be useful to you.
Todo
In the following releases we plan to add:
- Authorization
- Functionality check HTTP settings Headers
- Convenient interface to search by any parameters of the web server
- Sending email notifications for Remedy integration
If you are interested in the project - write, we will be happy for your commits and suggestions for improvement.
Secure your web and remember, only he is protected, who sees his vulnerabilities from the side!
')
Source: https://habr.com/ru/post/309660/
All Articles