Security Week 36: Nexus 5X vulnerability, crypto-fiber posting pictures, attacking Linux servers via Redis
 The combination of standard developer tools and a couple of undocumented features allows you to hack Nexus 5X phones - working on “pure” Android smartphones manufactured by LG. This is reported by IBM's X-Force laboratory ( news , research ), naturally after Google closed the vulnerability with a patch this week.
The combination of standard developer tools and a couple of undocumented features allows you to hack Nexus 5X phones - working on “pure” Android smartphones manufactured by LG. This is reported by IBM's X-Force laboratory ( news , research ), naturally after Google closed the vulnerability with a patch this week.Apparently the vulnerability could be exploited with a unique combination of firmware and bootloader. Operation requires physical access to the smartphone, or rather cunning and impractical manipulation of the computer to which the Nexus is connected. If you take possession of the phone, everything is simple and reliable. Go to the bootloader menu in fastboot mode, connect via USB. Next, via the adb interface, give the command fastboot oem panic - and this leads to the preservation of a complete memory dump. This dump can also be pulled from the device, and in turn, the clear text stores the password to access the phone.
Everything, you can reboot, enter the stolen password and continue to do whatever your heart desires. Another potential attack vector is interesting: via a “malicious” USB charger, although in practice this is not possible in all cases. IBM does not observe examples of exploitation of an attack, so the hole was closed before it could be used. But the usage scenario here fits well with the canons of some spy series: under cover of darkness, we change the standard charge to the prepared one and get full access to the device. The question is, how many more wonderful discoveries are prepared for us by modern devices. This is not a headphone jack, everything is serious.
')
All episodes of the series are available by tag .
Cry extortionist Cry pretends to be a non-existent state agency, uses Imgur and Google Maps
News Research on the website BleepingComputer.
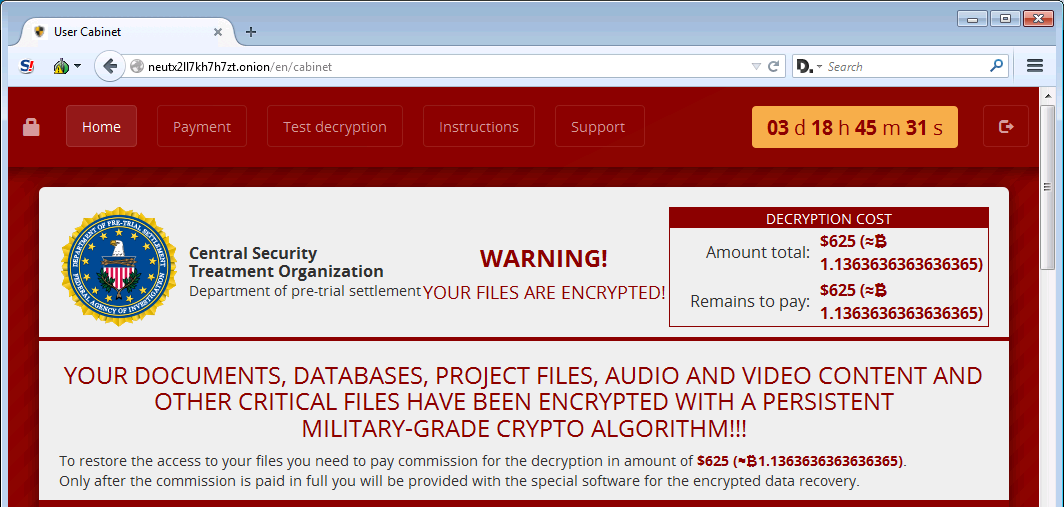
The Cry Trojan is not impressed by the number of victims (until the researchers registered about 8,000 infections), but it is interesting with methods of communication with the command server and data collection attempts that are not required to collect tribute. The infection method is also unknown (Trend Micro assumes the use of an exploit pack), but this is what happens after it. As usual, on the desktop, the ransomware Trojan leaves a postcard to the user with payment instructions and a 1.1 Bitcoin price tag (about $ 625). Sending information about an infected system to the server is unusual. Data is sent via UDP immediately to 4000 IP addresses — apparently with the goal of making it difficult to identify a real C & C server.
In addition, the data is sent in a non-standard way. Information is embedded in the image in PNG format, which is poured onto the Imgur image hosting. After uploading, the Trojan receives a unique image identifier from the service, and now it is sent to thousands of addresses. This method is used in parallel with the direct sending of data. The second interesting side effect of the Cry Trojan is the use of the Google Maps API. Using standard Windows functions, information is requested about nearby WiFi access points, which are used to determine the approximate location of the victim via Google. It is not yet clear why this information is extortionists: the researchers assume that in the future they will be able to threaten the victims more targeted, with the address
In a mass attack on Linux servers, the insecure settings of the Redis caching software were blamed.
News Previous news . Duo Labs study .
Last week, users of the BleepingComputer forum discussed strange attacks on Linux servers: victims found a complete lack of web server files and a text file with a link to the ransom request . The link reported that the owners of the servers were the victims of the Fairware extortioner and there was a demand for payment in the amount of two Bitcoins. It quickly became clear that the websites were deleted entirely, at the root and without the possibility of restoration, so that the ransom would be just an extra waste of time and money. But the reason for hacking servers was not clear, it was assumed that there was a brute force passwords for access via SSH.

Picture for query “brutfors”
Researchers from Duo Labs believe that SSH brute force is not to blame. This could be due to the insecure introduction of Redis software - data caching software. This is not about vulnerability, but about the wrong configuration (possible, however, by default in older versions), which allows you to remotely configure the software. Ideally, this configuration should only occur from trusted hosts, but exceptions are possible. Such exceptions in Duo Labs counted about 18,000, walking around the network by a specialized search engine Shodan.
Of these, an estimated 13,000 hosts could have been attacked (believed to be based on a unique SSH key), although not all eventually became victims of vandalism. And the attack method turned out to be quite simple: if there is a possibility of a remote Redis configuration, you can upload an SSH key to the server through it, and by using it you can login into the system with root rights. The rest is a matter of technique. Such a fig extortionist. By the way, this last year's post on Habré hints that the problem is not new.
What else happened
Lab experts share information about the new Gugi mobile banking Trojan.
Another patch of vulnerabilities in Android.
Mass leak of passwords to Rambler services - almost 100 million records.

Antiquities
"Perfume"
A resident very dangerous virus, standardly infects .COM files (COMMAND.COM is affected when the virus starts). Creates its own TSR-copy, changing nothing in the MCB blocks, which can cause the system to hang. Periodically erases random sectors on the A: drive. At the 80th attempt to infect an already infected file, it starts some kind of dialogue with the operator (in my sample virus, the text is erased). Intercepts int 21h.
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 78.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/309566/
All Articles