Google updated Android
 Google has released an update for Android, closing a number of important vulnerabilities. The update was a three-step and included several levels: 2016-09-01, 2016-09-05, 2016-09-06. The first level of the update fixes common vulnerabilities for all Android firmware, the second level is used to fix vulnerabilities in the Android kernel and its drivers from Broadcom, NVIDIA, Qualcomm (Nexus devices), and the third for two vulnerabilities in the kernel and Qualcomm driver. This is the first Google update that is addressed to Android 7. It fixes a critical RCE vulnerability with identifier CVE-2016-3862 in the well-known MediaServer component. Since Android 7 uses the modular architecture of the MediaServer, this vulnerability is not relevant for it. Outdated versions of Android use a monolithic version of the MediaServer service, therefore, when exploiting a vulnerability in one of its subsystems, attackers have a greater chance of remotely executing code in a system with extended privileges.
Google has released an update for Android, closing a number of important vulnerabilities. The update was a three-step and included several levels: 2016-09-01, 2016-09-05, 2016-09-06. The first level of the update fixes common vulnerabilities for all Android firmware, the second level is used to fix vulnerabilities in the Android kernel and its drivers from Broadcom, NVIDIA, Qualcomm (Nexus devices), and the third for two vulnerabilities in the kernel and Qualcomm driver. This is the first Google update that is addressed to Android 7. It fixes a critical RCE vulnerability with identifier CVE-2016-3862 in the well-known MediaServer component. Since Android 7 uses the modular architecture of the MediaServer, this vulnerability is not relevant for it. Outdated versions of Android use a monolithic version of the MediaServer service, therefore, when exploiting a vulnerability in one of its subsystems, attackers have a greater chance of remotely executing code in a system with extended privileges.A significant number of Important vulnerabilities have been fixed in the Mediaserver component. Three of these vulnerabilities with identifiers CVE-2016-3870, CVE-2016-3871, CVE-2016-3872 are of type Local Privilege Escalation (LPE) and can be used by attackers to execute their code with elevated privileges. Another five vulnerabilities such as Denial of Service (DoS) can be used by attackers to provoke a device hangup or unauthorized reboot.

Fig. The list of DoS vulnerabilities in MediaServer, some of them are also relevant for Android 7.
The update fixes the CVE-2016-3875 vulnerability in the system boot mechanism (device boot), which makes it possible for an attacker to boot the system in safe mode even when it is prohibited. Actual for Android 6.0 and 6.0.1. Another vulnerability with the CVE-2016-3876 identifier is present in the Settings component (Settings) and also allows attackers to boot the system in safe mode when this mode is disabled on the device. Vulnerability is also relevant for Android 7.
')
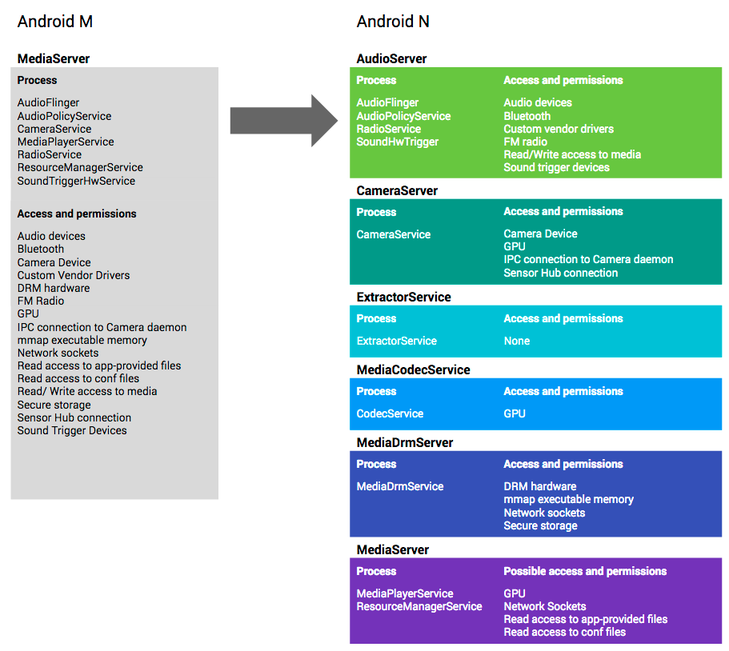
Fig. Architecture MediaServer in the new version of Android provides a secure modular architecture.
Several critical LPE vulnerabilities were fixed in the Android kernel and its various subsystems. Vulnerabilities allow attackers to execute their code at the privilege level of the Android kernel. Vulnerabilities are marked as critical, since deleting a privileged exploitation code may result in device reflashing. These vulnerabilities relate to the update level 2016-09-05 and are relevant only to Google devices, including, Nexus 5, Nexus 5X, Nexus 6, Nexus 6P, Nexus 9, Nexus Player, Pixel C, Android One.

Fig. Fixed vulnerabilities in the kernel and its network subsystem. Actual for all versions of Nexus.
The following kernel subsystems were also updated: netfilter, USB driver, sound subsystems (kernel sound subsystem), ASN.1 decoder, eCryptfs FileSystem, ext4 File System. Qualcomm, Synaptics, Broadcom, NVIDIA drivers were exposed to similar vulnerabilities. The following Qualcomm drivers have been updated. In total, within the framework of 2016-09-05, 29 vulnerabilities were fixed. One of the vulnerabilities in the network subsystem of the kernel with the identifier CVE-2016-4998 is of the type Information Disclosure.
- Qualcomm radio interface layer
- Qualcomm subsystem driver
- Camera driver
- Sound driver
- IPA driver
- Power driver
- Wi-Fi driver
- SPMI driver
- Sound codec
- DMA component
In 2016-09-06, two vulnerabilities were fixed. One type of LPE with the identifier CVE-2016-5340 in the kernel shared memory subsystem. The second with the identifier CVE-2016-2059 in the Qualcomm network component. Both are relevant for Nexus 5, Nexus 5X, Nexus 6, Nexus 6P, Android One.
The use of three levels of Android update is due to practical considerations. For example, the first level of updates is common to all Android devices and is released the very first. Next comes the next level for Google Nexus devices, which includes the first level and all previous updates. After that, another level of updates is released, after Google received feedback from the manufacturers of second-level driver updates. The third level includes the previous two and all previous Android updates. This does not exclude the fact that each of the update levels may receive the other two.
It is a subset of the security rules. Android partners are encouraged to fix all levels of security.
On September 5, 2016, security bulletins. Security patch level can be used for security patch level.
We encourage users to update their devices.

be secure.
Source: https://habr.com/ru/post/309530/
All Articles