Dewy calculations "for dummies"

"Natural" approach
Each of us saw drops of water that appear on the trees, flowers and grass. We will not discover anything new if we say that these dew drops do not fall from the sky, but are formed due to condensation of water vapor, which affect the air humidity indicator. Warm air contains more moisture than cold; at night, when warm air comes in contact with cold surfaces, water vapor condenses in the form of dew drops.

Also, the process of dew formation can be traced through a simple experiment. Take a glass and put it on the table. Now place ice or strongly cooled water inside the glass; You will soon notice that small drops of water have appeared on the outer surface of the glass. These water droplets are formed by the condensation of water vapor present in the air. Similarly, when trees, plants, and grass become cold during the night, water vapor from the air condenses on them in the form of dew. 
')
In cloudy weather, dew forms less than in clear. With a clear sky, both trees and plants have a cooler surface at night, more evaporation of water and, therefore, dew also forms more than when it is overcast and the plants are not sufficiently cooled at night.
If you have read this far, then you are probably wondering how this biological excursion is related to information technology? Now tell.
Traditional approach
To begin with, we will give an example with a regular script that is not related to dewy calculations. Your friend has a smartphone that is used for a variety of purposes, including downloading and listening to music, watching videos, and so on. Plus, applications on this smartphone are used more often than a
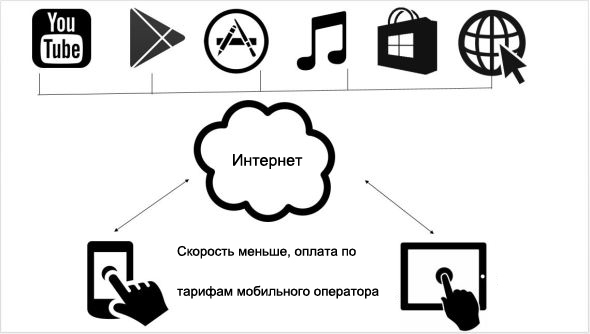
Each appeal to the Internet is paid, it does not matter what the speed of the Internet.
Your friend advises his colleague, who also downloads his favorite video to his iPhone, shows his favorite video, shows his friends and even shares with them through a special file-sharing application.
Comparison of two approaches
As air consists of water vapor, so communities of people around us consist of data. Also, as in clear weather, moisture in the air comes in contact with cool surfaces and forms water droplets on them, and people and people's desire to share data comes in contact with dedicated servers, forming a huge amount of small pools of data on these servers. These servers can be placed in residential complexes, shopping centers, sports and concert stadiums, amusement parks and so on. Small multimedia servers can be found on trains, buses, and airplanes. At the same time, each smartphone operates as an
The owner also has the opportunity to remain anonymous.
| Natural dew | Dewy calculations |
| Clear sky | The desire of people to share data |
| Heated air | Data available on mobile devices |
| Chilled surfaces | Community servers (open data warehouses) |
| Dew | Data on the community servers |
| Condensation | Copy public data from mobile devices to server |
| Evaporation | Copying public data from the server to mobile devices |
| Cloudy weather | The reluctance of people to share data |
Dew Computing Terminology
Dew in nature is formed only in a limited period of time; similarly, dewy computations - they act only when the user's device is connected to the server, and the data from the device is loaded onto it. Failure to do so will disrupt the data transfer process and limit its scope.
Dew Computing Approach
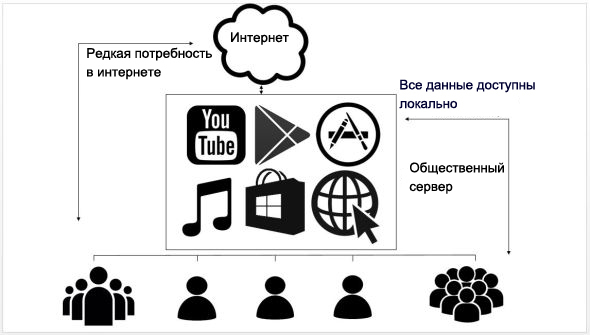
Let us return to the scenario that we discussed above. Suppose your friend and colleague live in the same residential complex, equipped with a community server.
Your friend is in a certain group where he joined to share his files, and any resident of the LCD can now access them.
The most important thing here is the identity of the owner, and it is the data owner who can decide whether to open his name to other users or remain anonymous. For example, if your friend decided to remain anonymous, people from his complex will not see his name in conjunction with the data laid out on a common server. According to the personal settings, some community members may receive notifications when new data is received, or they can set up notification for this purpose.

Public information is uploaded to the community server from the users mobile devices.
Since your friend made his video and music libraries public, his colleague will no longer have to download the video that he showed her; it will be enough just to get it from the community server - for free.
Go ahead: now you can install applications or get any data shared by your friends at high speed (like a LAN) and for free, without wasting mobile traffic. For example, since your friend's applications are always updated in a timely manner, all residents of the LCD can get the latest versions of applications from the server. As soon as
The ultimate goal of dewy computing
The goal of this concept is to participate together and share data in such a way that anyone can get what they need for free and at an excellent speed.
Suppose you are going to visit the mall tomorrow, and by the time you’ve finished shopping, the mall’s community server has already updated all your applications and the phone’s operating system — this is the basic idea of deeper computing using a specific example.
The goal is to stay in the range of the router, in this case, the mechanism of data sharing starts and we can get all the data we need, free of charge and at high speed.
Small community servers, especially multimedia, placed in buses, trains, airplanes, taxis and even cars will allow you to receive a collection of music and videos that you can listen to on the go or save without downloading. All public pools of information from mobile devices of passengers will get to the server, that is, each passenger will have a free shop from which he can select everything he needs. Now, during a long journey on the train, you can watch movies received from other passengers and available on the community servers.
In schools / colleges / universities, data can be shared not only by mobile devices, but also by PCs / computers / laptops, and both small text files and large pools of information such as software updates can act as data. A student with an outdated version of Windows will be able to get an update, share his notes, textbooks, tasks and everything else with other students, since the goal is that all the selected data is available publicly and free of charge when the “within the router” principle is implemented.
Important additions
Confidentiality. It is most important for the data that people are embarrassed to share. In dewy calculations you can remain anonymous.
Security. The “Everyone Sharing Everything” policy is dangerous enough. There will always be fraudsters who want to
Piracy. All that the data owner will share must comply with ethics and legislation - and this is the user's sole responsibility.
The composition of the community. The order of entry into the community is similar to the order of sharing
User participation. The more you participate, the more you will receive.
Amendment to modern technology
Various intelligent system algorithms, machine learning algorithms, analytical “big data” methods can be used on community servers to improve the notification / customization customization mechanisms.
Source: https://habr.com/ru/post/309456/
All Articles