The hunt for Lurk: from the study of malicious code to a criminal case
 When a company is subjected to cyber attack, the first thing to do is understand what it came from, remove the malicious code, and, preferably, find and close a vulnerable point in the infrastructure. And then you can ask the question "who is to blame," although, alas, quite often he is completely unanswered. The task of the security solution providers is to detect and investigate threats, provide protection capabilities, and inform clients. The search for cybercriminals should deal with law enforcement. For this, we share with them the results of our work, but there is one nuance here.
When a company is subjected to cyber attack, the first thing to do is understand what it came from, remove the malicious code, and, preferably, find and close a vulnerable point in the infrastructure. And then you can ask the question "who is to blame," although, alas, quite often he is completely unanswered. The task of the security solution providers is to detect and investigate threats, provide protection capabilities, and inform clients. The search for cybercriminals should deal with law enforcement. For this, we share with them the results of our work, but there is one nuance here.The set of knowledge to protect against malware is somewhat different from the set needed to investigate. In the latter case, there is a need for evidence of a link between different incidents, the belonging of different malware to the same source - well, in general, what is not always required to protect clients. It is important to translate information from a technical language to a legal one. Such work in the "Lab" deals with the Department of Investigation of computer incidents. Recently, they shared information about the investigation of the activities of the group Lurk, aimed at commercial organizations. Campaign victims were infected with a Trojan of the same name, which stole funds from corporate bank accounts.
This side of cybercrime work is covered in detail much less frequently than traditional threat research, and therefore the publication is particularly interesting. This text is a brief extract from several publications on the Securelist on the topic: starting with a brief study of 2012, and ending with a detailed technical analysis of the Lurk Trojan and a story about the many years of investigation into the activities of the group as a whole.
In June of this year, about 50 suspects , allegedly involved in the theft of 3 billion rubles from the accounts of residents of the CIS and CIS countries, were detained . The message of the Ministry of Internal Affairs indicated the commission of numerous embezzlements of "money from the settlement accounts of legal entities, as well as from correspondent accounts of financial institutions using malicious software." “Laboratory” provided the law enforcement agencies with expert support in the investigation, and, in fact, the detention itself put an end to the investigation of our experts, which lasted more than five years.
')
Start
Perhaps the most characteristic moment of the whole story is the story of the very first detection of a part of the Trojan code. These were discovered in 2011 after reports of several cases of theft of funds from corporate bank accounts. The attack technique did not correspond to the highest level of software protection for working with bank transfers of that time: it was enough to modify the bank details in the generated payment orders, after which the money was sent to the accounts of the intruders. The detected module was very difficult to get to work in the laboratory. An additional malicious module discovered later in the same year made it clear that the program is aimed at remote banking systems. But no more than that: the received data was enough to protect against a specific version of the code, but it was not enough to determine the scale of the attack. In a series of much more famous financial cyber attacks of that time ( ZeuS , SpyEye , Carberp ), Lurk was just another dangerous, but not an outstanding malware.
Infection of popular news sites
The situation cleared up in 2012, when there was a massive infection of users through popular news resources. Malicious code, not the first and not the last time, dragged through a banner network.
Sample code of an infected banner
Javascript code redirected to a malicious site, from where visitors were given an exploit for a vulnerability in Java . The malicious code was loaded as an encrypted library directly into the javaw.exe process memory - and this was already a rather non-standard approach for attacks of this type. The "incorporeal" method is known from CodeRed and Slammer virus epidemics, but in this case it was used to download the Lurk Trojan. At this stage, the attack got its name thanks to quite effective technologies of secretive infection and work.

Part of the Lurk malware code responsible for loading additional modules
Despite the fact that more than 300 thousand users were attacked, not all of them got a trojan in addition. A prerequisite for the further exploitation of the security breach was the availability of specialized software for corporate online banking on the infected computer. Looking ahead, I will say that in the end, only 60 thousand systems passed through the Lurk command servers, which is relatively few, precisely because of this selectivity.
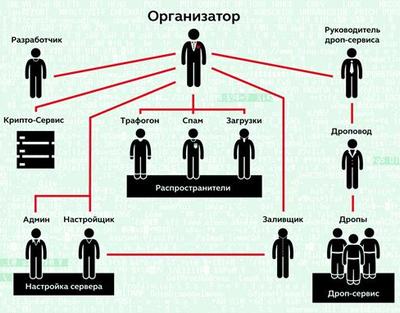
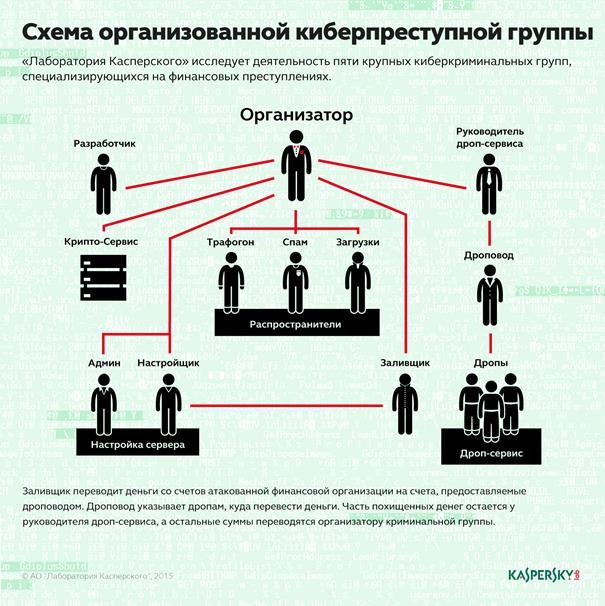
Organization
In 2013, there was enough evidence to reliably link different versions of malware to each other. The complexity of the malicious code grew, additional modules appeared, and the "support" of banking clients expanded. Since we are talking about corporate banking, there are not so many client software options, but for each authors of the attack, it was necessary to do some serious work on studying the principles of operation and reverse engineering of the code - not so much complex as long and tedious. At the same time, our experts used mistakes made by members of a criminal group, which provided information on the number of participants and similar data (examples of errors, however, are not given in the article, for obvious reasons).
In 2013, there were about 15 participants in the group, closer to the final, the number increased to 40. Some people were responsible for developing malware, others worked on the botnet management system, and others cashed out funds. New experienced developers searched in different ways, including through the banal job ads.
At this stage of Lurk work, almost everything was automated: infection and further transfer of funds to dummy accounts, even the distribution of money for subsequent cashing almost did not require human intervention.
No money left
The Golden Age ended rather quickly. Already in 2014, the group began to experience a shortage of funds. From the outside, this was noticeable by expanding the circle of potential victims, including ordinary users, and increasingly, criminals turned out to deal with a relatively small potential sum. The reason for this was changes in the field of security software for banking services. Vendors stopped posting demo versions of products on the site, it became more difficult to get new versions for studying. There were technologies to counter the simplest method of automatic substitution of bank details. The attackers even tried to get a copy of the programs to study through a dummy legal entity. At this moment, on the Lab side, all new versions of malicious modules were seen, and they could promptly analyze and update protection systems for clients. Meanwhile, the maintenance of an extensive campaign support infrastructure each month cost, according to our experts, tens of thousands of dollars.
Business diversification began: Angler's exploit-pack appeared, which earned criminal-to-criminal in the market. It is he who, by the way, is the most well-known product of the group outside Russia: at different times, new versions of the pack were analyzed by experts from many antivirus campaigns. In June of this year, several independent sources confirmed that the activity of Angler was completely discontinued, which just coincided with the arrest of the suspects.
The final attempt to broaden the scope of the cybercrime business was manual attacks on banking systems. Avtozaliv has not worked for a long time, the Lurk toolkit was used to penetrate the victim's infrastructure - and then how lucky. By that time, our experts had uncovered the methodology of the Carbanak campaign, which specialized in banks and large companies, and at the same time found similar in character attacks using different, but already well-known, malicious tools.
According to our experts, although the Lurk attacks continued until the spring of 2016, there were organizational problems within the group, including not the best way that affected compliance with the conspiracy. Especially at the most vulnerable stage of work - when cashing money. The set of front companies for the transfer of the stolen was limited, and as a result it was possible to gather enough technical expertise and evidence for the arrest of the suspects.
Some technical features
A full description of malicious modules Lurk is in this article, but here I will give only the most interesting features.
The majority of the victims were infected (in the later stages of work) with the help of Angler's exploit pack, through the hacking of a popular or specialized site (often accounting forums fell under the gun), directly or through third-party banners or partner elements. But, in the event that an “uninteresting” system was found to be infected in an “interesting” organization, reconnaissance over the local network was carried out, and penetration was carried out, including using the absolutely legitimate utility psexec.
The main body of the malware (core module) was loaded only on suitable systems. If the required target software was not detected, the intelligence modules were removed, but passwords for ftp servers from their respective clients could be stolen before that. The addresses of the command servers were not fixed in the main module. They were calculated (or more precisely generated from two sides) based on indirect information, for example, using data on current stock quotes.
In later versions of Lurk, keyboard interception is implemented, but only in the case of working in a specific program. In some cases, the video content of the screen was intercepted.
In the spring of this year, there was a series of reports on successful attacks on the SWIFT interbank transfer system. The details of these attacks are little known, and not the fact that they will be shared in the near future. Our analysis of Lurk provides an explanation for such slowness: here the reason is the need to collect a large amount of technical data, and because of the peculiarities of interaction with law enforcement agencies (again, it is easier to detect a malicious attack than to investigate everything to the end). One moment from the technical analysis of Lurk, I suppose, will be reproduced more than once in other investigations of similar attacks: you can reliably protect clients of financial systems only if the protection is implemented on the server side as well. In other words, the solution to the problem with this type of cyber attacks is to work together (in the case of Lurk, this is both a vendor of security solutions, software developers, banking organizations, their clients, and law enforcement agencies).
Disclaimer: This column is based on real events, but still reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/309260/
All Articles