Perimeter defense: old attacks are not worse than new ones

External threats to information security are usually associated with hacker attacks on the network perimeter, including complex targeted attacks against large companies and government agencies (APT). A recent example is the hacking of the Equation Group with the subsequent publication of part of their toolkit for overcoming the network perimeter. As it turned out, many exploits from this set used long-known vulnerabilities, although the “cherry on the cake” was 0-Day for SNMP services (an abbreviation of “ S security N o M y P roblem”). Unfortunately, we do not have a complete set of merged exploits to fully appreciate the scale of the disaster. However, we can use the approach from the reverse - to assess the degree of security of corporate perimeters based on the actual statistics of their vulnerabilities.
One of such studies was presented at the PHDays VI conference in our traditional collection Positive Research 2016. The sample included about 10,000 available addresses and 15,000 vulnerabilities, the study period was two years (2014-2015). However, it is necessary to clarify that the study was carried out only for network perimeters with a security level above the average: that is, only companies that have established asset inventory and vulnerability management processes (which actually allows collecting statistics) have been considered.
')
Let's start with the hottest topic in the published exploit pack: SNMP 0-Day. Is this threat relevant? Our research shows that yes. Here are some reasons for this situation:
- Analysis using honeypot systems shows that SNMP services are very popular with potential intruders - a wide range of hackers already knows about the availability of these services. And who else does not know, without complications can learn through Shodan.
- There are a lot of SNMP services, they are available on most modern network infrastructures. In particular, we have already said that the exploitation of SNMP vulnerabilities can penetrate the technological networks of telecom operators.
- Many SNMP services run on outdated software versions. According to our research, in the category of DNS, NTP and SNMP-services every tenth is vulnerable:

Based on these statistics, you can definitely evaluate the published exploit: it is very dangerous and can be used to overcome the network perimeter of many organizations.
However, another interesting question remains. Why did the Equation Group, which is loudly called the “complete state cyber weapon set,” turn out to have many exploits for old vulnerabilities, including those for which security updates were released more than 5 years ago? It would seem that such a cool hacker group should actively use new, unknown vulnerabilities.
The answer is paradoxically simple, if we correctly reformulate the question: why should hacker groups spend their precious time on 0-Days, if a significant part of the systems available via the Internet has not been updated for years?
Our study showed that three-quarters of all detected vulnerabilities are older than one year, 30% of vulnerabilities are older than 5 years, and almost every tenth vulnerability could be fixed 10 years ago. Over the investigated time interval, vulnerabilities were detected on 37% of the systems.

By clicking the picture will open in full size.
Thus, for successful attack there is no need to use the latest vulnerabilities: the old ones are great. They are cheaper, and the hacker group to disclose information about the exploitation of the old vulnerability is less critical than to “light up” 0-Day.
But so far we have considered only the situation with exploits in a closed toolkit. Are exploits from old open source vulnerabilities, say, MSF, suitable? To answer this question, we chose vulnerabilities with CVSS “High” values that were available at the beginning of the study period in the systems under test, and compared them with known exploit packs.
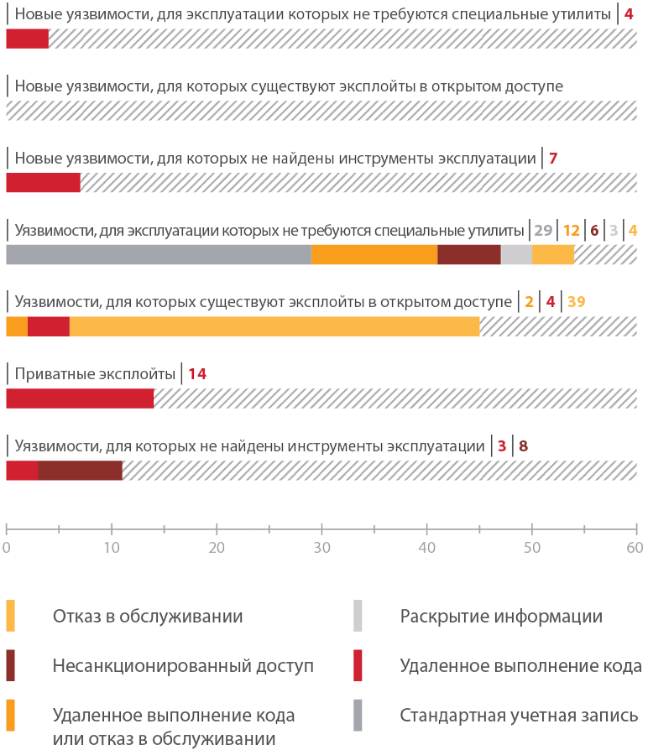
From this statistics it is clear that at the perimeters of the companies studied there are vulnerabilities that can be exploited through public exploits. However, this sample contains a very small set of vulnerabilities. Does this really mean that there are few of them? As we said earlier, the sampling on vulnerabilities in the previous picture was made only for the initial period of the study, and the level of perimeter security never remains the same. The dynamics of changes over two years are clearly shown by the following graphs:

By clicking the picture will open in full size.
So, a summary: to overcome the perimeters, the security level of which is estimated above the average, does not require any exploits from sealed sources, and the more secret knowledge of the APT-groups on the use of their own 0-Day. Enough standard tools.
How to defend
Taking into account the findings, we highlight the following main areas to improve the overall security level of the network perimeter:
- Permanent monitoring of the company's network perimeter, the result of which should be the rapid detection of services located on the perimeter and accessible from the Internet.
- Automated search for vulnerabilities in services located on the perimeter. The result should be the identification of vulnerabilities and monitoring their removal.
- Elimination of unnecessary services, the need to place them on the perimeter is not due to any objective necessity. These categories of services may include NTP, SNMP, database services, administrative interfaces, and other categories of potentially dangerous services.
- Implementing a patch management policy, with first of all, attention should be paid to systems with vulnerabilities for which there are open source exploits, as well as to the most vulnerable systems. The remaining systems should be updated in accordance with the prioritization of critical systems and vulnerabilities.
- Using an integrated approach to information security. Securing the network perimeter is the basis for ensuring information security, but the perimeter is not the only vector of intruder penetration into the company's infrastructure.
Full version of the report on the level of corporate perimeter security can be found here.
Author: Vladimir Lapshin, Head of Information Security Monitoring, Positive Technologies
Source: https://habr.com/ru/post/309072/
All Articles