AMD introduces new security mechanisms for its AMD-V hypervisor
 AMD has announced the release of a new technology to protect the memory of virtual machines hypervisor called Secure Encrypted Virtualization (SEV). AMD's new technology has common features with another similar initiative from Intel called Intel Software Guard Extensions (SGX), which allows an application to allocate specific regions of virtual memory (enclaves) that are not readable even by applications with higher privileges. Unlike SGX, SEV offers a similar concept for the memory of virtual machines, but protection, in this case, will be built by encrypting the contents of memory blocks. Encryption of the private part of the virtual machine's memory is performed by the guest key, and of the memory shared by the special key of the hypervisor.
AMD has announced the release of a new technology to protect the memory of virtual machines hypervisor called Secure Encrypted Virtualization (SEV). AMD's new technology has common features with another similar initiative from Intel called Intel Software Guard Extensions (SGX), which allows an application to allocate specific regions of virtual memory (enclaves) that are not readable even by applications with higher privileges. Unlike SGX, SEV offers a similar concept for the memory of virtual machines, but protection, in this case, will be built by encrypting the contents of memory blocks. Encryption of the private part of the virtual machine's memory is performed by the guest key, and of the memory shared by the special key of the hypervisor.This is an extension of the AMD-V architecture which supports running multiple VMs. It is intended that when it is used, it is intended to. This is a tag that has been kept by the SOC. AES with 128 bit encryption while it protects data outside the SOC. It is encrypted / decrypted when it comes to data associated with the tag.
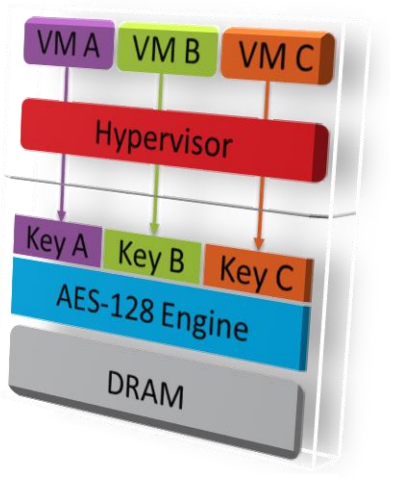
Fig. The SEV architecture, the contents of the virtual machine memory is encrypted using the AES symmetric algorithm and an individual key for each virtual machine.
Thus, the operations of encrypting / decrypting the contents of memory will occur at the level of the microprocessor (System-on-Chip, SOC) and at the moment when the data itself will be in its internal cache. When data is loaded into the internal memory of the microprocessor, it will be decrypted, and when unloaded it will be encrypted.
')
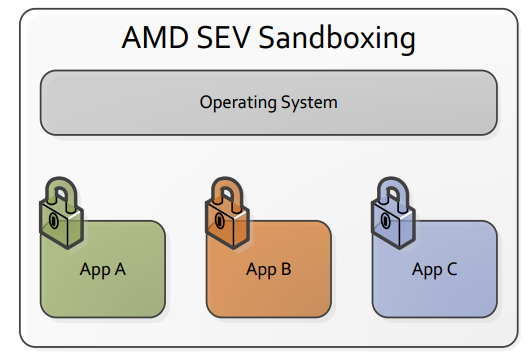
Fig. SEV also allows you to isolate and encrypt the memory of individual applications to protect against unauthorized access.
AMD specialists point out that memory isolation and encryption operations can occur not only at the level of entire virtual machines, but also at the level of individual applications, as provided for in the Intel SGX.
VMV is a hypervisor. In particular, it is possible to prevent these types of VMs (eg hypervisor read-anywhere).
SEV allows applications to protect memory regions not only from applications with higher privileges, but also from a potentially vulnerable hypervisor, vulnerabilities in which attackers can use for VM-escape attacks.

Fig. An example of using SEV.
The figure above shows a typical example of using SEV. A virtual machine (guest) marks virtual pages with code and application data as private (i.e., subject to encryption), and a mandatory protective measure is imposed on memory pages with process page tables. Shared service data (shared) that is accessible to both the hypervisor and the virtual machine is marked as public. The entire contents of the private part of the memory is encrypted using an individual for this virtual machine key, which is unknown even to the hypervisor. The contents of the shared memory are encrypted using the hypervisor key.
A more detailed description of the SEV can be found in the manual from AMD.
Source: https://habr.com/ru/post/308968/
All Articles