1 million webcams infected with the BASHLITE worm and used for DDoS attacks

More than a million internet-connected video cameras and DVRs have been compromised and are part of the botnet that its creators use to conduct DDoS attacks. This was reported by researchers from Level 3 Threat Research Labs. According to their information, the attackers use a family of malicious software, which is known under the names Lizkebab, BASHLITE, Torlus and Gafgyt - hackers have already infected about a million devices in different countries.
Security experts conducted a study of well-known botnets, and as they entered, they found out that the BASHLITE worm was associated with some of the most organized and well-structured ones. At the same time, the botnet size could vary from week to week - the researchers recorded interactions of the BASHLITE software with 74 bots, and in a few days there could be 120,000. In particular, a large botnet was found that used about 100 command servers - this system conducted up to 1000 DDoS attacks per day, many of them lasted 5 minutes or less.
')
Researchers estimate that BASHLITE has infected about 1 million Internet of Things devices, of which approximately 96% are cameras and video surveillance systems (DVRs). Much of the devices are located in Taiwan, Brazil and Colombia.
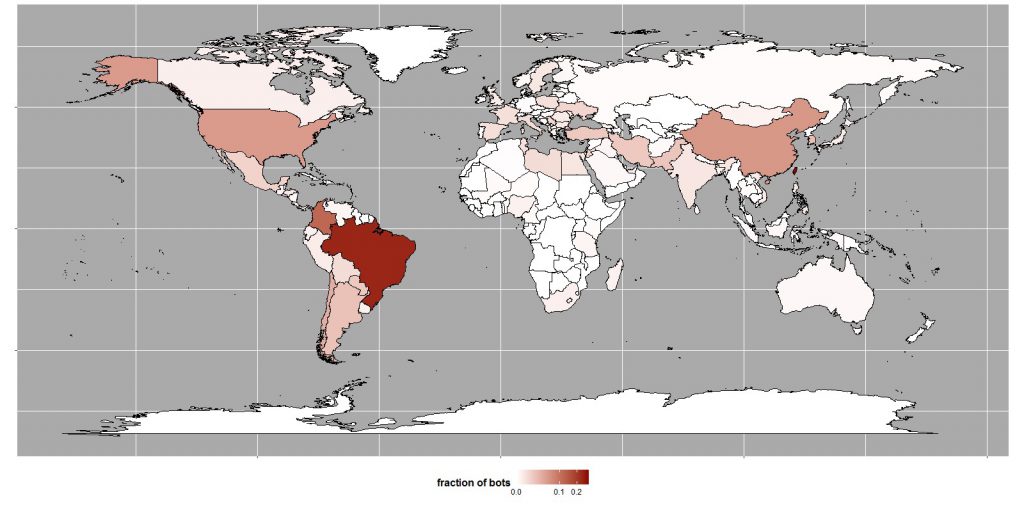
Geographical distribution of attacks
At the same time, attackers are most often interested in video surveillance systems - it is not difficult for them to take control of them, since very often Telnet services are not disabled on them, and web interfaces are accessible from the Internet with standard logins and passwords.
Much of the infected IoT devices are released by several companies, one of them is Dahua Technology. According to researchers from Level 3, vendors are already preparing patches to close the vulnerabilities that are used by the software BASHLITE.
This is not the first time that a camera connected to the Internet is attacked and combined into botnets. Earlier this year, researchers at Sucuri discovered a botnet of 25,000 Internet-connected video surveillance devices. In addition, a botnet for DDoS attacks consisting of infected webcams was found by experts from Arbor's Security Engineering and Response Team (ASERT).
Positive technologies also found critical vulnerabilities in popular firmware for DVR devices. Errors include the standard superuser password, which cannot be changed due to the nature of its storage, open service ports, and multiple vulnerabilities in the software of the DVR device that allow an attacker to access the system. In addition, experts have discovered the so-called master password, which fits to the account of any user of the system and provides access to a video surveillance device with maximum privileges. This password is the same for all DVR devices running this software and cannot be changed by the user.
Devices using vulnerable software are sold under dozens of brands around the world. At the same time, manufacturers often completely copy vulnerable software and use it without any changes in their own developments. At the same time, they probably do not have access to the source code of the initial system containing the vulnerabilities, which makes it impossible for them to fix security errors.
According to experts from Positive Technologies, the share of these systems is more than 90% of the market segment of devices of this class. Such devices are used in security systems primarily by small and medium-sized businesses, as well as by private individuals (for example, in order to keep an eye on their apartment via the Internet). A large number of vulnerable systems can be found on the Internet using ordinary search engines. At the time of discovery of vulnerabilities in the firmware, search engines indexed about 500,000 such devices, which would not be difficult for an attacker to get full access to.
More information was presented in a report during the Forum Positive Hack Days III:
Source: https://habr.com/ru/post/308898/
All Articles