Bitcoin - money for everyone
Translation of the Adam Tepper book “Bitcoin - The People's Money”. The book is a great introduction to Bitcoin "from scratch", but it may be useful to those who already understand the topic.
Table of contents
It seems that the preface for such a little book turns out to be a bit much, but somehow I will have to write a few words. I took up the translation of this text, firstly, as a kind of tribute to the deceased colleague (and friend), with whom I worked for the past few years; secondly, because this book is really a great introduction to bitcoin for people who are not knowledgeable about information technology. It seems to me that the appearance of this text is quite detailed, and at the same time not too long — it will be useful in Russian. The more people get acquainted with bitcoin, the less they will be afraid of him - after all, unfamiliar things scare away, and in the mysterious bitcoin there is absolutely nothing to worry about.
A few comments about the actual translation. A number of anglicisms - "mining", "blockchain", "hashing", etc. - are widely used in Russian-language articles on Bitcoin, and the attempt to get rid of them, I think, does not bode well for the meaning of the text; in fact, you can, of course, translate "mining" as "mining" or "production", "blockchain" as "chain of blocks" (which sounds somewhat clumsy), but how then to call "miner" - "prospector"? "Getter"? - this is too much.
')
The word "bitcoin" also, obviously, remains without translation. In the text, it is used as in the singular (“bitcoin” in the substantive sense, as “money”), and in the plural (“bitcoin” in a specific form, as “coins”).
If the word "dollar" is used in the text without further instructions, it means the US dollar.
The text of the book is available for download in PDF in English and Russian languages on the site www.independentreserve.com (registration is required), a paper version can also be ordered there (only English). Not being a professional translator, I will gladly accept amendments and clarifications, if any. I want to thank Olga Yurieva for the initial reading of the text and Vatslav Egurnova for the titanic work on editing.
Alexey Zhikharevich
Adam Tepper died tragically in a car accident in February 2015, before he finished this book. As a close friend of Adam and his business partner in countless projects, I had to finish what he started by completing his manuscript and publishing this book in print.
I would like to emphasize that, although I made some changes and edits to this book, I firmly believe that they correspond to what Adam himself would have done if he had such an opportunity. This book, therefore, remains the work of Adam Tepper, and corresponds to his authorial intent.
Special thanks to those who donated money to the Adam family, and also made a donation through the Bitcoin page of the Australian Association to help pay for the publication of this book. Also, thanks to the Bitcoin embassy in Australia and those who have spent time reading the book and reviews about it at different stages.
Adam was a kind, intelligent and passionate young man with a clear vision of a future in which bitcoin can change people's lives for the better. Adam's favorite writer was Richard Feynman for his ability to explain complex and seemingly inaccessible ideas in clear and simple words. This talent was inherent in Adam himself, and this book is a great confirmation of this. I hope you enjoy learning Bitcoin through the words and thoughts of Adam Tepper.
Adrian Gentle
 Adam Tepper February 13, 1981 - February 26, 2015
Adam Tepper February 13, 1981 - February 26, 2015
Since I am one of the founders of Independent Reserve, an online currency exchange service specializing in exchanging bitcoin for other currencies, I am often asked to clarify what bitcoin is and why it is important. At the very beginning, I probably didn’t explain it very well to people, because Bitcoin connects many different ideas, mostly unusual. Albert Einstein once said: “If you cannot explain something simply, then you yourself do not understand it well enough,” and I think that to some extent this was the reason that I initially had difficulties explaining to others what bitcoin
Today, I still meet people who have never heard of bitcoin, and they ask me what it is. I usually answer in the shortest possible way, explaining the practical benefits of Bitcoin and omitting more interesting details about how it works. If a person is interested, I am ready to answer his questions until he reaches an understanding at the level that suits him. This is also the purpose of my book, and I arranged the chapters of the book in a similar way. The intended audience of this book is people who are completely unfamiliar with Bitcoin and completely unfamiliar with computer science in general. It is designed for the reader who wants to understand the basics of how bitcoin works, and at the same time understand technologies. The book begins with a review of Bitcoin in a practical sense, then I disassemble the ideas behind Bitcoin, and finally answer some more general questions that ask me about Bitcoin today.
Adam Tepper
Bitcoin is a currency, and thus is money. Money was not always what it is in our understanding today, and essentially Bitcoin is another development of the idea of money. One of the key factors that highlights bitcoin in comparison with other well-known currencies, such as the US dollar ($), the British pound (£) or the euro (€), is that bitcoin is an electronic currency, which generally means that bitcoin is stored electronically on computers [1] , and transmitted electronically over the Internet. The prospect of electronic money can confuse or discourage many people, just as email could confuse someone in the 1980s when it was described as emails stored and sent electronically via the Internet. Today, email is so common that paper letters, especially personal letters, are considered old-fashioned, cumbersome and, among other things, slow.
The first email users in the late 1980s or early 1990s may remember that at the very beginning it was not very helpful, because most of your friends, family and colleagues did not have an email address, nor even, perhaps, Internet connections. Friends asked questions like: “What is an e-mail and how to use it?”. It was a time when there was no Gmail, no Google, not even Hotmail. Electronic mailboxes were mainly provided by Internet providers. But soon most people had email addresses, and today it seems extremely unusual if someone doesn’t have an email address at all, just as if a person doesn’t have a mobile phone.
I’m talking about e-mail because this is a great bitcoin analogy. E-mail took the process of sending letters, used for many thousands of years, and adapted it to transmit and store letters in electronic form. In a relatively short time, the process of exchanging handwritten letters has become an archaic and unusual method of communication. It would be hard to imagine that we should mail again for daily communication and wait for a response for several days or a week. It is also worth mentioning that over the past twenty or thirty years, the ways we use email have also changed somewhat. We have access to the e-mail from all our devices; we can send large attachments and diverse content; we can use email to make appointments that appear on our calendars. All these ideas were not originally laid out when creating e-mail, but became its development based on how we use mail. Of course, there are many other forms of electronic communication that have evolved later. This development refers to the continuous improvement of electronic communication in general. But initially very few people saw the benefits of using e-mail.
This brings us back to bitcoin. Just as e-mail became the thing that brought communication into the electronic age, so bitcoin is what brings our monetary system into the electronic era. Before we consider how bitcoin can do this, it’s worth taking a look at the history of money to build a perspective.
Money today is a very complex system. Most of the time it works, but from time to time it catastrophically breaks down. Although the system is complex, most complex things are invisible to us with its daily use. For most of our lives, the monetary system has barely changed - it’s something that we all grew up with, and most of us probably didn’t spend much time thinking about how it works. Money was not always the same. One of the biggest changes in the last hundred years has been the placement of most major currencies on the free market, as opposed to determining the price for gold or silver by the current government. This was a very significant progress of the monetary system, but let's look back even further to see how money has changed over thousands of years of use in various societies.
I remember when I was a child, I asked my father: "What did people do to money?" My father explained that “in the old days” people used the barter system, using sheep and other animals as currency. As a child, it was difficult for me to imagine how this could work, but in fact this is how money worked several thousand years ago. Sheep and cattle in general had certain drawbacks. They were difficult to store, difficult to move, and not easy to divide. Throughout human history, different cultures have used different products for these purposes. Seashells and rice were used as money, and then precious metals, gold or silver, which later became customary because they had many qualities suitable for currency: they were durable, portable, divisible and rare.
To make a transaction using a precious metal, such as gold, you can determine the value of an item as the value of a certain amount of gold. This decision was imperfect, since the process of assessing the purity of the metal and its weight did not contribute to the speed of transactions. States later improved this process by minting standardized coins containing a certain amount of precious metal, the weight and authenticity of which were confirmed by the state. This is an interesting moment in the history of money. It is interesting because, although the coins contained the prescribed amount of gold or silver, they were valued by the state, and the merchants did not need to analyze the purity and authenticity of the coins as such. Consequently, trust has now shifted to the state. It did not take long for governments to understand that since the value of coins lies in the sign of the mint, it will be cheaper to produce coins containing less precious metal than the indicated weight of the coin. This step in the history of money was a change that turned a coin from a unit of weight into a unit of value.
As European trade flourished in the Middle Ages, the idea of a bill of exchange spread, through which a merchant could offer a credit line to a trusted buyer. The goods were delivered to the buyer in exchange for a bill on which he pledged to make payment on a certain day in the future. Provided that the buyer was a respected person, or the bill was approved by a trustworthy guarantor, the seller could then submit it to the bank for redemption at a reduced price before the expected date. These bills were also used by the seller as a form of payment to make additional purchases from their suppliers. Thus, promissory notes - an early form of credit - became both a means of exchange and a store of value.
In the twelfth century, the English monarchy introduced a system based on similar prerequisites — mortgages through which the monarchy could make payments based on expected taxes that had not yet been received. They were also known as tally (notched wooden sticks). The treasury found that they could also be used as money. When the crown exhausted its resources, she could use a tally representing future tax payments to the crown as a form of payment to her own creditors, who in turn could either collect taxes directly from payers or use these tally to pay their own taxes to the government. Thus, the tally was taken as a medium of exchange for certain types of transactions and as a store of value. The Treasury soon realized that it could issue a tally without any specific tax payments. By doing this, the treasury created new money, secured by public trust and faith in the state, rather than specific incomes.
At about the same time, banks began to issue paper notes, quite correctly called "banknotes", which were treated in the same way that the government issued currency is circulating today. Only denominations issued by the largest, most creditworthy banks were widely accepted. Papers of smaller, less well-known institutions were used only locally. Away from home, they were taken at a reduced price, if they were taken at all. The spread of money types went hand in hand with the multiplication of the number of financial institutions.
Banknotes were a form of secured money that could be turned into gold or silver upon presentation to a bank. Since banks issued significantly more securities than they kept gold and silver on deposits, a sudden loss of confidence in the bank could have caused a massive redemption of banknotes, which led to bankruptcy.
The use of banknotes issued by private commercial banks as legal tender was gradually superseded by the issuance of banknotes authorized and controlled by national governments. The Bank of England was given the exclusive right to issue banknotes in England in 1694, thus ending the use of private currency in the kingdom. Australia passed a similar law more than two centuries later, in 1910, and the United States followed in 1913.
Government-authorized currencies were a form of secured money, since they were partially secured with gold or silver and theoretically could be turned into gold or silver. At the time of President Nixon, the US dollar was withdrawn from the "gold-backed" standard in 1971, which caused the collapse of the international Bretton Woods monetary system. Most of the major world currencies were then placed on the open market, completely losing touch with precious metals, now the value of the currency was based solely on the economy and the reliability of the government issuing it.
Having understood the history of money, we can also see their weakness. Now let's take a closer look at the work of Bitcoin and its advantages over existing forms of money.
Bitcoin technology is fascinating. The first time I heard about Bitcoin a few years ago, almost immediately, as it appeared in 2009. My friend Joe, a man who likes to advertise the latest technological trends, told me that "one guy had figured out how to create Internet money." I did not understand the meaning of this phrase, and I believe that at that time my friend did not understand it either.
I no longer thought about bitcoin before I noticed an online advertisement some time ago, in November 2012, which contained something about bitcoin, and thought that I should take a look. The first thing I noted is that bitcoin, whatever it was, was selling for $ 10, and so it was for some time. I expected it to cost no more than a few cents, or even fractions of a cent. Of course, not knowing anything about bitcoin at that time, I could not understand how much bitcoin should cost, but assuming that there are millions of bitcoins in circulation, $ 10 seemed to be a significant figure, and I was curious to find out everything in more detail. After reading the many materials I found on the Internet, I was still far from understanding what bitcoin was or how it worked. Only after careful re-reading and research of cross-references to various resources I began to put a picture in my head. Definitely, I would not call it a deep or thorough understanding, I still had a lot of questions.
However, bitcoin captured my interest, and, being a programmer, I decided to write my primitive program that would allow me to send and receive bitcoins (it was never published, it was just an experiment to see how it works and satisfy my curiosity). I never finished this program, but spent two or three weeks developing it, and doing this, I eventually came to understand how Bitcoin works, and was deeply impressed and amazed at the underlying technology. She was amazed because she elegantly brought together many dissimilar principles of programming into a system that no one had ever thought of before, and which could now be effectively used as money.
Not wanting to advertise the idea in vain, about which I had doubts whether it would turn out to be another “perpetual motion machine”, I waited until I understood bitcoin deep enough before transferring this knowledge to my business partner Adrian Adorable. I was met with skepticism at exactly the same level as I had expected. A month later, he remarked to me: “Bitcoin is really an amazing thing - I've bought a little.”
So what was it about bitcoin that we both found striking, and what later led us on the path to creating a company so tied to bitcoin? In the second part of the book, we will deal with the technologies underlying Bitcoin, but first I must explain how it works at a high level. Bitcoin is a cross between physical currency and a checkbook. So far, we can only draw this analogy, but let's start with this.
Using this example, let's say I want to send my friend Joe $ 50 (USD). I can write a check with his name on it, write the amount and put my signature on the bottom of the check. In a perfect world, this is a great system. Joe gets a check, and he can't change the amount. If the check is stolen, it won’t help the thief, because Joe’s name is on the check. And if my checkbook is stolen, then it will have no value for anyone, because the checks do not have my signature yet. This is a good system in theory, but in practice it has several disadvantages. First, the check itself is not money. A check is essentially a letter to the bank authorizing the bank to give Joe $ 50 of my money stored there. As long as Joe does not bring the check to the bank, he does not know for sure if I have this 50 dollars. It may take the bank several days or a week to give Joe the money. Signatures are very easy to fake, so if someone gets my checkbook, it will not be particularly difficult for him to write a fraudulent check. In Australia, checkbooks are not used for about a generation; the concept itself is as archaic for us as the trade in gold bullion, but surprisingly, this system prevails in many countries, including the United States.
Let's compare this transaction with the transaction that bitcoin uses - let's say I want to send my friend Joe 50 bitcoins (XBT [2] ). The first key difference between the checkbook example and the bitcoin is that in the case of
checkbook stores $ 50 bank for me. Bitcoin, however, looks more like cash, and 50 bitcoins can be stored physically on your computer. [3] . Let's say I have 50 bitcoins in a digital wallet on my mobile phone that I want to send Jo to his mobile phone. First I ask Joe his bitcoin address. When I send money to Joe’s address, they can only be spent with the secret key stored on Joe’s phone. No one else can use this money without access to his phone.
So, with the help of a program on my phone, I start a transaction that sends 50 bitcoins from my personal bitcoin address to Joe's bitcoin address. Then I put a digital signature on this transaction, using the secret key on my phone, and send this information to the Internet, so that it is visible to the whole world. It's true, I don't send anything directly to Joe, I send information for the entire Bitcoin network.
What happens next is that when the rest of the computers in the bitcoin network receive information about my transaction, they check that I really have 50 bitcoins in my wallet and that my signature is correct. If everything is in order, they mark the transaction as valid, and soon it becomes part of the official global bitcoin ledger, known as the “blockchain” or “blockchain”, and is stored in it (we will discuss this in more detail below).
In the meantime, the program on Joe's phone, along with the rest of the world, confirms the transaction I started. Almost instantly, this transaction is displayed on his phone as the arrival of 50 bitcoins.
If I sent money to Joe, I can no longer spend these 50 bitcoins, because the bitcoin network no longer recognizes these 50 bitcoins as belonging to me, and can be spent only if you use Joe's secret key. Let's look at this situation from a different angle: the transaction I started was, in effect, a “letter” to the bitcoin network, transferring to Joe my right to spend 50 bitcoins. It's easy!
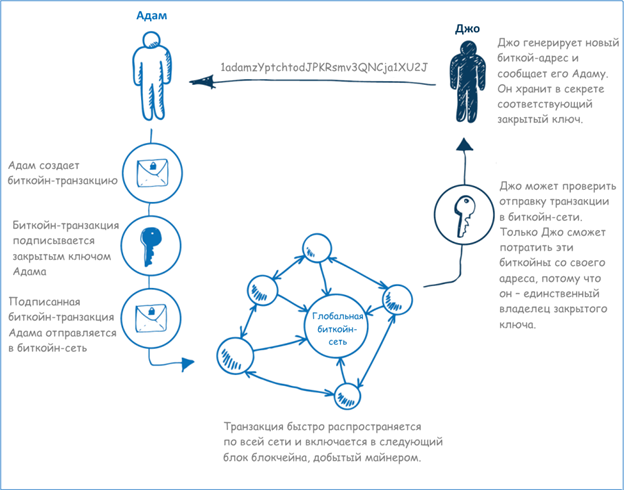 Fig. 1. Adam sends Joe bitcoins through the bitcoin network
Fig. 1. Adam sends Joe bitcoins through the bitcoin network
Let's look at this model more closely and analyze some of the differences between bitcoin and checkbook. In the case of a checkbook, there is a central bank that processes transactions.In the case of Bitcoin, there is no central transaction handler or supervisor — a decentralized model is used in which every member of the network, including the recipient, can authenticate the transaction. This is a quick process. For less risky transactions with small amounts, this process takes no more than a few seconds. For more risky transactions with large amounts, the transaction can be safely recognized as completed in about half an hour. Compare this with a bank check or SWIFT transfer, which usually takes from 1 to 5 days.
Another similar detail that you should have noticed is that bitcoin transactions are signed, just like old-fashioned checks. However, the difference is that a six-year-old child can manage with a fake signature on paper, whereas a fake digital signature used in a bitcoin transaction is almost impossible [4] .
Another interesting point is that the transaction processing cost and execution time are consistent, and they do not depend on the amount of the transaction [5] . Using the example above, I could send Joe a share of bit in bitcoins to pay the royalties he gets for his platinum album, or I could send him two million dollars to acquire his successful company. In any of these cases, the transaction fee will be the same, almost zero, and the execution time is almost instant. This ensures efficient, free and secure movement of money internationally at the speed of email.
Finally, it is worth noting that since the Bitcoin network covers the entire Internet, it doesn’t matter where Joe and I are physically located. We can sit in the same room or in different parts of the world - it does not matter. This does not affect the speed or the cost of the transaction.
In the previous chapter, we looked at an everyday example of how bitcoin can be used to send money between network members. However, here are the questions that people usually ask me: how Bitcoins are generated, how they are introduced into the economy, and where Bitcoin gets its value from. Before answering these questions, let us recall the history of money, which we discussed in the second chapter.
Until the twentieth century, money was at least partially provided with precious metals, such as gold or silver. Along with other important qualities that made gold and silver suitable as currency, was the fact that these metals were relatively rare. There was a steady, but slowly increasing influx of gold and silver, while they were mined from the earth. Mining required a lot of time, effort and cost. If gold and silver were abundant, and it would be easy to get them, then everyone would be engaged in mining, and they would cease to be valuable, respectively, they would cease to be suitable as money.
Although bitcoin mining and gold mining are very different in practice, the principle underlying them is the same, and therefore the generation of bitcoins have become similarly called “bitcoin mining”. Like gold, anyone can mine bitcoin with the appropriate resources. If you wanted to mine gold these days, you could do it, but remember that much of the gold near the surface of the earth has long been mined. Thus, you would need a bit of luck plus a great geological and logistic experience - as a result, most people are consumers of gold, not miners!
The way that bitcoin mining is done is that the bitcoin network introduces relatively small amounts of bitcoins into the economy at regular intervals. The bitcoin protocol sets a math problem that is built in such a way that it can be solved in about ten minutes. When the problem is solved, a person who owns a computer, who has solved the problem, is given a specified number of bitcoins. At the very beginning, perhaps, only one personal laptop solved these problems. Therefore, the task was relatively easy, so that the available laptop could solve it within ten minutes before repeating the process again. At this point, when bitcoin was in infancy and no one else used it, one bitcoin was not worth anything. Therefore, such an exercise in mining, which required small amounts of electricity,extracted some bitcoins that were worthless.
However, over time, two, then three, then thousands of laptops and home computers tried to solve a problem that was updated every ten minutes. With a thousand computers that tried to solve the problem, the network adjusted the level of complexity so that it became a thousand times higher than at the beginning. Therefore, each participant had about one chance in a thousand to solve the problem and achieve some kind of reward.
I don’t know exactly how much bitcoin was worth at this point in the story, but it began to cost something, even if it was a very small amount. Using a computer twenty-four hours a day is inexpensive in normal conditions when you just surf the Internet, but if you use a computer twenty-four hours a day to solve a mathematical problem, you will see that the processor is used almost 100%. This process increases energy consumption and increases the cost of electricity. People began to calculate the cost of using machines for mining Bitcoin and relate it to the statistical probability of solving a problem over a selected period of time. And from that time on, Bitcoin began to possess some value, even if only because of its rarity, and not because of its usefulness for such a small circle of people.
Then people realized that rather than using an old laptop or PC for computing, it would be more efficient to design computers designed specifically for bitcoin mining, and nothing more. People began to launch not one, not two, but entire computer farms in their apartments and residential premises. These computers mined bitcoins and consumed electricity. Some clever people later realized that GPUs (graphics processors) on video cards were much more productive for solving a specific type of problem proposed in Bitcoin mining, and wrote programs to take advantage of video cards and mine Bitcoins faster.
As you can see, not only has the number of people mining bitcoin increased, but also the number of machines used by these people and the power of these machines. The task for solving every ten minutes was now hundreds of thousands or maybe millions of times more difficult, and a miner with a simple laptop would have very little chance of getting anything.
After the GP mining phase, as it was called, equipment manufacturers began to develop ultra-fast motherboards specifically designed for mining Bitcoin, making GP mining slow and outdated. Today, bitcoin mining is a full-fledged industry with companies investing millions of dollars in bitcoin mining equipment. Today, like using a small paddle for gold mining, you cannot expect to start mining Bitcoin on a home computer and expect to receive money, because this will require extensive resources. Several bitcoin production farms were launched in Iceland, where geothermal electricity provides a cheap source of energy, which is combined with minimum cooling requirements for servers due to low temperatures.
So be it, if you cannot afford the gold mine, you can probably buy some share in it. In a similar way, companies that provide what is called the mining pool are now working. It works in such a way that you join the association of thousands of users who use home computers for bitcoin mining, and are guaranteed to receive a small percentage corresponding to the contribution of your personal computer to the total production - however, do not expect to get rich!
I talked a lot about how bitcoin mining works, and about the history of bitcoin mining, but the bitcoin mining process has two important roles in the bitcoin network in addition to generating new bitcoins for miners. First, in addition to solving mathematical problems, Bitcoin miners also process transactions. In the third chapter, I gave an example of sending 50 XBT to my friend Joe, and this transaction was sent to the Bitcoin network. The data of this transaction reached the set of miners actively mining Bitcoin, and when one of them successfully solved the math problem, he also processed this transaction, along with all the other Bitcoin transactions in the last ten minutes, and included them in the blockchain (Bitcoin account). In other words, these miners perform the necessary function in the bitcoin network: in addition to introducing money into the economy,they provide payment processing functions that allow Bitcoin transactions to work.
There is a third key role played by the mining process. The more miners in the bitcoin network, the more difficult the mathematical task becomes. The more complex the task, the more secure and resistant to fraudulent transactions the network becomes. We will not discuss this moment so far, but will return to it later in this book.
Now that you have an elementary understanding of some of the principles underlying Bitcoin, it's time to consider the advantages of Bitcoin over other types of money and understand how you could use it. Bitcoin is more profitable than ordinary currency in almost all circumstances when an electronic transaction is possible. However, before considering its advantages, it is worth noting the available alternatives. When we talk about alternatives, we not only compare bitcoin with other currencies, such as the dollar, pound or euro, but we also need to consider different types of transactions. The way in which we use money strongly depends on the amounts used, the type of goods and services we buy, and the relative position of participants.
In the simplest case, we use the physical transfer of cash when banknotes or coins pass from hand to hand. Cash transfer works best for amounts from about five cents to thousands of dollars. Obviously, it is possible to transfer large sums, but in most cases people find it more convenient to use other payment methods if the amount exceeds a thousand dollars. As for smaller (than the lower limit) amounts, here we are limited to the smallest denomination of the currency. Cash transfer is of limited use, since both participants must be in the same place.
Bank checks are often used to transfer large amounts between individuals. A bank check usually costs about five dollars, so it's not very economical to use them for amounts less than five hundred dollars. In practice, in most cases, the amount of a bank check is not limited, but it is a rather inconvenient process, requiring both participants to appear in a bank branch, so usually the use of bank checks for transactions is limited to one country. Participants must also meet in person to submit a check, or wait several days until the check is delivered by mail.
For merchants, electronic payments or credit cards are convenient means. This is a relatively expensive option for merchants, as they have to pay in order to create a trading channel with the bank, and also pay the bank a few percent of the amount of each transaction as transaction fees. Moreover, in the case of a refund, when the transaction turns out to be fraudulent, the merchant risks and he must return the money. This is especially true for online merchants, as they only get credit card information, but they don’t see the cards themselves. The possibilities of electronic payments and credit cards are usually limited to ten to ten thousand dollars.
International SWIFT transfers are the main method of transferring money between countries. SWIFT transfers are usually uneconomical for amounts less than a thousand dollars, due to the high fees charged by banks. SWIFT transfers are a very slow form of transaction: the recipient receives payment after a few days. Errors also occur during the translation process, resulting in even greater delays.
I have described some of the most common methods of transferring money between people, but, of course, this is not an exhaustive list. There are also large translation firms like Western Union, as well as a large number of specialized international transfer firms that can send small amounts of money faster and more economically than SWIFT or Western Union. Another group of companies includes PayPal and similar companies that act as a processor and insurer of payments between merchants and banks. And, again, that's not all. You have probably already begun to understand that our understanding of a transaction depends heavily on what we are trying to do and that we have a large variety of loosely coupled systems that have advantages and disadvantages depending on the circumstances.
Let's go back to bitcoin. Bitcoin allows me to send any amount of money anywhere in the world instantly and for free . What other transaction method has such wide coverage?
Let's continue. Bitcoin allows merchants to receive payments without the risk of return. In formulating it differently, if a merchant received a payment in bitcoins, there is no risk that the bank or a third party may later declare this payment fraudulent; Bitcoin payments are final. Of course, sellers and buyers can pay third parties for escrow services if they need it. It is also a boon to shoppers, particularly those who shop online. If you have ever made an online purchase with a credit card, you have to be upset when your card is not accepted, because you are traveling at this point, or making a purchase that the seller considers risky. For example, if you buy equipment for several thousand dollars, the seller may ask you to confirm your identity and address. This is inconvenient and frustrating for both the seller and the buyer, leading to undesirable delays and efforts to process the transaction on both sides. With Bitcoin, transactions are instantaneous, free of charge and pose no risk to the seller.
The benefits are even greater if you are a trader who often deals with international buyers, for example in the tourism industry. Imagine that you are renting a yacht. The buyer orders the boat a week before the holidays. Instead of worrying about transfer fees, getting acquainted with foreign currency and waiting a few days to get the money, you can send a deposit in bitcoins - from anywhere, for free and instantly, in a currency with which both the buyer and the seller are familiar. If renting a yacht turns out to be a secret engagement gift for the bride, it will also not be visible on credit card reports.
Another great advantage of Bitcoin is that a Bitcoin transaction does not require either party to provide important information to the other party. This is exactly the opposite of how credit cards or electronic payments work. Every time you make a purchase in a store using a credit card or electronic payment, you must transfer your card details and a pin code or signature. It is interesting to think about how important it seems to us to hide the pin-code from other people, and at the same time, just as we are ready to enter it into a machine belonging to a complete stranger. Pin-theft devices are known in Australia, but they are much more common in other parts of the world, this is especially true for international travelers. Using bitcoin completely removes this risk. You can shop anywhere in the world, pay any stranger, without worrying about the fact that your data can then be used for fraudulent purposes.
Another example of the circumstances in which bitcoin has significant advantages over other transaction methods is the payment of small amounts. A child may want to go to the store and buy there for ten cents a chocolate or lollipop, or the seller may want to sell a ring tone for a mobile phone for fifty cents online. Without Bitcoin, such small purchases can only be made for cash, since for most other funds it is required that the amount of the payment should cover the transaction fees. Bitcoin provides what is now called “micropayments,” in the case of such small amounts, or even smaller amounts, less than one cent. Moreover, bitcoin is not a credit line, it is the digital equivalent of cash, so you do not need to be an adult to use it.
What about the case of a traveler who urgently needs to send a hundred dollars to his mother in his country? SWIFT transfer will be expensive for both parties and will take several days. Service like Western Union will be faster, but even more expensive. Bitcoin works instantly and for free.
Bitcoin can be sent between participants anonymously. There are no restrictions on this anonymity, we will look at it in more detail in the following chapters, and now it’s enough to say that when I carry out a bitcoin transaction, I don’t need to worry about who will make the payment: the bank or the credit card company that keep the entire history of my purchases. I do not need to reveal my identity to the seller, and there are many valid and reasonable reasons why I would prefer to remain anonymous.
Another great advantage of Bitcoin is that its release is controlled. As we briefly reviewed in the previous chapter, bitcoin is generated through the mining process, and the bitcoin generation rate is controlled by the protocol itself. We will look at this in more detail later, but it can be said that the release of bitcoin is predictable, controlled, and inaccessible for manipulation by an individual, organization or government. We have observed many times throughout history, including recent history, examples of how governments negatively affect the issue of money, generating more money for the sake of their own immediate economic interests. These interests often represent a complete contrast with the interests of the people who hold the currency. We have seen how this can lead to an inflationary spiral that can destroy the entire economy. Bitcoin cannot be the subject of this kind of manipulation, since the release is controlled by the protocol itself, and its volume is known in advance by anyone who uses bitcoin.
Earlier, we said that bitcoin has similarities with cash, but cash is limited when it comes to protection against accidental loss or theft. Bitcoin is also not immune to losses of this kind, but it has many properties that allow people to protect their money from loss or theft. This makes it a much safer option to carry in the back pocket than a wallet full of cash.
Common currency is not intended for e-era. This is a money system that has been used for hundreds, if not thousands, of years, long before the invention of electricity, not to mention the development of computers and the Internet. It has been used since the time when the trade was carried out face to face, when there was not even the thought that it was possible to send a song from one end of the world to another for a small fee between the parties who had never even talked to each other. During the twentieth century, financial institutions adapted their ancient systems to the electronic era and developed new systems that met the requirements of modernity. During the service of these systems, as the requirements of e-commerce expanded, new systems were built on their basis, performing tasks for which they were not originally intended. As a result, we have creaking working banking system, which is not designed for a huge variety of electronic transactions carried out in the world today, and is completely dependent on financial institutions, which derive huge profits from this dependence.
From the very beginning, bitcoin was designed for electronic transactions, and this is his forte. It allows instant electronic transactions from anywhere in the world, for any amount, without having to trust the other party or any dependence on a third party. When digital currencies reach critical mass, our doubts today will seem silly.
At its core, bitcoin is an open protocol. Speaking of "protocol", I mean that bitcoin is a set of rules that bitcoin programs must comply with. By “open,” I mean that a protocol, or a set of rules, is publicly available, and anyone can check them. This protocol allows Bitcoin programs (which we usually call Bitcoin clients) to communicate with each other over the Internet in a standardized way.
Then the first question will be if bitcoin is an open protocol, or a set of rules that keeps people from writing programs that violate the rules. The answer is nothing. Anyone can write a program that uses the bitcoin protocol and communicates with other bitcoin programs via the Internet and tries to “break the rules” in its favor, however, clients that do not comply with the protocol are simply ignored by other clients.
As an analogy, imagine chess players by mail when players are in different places and their moves are sent in letters. Both players know what the entire board looks like, and any one of them can walk as he pleases if his move complies with the chess rules. Otherwise, the other player ignores or rejects this move. The same principle underlies the bitcoin: any of the “players” (bitcoin clients) knows exactly what the “board” (blockchain) looks like, and can independently verify from other sources that any “move” of another (transaction) is correct.
If we want to understand Bitcoin at a deeper level than the analogy, we must understand the idea of asymmetric encryption (also known as public key encryption). Asymmetric encryption is a key element of Bitcoin, and without it, Bitcoin could not exist. The idea of asymmetric encryption is not new, and in fact it is an integral part of the security of many software systems. We use asymmetric encryption every time we visit a secure (SSL) site, for example, an Internet bank site.
Before I explain what asymmetric encryption is, let's imagine such a task. Let's say Alice in Australia wants to send a letter to Bob in England. The content of the letter is a big secret. How can Alice send a letter to Bob without the risk that someone will read this letter on the way? Without asymmetric cryptography, this can only be achieved in the only way that Alice and Bob initially understand how to encode a letter. Then the letter will be encrypted, and Bob will know how to decrypt it when he receives it. But what if Alice and Bob don't have a prearranged key for the cipher; what if Bob had never met Alice before? In such circumstances, without asymmetric encryption, Alice cannot safely send a letter to Bob.
Thus, this leads us to asymmetric cryptography and the way it solves this problem. Some time ago, several talented mathematicians developed a way with which you can generate key pairs mathematically related to each other. In this context, you can think of a key as a very large number — a number with several hundred digits. [6] . These keys are called "public key" and "private key", or together - asymmetric keys. It turns out that these keys have several very useful properties!
Using the public key, you can encrypt the message in such a way that it will be possible to decrypt it only with the private key. Thus, Bob can now generate a pair of keys and transmit his public key to the world, since [7] get his private secret key. If Alice wants to send a secure message to Bob, she simply has to encrypt the contents of her letter with Bob’s public key using a known algorithm, and Bob can decrypt the message with her private key, which he does not reveal to anyone else.
You use asymmetric cryptography technology every day when you use Wi-Fi, Bluetooth, or secure websites where data is encrypted to prevent what is called a man-in-the-middle attack. In other words, asymmetric cryptography is used to prevent anyone else from intercepting your conversation, letter, or transaction.
So now we know how Alice can safely send a letter to Bob, but when Bob gets a letter, how can he be sure that Alice sent the letter and not someone else? It turns out that asymmetric keys can solve this problem. Alice also generates a pair of keys: public and private key. Like Bob, Alice reveals her public key to the world. Alice can digitally sign the contents of the letter using her private key. Then, using Alice’s public key, Bob can determine that the letter was indeed signed by Alice, since no one else can sign the letter without access to Alice’s private key. Thus, only Bob can read Alice’s letter, and Bob can make sure that it was Alice who wrote the letter.
This is a very useful and powerful idea - it still impresses me today, despite its everyday use. You can evaluate its usefulness for military communications, and, in fact, for many years the United States tried to stop the export of programs that use strong asymmetric cryptography.
 Fig. 2. Asymmetric encryption. Alice sends a signed encrypted message to Bob.
Fig. 2. Asymmetric encryption. Alice sends a signed encrypted message to Bob.
Now that we understand how asymmetric cryptography works, how does this apply to bitcoin? Remember, in Chapter Three, we made an analogy and said that in some respects bitcoin works on the principle of a checkbook?We said that one user sent bitcoins to the bitcoin address of another user, and that the transaction was signed by the sender of the transaction. This is the point where everything starts to connect: the fact is that the bitcoin address is a derivative of the public key.
Let's look at our original checkbook example in more detail, because now we understand the idea of a public key. I have 50 bitcoins on my mobile phone, and I would like to send them to my friend Jo's mobile phone. First, Joe presses a button on his phone to generate a new bitcoin address. Although, in fact, it creates a pair of asymmetric keys. The private key is stored on Jo's phone, and the derivative of the public key (Bitcoin address) is displayed on the screen and then sent to me. Using Joe’s bitcoin address, I start a transaction on my phone, indicating the amount I want to send to him. Then I sign this transaction with a digital signature using my private key and send the transaction to the Internet. Remember, we said that writing a check is the same as writing a letter to the bank,allowing the bank to allocate funds from my account to the specified person. In the case of bitcoin, the transaction is, in effect, a public announcement of the transfer of control over the XBT 50s, registered to my address, to the bitcoin address I specify. Only my private key allows me to allow bitcoin transfers to Joe's address, and I give this permission when I sign the transaction with a digital signature.
When a transaction is sent, Joe can confirm in the bitcoin network that he has the right to spend these bitcoins - the transaction is final. Of course, despite all these technical steps, all this happens automatically, behind the scenes, by pressing a few buttons on the phone.
 Fig. 3. Adam sends Joe bitcoins through the bitcoin network
Fig. 3. Adam sends Joe bitcoins through the bitcoin network
In Chapter Four, we looked at how bitcoins are generated and introduced into the economy. We explained that bitcoins are generated approximately every ten minutes in the course of solving a mathematical problem. In this chapter, we will take a closer look at how this works. To understand bitcoin mining, we need to get acquainted with another idea from computer science: this is hashing, or a cryptographic hash.
Hashing is a very interesting concept, which, like asymmetric cryptography, is one of the key ideas in the field of software security. As we did earlier, let's start with the presentation of the task. If I have a computer system, how could I safely store each user's password in such a way that if the system is compromised, then user passwords will not? In other words, for obvious reasons, it is a bad idea to store a database containing thousands or millions of user passwords.
The solution to this problem includes a cryptographic hash. The hashing process gets something to enter, such as a password, and passes this input through an algorithm that outputs a large number, called a "hash." The hash defines two distinct features. First, for the same input data, the hashing process always returns the same result. For example, if you enter a password that is passed through a hashing algorithm that generates a specific number, the same number will be generated each time. Secondly, hashing is a one-way process. It is impossible to take the value of the hash and, with the help of reverse engineering, reveal what was at the input. These two properties determine the cryptographic hash. If the process were reversible, it would not be called hashing, but good old encryption / decryption,and this is a completely different topic.
It turns out that the process of hashing values has many useful features applied to computer science. One of the tasks we suggested above was the task of storing user passwords securely in the system. Instead of storing the user's password, we first hash his password [8] and store the hash value. When the user tries to log in next time with a password, we don’t need to know what his password was, we only need to know that the password is the same as what was entered last time. In other words, if the hash of the entered password matches the hash stored in the database, we know that the user has entered the correct password - although we do not know and do not want to know what it was for the password. If our system is later compromised, the attacker will only receive a list of password hashes that are irreversible and have no value.
If you are like me, this process will seem fascinating to you, but you will probably ask yourself - if the passwords are hashed, how can it be that if you forget the password for a particular system, then the company can send it to you by email. This is a very good question. This means that passwords are not hashed, and this system is extremely insecure. Sadly, many systems today permit this. This is one of the reasons why you need to use different passwords for each of the systems to which you have access. When it is found in the news that the system has been “hacked” and thousands of passwords have been compromised, this happens because system designers could not ensure the security of user passwords using a hashing technique that is generally considered the best approach.
For the sake of interest, we note that if you forget the password to the system, which properly hashes user passwords, the correct approach is to reset the password by the system when the password is replaced with a temporary value, which allows you to change it to something else when log in. However, it should be noted that such an approach does not guarantee that the system actually hashes the passwords.
Now, how does this all apply to bitcoin mining? Well, we said that reverse hash development is not possible. Technically speaking, theoretically, it is possible through what is called a brute-force attack — going through all the possible input combinations until the same hash is obtained. However, in practice, the number of combinations is astronomically large, which makes such an attack impossible for practical purposes. It should also be noted that different input values may result in the same hash value, this phenomenon is called collision and it happens very rarely if you use the correct hashing algorithm, so for our discussion here it does not matter.
Now let's assume that there are only a million possible hash values, a number between zero and one million. In reality, of course, we know that much more than a million hash values are possible, but let's continue with a million to illustrate my point. Thus, the chances of correctly guessing the correct input for a given hash will be one in a million. Having a sufficient number of attempts and a sufficient time, in the end I will find the initial data, which, after hashing, will give the value that I am trying to find.
Let's assume that the trial and error process takes twenty-four hours to find a match (a modern home computer will do a million iterations in less than a second, but let's leave twenty-four hours for our example). Remembering that in our example we said that all the hash values are numbers between zero and one million, let's assume that instead of finding input data that will give a certain hash value, we would like to find input data that hash numbers give a smaller or equal to 10. That is, we want to find any input that will result in a hash value of 1, 2, 3, 4, 5, 6, 7, 8, 9, or 10. In this case, it is ten times more likely that what we get the hash value will do, so our computer will find a match on average ten times faster - now s take approximately 2.4 hours instead of 24 hours.
If I wanted to create a task that would be solved faster, say, in 10 minutes, I would raise the limit to any hash between 1 and 150. The task is now 150 times simpler than in the first example, and a quick calculation will show that such The problem should be solved by our (slow) computer in about 10 minutes. What happens if the second, equally powerful computer connects to attempts to find a solution to the problem? Now it can be solved twice as fast. If I want the solution to still take 10 minutes, I will have to make the task twice as difficult, setting the condition that the hash value should now be less than 75, not 150. As more and more computers are connected to the problem , and they start solving the problem more efficiently; we make it more complex by setting a smaller range of acceptable hash values.
And, if you still have not guessed, this is the task that the bitcoin network offers to the bitcoin miners. The difference, of course, is that there are far more than a million combinations, the numbers are so large that you can’t call them that easily. All the bitcoin miners in the world, while I am writing this text, collectively process approximately 350,000,000,000,000 input values per second in an attempt to find the same value that hash falls within a certain range of hash values.
The bitcoin network regularly assesses the complexity of the task, and if the task is solved faster or slower than the set interval of 10 minutes, then the task is adjusted accordingly by expanding or reducing the range of acceptable hash values. Of all the computers in the world that are trying to solve a problem, only the first one who decides receives bitcoins "as a reward", and the process begins anew. The next question is then: how does the rest of the bitcoin network confirm that the task was solved, and how are bitcoins generated in this process? The first question is simple. The computer that solved the problem announces this bitcoin network solution, and other computers check the solution. Although reverse engineering the input value for a given range of hash values is a slow process of trial and error, but once a solution is found, it is easy to check.simply by passing the proposed solution through a hashing algorithm and making sure that the resulting hash value falls within the specified range. Then, mined bitcoins are issued to a specific miner address, introducing new bitcoins into the economy. Just as the monarchs in the olden days issued tally for taxes that would never be collected, and banks issued notes for funds that they did not have, the bitcoin network slowly generates new bitcoins. The key difference between bitcoin and other systems, however, is that in all previous systems, the frequency of currency generation was set at the whim of the monarch, the government, the bank, or, in recent times, controlled by the government of the central bank. The frequency of bitcoin generation is set algorithmically, and cannot be the subject of manipulation of market participants - it is predetermined.The frequency of generation is determined by the bitcoin protocol, and decreases with time, until eventually the bitcoins are no longer generated at all. For any date in the past or future, you can calculate the approximate number of bitcoins in circulation.

Fig. 4.
Let us briefly take a pause in the previous direction of thought, and turn to decentralization. Decentralization is a relatively recent concept in computer knowledge, which finds more and more applications over the past decade. One of the first examples of decentralization was the peering (P2P) file exchange. Over the past years, there have been many implementations of it, the most common of which is now the network of torrents. If you are unfamiliar with torrents, let me give a brief introduction. The traditional method of downloading files from the Internet is quite simple. One computer (server) stores the file you need, and the other computer (client) requests this file from the server, and the server sends the file to the client. This model still prevails today, and most of the time you spend on the Internet works as described. By the wayThis model is called client-server. However, she has some limitations. One of these limitations is that the file cannot be uploaded faster than the server allows. This is usually not a problem, but what if there are a million people who want to download the same file from the server? The bandwidth of the server is limited, so that this limited channel must be divided between all people downloading the file. By the way, a separate server can not support a million connections, so you need a farm of servers that contain the file, which will lead to high costs for the owner of the servers, or low speed for clients downloading the file.but what if there are a million people who want to download the same file from the server? The bandwidth of the server is limited, so that this limited channel must be divided between all people downloading the file. By the way, a separate server can not support a million connections, so you need a farm of servers that contain the file, which will lead to high costs for the owner of the servers, or low speed for clients downloading the file.but what if there are a million people who want to download the same file from the server? The bandwidth of the server is limited, so that this limited channel must be divided between all people downloading the file. By the way, a separate server can not support a million connections, so you need a farm of servers that contain the file, which will lead to high costs for the owner of the servers, or low speed for clients downloading the file.which will lead to high costs for the owner of the servers, or a small speed for clients downloading the file.which will lead to high costs for the owner of the servers, or a small speed for clients downloading the file.
A distributed peering network can help here. It works like this: let's say I have a file that I want to make available to other people. Using a P2P program, this file is divided into hundreds of parts (the exact size and number of parts depends on many factors). Now people can download a file from my computer one piece at a time, in any order. The bandwidth on my part is not large, so initially it will be rather slow for those few people who try to download this file from my computer. If someone else has received one of the file parts from me, other people can now download this part either from me or from another network member. Over time, more and more people download some parts of the file from my computer, and others from other people's computers, untiluntil the original file is distributed among the computers of many people. If someone comes in and wants to download this file, the program will simultaneously download the file from many different computers, perhaps never connecting to my computer where the file was originally located - in fact, at this point I can turn off my computer altogether , and provided that there is a complete copy of the file on the Internet, people will continue to download it freely. This system proved to be very successful for files in high demand. Recently, we can see that the decentralized approach is used in software products for which it was not originally intended, and the most recent example is the blockchain.If someone comes in and wants to download this file, the program will simultaneously download the file from many different computers, perhaps never connecting to my computer where the file was originally located - in fact, at this point I can turn off my computer altogether , and provided that there is a complete copy of the file on the Internet, people will continue to download it freely. This system proved to be very successful for files in high demand. Recently, we can see that the decentralized approach is used in software products for which it was not originally intended, and the most recent example is the blockchain.If someone comes in and wants to download this file, the program will simultaneously download the file from many different computers, perhaps never connecting to my computer where the file was originally located - in fact, at this point I can turn off my computer altogether , and provided that there is a complete copy of the file on the Internet, people will continue to download it freely. This system proved to be very successful for files in high demand. Recently, we can see that the decentralized approach is used in software products for which it was not originally intended, and the most recent example is the blockchain.where the file was originally located - in essence, at this moment I can turn off my computer altogether, and provided that there is a complete copy of the file on the Internet, people will continue to download it freely. This system proved to be very successful for files in high demand. Recently, we can see that the decentralized approach is used in software products for which it was not originally intended, and the most recent example is the blockchain.where the file was originally located - in essence, at this moment I can turn off my computer altogether, and provided that there is a complete copy of the file on the Internet, people will continue to download it freely. This system proved to be very successful for files in high demand. Recently, we can see that the decentralized approach is used in software products for which it was not originally intended, and the most recent example is the blockchain.that the decentralized approach is used in software products for which it was not originally intended, and the most recent example is the blockchain.that the decentralized approach is used in software products for which it was not originally intended, and the most recent example is the blockchain.
We reviewed and discussed the three basic computer science ideas underlying bitcoin: asymmetric cryptography, cryptographic hash, and peer-to-peer networks. Although these ideas are interesting, they are not revolutionary in the context of Bitcoin. All these things have been used in various ways for a long time. However, what binds them together is a fundamentally new idea, which is the basis of Bitcoin. This idea is known as blockchain.
Blockchain is a decentralized open ledger: let's try to figure it out. In the case of a regular business, or better said, a bank, a ledger is a record set that contains details of user transactions and account balances. In modern banks, these records are stored in large software systems. As you can probably guess, these are large, resilient systems that must be supported by millions of users who perform millions of transactions daily. You may already be familiar with some of the symptoms of the difficulties experienced by banks with reliable management of such large data sets. For example, you could not download the transaction history from an Internet portal of your bank before a certain period in the past. Or perhaps you noticed that some transactions did not immediately appear in the history,until they are processed at night. All these and other similar oddities are the trade-offs necessary for banks to manage these (often ancient) systems containing huge amounts of data.
We said that the blockchain is a decentralized open ledger. We know what a ledger is: a set of records containing details of user transactions and account balances. Now let's explain what we mean by "decentralized" and "open." Unlike a bank, this ledger is not stored on a central server controlled by any person or organization. Blockchain-ledger is available publicly and is stored locally by a multitude of clients, it can be freely downloaded from the Internet. It may be hard to believe, but you got it right: the whole history of any Bitcoin transactions made by anyone around the world since the very beginning of Bitcoin (January 12, 2009) is publicly available for viewing to any person, besides, on most computers or Notebooks, where there are bitcoin programs, are stored copies of this ledger.You probably have a lot of questions, such as how this is possible, or why this is generally a good idea. Let's start with how this is possible. Of course, this is a large amount of data, but not impossibly large. Financial records take up very little space, and looking objectively, all records of bitcoin transactions from the very beginning at the time of this writing take up the same amount of space as a dozen, or so, movies in HD quality. If you download a bitcoin client that stores a local copy of the blockchain, it will take a long time to start the first time you start it, because it downloads a full copy of the blockchain. Another thing is that storing a full copy of the blockchain on all computers in the world is not absolutely necessary. This is definitely not possible on mobile devices, and now in the trend of bitcoin clients,which store only important things locally, not the whole blockchain. Nevertheless, this illustrates my assertion that the blockchain is publicly available to the whole world, and in fact there are many sites that make it easier to navigate through the history of all Bitcoin transactions made by anyone and anytime.
You may be somewhat disturbed by the moment that if you use bitcoin, the entire history of the transactions you have ever made will be publicly available. This is only partially true, and we will discuss this point later in the chapter on anonymity. A public ledger contains only bitcoin addresses and amounts. It does not contain any personal or identifiable information. In other words, if I send 50 bitcoins from address A to my friend Joe with address B, the whole world sees that 50 bitcoins are sent from address A to address B, but nobody can determine that address A belongs to me and address B belongs to Joe. So when I look at the blockchain, all I see is the balances of addresses and transactions from one address to another - none of this information compromises the confidentiality of the people carrying out these transactions.
Another point that needs to be understood, and which we have not yet discussed, is that, unlike email, where you can only have one address, or at least a small number of addresses, the number of Bitcoin addresses that can be in person, not limited. In fact, this is encouraged, and most Bitcoin clients are configured by default so that each transaction uses the new address. Let's look again at the example of sending 50 bitcoins to my friend Joe, now we already know a little more. When I ask Joe to tell me his bitcoin address, he, as a rule, does not give me an address containing the full amount of his wealth, but creates an absolutely new address with no bitcoins at all, and I send 50 bitcoins to this new address.Bitcoin programs do not require you to manage the balance of each address individually; they can show you the total balance of all addresses that you have ever created. If you look at my case, I hardly have an address containing the exact amount of money I want to send to Joe. For example, I may have a bitcoin address A, which has 30 bitcoins, and a bitcoin address B, with 35 bitcoins. In our example, the program will automatically generate a transaction that will take 30 bitcoins from address A, then 20 from address B, send these 50 bitcoins to Joe's address, and also send the remaining 15 bitcoins to the new address B, which she automatically generated for me. Both Joe and I may have hundreds or thousands of addresses containing small amounts of money, which together make up our complete bitcoin state.None of us can see the addresses of the other, except those used in the transaction.
The exception to this rule is the case when I receive one transaction for a large amount of money, say, a million dollars in bitcoins. If after that I want to spend 1 bitcoin from this address, the recipient will be able to see that I have about a million dollars in Bitcoins at my disposal, which I would not want to disclose. Suffice it to say that for the lucky ones who find themselves in this position, there are techniques to hide this wealth, throwing money at many addresses - modern programs make this process trivial.
Now that we know what a blockchain is, how does it actually work? The question is perhaps worth formulating as follows: how can we ensure a consistent record of transactions in a decentralized environment? The first thing to understand about the blockchain is that it is called a blockchain because it consists of a chain of consecutive blocks. A block is a group of transactions. Guess how often blocks are generated? About once every 10 minutes. Probably, you started to understand that there is a connection between the blockchain and bitcoin mining, and if you assumed that, you are right.
Remember, in Chapter Four we said that bitcoin mining, in addition to introducing bitcoins into the economy, also has two other goals. It provides payment processing and network security. Let's now look at how these tasks are performed during the bitcoin mining process. We mentioned above that when a transaction is initiated, it is sent to the Bitcoin network. What does this really mean? Bitcoin clients (i.e. programs) try to connect with many other bitcoin clients called peers. Usually each individual client is connected to 10-20 other peers. Some of these peers are regular transaction users, and a small number of these peers may be miners. When a bitcoin client receives information about a bitcoin transaction, it is transmitted from the client to the client untiluntil after a short period of time will not be received by one or several bitcoin miners.
Bitcoin miners do one more thing besides solving the hash problem and introducing bitcoins into the economy: they provide an important blockchain creation function, one block at a time. When a bitcoin miner receives information about a transaction, its authenticity is first checked, and then it is recorded in a block locally, on a bitcoin miner computer. If the bitcoin miner has successfully solved the problem, the solution of the problem is included in the block as part of it, along with all transactions created in the past 10 minutes. Then the block is closed and distributed over the Internet, and the process begins anew. Anyone else on the network can independently verify that the transactions in the block are genuine and that the solution to the hash problem, also known as “proof of work,” is true. Any subsequent miners who have solved the problem are ignored, their blocks no longer fit, and the process begins anew.Thus, a blockchain is a sequence of blocks containing transactions over a given ten-minute period. Each block is mathematically connected with the previous block, so you can trivially (for the computer!) Check the entire blockchain for authenticity without analyzing individual transactions.
And that brings us to the third goal bitcoin miners reach: network security. The actions taken to solve a cryptographic hash problem serve not only the interests of the miner, they are also needed to protect against dishonest miners who spend money twice, which is called "double waste". If you take an earlier example where I send 50 bitcoins to Joe, have Joe send me the book I bought from him instead (at today's prices it would be a rather expensive book). At the same time, what if I try to send the same 50 bitcoins to another person, before the first transaction has become processed and verified? Assuming that I have already received the goods from Joe, it will be problematic if the bitcoin network somehow accepts my payment to another participant and later rejects the initial payment that I sent to Joe.Bitcoin's decentralized mining solves this problem.
When I send a transaction for Joe to the bitcoin network, Joe will be able to see it almost instantly (usually after a few seconds). At this time, the transaction is visible, but not yet included in the block by the miner. If it is a transaction with a small amount, or a transaction between participants who trust each other, the visibility of the transaction on the network will usually be considered acceptable, however, with some effort on my part, it is still possible to spend money twice by sending another transaction to the network that uses the same means — but for transactions with a small amount, the effort required will probably not be worth the time spent (besides, of course, there is also the risk of being caught). After about 10 minutes, we can expect that my transaction will now officially be included in the bitcoin miner in the last blockchain block.At this point, the transaction has "one confirmation". Now, if you take into account that there are thousands of special Bitcoin-producing computers in the world, the likelihood that I will be able to deceive Joe and spend my money twice and successfully get the unit that will reject the transaction for Joe is very small. For transactions with medium or large amounts, it is usually considered prudent to wait for 3-6 confirmations, or, in other words, to wait for 3-6 consecutive blocks (from 30 to 60 minutes) to be obtained to be absolutely sure of the transaction. To successfully carry out double waste, in this case it will be necessary to successfully extract 6 blocks in a row that reject the transaction. And to achieve this, you need to control about 50% of the total computing power of the Bitcoin network. As you can see,this makes the double waste attempt extremely difficult and expensive, which primarily outweighs, in general, any benefits of double waste. You can also see that as the Bitcoin network grows, the number of miners increases and the difficulty of the hash problem increases, double waste becomes even more difficult for a dishonest miner. This is how bitcoin miners ensure network security.
In summary, bitcoin mining provides three things: transaction processing, network security, and the entry of bitcoins into the economy. This is an elegant system.
It is time to point out the fact that the miner has a choice whether to include the transaction in the block or not. The miner can reject all transactions if he wants, and just solve the hash problem. This is called “empty block mining” and happens from time to time. Then the question is, why should Miner even bother to include transactions in the block? There are several reasons. First, compared with the work that the miner does when trying to solve the hash problem, the inclusion of transactions in the block is a trivial operation that requires almost nothing from his computer. Secondly, transactions are included in the blockchain in the interests of the bitcoin community. If miners do not include transactions in the blockchain, bitcoin will not work, and if it does not work, then bitcoins will not cost anything. If bitcoin doesn't cost anything,then the miners will spend all their efforts on getting something that costs nothing. You may argue that it is good for the community that miners include transactions in the block, but for an individual miner it is unprofitable to spend resources on processing transactions. This is partly true, but, as I noted at the beginning of the paragraph, the necessary effort is negligible. There is also a third point. Miners can not take a commission for the inclusion of a transaction in the block, but the people carrying out the transaction may voluntarily offer a commission. Miners can then reject transactions that do not include a commission at all, or reject transactions with a commission below a certain value. What is the usual commission today? In most cases, it is zero. In today's economy, the miner’s stimulus is primarily Bitcoin, which he receives for a successfully mined block.Transactions are included in the block on the goodwill of the miners in the interests of the growth of Bitcoin-economy and the growth of Bitcoin. In some cases, Bitcoin clients automatically include a small commission (no more than a few cents) to make sure that the transactions will not be rejected by the miners and are more likely to be included in the next mined block.
Over time, the number of bitcoins received for a successfully mined block will gradually decrease until, around the year 2140, the reward for mining the block is zero. It is expected that over this long period of time, until the block reward as a stimulus for mining Bitcoin gradually decreases, this incentive will gradually be partially replaced and, eventually, will be superseded by the incentive in the form of transaction fees.
Due to the fact that the bitcoin economy is an open market, and that transaction fees are voluntary, the value of the commission will always be determined by supply and demand, which will create a competitive market with low transaction fees.
TL; DR: well-known slang term meaning “too long; do not read". This is a short summary at the end of a long text containing its abbreviated version. However, unfortunately, if you opened this chapter without reading the previous chapters of the second part, where the key principles of computer science underlying the bitcoin are described in general terms, then it will be difficult for you to understand this chapter, and in your understanding of bitcoin you will remain at the level of comparisons by analogy. If you read Part II, then this chapter is needed to bring all these ideas together into a clear understanding of Bitcoin.
First, we learned that asymmetric cryptography is the technology underlying private and public keys; using this relationship, we can mathematically check the validity of a bitcoin transaction signed with the sender's private key. Then we learned about a cryptographic hash, which is an irreversible algorithm applied to some data. By trial and error (more quadrillion attempts per second) miners in the bitcoin network are trying to calculate a cryptographic hash for random data until the resulting hash value falls into a predefined range - a task designed to solve on average ten minutes the whole bitcoin network. The difficulty of this task on the one hand protects the network from "double spending", and on the other hand controls the delivery of bitcoin. In addition, bitcoin miners also process transactions that form a block. If the miner successfully extracts the block (by solving a cryptographic hash problem), this block will be recognized by the bitcoin network and permanently included in the blockchain - an open decentralized bitcoin ledger. This is the shortest description of how this complex and elegant system works.
If you didn’t know anything about bitcoin before reading this book, you could still hear the title “Mt. Gox 'thanks to the mainstream media. Mt Gox made up an interesting bitcoin story, so it’s worth figuring out what happened. Mt Gox is a bankrupt Japanese bitcoin exchange launched by a Frenchman named Marc Karpeles.
Until 2013, bitcoin was little known outside the handful of people scattered around the world. Then he had not yet become mainstream and was not the subject of discussion by the governments of large states. If at that time you wanted to buy bitcoin, you had a very limited choice. In those years, Mt. Gox was unconditionally the largest bitcoin exchanger in the world, claiming to hold more than 80% of the bitcoin trading market. I think this was close to the truth, because at that time there were few alternatives.
Since Mt. Gox controlled the vast majority of bitcoin trades, and most people understood very little about bitcoin, the name “Mt. Gox ”has become almost synonymous with bitcoin as such. By the way, there is a famous story about why Mt. Gox became known as “Mt. Gox. " Apparently, when the site was created, the original owner had already bought the domain name mtgox .com for another project, on which he worked, related to the card game Magic: The Gathering. Therefore, the domain name meant “Magic The Gathering Online eXchange”. He later abandoned the idea of this site, and the domain name was used for the Bitcoin exchange, known as “Mt. Gox. " After some time, the first owner sold most of his company to Mark Carpeles.
Now I think in the early days of Mt. Gox, perhaps, no one imagined that the site would grow so much - maybe yes, but I doubt that they could suggest an incredible increase in Bitcoin in early 2013. For various reasons, bitcoin began to flourish, withdrawing the price of one bitcoin from about 10 to about 250 dollars in just a few months. Subsequently, the price rose to almost $ 1,000 by the end of the year. And where did people go to buy bitcoin? One of the few places where they could do this was the Mt. Gox.
I want to emphasize that I have no insider information about what Mt. did or did not do. Gox; I know about Mt. Gox only as their client, as well as from discussions with industry colleagues. In early 2013, my business partner Adrian and I used Mt. Gox to buy bitcoin. Since we have been developing software systems for financial institutions for most of our careers, Mt. Gox seemed to us unprofessional and amateurish. It took them several weeks to open and verify our accounts, their customer service worked poorly, and the site has not been updated for a long time. In addition, there were stories of failures of Mt. Gox under a relatively large load and reports that they were “hacked” and people lost money. It was definitely a type of financial system that I would not trust my money to. At the same time we were going to buy bitcoin. Our strategy was as follows: we deposited relatively small amounts of money, bought bitcoin, immediately took it out, and repeated this cycle again. Thus, in case of any problems with Mt. Gox our losses would be limited to the amount of the last deposit. Unfortunately for many other Mt. Gox, they did not use a similar approach. By mid-2013, it became apparent that Mt. Gox troubles because they suspended the withdrawal of money, and shortly thereafter, the company declared bankruptcy, recognizing the loss of almost all the bitcoins they stored for customers, which at the time of their bankruptcy was about half a billion US dollars, or about 7% of all bitcoins in circulation.
On any scale, this event was a disaster for Bitcoin as a whole. This was a disaster for everyone who had a Bitcoin account, and a disaster for the Bitcoin reputation, which many saw as a failure by itself due to the poor management of Mt. Gox. I do not know why Mt. Gox lost money. In one of their ads, they suspected that the money was stolen, but ultimately it was just speculation on how it happened - the point is that people lost a lot of money because of this.
Regretting those affected by the collapse of Mt. Gox, it should be noted that the announcement of their bankruptcy was in some way desirable. Their delays and the suspension of withdrawals, which lasted for many months, caused new problems for the bitcoin community and a very bad press reputation. Mt Gox was a ticking time bomb. Their collapse allowed other companies to start from scratch, much more reliable than Mt. Gox, and lead bitcoin ahead.
You may also notice that to some extent it is the poorly organized platform Mt. Gox led us to the idea of creating our own Bitcoin exchange, Independent Reserve. We knew that in order for bitcoin to ultimately be successful, we needed a stable, stable platform from which people can buy bitcoin, and Mt. Gox is not.
If you have not heard of the collapse of Mt. Gox in 2014, you may have heard of Silkroad. By the way, the name “Silk Road” originally refers to the sequence of trade routes that connected Asia and Europe over many periods of history. They were called so because of the profitable trade in Chinese silk, carried out along the paths, and significantly contributed to the development of trade between the two parts of the world.
The Silk Road, of which we speak, however, was a site of a special type. It was special because it did not have access from a regular browser. It could only be accessed using a special program called Tor. [9] , which made the user anonymous, allowing people to enter the site so that they could not be traced. Silkroad was essentially a marketplace where you could buy and sell goods. Due to the fact that it was set up with a clear goal to anonymize users, the products for sale were mostly black market items that were not on regular sites where authorities could track activity. Therefore, the predominant types of products available on Silkroad were illicit drugs, prescription drugs, firearms and other illegal goods.
Silkroad used bitcoin as a currency because bitcoin could be transferred between market participants anonymously. [10] . Unfortunately, this worsened the bitcoin's reputation, since the media made the false conclusion that since Silkroad uses bitcoin as currency, then all users of bitcoin are pirates and traffickers from Silkroad. In October 2013, the FBI was able to track down the site administrators, and the site was stopped [11] . What happened to the bitcoin price? There was a slight recession, and then it continued to grow. The reason for this is that the vast majority of Bitcoin users were not pirates and drug dealers, and the fact that Bitcoin continued to grow, despite the lack of Silkroad, is proof of that.
From this we can learn a few lessons. Firstly, all currencies are used to a certain extent and will be used for illegal purposes - this is proof of their suitability as a currency. In November 2013, in response to a request from the United States Senate, the Agency for Combating Financial Crimes emphasized that any illegal use of bitcoin is insignificant compared to $ 1.6 trillion of “global criminal income” in 1999.
It is also worth noting that any transactions carried out on Silkroad between anonymous participants, at least, did not lead to an increase in violence in society, as opposed to violence, which is sometimes associated with cash transactions carried out on the street.
Bitcoin is not the only digital currency, although it was the first and most successful internationally, and has an overwhelming market share (98%) in terms of capitalization compared to other digital currencies. Bitcoin first earned in 2009, and until 2011 there were no alternative digital currencies, like Lightcoin, which is largely a bitcoin clone with minor changes to several settings.
I believe that the developers of some of these early currencies had good intentions, but today there are over 500 “alternative Bitcoin” digital currencies in the world that most people (including me) have never heard of, and I believe that a good part of them, is nothing more than a scheme designed to bring profit to the developer.
Another thing is that, even though Bitcoin has become a huge evolutionary step in the history of money, it is still imperfect, and it is inevitable that the Bitcoin protocol will improve over time (as it already happened), and that potentially new digital currencies can be viable at the same time with bitcoin, or eventually replace bitcoin. The blockchain idea is essentially robust, and most digital currencies, if not all, are based on the same basic principles as bitcoin.
We have already mentioned that bitcoin and physical money have common properties. However, bitcoin has a number of features that allow you to protect it from accidental loss or theft in a manner unreachable for ordinary money.
For starters, you can backup your wallet. This means exactly what is said: just as you make backup copies of photos or letters, you can create a copy of your digital wallet and store it in different places. This is the easiest way to protect your bitcoins from accidental loss. If you lose your phone with a bitcoin wallet, or if the computer disk fails, you can restore all your money from a backup. Even better, you don’t even need to make a backup after each transaction. Most modern bitcoin wallets are designed in such a way that if you made a copy, even if there were no funds at the time when the copy was made - money received in the future will still be restored, so you need to backup the wallet only once. Some wallets are designed so that you can even generate new addresses, and still enough to copy the wallet only once [12] .
Backups protect your wallet from accidental data loss, but they do not protect you from thieves. However, wallets are easily encrypted and can be password protected. Then, if someone steals your bitcoin wallet on it, he will not be able to spend it without your password. In the meantime, you can restore your wallet from a backup and transfer money to a new wallet for security. Then, even if the thieves can guess your password, bitcoins will already be sent to the new address, and your old wallet will become absolutely useless for them. All these things do not require the possession of special skills, they are usually part of most bitcoin programs and they are very easy to use even for a beginner.
These features are great for protecting funds in reasonable amounts; however, when dealing with large amounts of bitcoins, say, equivalent to a million dollars, we may want to take extra precautions. After all, what if an attacker gains access to our computer and installs a spy program that secretly records the passwords that you typed? History shows that there is no limit to the cunning and dishonest techniques that thieves can invent when it comes to stealing money. Suffice it to recall some well-known casino robberies in Las Vegas and things people went to when large sums of money were at stake. However, bitcoin provides great opportunities when it comes to security. One of the ways to protect a large amount of bitcoins is called freezing. The idea of freezing in this context means storing bitcoins on a computer or other device that is not connected to the Internet. A computer or mobile phone connected to the Internet can potentially be hacked by anyone from anywhere in the world if a vulnerability is found. But storing bitcoins on a computer that is not connected to the Internet, you immediately limit potential threats to only those that come from people who have physical access to this computer. Of course, the wallet on this computer must be encrypted and protected with a strong password. Modern programs easily provide the ability to store bitcoins in the freeze.
Bitcoin has even more advanced security features, such as “multi-signature” addresses (in common parlance known as “multisig” addresses). In all the examples we have given so far, we have described how I send 50 bitcoins to my friend Joe in a transaction signed with the corresponding private key that I have. In the case of multisig addresses, the transaction can be configured in such a way that two different people, or three people, or two out of three people, or any combination of signatures you can present, will be needed for the signature. For example, you may have a bitcoin wallet that requires both signatures — yours and your business partner — to send a transaction, or just one of the signatures. Or perhaps you have a board of directors, and the transaction should be signed by any three of the seven directors. These are very powerful tools that allow Bitcoin to be secured in ways inaccessible to physical money.
The last bitcoin wallet security method we’re talking about is called a “paper wallet”, and this is the most primitive of all bitcoin security devices. You can simply print your private key on paper, and in the case of an EMP [13] , which destroys all your electronic devices, you can recover funds using a printed private key. Of course, you can go even further, and print half of the private key on one sheet, and the other half - on the other, and store them in various safe places - the possibilities are endless.
So far in this book, we have discussed the most common and simple type of transaction - participant A sends money to participant B. We looked at how this process is carried out using bitcoin, as well as some of the great advantages of bitcoin compared to a regular currency. However, using this example, we barely scratched the surface of what bitcoin and blockchain technology can really achieve. We introduce the idea of "smart contracts". Bitcoin is able to create complex transactions involving many participants. Let's take an example.
Let, say, a car manufacturer makes a new car. In the process of its creation, a new bitcoin address is generated, to which the symbolic sum of bitcoins (i.e., 0.0001) is deposited, and this transaction is recorded in the blockchain. The manufacturer assigns this public address to the machine. The private key is then issued to the seller, who can store it on his mobile phone, so that his phone also serves as a car key, allowing him to open and start the car.
When the seller is going to sell the car to the buyer, the transaction is recorded in such a way that the money is transferred to the seller, and the car is transferred to the buyer as an address to which he can access from a mobile phone. Both participants must sign a transaction so that it becomes valid and is included in the blockchain. When the transaction is completed, the buyer can “present” his phone to the machine via NFC [14] , and the car recognizes the new owner and turns on the ignition. In this example, a transaction between two participants occurs at the same time, and thus, neither participant should trust the other. Moreover, the buyer can review the entire transaction history for the machine on the blockchain to make sure that it is real and make sure that the seller really owns the car.
Let's expand on this example. What if the buyer cannot afford to buy a car, and he needs to borrow money to make a purchase. A bitcoin transaction can be built in such a way that the creditor has ownership of the car until either the agreed amount is paid to him within a certain period of time, and then the car is transferred to the debtor, or the debtor loses the security, and the creditor remains the owner of the car .
The idea of a multilateral agreement is not new, banks borrowed money at all times. However, when using bitcoin and blockchain technology, the process becomes much more efficient, and participants need to trust each other to a lesser extent in order to fulfill the terms of the contract, which are automatically respected by the bitcoin network. It is interesting to see what new possibilities of using bitcoin and blockchain people will open tomorrow.
One of the big questions that has arisen about Bitcoin is whether transactions are anonymous and, if they are anonymous, whether bitcoin will not contribute to money laundering and other crimes. The answer here is both yes and no. Let's look at this question more closely.
Suppose, say, I buy something big worth millions of dollars from a stranger to me, and he gives me a new bitcoin address to which I have to transfer 10,000 bitcoins. At this point, the transaction is anonymous. Assuming that another participant generated a completely new address, I cannot determine who he is, and no one can associate the receipt of 10,000 bitcoins with this person. If this person keeps these funds and never spends them, he will remain anonymous. At some point, however, a stranger will most likely want to spend his 10,000 bitcoins, or perhaps exchange them for fiat currency. [15] . Now, if our stranger finds another stranger on the street and sells his 10,000 bitcoins for a million dollars in cash, everything will still be quite anonymous. However, usually, especially in the case of large sums, this person will need to spend this money with the help of a legitimate business or exchange it in a trustworthy exchanger. At these points, in particular during currency exchange, in the process of opening an account, a strict identity check is required to comply with AML / CTF standards. [16] , applied in the traditional financial sector. As soon as money begins to be spent through the usual channels, it becomes possible for the researcher to connect the dots and trace the transaction history. So, is Bitcoin anonymous? It can be as much as cash is anonymous. Cash may also be anonymous, but if one day you come to the bank with a million dollars in cash, authorities may raise their eyebrows in surprise.
Many world governments are now asking themselves whether bitcoin should be considered legal tender, and if so, should it be regulated, and if so, to what extent.
In my opinion, the answer is that bitcoin needs balanced and well-thought-out regulation. Regulation that does not overwhelm a new industry, but at the same time protects consumers from unlawful actions. Another point to take into account is that we cannot take yesterday's laws, applied to a completely different financial paradigm, and use them for bitcoin. Bitcoin works in a way fundamentally different from ordinary currency, and it is necessary to develop such a regulation that supports a decentralized digital model.
Then the question arises of how this regulation should look like? I believe that it is absolutely necessary to allow Bitcoin and other digital currencies as legal means of payment; the idea of a currency issued by a state may one day be a relic of the past. Governments and economies should use this new world currency and watch how trade flourishes, as people can conduct transactions around the world in the blink of an eye, without delay due to outdated and creaking banking systems. Even without taking Bitcoin into account, as a software developer who spent many years creating programs for financial institutions, I can say that most of the systems I saw are really ancient. These are large computers, created over thirty years ago,who need special (really old) engineers to service them. This is one of the reasons why banks are slowly adopting new technologies, because their systems are not ready for renewal.
The adoption of Bitcoin can lead to an increase in trade around the world, perhaps even removing entire states from poverty, turning them into flourishing economies.
Where, in my opinion, regulation is necessaryso it is in financial institutions storing bitcoin for other people, like banks. We have already witnessed the first great financial collapse of Bitcoin with the fall of Mt. Gox, and no later than a week before I write these lines, we saw how Bitstamp, the European bitcoin exchange, lost five million dollars to bitcoins from its digital storage. To their credit, most of their funds were kept safely in a freeze, and they replenished the balance of account holders. This emphasizes, however, that without some oversight of the security measures that these organizations undertake, consumers will not be able to trust the institutions responsible for storing their bitcoins.
It is important to emphasize that this is not a bitcoin vulnerability in itself, it is only a sign of the immaturity of the bitcoin financial sector. In the twelve months since Mt. Gox, we could see how the whole industry is taking big steps to improve security, and will undoubtedly continue to do so. Bitcoin’s strong, stable and secure financial sector is in everyone’s interest — and a balanced level of regulatory oversight in this area will not bring anything wrong.
For regulators, it is important to remember that since bitcoin is a new industry, it moves in very fast steps, and new methods develop all the time. It would be a step back for regulators if, with a limited understanding of a developing industry, they would require something impossible to execute instructions, or create instructions that are harmful for Bitcoin growth. The best move for them at the moment will be to stay a step behind and observe carefully, taking the necessary steps as the industry matures. This principle probably applies to many areas.
Many events have significantly changed the face of Bitcoin, from the initial starting point at the end of 2008, to the flourishing industry that it has become now. The following are some of the key points in this chronology.
October 2008. An anonymous article has been published entitled “Bitcoin: a peer-to-peer electronic money system,” essentially describing what bitcoin has become. The article was published by a person using the pseudonym Satoshi Nakamoto .
January 2009.The first blockchain block, also called the genesis block, was extracted, version 0.1 of the bitcoin program (including the source code) became publicly available. The program was written anonymously, and because of a rather non-standard programming style, combined with rigorous theoretical know-how and completeness, speculations about whether it was written by an academic with little programming experience or perhaps a team of such people have been popular for a long time.
Then, on January 12, 2009 , the first bitcoin transaction occurred - from Satoshi Nakamoto to Hel Finney
October 2009.The New Liberty Standard website published a bitcoin exchange rate that seemed to be appropriate for it at that time, based on a formula that included the cost of electricity needed to operate a bitcoin computer. Their proposed exchange rate was USD 1 = XBT 1309.03.
February 2010. There was the first bitcoin exchange called “The Bitcoin Market”. This exchange did not last long, and was closed due to problems with fraud a little over a year later.
May 2010. A US programmer named Laszlo bought some pizzas at Jercos for 10,000 bitcoins. The price of pizza was $ 25 (the equivalent of a bitcoin price of $ 0.0025).
July 2010.Bitcoin was mentioned on Slashdot’s famous IT website, which caused a tenfold increase in price in less than a week. The price rose from $ 0.008 to $ 0.08. That same month, Jed McCaleb launched Mt. Gox, having read about Bitcoin on Slashdot. Interestingly, Jed McCaleb said later in 2011 after selling Mt. Gox:
« I created Mt . Gox for fun, after reading about bitcoin last summer. It was fun and fun to do. I'm still convinced that bitcoin has a beautiful future. But to really make Mt . Gox as it may be, takes more time than I have now. So I decided to pass the baton to someone who has more opportunities to take the site to the next level. "
In other words, McCaleb worked on Mt. Gox alone for a few weeks or months in his spare time - everything worked out because he had a hobby and bitcoin did not have real value at the time. He recognized this fact at the moment when he sold the site. Compare this with a modern stock exchange, such as Independent Reserve, which was developed by a team of professional programmers for more than 18 months, including measures provided for in the system to ensure its security, scalability, stability and reliability. It is not surprising that without extensive processing of Mt. Gox was not able to support the multi-million dollar industry in the future.
Another interesting thing that happened in July 2010 was that this month someone came up with a way to use the GPU (graphics processor) to extract bitcoin faster than was possible using the usual production method on the central processor.
The global frequency of processing hashes by the bitcoin network has now reached 1 gigachesh (GH), or 1,000,000,000 (1 billion) hashes per second.
August 2010A bitcoin protocol was discovered and then exploited. This led to the creation of more than 184 billion bitcoins generated in a single transaction. Within hours, the problem was discovered and the vulnerability fixed. The transaction history from this transaction has been permanently deleted. It was the only major security flaw found and used in the entire history of Bitcoin.
November 2010. The capitalization of the bitcoin market for the first time exceeded one million US dollars. Bitcoin price on Mt. Gox reached 50 cents.
December 2010. The global frequency of processing hashes bitcoin network for the first time exceeded 100 GH.
February 2011.Silkroad has opened, a networked black market that uses bitcoin as a form of payment. In the same month, the bitcoin rate on Mt. Gox first reached parity with the dollar.
March 2011. Jed McCaleb sold Mt. Gox to Mark Carpeles.
April 2011. Traditional media has written about bitcoin for the first time, TIME has published an article entitled “Online currency can challenge governments and banks.”
June 2011. Bitcoin price on Mt. Gox for the first time exceeded 10 dollars. That same month, Mt. Gox began to show signs of problems, a serious security breach was found in their system, leading to the compromising of personal data of more than 60,000 users, as well as fraudulent requests for hundreds of thousands of bitcoins, which caused a sharp drop in prices to 1 cent.
In June, the largest Bitcoin theft occurred in history. 25,000,000 bitcoins worth more than a quarter of a million US dollars were stolen.
In the same month, WikiLeaks began accepting donations in bitcoins.
July 2011. Just a month after the security problems of Mt. Gox Polish bitcoin exchange, at that time the third largest in the world, lost 17,000 bitcoins of its customers.
August 2011 Another bitcoin company that processed bitcoin transactions lost more than 150,000 bitcoins worth more than $ 2 million at that time.
At that time, many such incidents happened. As you can see, it was an unpleasant story for Bitcoin, so it’s worth taking time to analyze what “loss” means and why it continued to happen. It should be noted that in all these cases (excluding the vulnerability discovered in August 2010), the problem was not in Bitcoin itself, but in the incompetence of the people managing the companies that were charged with storing bitcoins for other people. At that time, as much as now, these companies were not regulated at all, but people trusted them bitcoins for millions of dollars.
At the heart of the bitcoin wallet, which stores someone's bitcoin, is a file or a set of files on your computer. To protect these files, you need to backup them and encrypt them as described in the chapter “How to secure your bitcoin”. The organization responsible for bitcoins worth millions of dollars in essence should perform the same task, but the methods used should be some kind of more reliable (compare the protection of money in your wallet with the bank vault, with gold in Fort Knox - as responsibility increases, the level of security should also increase). If the files in which the private keys for the bitcoin wallet are stored are damaged or changed (for example, due to a hardware failure), or the thief got access to the computer and stole the files, then the bitcoins are lost.
There are fewer such security incidents today, but the threat still persists, which is why companies and individuals should keep this in mind.
October 2011. A former Google employee creates Litecoin, an alternative to bitcoin.
May 2012. More than half of the bitcoin transactions in a month were caused by the online game SatoshiDICE.
June 2012. The famous online wallet Coinbase is based in San Francisco, USA.
November 2012. The reward for bitcoin mining was reduced by half for the first time - the reward for mining a unit dropped from 50 XBT to 25 XBT (this happened during the extraction of 210,000 units).
The popular online blogging platform Wordpress is starting to accept payments in bitcoins.
December 2012. Bitcoin Central, the first Bitcoin exchange licensed as a European bank, begins operations in the European regulatory and legal segment.
January 2013. The first ASIC (Application Specific Integration Circuit - Special Purpose Integrated Circuit) - Bitcoin mining machines were released. Just as the GPU beat the CPU, the ASIC is now the most powerful and efficient machine available - this is special equipment designed only for bitcoin mining.
BitPay, a US-based Bitcoin payment processing company, announced that the number of transactions with their merchants exceeded 10,000.
February 2013.Bitcoin price has reached its greatest height, exceeding the value of 31.91 dollars, fixed at Mt. Gox 601 days before this in June 2011.
March 2013. The blockchain split for two, caused by the different behavior of two different versions of bitcoin programs. This meant that users with the old version of the program saw one transaction, while users with the new version saw another set of transactions. The split was quickly corrected by bitcoin miners who returned to an earlier version of the program. The bitcoin price temporarily fell during this period, but it quickly strengthened again to the price before branching.
By the end of the month, the price rose even more, and the total capitalization of the Bitcoin market for the first time exceeded one billion US dollars.
April 2013.Price continued impressive growth in April, reaching $ 250. The Cyprus financial crisis was called a potential catalyst for unprecedented growth. After the peak, the price stabilized at $ 120 for the next few months.
May 2013. Something that aroused my interest during my research, ESEA, a computer games company in the United States, used users' computers using a carefully crafted malware program to secretly extract bitcoin. They were caught and received a class action for millions of dollars. This, of course, is not the only example of such activity. In one of the places where I used to work, an employee was fired for secretly using the company's powerful computers to mine Bitcoin.
Probably less interesting, but more importantly, that same month the first Bitcoin ATM was opened in San Diego, USA.
Coinbase also received over $ 5 million in May from investors, the largest investment in the bitcoin industry at that time.
June 2013. In Sydney, Australia, our company, Independent Reserve, was founded. Before that, we spent six months analyzing the bitcoin and bitcoin market in order to understand how best to integrate into the new economy. We decided that Australia needed a reliable bitcoin exchange to create a solid foundation that other bitcoin-related businesses could use as a basis for their own offers.
August 2013.A federal judge in the United States classified bitcoin as a legal tender. At the same time, the German government legitimized bitcoin, declaring digital currencies a “unit of account”. Also in August, bitcoin appeared on the Bloomberg terminals with the currency code XBT.
September 2013. The global computing power of the Bitcoin network for the first time reached 1 pentahesh or 1,000,000,000,000,000 (1 quadrillion) hashes per second.
October 2013. The infamous Silkroad site was closed by the FBI. Instead of a skeptic-predicted collapse of the market, the price of bitcoin fell for a short time, but then continued to grow, as it became clear that most of the transactions were not related to Silkroad, and Silkroad was a relatively small player in the Bitcoin economy.
In the same month, global investment bank Merill Lynch called bitcoin potentially "the main payment instrument in e-commerce, able to become a serious competitor to traditional money transfer systems ."
In October, the largest Chinese search engine Baidu became the first service of this kind to accept bitcoin.
November 2013.
The head of the US Federal Reserve, Ben Bernanke, publicly announced that Bitcoin " may have a long-term perspective, especially if innovation offers a faster, safer and more efficient payment system". The US Senate, which held a Bitcoin hearing, also cautiously favored digital currencies, and the Financial Crimes Enforcement Network declared Bitcoin innovative and useful, warning that premature regulation could stifle innovation. They also pointed out to critics that any illegal use of bitcoin was insignificant compared to $ 1.6 trillion of “global criminal income” in 1999. The positive results of the hearings in the Senate in November caused the rise in the Bitcoin price to $ 1,242.
At the same time, billionaire entrepreneur Sir Richard Branson announced at CNBC that his company, Virgin Galactic, engaged in commercial space flights, will accept payments in bitcoins. He called bitcoin an “exciting new currency.” The company has already received the first payment worth about $ 250,000.
At this point in the history of Bitcoin, it is used to transfer more money than Western Union, about 245 million dollars a month.
December 2013. One of Tesla Model S electric cars Ilona Mask (PayPal, SpaceX, Tesla, SolarCity) was sold in the US for bitcoins. The price of the car at that time was about 103,000 dollars.
However, while Bitcoin flourished in the west, in the east, the Central Bank of China prohibited financial institutions from processing bitcoin transactions, which caused the price to fall to about $ 500. This ruling prompted Baidu to stop accepting Bitcoin payments.
January 2014. Global computing power for the first time reached 10 pentaheshs.
March 2014. The British Tax Administration stated that Bitcoin should be considered as the currency for executing transactions.
June 2014. Expedia, one of the largest travel agencies in the world, is starting to accept bitcoin payments.
The global computing power of the network reaches 100 pentaheshs.
July 2014.Dell, one of the largest computer makers in the world, is starting to accept bitcoin payments.
September 2014. PayPal, one of the largest payment processing companies, gives merchants the ability to accept payments in bitcoins.
October 2014. Independent Reserve, the most advanced and secure bitcoin exchange in Australia, was launched in Sydney.
November 2014. The Australian Senate begins exploring the use of bitcoin and digital currencies in Australia.
December 2014. Microsoft, one of the largest software makers in the world, is starting to accept bitcoin for some online purchases.
January 2015The New York Stock Exchange and a consortium of international banks are investing $ 75 million in the bitcoin industry.
August 2015 The Australian Senate issues recommendations on the study of digital currencies, demanding to treat Bitcoin as ordinary money for tax purposes, and also to apply anti-money laundering laws to digital currencies. This result is perceived by the Australian bitcoin industry as a very positive step towards legalizing a young currency.
I hope you enjoyed reading the book of Adam, as well as I liked the time spent editing and completing his manuscript. For the last 14 years, Adam and I have worked together on so many different projects that it often seemed to me that he was here, next to me, working on this book, arguing about some formulations or trying to convince me that his interpretation of the obscure grammatical rule is more correct, than mine
While I was working on the book, I wondered whether to include additional chapters and expand some sections. I know that Adam would probably have written more if he had a chance, but I decided that it would be better to keep the book close to the original in order to demonstrate the work and thoughts of Adam himself. It seemed to me more important than adding another chapter, say, "Side chains" or "The Future of Bitcoin", and, in my opinion, this book is quite strong as it is, it does not need additional content.
I am sorry that Adam cannot see his ambitions realized, and his book published. I know that he would be proud to see this project completed. It was the culmination of many hours of work on the text, many years of research and hard work in the IT and Bitcoin industry, which gave him the knowledge and understanding to write this book.
I know that this publication would bring him joy, which will leave his mark on history for many years.
Adrian Gentle
[1] Bitcoins can be stored non-electronically, for example, on paper, but this is the exception rather than the rule. Transactions, however, are always electronic.
[2] XBT is accepted as the standard currency for Bitcoin. In other currency notation, the first character usually means the country that issued the currency. In some places, the alternative BTC designation is still used.
[3] When I say "computer", in fact, I mean any electronic device where the corresponding program is installed. This may be a mobile phone, laptop or similar device.
[4] Technically, the “impossibility” of hacking has not been proven for any form of software encryption or digital signature, but it can be reasonably stated that forging a digital signature is so difficult that it is almost impossible in all practical applications.
[5] Below we will see that as a precaution against fraud, it is reasonable to wait half an hour to confirm a transaction with a significant amount, but usually all transactions can be seen in a few seconds.
[6] It is worthwhile to stop and think about how astronomically large a number, consisting of several hundred numbers. This is many orders of magnitude more than the number of atoms in the observable universe.
[7] As we already noted in the third chapter, there is nothing truly “impossible” in the world of cryptography, but in practice some things are considered rather complicated so that for all practical purposes we consider them impossible.
[8] The process of hashing a user password is a bit more complicated, and includes adding a random value to the password, known as “salt.” Thus, if two people have the same password, this provides different hash values, making the system more secure.
[9] Tor is an abbreviation for The Onion Router (onion router), this project was originally developed for the US Navy, and was designed for encrypted and anonymous online communication. Now this software is widely used on the Internet to provide anonymity for people who want to keep their online privacy confidential.
[10] For a more serious discussion of this topic, see Chapter Eight - “Anonymity.”
[11] Silkroad has since replaced other anonymous black markets that have grown due to its decline.
[12] Such wallets are called “hierarchically deterministic” or “HD-wallets”.
[13] "EMP" or "electromagnetic pulse" is a brief, strong release of energy that can cause data loss stored on computer disks without being recoverable. It can occur naturally, for example, due to a lightning strike, or due to a person, as a form of weapon.
[14] NFC (Near Field Communication) is near-field communication, a technology that is increasingly used in modern telephones and enables data exchange between devices in close proximity to each other.
[15] “Fiat currency” is money that the government declares to be legal tender, but which is not provided with physical values. The value of fiat money is derived from the relationship between supply and demand, and not from the value of the material from which they are made.
[16] AML / CTF (Anti Money Laundering / Counter Terrorism Financing) - counteracting money laundering and terrorist financing is a set of legal requirements that banks and other financial institutions must follow to ensure that their customers do not use money for illegal purposes. Since bitcoin exchanges, along with bitcoin, deal with traditional currencies, they are usually also required to follow various procedures for verifying the identity of their clients and notifying them of suspicious transactions.

Adam Tepper BITKOIN - MONEY FOR EVERYONE
Table of contents
Translator's Preface
Adriana's Preface are Precious.
Foreword
Part I. What is bitcoin
Chapter one. Introduction to bitcoin
Chapter two Money history
Chapter Three Working example
Chapter Four How bitcoin is mined
Chapter Five Why use bitcoin
Part II. How bitcoin works
Chapter Six Asymmetric keys
Chapter Seven. Hashing
Chapter Eight Decentralization
Chapter Nine. Blockchain
Chapter Ten. Bitcoin mining
Chapter Eleven. Miner's stimulus
Chapter Twelve. TL; DR
Part III. Broader view
Chapter Thirteen Mt Gox
Chapter Fourteen. Silkroad
Chapter Fifteen. Other digital currencies.
Chapter Sixteen. How to secure your bitcoin
Chapter Seventeen. Smart contracts.
Chapter Eighteen. Anonymity
Chapter Nineteen. Regulation
Chapter Twenty. Chronology
The afterword of Adriana is Delighted.
Translator's Preface
It seems that the preface for such a little book turns out to be a bit much, but somehow I will have to write a few words. I took up the translation of this text, firstly, as a kind of tribute to the deceased colleague (and friend), with whom I worked for the past few years; secondly, because this book is really a great introduction to bitcoin for people who are not knowledgeable about information technology. It seems to me that the appearance of this text is quite detailed, and at the same time not too long — it will be useful in Russian. The more people get acquainted with bitcoin, the less they will be afraid of him - after all, unfamiliar things scare away, and in the mysterious bitcoin there is absolutely nothing to worry about.
A few comments about the actual translation. A number of anglicisms - "mining", "blockchain", "hashing", etc. - are widely used in Russian-language articles on Bitcoin, and the attempt to get rid of them, I think, does not bode well for the meaning of the text; in fact, you can, of course, translate "mining" as "mining" or "production", "blockchain" as "chain of blocks" (which sounds somewhat clumsy), but how then to call "miner" - "prospector"? "Getter"? - this is too much.
')
The word "bitcoin" also, obviously, remains without translation. In the text, it is used as in the singular (“bitcoin” in the substantive sense, as “money”), and in the plural (“bitcoin” in a specific form, as “coins”).
If the word "dollar" is used in the text without further instructions, it means the US dollar.
The text of the book is available for download in PDF in English and Russian languages on the site www.independentreserve.com (registration is required), a paper version can also be ordered there (only English). Not being a professional translator, I will gladly accept amendments and clarifications, if any. I want to thank Olga Yurieva for the initial reading of the text and Vatslav Egurnova for the titanic work on editing.
Alexey Zhikharevich
Adriana Preface Preface
Adam Tepper died tragically in a car accident in February 2015, before he finished this book. As a close friend of Adam and his business partner in countless projects, I had to finish what he started by completing his manuscript and publishing this book in print.
I would like to emphasize that, although I made some changes and edits to this book, I firmly believe that they correspond to what Adam himself would have done if he had such an opportunity. This book, therefore, remains the work of Adam Tepper, and corresponds to his authorial intent.
Special thanks to those who donated money to the Adam family, and also made a donation through the Bitcoin page of the Australian Association to help pay for the publication of this book. Also, thanks to the Bitcoin embassy in Australia and those who have spent time reading the book and reviews about it at different stages.
Adam was a kind, intelligent and passionate young man with a clear vision of a future in which bitcoin can change people's lives for the better. Adam's favorite writer was Richard Feynman for his ability to explain complex and seemingly inaccessible ideas in clear and simple words. This talent was inherent in Adam himself, and this book is a great confirmation of this. I hope you enjoy learning Bitcoin through the words and thoughts of Adam Tepper.
Adrian Gentle

Foreword
Since I am one of the founders of Independent Reserve, an online currency exchange service specializing in exchanging bitcoin for other currencies, I am often asked to clarify what bitcoin is and why it is important. At the very beginning, I probably didn’t explain it very well to people, because Bitcoin connects many different ideas, mostly unusual. Albert Einstein once said: “If you cannot explain something simply, then you yourself do not understand it well enough,” and I think that to some extent this was the reason that I initially had difficulties explaining to others what bitcoin
Today, I still meet people who have never heard of bitcoin, and they ask me what it is. I usually answer in the shortest possible way, explaining the practical benefits of Bitcoin and omitting more interesting details about how it works. If a person is interested, I am ready to answer his questions until he reaches an understanding at the level that suits him. This is also the purpose of my book, and I arranged the chapters of the book in a similar way. The intended audience of this book is people who are completely unfamiliar with Bitcoin and completely unfamiliar with computer science in general. It is designed for the reader who wants to understand the basics of how bitcoin works, and at the same time understand technologies. The book begins with a review of Bitcoin in a practical sense, then I disassemble the ideas behind Bitcoin, and finally answer some more general questions that ask me about Bitcoin today.
Adam Tepper
money - metal and paper signs, which are a measure of value in the sale, a means of payment and the subject of accumulation
currency - the monetary system of the country, as well as the monetary units of this system
Part I. What is bitcoin. Chapter one. Introduction to bitcoin
Bitcoin is a currency, and thus is money. Money was not always what it is in our understanding today, and essentially Bitcoin is another development of the idea of money. One of the key factors that highlights bitcoin in comparison with other well-known currencies, such as the US dollar ($), the British pound (£) or the euro (€), is that bitcoin is an electronic currency, which generally means that bitcoin is stored electronically on computers [1] , and transmitted electronically over the Internet. The prospect of electronic money can confuse or discourage many people, just as email could confuse someone in the 1980s when it was described as emails stored and sent electronically via the Internet. Today, email is so common that paper letters, especially personal letters, are considered old-fashioned, cumbersome and, among other things, slow.
The first email users in the late 1980s or early 1990s may remember that at the very beginning it was not very helpful, because most of your friends, family and colleagues did not have an email address, nor even, perhaps, Internet connections. Friends asked questions like: “What is an e-mail and how to use it?”. It was a time when there was no Gmail, no Google, not even Hotmail. Electronic mailboxes were mainly provided by Internet providers. But soon most people had email addresses, and today it seems extremely unusual if someone doesn’t have an email address at all, just as if a person doesn’t have a mobile phone.
I’m talking about e-mail because this is a great bitcoin analogy. E-mail took the process of sending letters, used for many thousands of years, and adapted it to transmit and store letters in electronic form. In a relatively short time, the process of exchanging handwritten letters has become an archaic and unusual method of communication. It would be hard to imagine that we should mail again for daily communication and wait for a response for several days or a week. It is also worth mentioning that over the past twenty or thirty years, the ways we use email have also changed somewhat. We have access to the e-mail from all our devices; we can send large attachments and diverse content; we can use email to make appointments that appear on our calendars. All these ideas were not originally laid out when creating e-mail, but became its development based on how we use mail. Of course, there are many other forms of electronic communication that have evolved later. This development refers to the continuous improvement of electronic communication in general. But initially very few people saw the benefits of using e-mail.
This brings us back to bitcoin. Just as e-mail became the thing that brought communication into the electronic age, so bitcoin is what brings our monetary system into the electronic era. Before we consider how bitcoin can do this, it’s worth taking a look at the history of money to build a perspective.
Chapter two Money history
Money today is a very complex system. Most of the time it works, but from time to time it catastrophically breaks down. Although the system is complex, most complex things are invisible to us with its daily use. For most of our lives, the monetary system has barely changed - it’s something that we all grew up with, and most of us probably didn’t spend much time thinking about how it works. Money was not always the same. One of the biggest changes in the last hundred years has been the placement of most major currencies on the free market, as opposed to determining the price for gold or silver by the current government. This was a very significant progress of the monetary system, but let's look back even further to see how money has changed over thousands of years of use in various societies.
I remember when I was a child, I asked my father: "What did people do to money?" My father explained that “in the old days” people used the barter system, using sheep and other animals as currency. As a child, it was difficult for me to imagine how this could work, but in fact this is how money worked several thousand years ago. Sheep and cattle in general had certain drawbacks. They were difficult to store, difficult to move, and not easy to divide. Throughout human history, different cultures have used different products for these purposes. Seashells and rice were used as money, and then precious metals, gold or silver, which later became customary because they had many qualities suitable for currency: they were durable, portable, divisible and rare.
To make a transaction using a precious metal, such as gold, you can determine the value of an item as the value of a certain amount of gold. This decision was imperfect, since the process of assessing the purity of the metal and its weight did not contribute to the speed of transactions. States later improved this process by minting standardized coins containing a certain amount of precious metal, the weight and authenticity of which were confirmed by the state. This is an interesting moment in the history of money. It is interesting because, although the coins contained the prescribed amount of gold or silver, they were valued by the state, and the merchants did not need to analyze the purity and authenticity of the coins as such. Consequently, trust has now shifted to the state. It did not take long for governments to understand that since the value of coins lies in the sign of the mint, it will be cheaper to produce coins containing less precious metal than the indicated weight of the coin. This step in the history of money was a change that turned a coin from a unit of weight into a unit of value.
As European trade flourished in the Middle Ages, the idea of a bill of exchange spread, through which a merchant could offer a credit line to a trusted buyer. The goods were delivered to the buyer in exchange for a bill on which he pledged to make payment on a certain day in the future. Provided that the buyer was a respected person, or the bill was approved by a trustworthy guarantor, the seller could then submit it to the bank for redemption at a reduced price before the expected date. These bills were also used by the seller as a form of payment to make additional purchases from their suppliers. Thus, promissory notes - an early form of credit - became both a means of exchange and a store of value.
In the twelfth century, the English monarchy introduced a system based on similar prerequisites — mortgages through which the monarchy could make payments based on expected taxes that had not yet been received. They were also known as tally (notched wooden sticks). The treasury found that they could also be used as money. When the crown exhausted its resources, she could use a tally representing future tax payments to the crown as a form of payment to her own creditors, who in turn could either collect taxes directly from payers or use these tally to pay their own taxes to the government. Thus, the tally was taken as a medium of exchange for certain types of transactions and as a store of value. The Treasury soon realized that it could issue a tally without any specific tax payments. By doing this, the treasury created new money, secured by public trust and faith in the state, rather than specific incomes.
At about the same time, banks began to issue paper notes, quite correctly called "banknotes", which were treated in the same way that the government issued currency is circulating today. Only denominations issued by the largest, most creditworthy banks were widely accepted. Papers of smaller, less well-known institutions were used only locally. Away from home, they were taken at a reduced price, if they were taken at all. The spread of money types went hand in hand with the multiplication of the number of financial institutions.
Banknotes were a form of secured money that could be turned into gold or silver upon presentation to a bank. Since banks issued significantly more securities than they kept gold and silver on deposits, a sudden loss of confidence in the bank could have caused a massive redemption of banknotes, which led to bankruptcy.
The use of banknotes issued by private commercial banks as legal tender was gradually superseded by the issuance of banknotes authorized and controlled by national governments. The Bank of England was given the exclusive right to issue banknotes in England in 1694, thus ending the use of private currency in the kingdom. Australia passed a similar law more than two centuries later, in 1910, and the United States followed in 1913.
Government-authorized currencies were a form of secured money, since they were partially secured with gold or silver and theoretically could be turned into gold or silver. At the time of President Nixon, the US dollar was withdrawn from the "gold-backed" standard in 1971, which caused the collapse of the international Bretton Woods monetary system. Most of the major world currencies were then placed on the open market, completely losing touch with precious metals, now the value of the currency was based solely on the economy and the reliability of the government issuing it.
Having understood the history of money, we can also see their weakness. Now let's take a closer look at the work of Bitcoin and its advantages over existing forms of money.
Chapter Three Working example
Bitcoin technology is fascinating. The first time I heard about Bitcoin a few years ago, almost immediately, as it appeared in 2009. My friend Joe, a man who likes to advertise the latest technological trends, told me that "one guy had figured out how to create Internet money." I did not understand the meaning of this phrase, and I believe that at that time my friend did not understand it either.
I no longer thought about bitcoin before I noticed an online advertisement some time ago, in November 2012, which contained something about bitcoin, and thought that I should take a look. The first thing I noted is that bitcoin, whatever it was, was selling for $ 10, and so it was for some time. I expected it to cost no more than a few cents, or even fractions of a cent. Of course, not knowing anything about bitcoin at that time, I could not understand how much bitcoin should cost, but assuming that there are millions of bitcoins in circulation, $ 10 seemed to be a significant figure, and I was curious to find out everything in more detail. After reading the many materials I found on the Internet, I was still far from understanding what bitcoin was or how it worked. Only after careful re-reading and research of cross-references to various resources I began to put a picture in my head. Definitely, I would not call it a deep or thorough understanding, I still had a lot of questions.
However, bitcoin captured my interest, and, being a programmer, I decided to write my primitive program that would allow me to send and receive bitcoins (it was never published, it was just an experiment to see how it works and satisfy my curiosity). I never finished this program, but spent two or three weeks developing it, and doing this, I eventually came to understand how Bitcoin works, and was deeply impressed and amazed at the underlying technology. She was amazed because she elegantly brought together many dissimilar principles of programming into a system that no one had ever thought of before, and which could now be effectively used as money.
Not wanting to advertise the idea in vain, about which I had doubts whether it would turn out to be another “perpetual motion machine”, I waited until I understood bitcoin deep enough before transferring this knowledge to my business partner Adrian Adorable. I was met with skepticism at exactly the same level as I had expected. A month later, he remarked to me: “Bitcoin is really an amazing thing - I've bought a little.”
So what was it about bitcoin that we both found striking, and what later led us on the path to creating a company so tied to bitcoin? In the second part of the book, we will deal with the technologies underlying Bitcoin, but first I must explain how it works at a high level. Bitcoin is a cross between physical currency and a checkbook. So far, we can only draw this analogy, but let's start with this.
Using this example, let's say I want to send my friend Joe $ 50 (USD). I can write a check with his name on it, write the amount and put my signature on the bottom of the check. In a perfect world, this is a great system. Joe gets a check, and he can't change the amount. If the check is stolen, it won’t help the thief, because Joe’s name is on the check. And if my checkbook is stolen, then it will have no value for anyone, because the checks do not have my signature yet. This is a good system in theory, but in practice it has several disadvantages. First, the check itself is not money. A check is essentially a letter to the bank authorizing the bank to give Joe $ 50 of my money stored there. As long as Joe does not bring the check to the bank, he does not know for sure if I have this 50 dollars. It may take the bank several days or a week to give Joe the money. Signatures are very easy to fake, so if someone gets my checkbook, it will not be particularly difficult for him to write a fraudulent check. In Australia, checkbooks are not used for about a generation; the concept itself is as archaic for us as the trade in gold bullion, but surprisingly, this system prevails in many countries, including the United States.
Let's compare this transaction with the transaction that bitcoin uses - let's say I want to send my friend Joe 50 bitcoins (XBT [2] ). The first key difference between the checkbook example and the bitcoin is that in the case of
checkbook stores $ 50 bank for me. Bitcoin, however, looks more like cash, and 50 bitcoins can be stored physically on your computer. [3] . Let's say I have 50 bitcoins in a digital wallet on my mobile phone that I want to send Jo to his mobile phone. First I ask Joe his bitcoin address. When I send money to Joe’s address, they can only be spent with the secret key stored on Joe’s phone. No one else can use this money without access to his phone.
So, with the help of a program on my phone, I start a transaction that sends 50 bitcoins from my personal bitcoin address to Joe's bitcoin address. Then I put a digital signature on this transaction, using the secret key on my phone, and send this information to the Internet, so that it is visible to the whole world. It's true, I don't send anything directly to Joe, I send information for the entire Bitcoin network.
What happens next is that when the rest of the computers in the bitcoin network receive information about my transaction, they check that I really have 50 bitcoins in my wallet and that my signature is correct. If everything is in order, they mark the transaction as valid, and soon it becomes part of the official global bitcoin ledger, known as the “blockchain” or “blockchain”, and is stored in it (we will discuss this in more detail below).
In the meantime, the program on Joe's phone, along with the rest of the world, confirms the transaction I started. Almost instantly, this transaction is displayed on his phone as the arrival of 50 bitcoins.
If I sent money to Joe, I can no longer spend these 50 bitcoins, because the bitcoin network no longer recognizes these 50 bitcoins as belonging to me, and can be spent only if you use Joe's secret key. Let's look at this situation from a different angle: the transaction I started was, in effect, a “letter” to the bitcoin network, transferring to Joe my right to spend 50 bitcoins. It's easy!

Let's look at this model more closely and analyze some of the differences between bitcoin and checkbook. In the case of a checkbook, there is a central bank that processes transactions.In the case of Bitcoin, there is no central transaction handler or supervisor — a decentralized model is used in which every member of the network, including the recipient, can authenticate the transaction. This is a quick process. For less risky transactions with small amounts, this process takes no more than a few seconds. For more risky transactions with large amounts, the transaction can be safely recognized as completed in about half an hour. Compare this with a bank check or SWIFT transfer, which usually takes from 1 to 5 days.
Another similar detail that you should have noticed is that bitcoin transactions are signed, just like old-fashioned checks. However, the difference is that a six-year-old child can manage with a fake signature on paper, whereas a fake digital signature used in a bitcoin transaction is almost impossible [4] .
Another interesting point is that the transaction processing cost and execution time are consistent, and they do not depend on the amount of the transaction [5] . Using the example above, I could send Joe a share of bit in bitcoins to pay the royalties he gets for his platinum album, or I could send him two million dollars to acquire his successful company. In any of these cases, the transaction fee will be the same, almost zero, and the execution time is almost instant. This ensures efficient, free and secure movement of money internationally at the speed of email.
Finally, it is worth noting that since the Bitcoin network covers the entire Internet, it doesn’t matter where Joe and I are physically located. We can sit in the same room or in different parts of the world - it does not matter. This does not affect the speed or the cost of the transaction.
Chapter Four How bitcoin is mined
In the previous chapter, we looked at an everyday example of how bitcoin can be used to send money between network members. However, here are the questions that people usually ask me: how Bitcoins are generated, how they are introduced into the economy, and where Bitcoin gets its value from. Before answering these questions, let us recall the history of money, which we discussed in the second chapter.
Until the twentieth century, money was at least partially provided with precious metals, such as gold or silver. Along with other important qualities that made gold and silver suitable as currency, was the fact that these metals were relatively rare. There was a steady, but slowly increasing influx of gold and silver, while they were mined from the earth. Mining required a lot of time, effort and cost. If gold and silver were abundant, and it would be easy to get them, then everyone would be engaged in mining, and they would cease to be valuable, respectively, they would cease to be suitable as money.
Although bitcoin mining and gold mining are very different in practice, the principle underlying them is the same, and therefore the generation of bitcoins have become similarly called “bitcoin mining”. Like gold, anyone can mine bitcoin with the appropriate resources. If you wanted to mine gold these days, you could do it, but remember that much of the gold near the surface of the earth has long been mined. Thus, you would need a bit of luck plus a great geological and logistic experience - as a result, most people are consumers of gold, not miners!
The way that bitcoin mining is done is that the bitcoin network introduces relatively small amounts of bitcoins into the economy at regular intervals. The bitcoin protocol sets a math problem that is built in such a way that it can be solved in about ten minutes. When the problem is solved, a person who owns a computer, who has solved the problem, is given a specified number of bitcoins. At the very beginning, perhaps, only one personal laptop solved these problems. Therefore, the task was relatively easy, so that the available laptop could solve it within ten minutes before repeating the process again. At this point, when bitcoin was in infancy and no one else used it, one bitcoin was not worth anything. Therefore, such an exercise in mining, which required small amounts of electricity,extracted some bitcoins that were worthless.
However, over time, two, then three, then thousands of laptops and home computers tried to solve a problem that was updated every ten minutes. With a thousand computers that tried to solve the problem, the network adjusted the level of complexity so that it became a thousand times higher than at the beginning. Therefore, each participant had about one chance in a thousand to solve the problem and achieve some kind of reward.
I don’t know exactly how much bitcoin was worth at this point in the story, but it began to cost something, even if it was a very small amount. Using a computer twenty-four hours a day is inexpensive in normal conditions when you just surf the Internet, but if you use a computer twenty-four hours a day to solve a mathematical problem, you will see that the processor is used almost 100%. This process increases energy consumption and increases the cost of electricity. People began to calculate the cost of using machines for mining Bitcoin and relate it to the statistical probability of solving a problem over a selected period of time. And from that time on, Bitcoin began to possess some value, even if only because of its rarity, and not because of its usefulness for such a small circle of people.
Then people realized that rather than using an old laptop or PC for computing, it would be more efficient to design computers designed specifically for bitcoin mining, and nothing more. People began to launch not one, not two, but entire computer farms in their apartments and residential premises. These computers mined bitcoins and consumed electricity. Some clever people later realized that GPUs (graphics processors) on video cards were much more productive for solving a specific type of problem proposed in Bitcoin mining, and wrote programs to take advantage of video cards and mine Bitcoins faster.
As you can see, not only has the number of people mining bitcoin increased, but also the number of machines used by these people and the power of these machines. The task for solving every ten minutes was now hundreds of thousands or maybe millions of times more difficult, and a miner with a simple laptop would have very little chance of getting anything.
After the GP mining phase, as it was called, equipment manufacturers began to develop ultra-fast motherboards specifically designed for mining Bitcoin, making GP mining slow and outdated. Today, bitcoin mining is a full-fledged industry with companies investing millions of dollars in bitcoin mining equipment. Today, like using a small paddle for gold mining, you cannot expect to start mining Bitcoin on a home computer and expect to receive money, because this will require extensive resources. Several bitcoin production farms were launched in Iceland, where geothermal electricity provides a cheap source of energy, which is combined with minimum cooling requirements for servers due to low temperatures.
So be it, if you cannot afford the gold mine, you can probably buy some share in it. In a similar way, companies that provide what is called the mining pool are now working. It works in such a way that you join the association of thousands of users who use home computers for bitcoin mining, and are guaranteed to receive a small percentage corresponding to the contribution of your personal computer to the total production - however, do not expect to get rich!
I talked a lot about how bitcoin mining works, and about the history of bitcoin mining, but the bitcoin mining process has two important roles in the bitcoin network in addition to generating new bitcoins for miners. First, in addition to solving mathematical problems, Bitcoin miners also process transactions. In the third chapter, I gave an example of sending 50 XBT to my friend Joe, and this transaction was sent to the Bitcoin network. The data of this transaction reached the set of miners actively mining Bitcoin, and when one of them successfully solved the math problem, he also processed this transaction, along with all the other Bitcoin transactions in the last ten minutes, and included them in the blockchain (Bitcoin account). In other words, these miners perform the necessary function in the bitcoin network: in addition to introducing money into the economy,they provide payment processing functions that allow Bitcoin transactions to work.
There is a third key role played by the mining process. The more miners in the bitcoin network, the more difficult the mathematical task becomes. The more complex the task, the more secure and resistant to fraudulent transactions the network becomes. We will not discuss this moment so far, but will return to it later in this book.
Chapter Five Why use bitcoin
Now that you have an elementary understanding of some of the principles underlying Bitcoin, it's time to consider the advantages of Bitcoin over other types of money and understand how you could use it. Bitcoin is more profitable than ordinary currency in almost all circumstances when an electronic transaction is possible. However, before considering its advantages, it is worth noting the available alternatives. When we talk about alternatives, we not only compare bitcoin with other currencies, such as the dollar, pound or euro, but we also need to consider different types of transactions. The way in which we use money strongly depends on the amounts used, the type of goods and services we buy, and the relative position of participants.
In the simplest case, we use the physical transfer of cash when banknotes or coins pass from hand to hand. Cash transfer works best for amounts from about five cents to thousands of dollars. Obviously, it is possible to transfer large sums, but in most cases people find it more convenient to use other payment methods if the amount exceeds a thousand dollars. As for smaller (than the lower limit) amounts, here we are limited to the smallest denomination of the currency. Cash transfer is of limited use, since both participants must be in the same place.
Bank checks are often used to transfer large amounts between individuals. A bank check usually costs about five dollars, so it's not very economical to use them for amounts less than five hundred dollars. In practice, in most cases, the amount of a bank check is not limited, but it is a rather inconvenient process, requiring both participants to appear in a bank branch, so usually the use of bank checks for transactions is limited to one country. Participants must also meet in person to submit a check, or wait several days until the check is delivered by mail.
For merchants, electronic payments or credit cards are convenient means. This is a relatively expensive option for merchants, as they have to pay in order to create a trading channel with the bank, and also pay the bank a few percent of the amount of each transaction as transaction fees. Moreover, in the case of a refund, when the transaction turns out to be fraudulent, the merchant risks and he must return the money. This is especially true for online merchants, as they only get credit card information, but they don’t see the cards themselves. The possibilities of electronic payments and credit cards are usually limited to ten to ten thousand dollars.
International SWIFT transfers are the main method of transferring money between countries. SWIFT transfers are usually uneconomical for amounts less than a thousand dollars, due to the high fees charged by banks. SWIFT transfers are a very slow form of transaction: the recipient receives payment after a few days. Errors also occur during the translation process, resulting in even greater delays.
I have described some of the most common methods of transferring money between people, but, of course, this is not an exhaustive list. There are also large translation firms like Western Union, as well as a large number of specialized international transfer firms that can send small amounts of money faster and more economically than SWIFT or Western Union. Another group of companies includes PayPal and similar companies that act as a processor and insurer of payments between merchants and banks. And, again, that's not all. You have probably already begun to understand that our understanding of a transaction depends heavily on what we are trying to do and that we have a large variety of loosely coupled systems that have advantages and disadvantages depending on the circumstances.
Let's go back to bitcoin. Bitcoin allows me to send any amount of money anywhere in the world instantly and for free . What other transaction method has such wide coverage?
Let's continue. Bitcoin allows merchants to receive payments without the risk of return. In formulating it differently, if a merchant received a payment in bitcoins, there is no risk that the bank or a third party may later declare this payment fraudulent; Bitcoin payments are final. Of course, sellers and buyers can pay third parties for escrow services if they need it. It is also a boon to shoppers, particularly those who shop online. If you have ever made an online purchase with a credit card, you have to be upset when your card is not accepted, because you are traveling at this point, or making a purchase that the seller considers risky. For example, if you buy equipment for several thousand dollars, the seller may ask you to confirm your identity and address. This is inconvenient and frustrating for both the seller and the buyer, leading to undesirable delays and efforts to process the transaction on both sides. With Bitcoin, transactions are instantaneous, free of charge and pose no risk to the seller.
The benefits are even greater if you are a trader who often deals with international buyers, for example in the tourism industry. Imagine that you are renting a yacht. The buyer orders the boat a week before the holidays. Instead of worrying about transfer fees, getting acquainted with foreign currency and waiting a few days to get the money, you can send a deposit in bitcoins - from anywhere, for free and instantly, in a currency with which both the buyer and the seller are familiar. If renting a yacht turns out to be a secret engagement gift for the bride, it will also not be visible on credit card reports.
Another great advantage of Bitcoin is that a Bitcoin transaction does not require either party to provide important information to the other party. This is exactly the opposite of how credit cards or electronic payments work. Every time you make a purchase in a store using a credit card or electronic payment, you must transfer your card details and a pin code or signature. It is interesting to think about how important it seems to us to hide the pin-code from other people, and at the same time, just as we are ready to enter it into a machine belonging to a complete stranger. Pin-theft devices are known in Australia, but they are much more common in other parts of the world, this is especially true for international travelers. Using bitcoin completely removes this risk. You can shop anywhere in the world, pay any stranger, without worrying about the fact that your data can then be used for fraudulent purposes.
Another example of the circumstances in which bitcoin has significant advantages over other transaction methods is the payment of small amounts. A child may want to go to the store and buy there for ten cents a chocolate or lollipop, or the seller may want to sell a ring tone for a mobile phone for fifty cents online. Without Bitcoin, such small purchases can only be made for cash, since for most other funds it is required that the amount of the payment should cover the transaction fees. Bitcoin provides what is now called “micropayments,” in the case of such small amounts, or even smaller amounts, less than one cent. Moreover, bitcoin is not a credit line, it is the digital equivalent of cash, so you do not need to be an adult to use it.
What about the case of a traveler who urgently needs to send a hundred dollars to his mother in his country? SWIFT transfer will be expensive for both parties and will take several days. Service like Western Union will be faster, but even more expensive. Bitcoin works instantly and for free.
Bitcoin can be sent between participants anonymously. There are no restrictions on this anonymity, we will look at it in more detail in the following chapters, and now it’s enough to say that when I carry out a bitcoin transaction, I don’t need to worry about who will make the payment: the bank or the credit card company that keep the entire history of my purchases. I do not need to reveal my identity to the seller, and there are many valid and reasonable reasons why I would prefer to remain anonymous.
Another great advantage of Bitcoin is that its release is controlled. As we briefly reviewed in the previous chapter, bitcoin is generated through the mining process, and the bitcoin generation rate is controlled by the protocol itself. We will look at this in more detail later, but it can be said that the release of bitcoin is predictable, controlled, and inaccessible for manipulation by an individual, organization or government. We have observed many times throughout history, including recent history, examples of how governments negatively affect the issue of money, generating more money for the sake of their own immediate economic interests. These interests often represent a complete contrast with the interests of the people who hold the currency. We have seen how this can lead to an inflationary spiral that can destroy the entire economy. Bitcoin cannot be the subject of this kind of manipulation, since the release is controlled by the protocol itself, and its volume is known in advance by anyone who uses bitcoin.
Earlier, we said that bitcoin has similarities with cash, but cash is limited when it comes to protection against accidental loss or theft. Bitcoin is also not immune to losses of this kind, but it has many properties that allow people to protect their money from loss or theft. This makes it a much safer option to carry in the back pocket than a wallet full of cash.
Common currency is not intended for e-era. This is a money system that has been used for hundreds, if not thousands, of years, long before the invention of electricity, not to mention the development of computers and the Internet. It has been used since the time when the trade was carried out face to face, when there was not even the thought that it was possible to send a song from one end of the world to another for a small fee between the parties who had never even talked to each other. During the twentieth century, financial institutions adapted their ancient systems to the electronic era and developed new systems that met the requirements of modernity. During the service of these systems, as the requirements of e-commerce expanded, new systems were built on their basis, performing tasks for which they were not originally intended. As a result, we have creaking working banking system, which is not designed for a huge variety of electronic transactions carried out in the world today, and is completely dependent on financial institutions, which derive huge profits from this dependence.
From the very beginning, bitcoin was designed for electronic transactions, and this is his forte. It allows instant electronic transactions from anywhere in the world, for any amount, without having to trust the other party or any dependence on a third party. When digital currencies reach critical mass, our doubts today will seem silly.
Part II. How bitcoin works
Chapter Six Asymmetric keys
At its core, bitcoin is an open protocol. Speaking of "protocol", I mean that bitcoin is a set of rules that bitcoin programs must comply with. By “open,” I mean that a protocol, or a set of rules, is publicly available, and anyone can check them. This protocol allows Bitcoin programs (which we usually call Bitcoin clients) to communicate with each other over the Internet in a standardized way.
Then the first question will be if bitcoin is an open protocol, or a set of rules that keeps people from writing programs that violate the rules. The answer is nothing. Anyone can write a program that uses the bitcoin protocol and communicates with other bitcoin programs via the Internet and tries to “break the rules” in its favor, however, clients that do not comply with the protocol are simply ignored by other clients.
As an analogy, imagine chess players by mail when players are in different places and their moves are sent in letters. Both players know what the entire board looks like, and any one of them can walk as he pleases if his move complies with the chess rules. Otherwise, the other player ignores or rejects this move. The same principle underlies the bitcoin: any of the “players” (bitcoin clients) knows exactly what the “board” (blockchain) looks like, and can independently verify from other sources that any “move” of another (transaction) is correct.
If we want to understand Bitcoin at a deeper level than the analogy, we must understand the idea of asymmetric encryption (also known as public key encryption). Asymmetric encryption is a key element of Bitcoin, and without it, Bitcoin could not exist. The idea of asymmetric encryption is not new, and in fact it is an integral part of the security of many software systems. We use asymmetric encryption every time we visit a secure (SSL) site, for example, an Internet bank site.
Before I explain what asymmetric encryption is, let's imagine such a task. Let's say Alice in Australia wants to send a letter to Bob in England. The content of the letter is a big secret. How can Alice send a letter to Bob without the risk that someone will read this letter on the way? Without asymmetric cryptography, this can only be achieved in the only way that Alice and Bob initially understand how to encode a letter. Then the letter will be encrypted, and Bob will know how to decrypt it when he receives it. But what if Alice and Bob don't have a prearranged key for the cipher; what if Bob had never met Alice before? In such circumstances, without asymmetric encryption, Alice cannot safely send a letter to Bob.
Thus, this leads us to asymmetric cryptography and the way it solves this problem. Some time ago, several talented mathematicians developed a way with which you can generate key pairs mathematically related to each other. In this context, you can think of a key as a very large number — a number with several hundred digits. [6] . These keys are called "public key" and "private key", or together - asymmetric keys. It turns out that these keys have several very useful properties!
Using the public key, you can encrypt the message in such a way that it will be possible to decrypt it only with the private key. Thus, Bob can now generate a pair of keys and transmit his public key to the world, since [7] get his private secret key. If Alice wants to send a secure message to Bob, she simply has to encrypt the contents of her letter with Bob’s public key using a known algorithm, and Bob can decrypt the message with her private key, which he does not reveal to anyone else.
You use asymmetric cryptography technology every day when you use Wi-Fi, Bluetooth, or secure websites where data is encrypted to prevent what is called a man-in-the-middle attack. In other words, asymmetric cryptography is used to prevent anyone else from intercepting your conversation, letter, or transaction.
So now we know how Alice can safely send a letter to Bob, but when Bob gets a letter, how can he be sure that Alice sent the letter and not someone else? It turns out that asymmetric keys can solve this problem. Alice also generates a pair of keys: public and private key. Like Bob, Alice reveals her public key to the world. Alice can digitally sign the contents of the letter using her private key. Then, using Alice’s public key, Bob can determine that the letter was indeed signed by Alice, since no one else can sign the letter without access to Alice’s private key. Thus, only Bob can read Alice’s letter, and Bob can make sure that it was Alice who wrote the letter.
This is a very useful and powerful idea - it still impresses me today, despite its everyday use. You can evaluate its usefulness for military communications, and, in fact, for many years the United States tried to stop the export of programs that use strong asymmetric cryptography.

Now that we understand how asymmetric cryptography works, how does this apply to bitcoin? Remember, in Chapter Three, we made an analogy and said that in some respects bitcoin works on the principle of a checkbook?We said that one user sent bitcoins to the bitcoin address of another user, and that the transaction was signed by the sender of the transaction. This is the point where everything starts to connect: the fact is that the bitcoin address is a derivative of the public key.
Let's look at our original checkbook example in more detail, because now we understand the idea of a public key. I have 50 bitcoins on my mobile phone, and I would like to send them to my friend Jo's mobile phone. First, Joe presses a button on his phone to generate a new bitcoin address. Although, in fact, it creates a pair of asymmetric keys. The private key is stored on Jo's phone, and the derivative of the public key (Bitcoin address) is displayed on the screen and then sent to me. Using Joe’s bitcoin address, I start a transaction on my phone, indicating the amount I want to send to him. Then I sign this transaction with a digital signature using my private key and send the transaction to the Internet. Remember, we said that writing a check is the same as writing a letter to the bank,allowing the bank to allocate funds from my account to the specified person. In the case of bitcoin, the transaction is, in effect, a public announcement of the transfer of control over the XBT 50s, registered to my address, to the bitcoin address I specify. Only my private key allows me to allow bitcoin transfers to Joe's address, and I give this permission when I sign the transaction with a digital signature.
When a transaction is sent, Joe can confirm in the bitcoin network that he has the right to spend these bitcoins - the transaction is final. Of course, despite all these technical steps, all this happens automatically, behind the scenes, by pressing a few buttons on the phone.

Chapter Seven. Hashing
In Chapter Four, we looked at how bitcoins are generated and introduced into the economy. We explained that bitcoins are generated approximately every ten minutes in the course of solving a mathematical problem. In this chapter, we will take a closer look at how this works. To understand bitcoin mining, we need to get acquainted with another idea from computer science: this is hashing, or a cryptographic hash.
Hashing is a very interesting concept, which, like asymmetric cryptography, is one of the key ideas in the field of software security. As we did earlier, let's start with the presentation of the task. If I have a computer system, how could I safely store each user's password in such a way that if the system is compromised, then user passwords will not? In other words, for obvious reasons, it is a bad idea to store a database containing thousands or millions of user passwords.
The solution to this problem includes a cryptographic hash. The hashing process gets something to enter, such as a password, and passes this input through an algorithm that outputs a large number, called a "hash." The hash defines two distinct features. First, for the same input data, the hashing process always returns the same result. For example, if you enter a password that is passed through a hashing algorithm that generates a specific number, the same number will be generated each time. Secondly, hashing is a one-way process. It is impossible to take the value of the hash and, with the help of reverse engineering, reveal what was at the input. These two properties determine the cryptographic hash. If the process were reversible, it would not be called hashing, but good old encryption / decryption,and this is a completely different topic.
It turns out that the process of hashing values has many useful features applied to computer science. One of the tasks we suggested above was the task of storing user passwords securely in the system. Instead of storing the user's password, we first hash his password [8] and store the hash value. When the user tries to log in next time with a password, we don’t need to know what his password was, we only need to know that the password is the same as what was entered last time. In other words, if the hash of the entered password matches the hash stored in the database, we know that the user has entered the correct password - although we do not know and do not want to know what it was for the password. If our system is later compromised, the attacker will only receive a list of password hashes that are irreversible and have no value.
If you are like me, this process will seem fascinating to you, but you will probably ask yourself - if the passwords are hashed, how can it be that if you forget the password for a particular system, then the company can send it to you by email. This is a very good question. This means that passwords are not hashed, and this system is extremely insecure. Sadly, many systems today permit this. This is one of the reasons why you need to use different passwords for each of the systems to which you have access. When it is found in the news that the system has been “hacked” and thousands of passwords have been compromised, this happens because system designers could not ensure the security of user passwords using a hashing technique that is generally considered the best approach.
For the sake of interest, we note that if you forget the password to the system, which properly hashes user passwords, the correct approach is to reset the password by the system when the password is replaced with a temporary value, which allows you to change it to something else when log in. However, it should be noted that such an approach does not guarantee that the system actually hashes the passwords.
Now, how does this all apply to bitcoin mining? Well, we said that reverse hash development is not possible. Technically speaking, theoretically, it is possible through what is called a brute-force attack — going through all the possible input combinations until the same hash is obtained. However, in practice, the number of combinations is astronomically large, which makes such an attack impossible for practical purposes. It should also be noted that different input values may result in the same hash value, this phenomenon is called collision and it happens very rarely if you use the correct hashing algorithm, so for our discussion here it does not matter.
Now let's assume that there are only a million possible hash values, a number between zero and one million. In reality, of course, we know that much more than a million hash values are possible, but let's continue with a million to illustrate my point. Thus, the chances of correctly guessing the correct input for a given hash will be one in a million. Having a sufficient number of attempts and a sufficient time, in the end I will find the initial data, which, after hashing, will give the value that I am trying to find.
Let's assume that the trial and error process takes twenty-four hours to find a match (a modern home computer will do a million iterations in less than a second, but let's leave twenty-four hours for our example). Remembering that in our example we said that all the hash values are numbers between zero and one million, let's assume that instead of finding input data that will give a certain hash value, we would like to find input data that hash numbers give a smaller or equal to 10. That is, we want to find any input that will result in a hash value of 1, 2, 3, 4, 5, 6, 7, 8, 9, or 10. In this case, it is ten times more likely that what we get the hash value will do, so our computer will find a match on average ten times faster - now s take approximately 2.4 hours instead of 24 hours.
If I wanted to create a task that would be solved faster, say, in 10 minutes, I would raise the limit to any hash between 1 and 150. The task is now 150 times simpler than in the first example, and a quick calculation will show that such The problem should be solved by our (slow) computer in about 10 minutes. What happens if the second, equally powerful computer connects to attempts to find a solution to the problem? Now it can be solved twice as fast. If I want the solution to still take 10 minutes, I will have to make the task twice as difficult, setting the condition that the hash value should now be less than 75, not 150. As more and more computers are connected to the problem , and they start solving the problem more efficiently; we make it more complex by setting a smaller range of acceptable hash values.
And, if you still have not guessed, this is the task that the bitcoin network offers to the bitcoin miners. The difference, of course, is that there are far more than a million combinations, the numbers are so large that you can’t call them that easily. All the bitcoin miners in the world, while I am writing this text, collectively process approximately 350,000,000,000,000 input values per second in an attempt to find the same value that hash falls within a certain range of hash values.
The bitcoin network regularly assesses the complexity of the task, and if the task is solved faster or slower than the set interval of 10 minutes, then the task is adjusted accordingly by expanding or reducing the range of acceptable hash values. Of all the computers in the world that are trying to solve a problem, only the first one who decides receives bitcoins "as a reward", and the process begins anew. The next question is then: how does the rest of the bitcoin network confirm that the task was solved, and how are bitcoins generated in this process? The first question is simple. The computer that solved the problem announces this bitcoin network solution, and other computers check the solution. Although reverse engineering the input value for a given range of hash values is a slow process of trial and error, but once a solution is found, it is easy to check.simply by passing the proposed solution through a hashing algorithm and making sure that the resulting hash value falls within the specified range. Then, mined bitcoins are issued to a specific miner address, introducing new bitcoins into the economy. Just as the monarchs in the olden days issued tally for taxes that would never be collected, and banks issued notes for funds that they did not have, the bitcoin network slowly generates new bitcoins. The key difference between bitcoin and other systems, however, is that in all previous systems, the frequency of currency generation was set at the whim of the monarch, the government, the bank, or, in recent times, controlled by the government of the central bank. The frequency of bitcoin generation is set algorithmically, and cannot be the subject of manipulation of market participants - it is predetermined.The frequency of generation is determined by the bitcoin protocol, and decreases with time, until eventually the bitcoins are no longer generated at all. For any date in the past or future, you can calculate the approximate number of bitcoins in circulation.

Fig. 4.
.
Let us briefly take a pause in the previous direction of thought, and turn to decentralization. Decentralization is a relatively recent concept in computer knowledge, which finds more and more applications over the past decade. One of the first examples of decentralization was the peering (P2P) file exchange. Over the past years, there have been many implementations of it, the most common of which is now the network of torrents. If you are unfamiliar with torrents, let me give a brief introduction. The traditional method of downloading files from the Internet is quite simple. One computer (server) stores the file you need, and the other computer (client) requests this file from the server, and the server sends the file to the client. This model still prevails today, and most of the time you spend on the Internet works as described. By the wayThis model is called client-server. However, she has some limitations. One of these limitations is that the file cannot be uploaded faster than the server allows. This is usually not a problem, but what if there are a million people who want to download the same file from the server? The bandwidth of the server is limited, so that this limited channel must be divided between all people downloading the file. By the way, a separate server can not support a million connections, so you need a farm of servers that contain the file, which will lead to high costs for the owner of the servers, or low speed for clients downloading the file.but what if there are a million people who want to download the same file from the server? The bandwidth of the server is limited, so that this limited channel must be divided between all people downloading the file. By the way, a separate server can not support a million connections, so you need a farm of servers that contain the file, which will lead to high costs for the owner of the servers, or low speed for clients downloading the file.but what if there are a million people who want to download the same file from the server? The bandwidth of the server is limited, so that this limited channel must be divided between all people downloading the file. By the way, a separate server can not support a million connections, so you need a farm of servers that contain the file, which will lead to high costs for the owner of the servers, or low speed for clients downloading the file.which will lead to high costs for the owner of the servers, or a small speed for clients downloading the file.which will lead to high costs for the owner of the servers, or a small speed for clients downloading the file.
A distributed peering network can help here. It works like this: let's say I have a file that I want to make available to other people. Using a P2P program, this file is divided into hundreds of parts (the exact size and number of parts depends on many factors). Now people can download a file from my computer one piece at a time, in any order. The bandwidth on my part is not large, so initially it will be rather slow for those few people who try to download this file from my computer. If someone else has received one of the file parts from me, other people can now download this part either from me or from another network member. Over time, more and more people download some parts of the file from my computer, and others from other people's computers, untiluntil the original file is distributed among the computers of many people. If someone comes in and wants to download this file, the program will simultaneously download the file from many different computers, perhaps never connecting to my computer where the file was originally located - in fact, at this point I can turn off my computer altogether , and provided that there is a complete copy of the file on the Internet, people will continue to download it freely. This system proved to be very successful for files in high demand. Recently, we can see that the decentralized approach is used in software products for which it was not originally intended, and the most recent example is the blockchain.If someone comes in and wants to download this file, the program will simultaneously download the file from many different computers, perhaps never connecting to my computer where the file was originally located - in fact, at this point I can turn off my computer altogether , and provided that there is a complete copy of the file on the Internet, people will continue to download it freely. This system proved to be very successful for files in high demand. Recently, we can see that the decentralized approach is used in software products for which it was not originally intended, and the most recent example is the blockchain.If someone comes in and wants to download this file, the program will simultaneously download the file from many different computers, perhaps never connecting to my computer where the file was originally located - in fact, at this point I can turn off my computer altogether , and provided that there is a complete copy of the file on the Internet, people will continue to download it freely. This system proved to be very successful for files in high demand. Recently, we can see that the decentralized approach is used in software products for which it was not originally intended, and the most recent example is the blockchain.where the file was originally located - in essence, at this moment I can turn off my computer altogether, and provided that there is a complete copy of the file on the Internet, people will continue to download it freely. This system proved to be very successful for files in high demand. Recently, we can see that the decentralized approach is used in software products for which it was not originally intended, and the most recent example is the blockchain.where the file was originally located - in essence, at this moment I can turn off my computer altogether, and provided that there is a complete copy of the file on the Internet, people will continue to download it freely. This system proved to be very successful for files in high demand. Recently, we can see that the decentralized approach is used in software products for which it was not originally intended, and the most recent example is the blockchain.that the decentralized approach is used in software products for which it was not originally intended, and the most recent example is the blockchain.that the decentralized approach is used in software products for which it was not originally intended, and the most recent example is the blockchain.
Chapter Nine. Blockchain
We reviewed and discussed the three basic computer science ideas underlying bitcoin: asymmetric cryptography, cryptographic hash, and peer-to-peer networks. Although these ideas are interesting, they are not revolutionary in the context of Bitcoin. All these things have been used in various ways for a long time. However, what binds them together is a fundamentally new idea, which is the basis of Bitcoin. This idea is known as blockchain.
Blockchain is a decentralized open ledger: let's try to figure it out. In the case of a regular business, or better said, a bank, a ledger is a record set that contains details of user transactions and account balances. In modern banks, these records are stored in large software systems. As you can probably guess, these are large, resilient systems that must be supported by millions of users who perform millions of transactions daily. You may already be familiar with some of the symptoms of the difficulties experienced by banks with reliable management of such large data sets. For example, you could not download the transaction history from an Internet portal of your bank before a certain period in the past. Or perhaps you noticed that some transactions did not immediately appear in the history,until they are processed at night. All these and other similar oddities are the trade-offs necessary for banks to manage these (often ancient) systems containing huge amounts of data.
We said that the blockchain is a decentralized open ledger. We know what a ledger is: a set of records containing details of user transactions and account balances. Now let's explain what we mean by "decentralized" and "open." Unlike a bank, this ledger is not stored on a central server controlled by any person or organization. Blockchain-ledger is available publicly and is stored locally by a multitude of clients, it can be freely downloaded from the Internet. It may be hard to believe, but you got it right: the whole history of any Bitcoin transactions made by anyone around the world since the very beginning of Bitcoin (January 12, 2009) is publicly available for viewing to any person, besides, on most computers or Notebooks, where there are bitcoin programs, are stored copies of this ledger.You probably have a lot of questions, such as how this is possible, or why this is generally a good idea. Let's start with how this is possible. Of course, this is a large amount of data, but not impossibly large. Financial records take up very little space, and looking objectively, all records of bitcoin transactions from the very beginning at the time of this writing take up the same amount of space as a dozen, or so, movies in HD quality. If you download a bitcoin client that stores a local copy of the blockchain, it will take a long time to start the first time you start it, because it downloads a full copy of the blockchain. Another thing is that storing a full copy of the blockchain on all computers in the world is not absolutely necessary. This is definitely not possible on mobile devices, and now in the trend of bitcoin clients,which store only important things locally, not the whole blockchain. Nevertheless, this illustrates my assertion that the blockchain is publicly available to the whole world, and in fact there are many sites that make it easier to navigate through the history of all Bitcoin transactions made by anyone and anytime.
You may be somewhat disturbed by the moment that if you use bitcoin, the entire history of the transactions you have ever made will be publicly available. This is only partially true, and we will discuss this point later in the chapter on anonymity. A public ledger contains only bitcoin addresses and amounts. It does not contain any personal or identifiable information. In other words, if I send 50 bitcoins from address A to my friend Joe with address B, the whole world sees that 50 bitcoins are sent from address A to address B, but nobody can determine that address A belongs to me and address B belongs to Joe. So when I look at the blockchain, all I see is the balances of addresses and transactions from one address to another - none of this information compromises the confidentiality of the people carrying out these transactions.
Another point that needs to be understood, and which we have not yet discussed, is that, unlike email, where you can only have one address, or at least a small number of addresses, the number of Bitcoin addresses that can be in person, not limited. In fact, this is encouraged, and most Bitcoin clients are configured by default so that each transaction uses the new address. Let's look again at the example of sending 50 bitcoins to my friend Joe, now we already know a little more. When I ask Joe to tell me his bitcoin address, he, as a rule, does not give me an address containing the full amount of his wealth, but creates an absolutely new address with no bitcoins at all, and I send 50 bitcoins to this new address.Bitcoin programs do not require you to manage the balance of each address individually; they can show you the total balance of all addresses that you have ever created. If you look at my case, I hardly have an address containing the exact amount of money I want to send to Joe. For example, I may have a bitcoin address A, which has 30 bitcoins, and a bitcoin address B, with 35 bitcoins. In our example, the program will automatically generate a transaction that will take 30 bitcoins from address A, then 20 from address B, send these 50 bitcoins to Joe's address, and also send the remaining 15 bitcoins to the new address B, which she automatically generated for me. Both Joe and I may have hundreds or thousands of addresses containing small amounts of money, which together make up our complete bitcoin state.None of us can see the addresses of the other, except those used in the transaction.
The exception to this rule is the case when I receive one transaction for a large amount of money, say, a million dollars in bitcoins. If after that I want to spend 1 bitcoin from this address, the recipient will be able to see that I have about a million dollars in Bitcoins at my disposal, which I would not want to disclose. Suffice it to say that for the lucky ones who find themselves in this position, there are techniques to hide this wealth, throwing money at many addresses - modern programs make this process trivial.
Now that we know what a blockchain is, how does it actually work? The question is perhaps worth formulating as follows: how can we ensure a consistent record of transactions in a decentralized environment? The first thing to understand about the blockchain is that it is called a blockchain because it consists of a chain of consecutive blocks. A block is a group of transactions. Guess how often blocks are generated? About once every 10 minutes. Probably, you started to understand that there is a connection between the blockchain and bitcoin mining, and if you assumed that, you are right.
Chapter Ten. Bitcoin mining
Remember, in Chapter Four we said that bitcoin mining, in addition to introducing bitcoins into the economy, also has two other goals. It provides payment processing and network security. Let's now look at how these tasks are performed during the bitcoin mining process. We mentioned above that when a transaction is initiated, it is sent to the Bitcoin network. What does this really mean? Bitcoin clients (i.e. programs) try to connect with many other bitcoin clients called peers. Usually each individual client is connected to 10-20 other peers. Some of these peers are regular transaction users, and a small number of these peers may be miners. When a bitcoin client receives information about a bitcoin transaction, it is transmitted from the client to the client untiluntil after a short period of time will not be received by one or several bitcoin miners.
Bitcoin miners do one more thing besides solving the hash problem and introducing bitcoins into the economy: they provide an important blockchain creation function, one block at a time. When a bitcoin miner receives information about a transaction, its authenticity is first checked, and then it is recorded in a block locally, on a bitcoin miner computer. If the bitcoin miner has successfully solved the problem, the solution of the problem is included in the block as part of it, along with all transactions created in the past 10 minutes. Then the block is closed and distributed over the Internet, and the process begins anew. Anyone else on the network can independently verify that the transactions in the block are genuine and that the solution to the hash problem, also known as “proof of work,” is true. Any subsequent miners who have solved the problem are ignored, their blocks no longer fit, and the process begins anew.Thus, a blockchain is a sequence of blocks containing transactions over a given ten-minute period. Each block is mathematically connected with the previous block, so you can trivially (for the computer!) Check the entire blockchain for authenticity without analyzing individual transactions.
And that brings us to the third goal bitcoin miners reach: network security. The actions taken to solve a cryptographic hash problem serve not only the interests of the miner, they are also needed to protect against dishonest miners who spend money twice, which is called "double waste". If you take an earlier example where I send 50 bitcoins to Joe, have Joe send me the book I bought from him instead (at today's prices it would be a rather expensive book). At the same time, what if I try to send the same 50 bitcoins to another person, before the first transaction has become processed and verified? Assuming that I have already received the goods from Joe, it will be problematic if the bitcoin network somehow accepts my payment to another participant and later rejects the initial payment that I sent to Joe.Bitcoin's decentralized mining solves this problem.
When I send a transaction for Joe to the bitcoin network, Joe will be able to see it almost instantly (usually after a few seconds). At this time, the transaction is visible, but not yet included in the block by the miner. If it is a transaction with a small amount, or a transaction between participants who trust each other, the visibility of the transaction on the network will usually be considered acceptable, however, with some effort on my part, it is still possible to spend money twice by sending another transaction to the network that uses the same means — but for transactions with a small amount, the effort required will probably not be worth the time spent (besides, of course, there is also the risk of being caught). After about 10 minutes, we can expect that my transaction will now officially be included in the bitcoin miner in the last blockchain block.At this point, the transaction has "one confirmation". Now, if you take into account that there are thousands of special Bitcoin-producing computers in the world, the likelihood that I will be able to deceive Joe and spend my money twice and successfully get the unit that will reject the transaction for Joe is very small. For transactions with medium or large amounts, it is usually considered prudent to wait for 3-6 confirmations, or, in other words, to wait for 3-6 consecutive blocks (from 30 to 60 minutes) to be obtained to be absolutely sure of the transaction. To successfully carry out double waste, in this case it will be necessary to successfully extract 6 blocks in a row that reject the transaction. And to achieve this, you need to control about 50% of the total computing power of the Bitcoin network. As you can see,this makes the double waste attempt extremely difficult and expensive, which primarily outweighs, in general, any benefits of double waste. You can also see that as the Bitcoin network grows, the number of miners increases and the difficulty of the hash problem increases, double waste becomes even more difficult for a dishonest miner. This is how bitcoin miners ensure network security.
In summary, bitcoin mining provides three things: transaction processing, network security, and the entry of bitcoins into the economy. This is an elegant system.
Chapter Eleven. Miner's stimulus
It is time to point out the fact that the miner has a choice whether to include the transaction in the block or not. The miner can reject all transactions if he wants, and just solve the hash problem. This is called “empty block mining” and happens from time to time. Then the question is, why should Miner even bother to include transactions in the block? There are several reasons. First, compared with the work that the miner does when trying to solve the hash problem, the inclusion of transactions in the block is a trivial operation that requires almost nothing from his computer. Secondly, transactions are included in the blockchain in the interests of the bitcoin community. If miners do not include transactions in the blockchain, bitcoin will not work, and if it does not work, then bitcoins will not cost anything. If bitcoin doesn't cost anything,then the miners will spend all their efforts on getting something that costs nothing. You may argue that it is good for the community that miners include transactions in the block, but for an individual miner it is unprofitable to spend resources on processing transactions. This is partly true, but, as I noted at the beginning of the paragraph, the necessary effort is negligible. There is also a third point. Miners can not take a commission for the inclusion of a transaction in the block, but the people carrying out the transaction may voluntarily offer a commission. Miners can then reject transactions that do not include a commission at all, or reject transactions with a commission below a certain value. What is the usual commission today? In most cases, it is zero. In today's economy, the miner’s stimulus is primarily Bitcoin, which he receives for a successfully mined block.Transactions are included in the block on the goodwill of the miners in the interests of the growth of Bitcoin-economy and the growth of Bitcoin. In some cases, Bitcoin clients automatically include a small commission (no more than a few cents) to make sure that the transactions will not be rejected by the miners and are more likely to be included in the next mined block.
Over time, the number of bitcoins received for a successfully mined block will gradually decrease until, around the year 2140, the reward for mining the block is zero. It is expected that over this long period of time, until the block reward as a stimulus for mining Bitcoin gradually decreases, this incentive will gradually be partially replaced and, eventually, will be superseded by the incentive in the form of transaction fees.
Due to the fact that the bitcoin economy is an open market, and that transaction fees are voluntary, the value of the commission will always be determined by supply and demand, which will create a competitive market with low transaction fees.
Chapter Twelve. TL; DR
TL; DR: well-known slang term meaning “too long; do not read". This is a short summary at the end of a long text containing its abbreviated version. However, unfortunately, if you opened this chapter without reading the previous chapters of the second part, where the key principles of computer science underlying the bitcoin are described in general terms, then it will be difficult for you to understand this chapter, and in your understanding of bitcoin you will remain at the level of comparisons by analogy. If you read Part II, then this chapter is needed to bring all these ideas together into a clear understanding of Bitcoin.
First, we learned that asymmetric cryptography is the technology underlying private and public keys; using this relationship, we can mathematically check the validity of a bitcoin transaction signed with the sender's private key. Then we learned about a cryptographic hash, which is an irreversible algorithm applied to some data. By trial and error (more quadrillion attempts per second) miners in the bitcoin network are trying to calculate a cryptographic hash for random data until the resulting hash value falls into a predefined range - a task designed to solve on average ten minutes the whole bitcoin network. The difficulty of this task on the one hand protects the network from "double spending", and on the other hand controls the delivery of bitcoin. In addition, bitcoin miners also process transactions that form a block. If the miner successfully extracts the block (by solving a cryptographic hash problem), this block will be recognized by the bitcoin network and permanently included in the blockchain - an open decentralized bitcoin ledger. This is the shortest description of how this complex and elegant system works.
Part III. Broader view
Chapter Thirteen Mt Gox
If you didn’t know anything about bitcoin before reading this book, you could still hear the title “Mt. Gox 'thanks to the mainstream media. Mt Gox made up an interesting bitcoin story, so it’s worth figuring out what happened. Mt Gox is a bankrupt Japanese bitcoin exchange launched by a Frenchman named Marc Karpeles.
Until 2013, bitcoin was little known outside the handful of people scattered around the world. Then he had not yet become mainstream and was not the subject of discussion by the governments of large states. If at that time you wanted to buy bitcoin, you had a very limited choice. In those years, Mt. Gox was unconditionally the largest bitcoin exchanger in the world, claiming to hold more than 80% of the bitcoin trading market. I think this was close to the truth, because at that time there were few alternatives.
Since Mt. Gox controlled the vast majority of bitcoin trades, and most people understood very little about bitcoin, the name “Mt. Gox ”has become almost synonymous with bitcoin as such. By the way, there is a famous story about why Mt. Gox became known as “Mt. Gox. " Apparently, when the site was created, the original owner had already bought the domain name mtgox .com for another project, on which he worked, related to the card game Magic: The Gathering. Therefore, the domain name meant “Magic The Gathering Online eXchange”. He later abandoned the idea of this site, and the domain name was used for the Bitcoin exchange, known as “Mt. Gox. " After some time, the first owner sold most of his company to Mark Carpeles.
Now I think in the early days of Mt. Gox, perhaps, no one imagined that the site would grow so much - maybe yes, but I doubt that they could suggest an incredible increase in Bitcoin in early 2013. For various reasons, bitcoin began to flourish, withdrawing the price of one bitcoin from about 10 to about 250 dollars in just a few months. Subsequently, the price rose to almost $ 1,000 by the end of the year. And where did people go to buy bitcoin? One of the few places where they could do this was the Mt. Gox.
I want to emphasize that I have no insider information about what Mt. did or did not do. Gox; I know about Mt. Gox only as their client, as well as from discussions with industry colleagues. In early 2013, my business partner Adrian and I used Mt. Gox to buy bitcoin. Since we have been developing software systems for financial institutions for most of our careers, Mt. Gox seemed to us unprofessional and amateurish. It took them several weeks to open and verify our accounts, their customer service worked poorly, and the site has not been updated for a long time. In addition, there were stories of failures of Mt. Gox under a relatively large load and reports that they were “hacked” and people lost money. It was definitely a type of financial system that I would not trust my money to. At the same time we were going to buy bitcoin. Our strategy was as follows: we deposited relatively small amounts of money, bought bitcoin, immediately took it out, and repeated this cycle again. Thus, in case of any problems with Mt. Gox our losses would be limited to the amount of the last deposit. Unfortunately for many other Mt. Gox, they did not use a similar approach. By mid-2013, it became apparent that Mt. Gox troubles because they suspended the withdrawal of money, and shortly thereafter, the company declared bankruptcy, recognizing the loss of almost all the bitcoins they stored for customers, which at the time of their bankruptcy was about half a billion US dollars, or about 7% of all bitcoins in circulation.
On any scale, this event was a disaster for Bitcoin as a whole. This was a disaster for everyone who had a Bitcoin account, and a disaster for the Bitcoin reputation, which many saw as a failure by itself due to the poor management of Mt. Gox. I do not know why Mt. Gox lost money. In one of their ads, they suspected that the money was stolen, but ultimately it was just speculation on how it happened - the point is that people lost a lot of money because of this.
Regretting those affected by the collapse of Mt. Gox, it should be noted that the announcement of their bankruptcy was in some way desirable. Their delays and the suspension of withdrawals, which lasted for many months, caused new problems for the bitcoin community and a very bad press reputation. Mt Gox was a ticking time bomb. Their collapse allowed other companies to start from scratch, much more reliable than Mt. Gox, and lead bitcoin ahead.
You may also notice that to some extent it is the poorly organized platform Mt. Gox led us to the idea of creating our own Bitcoin exchange, Independent Reserve. We knew that in order for bitcoin to ultimately be successful, we needed a stable, stable platform from which people can buy bitcoin, and Mt. Gox is not.
Chapter Fourteen. Silkroad
If you have not heard of the collapse of Mt. Gox in 2014, you may have heard of Silkroad. By the way, the name “Silk Road” originally refers to the sequence of trade routes that connected Asia and Europe over many periods of history. They were called so because of the profitable trade in Chinese silk, carried out along the paths, and significantly contributed to the development of trade between the two parts of the world.
The Silk Road, of which we speak, however, was a site of a special type. It was special because it did not have access from a regular browser. It could only be accessed using a special program called Tor. [9] , which made the user anonymous, allowing people to enter the site so that they could not be traced. Silkroad was essentially a marketplace where you could buy and sell goods. Due to the fact that it was set up with a clear goal to anonymize users, the products for sale were mostly black market items that were not on regular sites where authorities could track activity. Therefore, the predominant types of products available on Silkroad were illicit drugs, prescription drugs, firearms and other illegal goods.
Silkroad used bitcoin as a currency because bitcoin could be transferred between market participants anonymously. [10] . Unfortunately, this worsened the bitcoin's reputation, since the media made the false conclusion that since Silkroad uses bitcoin as currency, then all users of bitcoin are pirates and traffickers from Silkroad. In October 2013, the FBI was able to track down the site administrators, and the site was stopped [11] . What happened to the bitcoin price? There was a slight recession, and then it continued to grow. The reason for this is that the vast majority of Bitcoin users were not pirates and drug dealers, and the fact that Bitcoin continued to grow, despite the lack of Silkroad, is proof of that.
From this we can learn a few lessons. Firstly, all currencies are used to a certain extent and will be used for illegal purposes - this is proof of their suitability as a currency. In November 2013, in response to a request from the United States Senate, the Agency for Combating Financial Crimes emphasized that any illegal use of bitcoin is insignificant compared to $ 1.6 trillion of “global criminal income” in 1999.
It is also worth noting that any transactions carried out on Silkroad between anonymous participants, at least, did not lead to an increase in violence in society, as opposed to violence, which is sometimes associated with cash transactions carried out on the street.
Chapter Fifteen. Other digital currencies
Bitcoin is not the only digital currency, although it was the first and most successful internationally, and has an overwhelming market share (98%) in terms of capitalization compared to other digital currencies. Bitcoin first earned in 2009, and until 2011 there were no alternative digital currencies, like Lightcoin, which is largely a bitcoin clone with minor changes to several settings.
I believe that the developers of some of these early currencies had good intentions, but today there are over 500 “alternative Bitcoin” digital currencies in the world that most people (including me) have never heard of, and I believe that a good part of them, is nothing more than a scheme designed to bring profit to the developer.
Another thing is that, even though Bitcoin has become a huge evolutionary step in the history of money, it is still imperfect, and it is inevitable that the Bitcoin protocol will improve over time (as it already happened), and that potentially new digital currencies can be viable at the same time with bitcoin, or eventually replace bitcoin. The blockchain idea is essentially robust, and most digital currencies, if not all, are based on the same basic principles as bitcoin.
Chapter Sixteen. How to secure your bitcoin
We have already mentioned that bitcoin and physical money have common properties. However, bitcoin has a number of features that allow you to protect it from accidental loss or theft in a manner unreachable for ordinary money.
For starters, you can backup your wallet. This means exactly what is said: just as you make backup copies of photos or letters, you can create a copy of your digital wallet and store it in different places. This is the easiest way to protect your bitcoins from accidental loss. If you lose your phone with a bitcoin wallet, or if the computer disk fails, you can restore all your money from a backup. Even better, you don’t even need to make a backup after each transaction. Most modern bitcoin wallets are designed in such a way that if you made a copy, even if there were no funds at the time when the copy was made - money received in the future will still be restored, so you need to backup the wallet only once. Some wallets are designed so that you can even generate new addresses, and still enough to copy the wallet only once [12] .
Backups protect your wallet from accidental data loss, but they do not protect you from thieves. However, wallets are easily encrypted and can be password protected. Then, if someone steals your bitcoin wallet on it, he will not be able to spend it without your password. In the meantime, you can restore your wallet from a backup and transfer money to a new wallet for security. Then, even if the thieves can guess your password, bitcoins will already be sent to the new address, and your old wallet will become absolutely useless for them. All these things do not require the possession of special skills, they are usually part of most bitcoin programs and they are very easy to use even for a beginner.
These features are great for protecting funds in reasonable amounts; however, when dealing with large amounts of bitcoins, say, equivalent to a million dollars, we may want to take extra precautions. After all, what if an attacker gains access to our computer and installs a spy program that secretly records the passwords that you typed? History shows that there is no limit to the cunning and dishonest techniques that thieves can invent when it comes to stealing money. Suffice it to recall some well-known casino robberies in Las Vegas and things people went to when large sums of money were at stake. However, bitcoin provides great opportunities when it comes to security. One of the ways to protect a large amount of bitcoins is called freezing. The idea of freezing in this context means storing bitcoins on a computer or other device that is not connected to the Internet. A computer or mobile phone connected to the Internet can potentially be hacked by anyone from anywhere in the world if a vulnerability is found. But storing bitcoins on a computer that is not connected to the Internet, you immediately limit potential threats to only those that come from people who have physical access to this computer. Of course, the wallet on this computer must be encrypted and protected with a strong password. Modern programs easily provide the ability to store bitcoins in the freeze.
Bitcoin has even more advanced security features, such as “multi-signature” addresses (in common parlance known as “multisig” addresses). In all the examples we have given so far, we have described how I send 50 bitcoins to my friend Joe in a transaction signed with the corresponding private key that I have. In the case of multisig addresses, the transaction can be configured in such a way that two different people, or three people, or two out of three people, or any combination of signatures you can present, will be needed for the signature. For example, you may have a bitcoin wallet that requires both signatures — yours and your business partner — to send a transaction, or just one of the signatures. Or perhaps you have a board of directors, and the transaction should be signed by any three of the seven directors. These are very powerful tools that allow Bitcoin to be secured in ways inaccessible to physical money.
The last bitcoin wallet security method we’re talking about is called a “paper wallet”, and this is the most primitive of all bitcoin security devices. You can simply print your private key on paper, and in the case of an EMP [13] , which destroys all your electronic devices, you can recover funds using a printed private key. Of course, you can go even further, and print half of the private key on one sheet, and the other half - on the other, and store them in various safe places - the possibilities are endless.
Chapter Seventeen. Smart contracts
So far in this book, we have discussed the most common and simple type of transaction - participant A sends money to participant B. We looked at how this process is carried out using bitcoin, as well as some of the great advantages of bitcoin compared to a regular currency. However, using this example, we barely scratched the surface of what bitcoin and blockchain technology can really achieve. We introduce the idea of "smart contracts". Bitcoin is able to create complex transactions involving many participants. Let's take an example.
Let, say, a car manufacturer makes a new car. In the process of its creation, a new bitcoin address is generated, to which the symbolic sum of bitcoins (i.e., 0.0001) is deposited, and this transaction is recorded in the blockchain. The manufacturer assigns this public address to the machine. The private key is then issued to the seller, who can store it on his mobile phone, so that his phone also serves as a car key, allowing him to open and start the car.
When the seller is going to sell the car to the buyer, the transaction is recorded in such a way that the money is transferred to the seller, and the car is transferred to the buyer as an address to which he can access from a mobile phone. Both participants must sign a transaction so that it becomes valid and is included in the blockchain. When the transaction is completed, the buyer can “present” his phone to the machine via NFC [14] , and the car recognizes the new owner and turns on the ignition. In this example, a transaction between two participants occurs at the same time, and thus, neither participant should trust the other. Moreover, the buyer can review the entire transaction history for the machine on the blockchain to make sure that it is real and make sure that the seller really owns the car.
Let's expand on this example. What if the buyer cannot afford to buy a car, and he needs to borrow money to make a purchase. A bitcoin transaction can be built in such a way that the creditor has ownership of the car until either the agreed amount is paid to him within a certain period of time, and then the car is transferred to the debtor, or the debtor loses the security, and the creditor remains the owner of the car .
The idea of a multilateral agreement is not new, banks borrowed money at all times. However, when using bitcoin and blockchain technology, the process becomes much more efficient, and participants need to trust each other to a lesser extent in order to fulfill the terms of the contract, which are automatically respected by the bitcoin network. It is interesting to see what new possibilities of using bitcoin and blockchain people will open tomorrow.
Chapter Eighteen. Anonymity
One of the big questions that has arisen about Bitcoin is whether transactions are anonymous and, if they are anonymous, whether bitcoin will not contribute to money laundering and other crimes. The answer here is both yes and no. Let's look at this question more closely.
Suppose, say, I buy something big worth millions of dollars from a stranger to me, and he gives me a new bitcoin address to which I have to transfer 10,000 bitcoins. At this point, the transaction is anonymous. Assuming that another participant generated a completely new address, I cannot determine who he is, and no one can associate the receipt of 10,000 bitcoins with this person. If this person keeps these funds and never spends them, he will remain anonymous. At some point, however, a stranger will most likely want to spend his 10,000 bitcoins, or perhaps exchange them for fiat currency. [15] . Now, if our stranger finds another stranger on the street and sells his 10,000 bitcoins for a million dollars in cash, everything will still be quite anonymous. However, usually, especially in the case of large sums, this person will need to spend this money with the help of a legitimate business or exchange it in a trustworthy exchanger. At these points, in particular during currency exchange, in the process of opening an account, a strict identity check is required to comply with AML / CTF standards. [16] , applied in the traditional financial sector. As soon as money begins to be spent through the usual channels, it becomes possible for the researcher to connect the dots and trace the transaction history. So, is Bitcoin anonymous? It can be as much as cash is anonymous. Cash may also be anonymous, but if one day you come to the bank with a million dollars in cash, authorities may raise their eyebrows in surprise.
Chapter Nineteen. Regulation
Many world governments are now asking themselves whether bitcoin should be considered legal tender, and if so, should it be regulated, and if so, to what extent.
In my opinion, the answer is that bitcoin needs balanced and well-thought-out regulation. Regulation that does not overwhelm a new industry, but at the same time protects consumers from unlawful actions. Another point to take into account is that we cannot take yesterday's laws, applied to a completely different financial paradigm, and use them for bitcoin. Bitcoin works in a way fundamentally different from ordinary currency, and it is necessary to develop such a regulation that supports a decentralized digital model.
Then the question arises of how this regulation should look like? I believe that it is absolutely necessary to allow Bitcoin and other digital currencies as legal means of payment; the idea of a currency issued by a state may one day be a relic of the past. Governments and economies should use this new world currency and watch how trade flourishes, as people can conduct transactions around the world in the blink of an eye, without delay due to outdated and creaking banking systems. Even without taking Bitcoin into account, as a software developer who spent many years creating programs for financial institutions, I can say that most of the systems I saw are really ancient. These are large computers, created over thirty years ago,who need special (really old) engineers to service them. This is one of the reasons why banks are slowly adopting new technologies, because their systems are not ready for renewal.
The adoption of Bitcoin can lead to an increase in trade around the world, perhaps even removing entire states from poverty, turning them into flourishing economies.
Where, in my opinion, regulation is necessaryso it is in financial institutions storing bitcoin for other people, like banks. We have already witnessed the first great financial collapse of Bitcoin with the fall of Mt. Gox, and no later than a week before I write these lines, we saw how Bitstamp, the European bitcoin exchange, lost five million dollars to bitcoins from its digital storage. To their credit, most of their funds were kept safely in a freeze, and they replenished the balance of account holders. This emphasizes, however, that without some oversight of the security measures that these organizations undertake, consumers will not be able to trust the institutions responsible for storing their bitcoins.
It is important to emphasize that this is not a bitcoin vulnerability in itself, it is only a sign of the immaturity of the bitcoin financial sector. In the twelve months since Mt. Gox, we could see how the whole industry is taking big steps to improve security, and will undoubtedly continue to do so. Bitcoin’s strong, stable and secure financial sector is in everyone’s interest — and a balanced level of regulatory oversight in this area will not bring anything wrong.
For regulators, it is important to remember that since bitcoin is a new industry, it moves in very fast steps, and new methods develop all the time. It would be a step back for regulators if, with a limited understanding of a developing industry, they would require something impossible to execute instructions, or create instructions that are harmful for Bitcoin growth. The best move for them at the moment will be to stay a step behind and observe carefully, taking the necessary steps as the industry matures. This principle probably applies to many areas.
Chapter Twenty. Chronology
Many events have significantly changed the face of Bitcoin, from the initial starting point at the end of 2008, to the flourishing industry that it has become now. The following are some of the key points in this chronology.
October 2008. An anonymous article has been published entitled “Bitcoin: a peer-to-peer electronic money system,” essentially describing what bitcoin has become. The article was published by a person using the pseudonym Satoshi Nakamoto .
January 2009.The first blockchain block, also called the genesis block, was extracted, version 0.1 of the bitcoin program (including the source code) became publicly available. The program was written anonymously, and because of a rather non-standard programming style, combined with rigorous theoretical know-how and completeness, speculations about whether it was written by an academic with little programming experience or perhaps a team of such people have been popular for a long time.
Then, on January 12, 2009 , the first bitcoin transaction occurred - from Satoshi Nakamoto to Hel Finney
October 2009.The New Liberty Standard website published a bitcoin exchange rate that seemed to be appropriate for it at that time, based on a formula that included the cost of electricity needed to operate a bitcoin computer. Their proposed exchange rate was USD 1 = XBT 1309.03.
February 2010. There was the first bitcoin exchange called “The Bitcoin Market”. This exchange did not last long, and was closed due to problems with fraud a little over a year later.
May 2010. A US programmer named Laszlo bought some pizzas at Jercos for 10,000 bitcoins. The price of pizza was $ 25 (the equivalent of a bitcoin price of $ 0.0025).
July 2010.Bitcoin was mentioned on Slashdot’s famous IT website, which caused a tenfold increase in price in less than a week. The price rose from $ 0.008 to $ 0.08. That same month, Jed McCaleb launched Mt. Gox, having read about Bitcoin on Slashdot. Interestingly, Jed McCaleb said later in 2011 after selling Mt. Gox:
« I created Mt . Gox for fun, after reading about bitcoin last summer. It was fun and fun to do. I'm still convinced that bitcoin has a beautiful future. But to really make Mt . Gox as it may be, takes more time than I have now. So I decided to pass the baton to someone who has more opportunities to take the site to the next level. "
In other words, McCaleb worked on Mt. Gox alone for a few weeks or months in his spare time - everything worked out because he had a hobby and bitcoin did not have real value at the time. He recognized this fact at the moment when he sold the site. Compare this with a modern stock exchange, such as Independent Reserve, which was developed by a team of professional programmers for more than 18 months, including measures provided for in the system to ensure its security, scalability, stability and reliability. It is not surprising that without extensive processing of Mt. Gox was not able to support the multi-million dollar industry in the future.
Another interesting thing that happened in July 2010 was that this month someone came up with a way to use the GPU (graphics processor) to extract bitcoin faster than was possible using the usual production method on the central processor.
The global frequency of processing hashes by the bitcoin network has now reached 1 gigachesh (GH), or 1,000,000,000 (1 billion) hashes per second.
August 2010A bitcoin protocol was discovered and then exploited. This led to the creation of more than 184 billion bitcoins generated in a single transaction. Within hours, the problem was discovered and the vulnerability fixed. The transaction history from this transaction has been permanently deleted. It was the only major security flaw found and used in the entire history of Bitcoin.
November 2010. The capitalization of the bitcoin market for the first time exceeded one million US dollars. Bitcoin price on Mt. Gox reached 50 cents.
December 2010. The global frequency of processing hashes bitcoin network for the first time exceeded 100 GH.
February 2011.Silkroad has opened, a networked black market that uses bitcoin as a form of payment. In the same month, the bitcoin rate on Mt. Gox first reached parity with the dollar.
March 2011. Jed McCaleb sold Mt. Gox to Mark Carpeles.
April 2011. Traditional media has written about bitcoin for the first time, TIME has published an article entitled “Online currency can challenge governments and banks.”
June 2011. Bitcoin price on Mt. Gox for the first time exceeded 10 dollars. That same month, Mt. Gox began to show signs of problems, a serious security breach was found in their system, leading to the compromising of personal data of more than 60,000 users, as well as fraudulent requests for hundreds of thousands of bitcoins, which caused a sharp drop in prices to 1 cent.
In June, the largest Bitcoin theft occurred in history. 25,000,000 bitcoins worth more than a quarter of a million US dollars were stolen.
In the same month, WikiLeaks began accepting donations in bitcoins.
July 2011. Just a month after the security problems of Mt. Gox Polish bitcoin exchange, at that time the third largest in the world, lost 17,000 bitcoins of its customers.
August 2011 Another bitcoin company that processed bitcoin transactions lost more than 150,000 bitcoins worth more than $ 2 million at that time.
At that time, many such incidents happened. As you can see, it was an unpleasant story for Bitcoin, so it’s worth taking time to analyze what “loss” means and why it continued to happen. It should be noted that in all these cases (excluding the vulnerability discovered in August 2010), the problem was not in Bitcoin itself, but in the incompetence of the people managing the companies that were charged with storing bitcoins for other people. At that time, as much as now, these companies were not regulated at all, but people trusted them bitcoins for millions of dollars.
At the heart of the bitcoin wallet, which stores someone's bitcoin, is a file or a set of files on your computer. To protect these files, you need to backup them and encrypt them as described in the chapter “How to secure your bitcoin”. The organization responsible for bitcoins worth millions of dollars in essence should perform the same task, but the methods used should be some kind of more reliable (compare the protection of money in your wallet with the bank vault, with gold in Fort Knox - as responsibility increases, the level of security should also increase). If the files in which the private keys for the bitcoin wallet are stored are damaged or changed (for example, due to a hardware failure), or the thief got access to the computer and stole the files, then the bitcoins are lost.
There are fewer such security incidents today, but the threat still persists, which is why companies and individuals should keep this in mind.
October 2011. A former Google employee creates Litecoin, an alternative to bitcoin.
May 2012. More than half of the bitcoin transactions in a month were caused by the online game SatoshiDICE.
June 2012. The famous online wallet Coinbase is based in San Francisco, USA.
November 2012. The reward for bitcoin mining was reduced by half for the first time - the reward for mining a unit dropped from 50 XBT to 25 XBT (this happened during the extraction of 210,000 units).
The popular online blogging platform Wordpress is starting to accept payments in bitcoins.
December 2012. Bitcoin Central, the first Bitcoin exchange licensed as a European bank, begins operations in the European regulatory and legal segment.
January 2013. The first ASIC (Application Specific Integration Circuit - Special Purpose Integrated Circuit) - Bitcoin mining machines were released. Just as the GPU beat the CPU, the ASIC is now the most powerful and efficient machine available - this is special equipment designed only for bitcoin mining.
BitPay, a US-based Bitcoin payment processing company, announced that the number of transactions with their merchants exceeded 10,000.
February 2013.Bitcoin price has reached its greatest height, exceeding the value of 31.91 dollars, fixed at Mt. Gox 601 days before this in June 2011.
March 2013. The blockchain split for two, caused by the different behavior of two different versions of bitcoin programs. This meant that users with the old version of the program saw one transaction, while users with the new version saw another set of transactions. The split was quickly corrected by bitcoin miners who returned to an earlier version of the program. The bitcoin price temporarily fell during this period, but it quickly strengthened again to the price before branching.
By the end of the month, the price rose even more, and the total capitalization of the Bitcoin market for the first time exceeded one billion US dollars.
April 2013.Price continued impressive growth in April, reaching $ 250. The Cyprus financial crisis was called a potential catalyst for unprecedented growth. After the peak, the price stabilized at $ 120 for the next few months.
May 2013. Something that aroused my interest during my research, ESEA, a computer games company in the United States, used users' computers using a carefully crafted malware program to secretly extract bitcoin. They were caught and received a class action for millions of dollars. This, of course, is not the only example of such activity. In one of the places where I used to work, an employee was fired for secretly using the company's powerful computers to mine Bitcoin.
Probably less interesting, but more importantly, that same month the first Bitcoin ATM was opened in San Diego, USA.
Coinbase also received over $ 5 million in May from investors, the largest investment in the bitcoin industry at that time.
June 2013. In Sydney, Australia, our company, Independent Reserve, was founded. Before that, we spent six months analyzing the bitcoin and bitcoin market in order to understand how best to integrate into the new economy. We decided that Australia needed a reliable bitcoin exchange to create a solid foundation that other bitcoin-related businesses could use as a basis for their own offers.
August 2013.A federal judge in the United States classified bitcoin as a legal tender. At the same time, the German government legitimized bitcoin, declaring digital currencies a “unit of account”. Also in August, bitcoin appeared on the Bloomberg terminals with the currency code XBT.
September 2013. The global computing power of the Bitcoin network for the first time reached 1 pentahesh or 1,000,000,000,000,000 (1 quadrillion) hashes per second.
October 2013. The infamous Silkroad site was closed by the FBI. Instead of a skeptic-predicted collapse of the market, the price of bitcoin fell for a short time, but then continued to grow, as it became clear that most of the transactions were not related to Silkroad, and Silkroad was a relatively small player in the Bitcoin economy.
In the same month, global investment bank Merill Lynch called bitcoin potentially "the main payment instrument in e-commerce, able to become a serious competitor to traditional money transfer systems ."
In October, the largest Chinese search engine Baidu became the first service of this kind to accept bitcoin.
November 2013.
The head of the US Federal Reserve, Ben Bernanke, publicly announced that Bitcoin " may have a long-term perspective, especially if innovation offers a faster, safer and more efficient payment system". The US Senate, which held a Bitcoin hearing, also cautiously favored digital currencies, and the Financial Crimes Enforcement Network declared Bitcoin innovative and useful, warning that premature regulation could stifle innovation. They also pointed out to critics that any illegal use of bitcoin was insignificant compared to $ 1.6 trillion of “global criminal income” in 1999. The positive results of the hearings in the Senate in November caused the rise in the Bitcoin price to $ 1,242.
At the same time, billionaire entrepreneur Sir Richard Branson announced at CNBC that his company, Virgin Galactic, engaged in commercial space flights, will accept payments in bitcoins. He called bitcoin an “exciting new currency.” The company has already received the first payment worth about $ 250,000.
At this point in the history of Bitcoin, it is used to transfer more money than Western Union, about 245 million dollars a month.
December 2013. One of Tesla Model S electric cars Ilona Mask (PayPal, SpaceX, Tesla, SolarCity) was sold in the US for bitcoins. The price of the car at that time was about 103,000 dollars.
However, while Bitcoin flourished in the west, in the east, the Central Bank of China prohibited financial institutions from processing bitcoin transactions, which caused the price to fall to about $ 500. This ruling prompted Baidu to stop accepting Bitcoin payments.
January 2014. Global computing power for the first time reached 10 pentaheshs.
March 2014. The British Tax Administration stated that Bitcoin should be considered as the currency for executing transactions.
June 2014. Expedia, one of the largest travel agencies in the world, is starting to accept bitcoin payments.
The global computing power of the network reaches 100 pentaheshs.
July 2014.Dell, one of the largest computer makers in the world, is starting to accept bitcoin payments.
September 2014. PayPal, one of the largest payment processing companies, gives merchants the ability to accept payments in bitcoins.
October 2014. Independent Reserve, the most advanced and secure bitcoin exchange in Australia, was launched in Sydney.
November 2014. The Australian Senate begins exploring the use of bitcoin and digital currencies in Australia.
December 2014. Microsoft, one of the largest software makers in the world, is starting to accept bitcoin for some online purchases.
January 2015The New York Stock Exchange and a consortium of international banks are investing $ 75 million in the bitcoin industry.
August 2015 The Australian Senate issues recommendations on the study of digital currencies, demanding to treat Bitcoin as ordinary money for tax purposes, and also to apply anti-money laundering laws to digital currencies. This result is perceived by the Australian bitcoin industry as a very positive step towards legalizing a young currency.
Adrian's Epilogue Delighted
I hope you enjoyed reading the book of Adam, as well as I liked the time spent editing and completing his manuscript. For the last 14 years, Adam and I have worked together on so many different projects that it often seemed to me that he was here, next to me, working on this book, arguing about some formulations or trying to convince me that his interpretation of the obscure grammatical rule is more correct, than mine
While I was working on the book, I wondered whether to include additional chapters and expand some sections. I know that Adam would probably have written more if he had a chance, but I decided that it would be better to keep the book close to the original in order to demonstrate the work and thoughts of Adam himself. It seemed to me more important than adding another chapter, say, "Side chains" or "The Future of Bitcoin", and, in my opinion, this book is quite strong as it is, it does not need additional content.
I am sorry that Adam cannot see his ambitions realized, and his book published. I know that he would be proud to see this project completed. It was the culmination of many hours of work on the text, many years of research and hard work in the IT and Bitcoin industry, which gave him the knowledge and understanding to write this book.
I know that this publication would bring him joy, which will leave his mark on history for many years.
Adrian Gentle
[1] Bitcoins can be stored non-electronically, for example, on paper, but this is the exception rather than the rule. Transactions, however, are always electronic.
[2] XBT is accepted as the standard currency for Bitcoin. In other currency notation, the first character usually means the country that issued the currency. In some places, the alternative BTC designation is still used.
[3] When I say "computer", in fact, I mean any electronic device where the corresponding program is installed. This may be a mobile phone, laptop or similar device.
[4] Technically, the “impossibility” of hacking has not been proven for any form of software encryption or digital signature, but it can be reasonably stated that forging a digital signature is so difficult that it is almost impossible in all practical applications.
[5] Below we will see that as a precaution against fraud, it is reasonable to wait half an hour to confirm a transaction with a significant amount, but usually all transactions can be seen in a few seconds.
[6] It is worthwhile to stop and think about how astronomically large a number, consisting of several hundred numbers. This is many orders of magnitude more than the number of atoms in the observable universe.
[7] As we already noted in the third chapter, there is nothing truly “impossible” in the world of cryptography, but in practice some things are considered rather complicated so that for all practical purposes we consider them impossible.
[8] The process of hashing a user password is a bit more complicated, and includes adding a random value to the password, known as “salt.” Thus, if two people have the same password, this provides different hash values, making the system more secure.
[9] Tor is an abbreviation for The Onion Router (onion router), this project was originally developed for the US Navy, and was designed for encrypted and anonymous online communication. Now this software is widely used on the Internet to provide anonymity for people who want to keep their online privacy confidential.
[10] For a more serious discussion of this topic, see Chapter Eight - “Anonymity.”
[11] Silkroad has since replaced other anonymous black markets that have grown due to its decline.
[12] Such wallets are called “hierarchically deterministic” or “HD-wallets”.
[13] "EMP" or "electromagnetic pulse" is a brief, strong release of energy that can cause data loss stored on computer disks without being recoverable. It can occur naturally, for example, due to a lightning strike, or due to a person, as a form of weapon.
[14] NFC (Near Field Communication) is near-field communication, a technology that is increasingly used in modern telephones and enables data exchange between devices in close proximity to each other.
[15] “Fiat currency” is money that the government declares to be legal tender, but which is not provided with physical values. The value of fiat money is derived from the relationship between supply and demand, and not from the value of the material from which they are made.
[16] AML / CTF (Anti Money Laundering / Counter Terrorism Financing) - counteracting money laundering and terrorist financing is a set of legal requirements that banks and other financial institutions must follow to ensure that their customers do not use money for illegal purposes. Since bitcoin exchanges, along with bitcoin, deal with traditional currencies, they are usually also required to follow various procedures for verifying the identity of their clients and notifying them of suspicious transactions.
Source: https://habr.com/ru/post/308828/
All Articles