Visualize attacks, anomalies, and information security breaches using OpenGraphiti
Those who visit our headquarters from San Jose are always struck by a large video wall that displays a real-time attack pattern with the ability to drill down after touching certain areas of the screen.
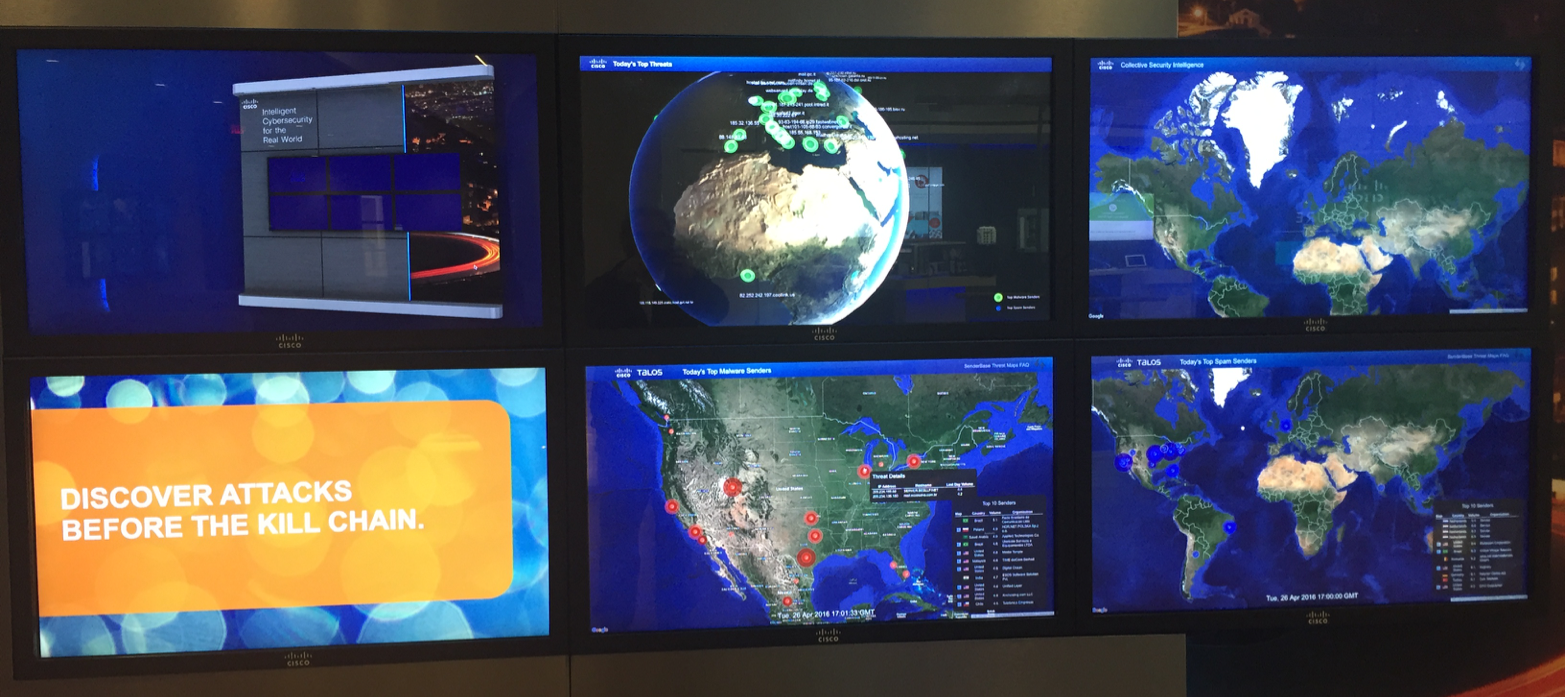
However, like any attack map, and I already have 34 in my collection , any such visualization is ineffective in real life. Show bosses, show reporters, include in any video ... It's all useful, but in practice it is applicable a little. Usually you have your own data sets that are generated by your security tools. And you are interested in what is happening in your network or directed at your network, but certainly not beautiful cards with “ballistic missile strikes”, which are drawn by an absolute majority of companies providing attack visualization services.
')

One of the solutions to the problem that has arisen is the open source toolkit OpenGraphiti , developed by OpenDNS , which is now part of Cisco . OpenGraphiti is a free 3D data visualization engine that analysts can use to display and analyze semantic networks. Having your own API allows you to effectively use OpenGraphiti for your own purposes, which, in the case of information security, include:
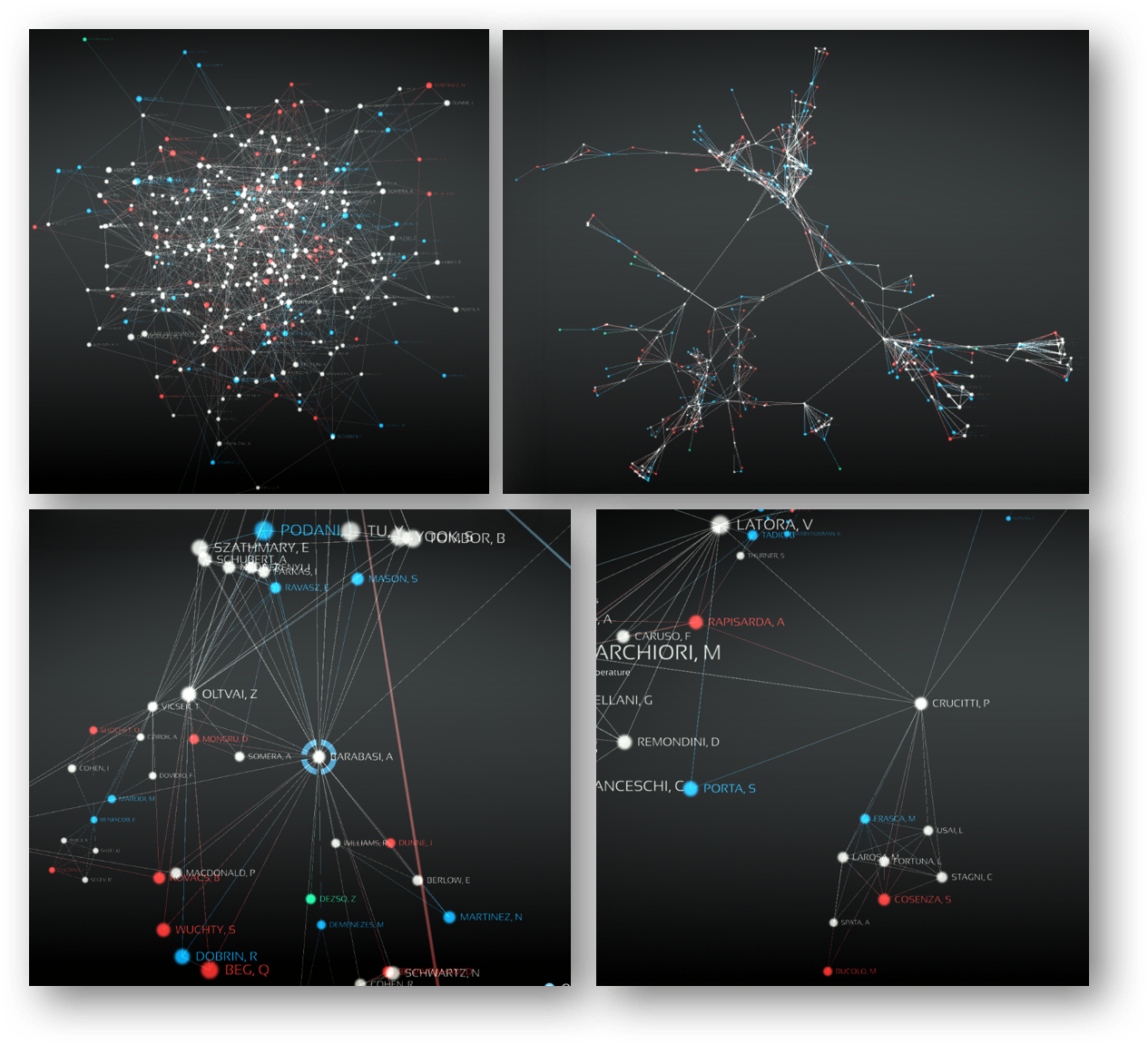
Here's how, for example, the part of the Dark Hotel spy campaign network built with OpenGraphiti looks like:

It is necessary to give some explanations to the color legend of this semantic network. Red shows the domains to which the initial request was directed, and the blue - the final point, to which the request was redirected through intermediate nodes marked in white. It is worth paying attention to these differences, since they once again demonstrate that banal “black” lists in the proxy, access control systems to the Internet or even in ITU, are focused on fighting the “red” nodes, completely ignoring the complex chain of interaction in the malicious infrastructure.
And this is what the ZeuS semantic network looks like:

Finally, this is how the Shellshock vulnerability spreads:
Of course, the essence of the semantic network is best displayed not by a static picture, but by a dynamic changing map, which can change its scale and detail depending on the tasks facing analysts. For example, this is how WikiLeaks sees the site and interacts with it:
The semantic network is, as Wikipedia says, an information model of the domain that has the form of a directed graph. This graph consists of vertices (nodes), which are the studied entities. Here's how, for example, the semantic map of concepts of domestic GOST R ISO / IEC 15408, also known as “General criteria”, looks.

If it is more practical to apply the semantic network to the visualization of attacks and other anomalies, then different characteristics of servers and nodes in the network — Web, email, NTP, SSH, etc. — can be considered as entities or vertices of the graph. Another example is social media accounts or email inboxes. The edges or arcs of such a graph (connections between nodes) describe relationships between entities. Examples of such edges are bandwidth, time, number of connections / messages, etc.
In the process of creating our own semantic network, we will need to create our own set of entities of interest to us, depending on the goals of the analysis. For example, when analyzing social networks, both individuals and companies that interest us can be used as entities (graph vertices). At the same time as the edges of the graph can be considered:
It is very easy to analyze internal and external communications using a semantic network. You can take e-mail addresses as entities, and you can take many different attributes as relationships between entities:
If we want to analyze network interaction, then we can take IP addresses, servers, hosts, ITUs, routers, proxies, autonomous systems, etc., as the entities under study. And as relations (edges of the graph) we can analyze the ports used in the network interaction, the host name (hostname), the country (geo-binding), the autonomous system (AS), the domain. Note that the autonomous system is mentioned twice - both as an entity and as a relationship. Why is that? It all depends on what we want to analyze. If we are interested in how traffic flows between different autonomous systems, then they will interest us precisely as entities, that is, nodes of the semantic network. And if we are interested in from where we are most often attacked, then the autonomous system turns into a relation for us, that is, the edges of the graph.
The benefits enjoyed by OpenGraphiti include:
If a little more attention is paid to the first advantage, then with the help of visualization we can identify the use of DGA (Domain Generation Algorithms), which are used not only for marketing purposes, but also by malware. One-day sites whose domains are created automatically and in large numbers in order to bypass the blacklist mechanism.

Once again, OpenGraphiti is a free open source tool, the requirements for which are quite simple:
Instructions for installing and configuring OpenGraphiti are available at www.opengraphiti.com . The construction itself is customizable and can be integrated into its own monitoring centers (SOC), tying it with your own data. So, for example, OpenGraphiti runs on the OpenDNS site (Chrome is required):

Obviously, as the data grows, so does the complexity of the map. It can be managed using entity grouping or selection. For example, I can visualize not the entire network for millions of IP addresses (as in the Cisco network), but the sets of nodes grouped by different criteria — geolocation, departmental membership, node importance, etc. This allows us not to immediately immerse in the details, but to embrace the picture from a bird's-eye view and then dive into the region we need at the given moment in time.
Here's how, for example, the Zbot botnet map looks like:

Using the scaling function for various parameters, we can change the level of detail of the same map:

Why do we need visualization and why can we not get along with plain text or tabular presentation of the data that the existing defenses generate to us? There is a good analogy. If we imagine that the human eye can transmit visual data to the brain at the speed of Ethernet, then reading the text allows you to interact with the brain at dial-up speed. It is obvious that working with textual information, namely, it is mainly used by most of the means of protection, today has a number of shortcomings, among which the main thing is precisely the speed of perception and the detection of implicit interdependencies. This is especially important when we are dealing with monitoring large amounts of frequently changing data. To achieve the desired effect with textual data is difficult and visualization, which by no means cancels the already existing types of analysis, is a good help (provided that we know what to look for and where).
In conclusion, I would like to note that today, in an environment where IS analysts are overloaded, it is very important to choose the right toolkit for visualizing large amounts of data, allowing you to see the protected system, which allows us to ask the right questions and get the right answers, which is the key building the right information security strategy in the enterprise. And OpenGraphiti helps in solving this problem.

However, like any attack map, and I already have 34 in my collection , any such visualization is ineffective in real life. Show bosses, show reporters, include in any video ... It's all useful, but in practice it is applicable a little. Usually you have your own data sets that are generated by your security tools. And you are interested in what is happening in your network or directed at your network, but certainly not beautiful cards with “ballistic missile strikes”, which are drawn by an absolute majority of companies providing attack visualization services.
')

One of the solutions to the problem that has arisen is the open source toolkit OpenGraphiti , developed by OpenDNS , which is now part of Cisco . OpenGraphiti is a free 3D data visualization engine that analysts can use to display and analyze semantic networks. Having your own API allows you to effectively use OpenGraphiti for your own purposes, which, in the case of information security, include:
- botnet visualization
- DDoS Attack Visualization
- spamming visualization
- visualization of hacker campaigns
- visualization of the movement of the malware / hacker over the network
- vulnerability visualization
- visualization of wireless devices, incl. and unauthorized
- visualization of IoT devices
- visualization of information flows within the corporate or departmental network, including in the analysis of e-mail
- visualization of connections in social networks
- etc.
Here's how, for example, the part of the Dark Hotel spy campaign network built with OpenGraphiti looks like:

It is necessary to give some explanations to the color legend of this semantic network. Red shows the domains to which the initial request was directed, and the blue - the final point, to which the request was redirected through intermediate nodes marked in white. It is worth paying attention to these differences, since they once again demonstrate that banal “black” lists in the proxy, access control systems to the Internet or even in ITU, are focused on fighting the “red” nodes, completely ignoring the complex chain of interaction in the malicious infrastructure.
And this is what the ZeuS semantic network looks like:

Finally, this is how the Shellshock vulnerability spreads:

Of course, the essence of the semantic network is best displayed not by a static picture, but by a dynamic changing map, which can change its scale and detail depending on the tasks facing analysts. For example, this is how WikiLeaks sees the site and interacts with it:
What is a semantic network?
The semantic network is, as Wikipedia says, an information model of the domain that has the form of a directed graph. This graph consists of vertices (nodes), which are the studied entities. Here's how, for example, the semantic map of concepts of domestic GOST R ISO / IEC 15408, also known as “General criteria”, looks.

If it is more practical to apply the semantic network to the visualization of attacks and other anomalies, then different characteristics of servers and nodes in the network — Web, email, NTP, SSH, etc. — can be considered as entities or vertices of the graph. Another example is social media accounts or email inboxes. The edges or arcs of such a graph (connections between nodes) describe relationships between entities. Examples of such edges are bandwidth, time, number of connections / messages, etc.
In the process of creating our own semantic network, we will need to create our own set of entities of interest to us, depending on the goals of the analysis. For example, when analyzing social networks, both individuals and companies that interest us can be used as entities (graph vertices). At the same time as the edges of the graph can be considered:
- Place of work
- Account creation date (allows bots to be calculated)
- Account activity
- Religion
- Groups in which subjects of interest are involved
- Etc.
It is very easy to analyze internal and external communications using a semantic network. You can take e-mail addresses as entities, and you can take many different attributes as relationships between entities:
- time of writing letters (or sending messages using instant messengers)
- communication method (e-mail, skype, Jabber, etc.)
- device (personal or service)
- etc.

If we want to analyze network interaction, then we can take IP addresses, servers, hosts, ITUs, routers, proxies, autonomous systems, etc., as the entities under study. And as relations (edges of the graph) we can analyze the ports used in the network interaction, the host name (hostname), the country (geo-binding), the autonomous system (AS), the domain. Note that the autonomous system is mentioned twice - both as an entity and as a relationship. Why is that? It all depends on what we want to analyze. If we are interested in how traffic flows between different autonomous systems, then they will interest us precisely as entities, that is, nodes of the semantic network. And if we are interested in from where we are most often attacked, then the autonomous system turns into a relation for us, that is, the edges of the graph.
The benefits enjoyed by OpenGraphiti include:
- provision of context for searching various interrelations between entities of interest, including various anomalies
- “Story” of the history of your security on the basis of Big Data
- the ability to compare different attacks and campaigns
- assistance in the attribution of intruders and finding out the entry points for various infringements of information security
- show “show” in real time, which allows you to correlate an attack or other violation with various news from the world of security (publishing information about vulnerabilities, new attacks, etc.).
If a little more attention is paid to the first advantage, then with the help of visualization we can identify the use of DGA (Domain Generation Algorithms), which are used not only for marketing purposes, but also by malware. One-day sites whose domains are created automatically and in large numbers in order to bypass the blacklist mechanism.

Once again, OpenGraphiti is a free open source tool, the requirements for which are quite simple:
- MacOS or Linux
- Clang ++ or g ++
- Python 2.7.x
Instructions for installing and configuring OpenGraphiti are available at www.opengraphiti.com . The construction itself is customizable and can be integrated into its own monitoring centers (SOC), tying it with your own data. So, for example, OpenGraphiti runs on the OpenDNS site (Chrome is required):

Obviously, as the data grows, so does the complexity of the map. It can be managed using entity grouping or selection. For example, I can visualize not the entire network for millions of IP addresses (as in the Cisco network), but the sets of nodes grouped by different criteria — geolocation, departmental membership, node importance, etc. This allows us not to immediately immerse in the details, but to embrace the picture from a bird's-eye view and then dive into the region we need at the given moment in time.
Here's how, for example, the Zbot botnet map looks like:

Using the scaling function for various parameters, we can change the level of detail of the same map:

Why do we need visualization and why can we not get along with plain text or tabular presentation of the data that the existing defenses generate to us? There is a good analogy. If we imagine that the human eye can transmit visual data to the brain at the speed of Ethernet, then reading the text allows you to interact with the brain at dial-up speed. It is obvious that working with textual information, namely, it is mainly used by most of the means of protection, today has a number of shortcomings, among which the main thing is precisely the speed of perception and the detection of implicit interdependencies. This is especially important when we are dealing with monitoring large amounts of frequently changing data. To achieve the desired effect with textual data is difficult and visualization, which by no means cancels the already existing types of analysis, is a good help (provided that we know what to look for and where).
In conclusion, I would like to note that today, in an environment where IS analysts are overloaded, it is very important to choose the right toolkit for visualizing large amounts of data, allowing you to see the protected system, which allows us to ask the right questions and get the right answers, which is the key building the right information security strategy in the enterprise. And OpenGraphiti helps in solving this problem.
Source: https://habr.com/ru/post/308774/
All Articles