DDoS: IT Maniacs on the Point of Attack
Security of online projects, corporate IT resources, data centers is one of the key priorities that requires constant attention and development. The term “DDoS” is familiar to many people at first hand or at least in the press. Unfortunately, this phenomenon is widespread. When DDoS-attack occurs distributed attack on the organization's IT system in order to bring it to failure. In this case, the legitimate users of the system can not access its resources, or this access is difficult.

DDoS attacks are exposed to Internet projects and sites around the world. So in 2015, Wallarm detected more than 100 million attacks on its clients' web resources. Often such attacks are ordered by competitors. Another reason for organizing attacks is extortion through blackmail.

According to Qrator Labs, in 2015 the increase in the number of attacks in Russia was 100%.
Meanwhile, according to Qrator , in 2015 in Russia the number of DDoS attacks doubled compared with 2014. In 84% of cases, there is an alternation of DDoS attacks and site hacking attempts. Similar incidents have become frequent in the world. Solar JSOC experts attribute the increase in the number of DDoS attacks during the whole of 2015, primarily to the competitive struggle that has intensified by the end of the year.
')
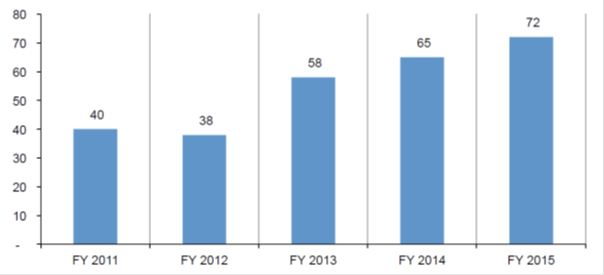
Increase in the frequency of DDoS attacks in the world (data from the Ponemon Institute , 2016).
The target of such attacks are a variety of organizations.
After analyzing the statistical data for the 2nd quarter of 2016, the specialists of the DDoS-GUARD security provider came to a different conclusion : the activity of hackers has decreased significantly, but they have become tougher to act. DDoS attacks were recorded at 57% less than in the previous quarter - only 12,583. But the quality of attacks, power and complexity increased markedly. Based on this, it can be assumed that in the spring and in the beginning of summer most DDoS attacks were organized and carried out by professional hackers.
According to DDoS-GUARD , in the second quarter of 2016 compared to the previous quarter, attacks from China and Russia became slightly smaller, but the three leaders remained the same:
For companies from the banking, telecommunications and government sectors, countering DDoS attacks remains a hot issue. The main target of the attackers is e-commerce companies, banks, social networks and even game resources . Also in 2015, among the most frequent goals were travel companies and real estate agencies. According to 42Future, 25% of the largest retailers have come across DDoS over the past year. The number of attacks on retailer sites increased by about 70% compared with 2014.
Growth in the average number of DDoS attacks on sites of various industries in 2015
All over the world, these attacks lead to serious material damage.
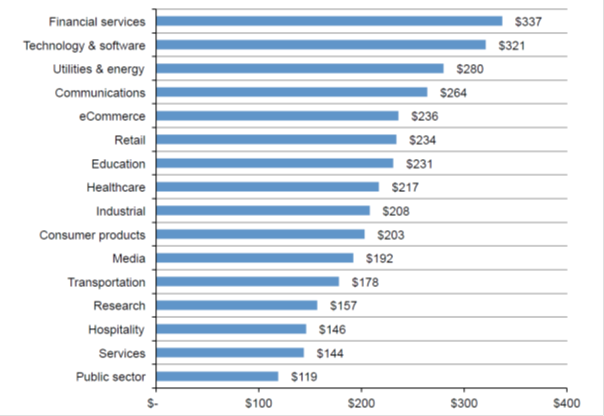
The average damage from a single DDoS attack in various industries, thousand dollars (data from the Ponemon Institute , 2016).
Qrator Labs identifies the following categories of target resources for targeted attacks:
1. E-commerce, and above all online retailers. Fraud with bonus points, hunting for user bases.
2. Payment systems and aggregators, financial brokers and other financial institutions. Attempt to access the database with the ability to change balances.
3. Game industry. Frode with the internal economy of games, the collapse of source codes, etc.
4. Advertising networks. Fraud with the internal balances of accounts and fraud with the number of hits.
5 MASS MEDIA. Violation of the availability and performance of resources.
At the same time, hacking of web applications often becomes a stepping stone to access to the company's internal infrastructure.
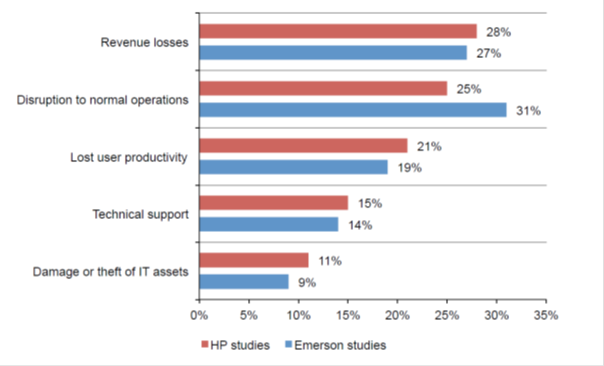
The most serious types of financial damage to companies from DDoS attacks are loss of profits, violations in the robot, reduced user productivity, technical support problems, damage or damage to IT resources (data from HPE (red) and Emerson Network Power (blue), 2016) .
The target of the attackers may be computing resources, which they later use for further DDoS attacks, as a proxy server, mining cryptocurrency, etc.
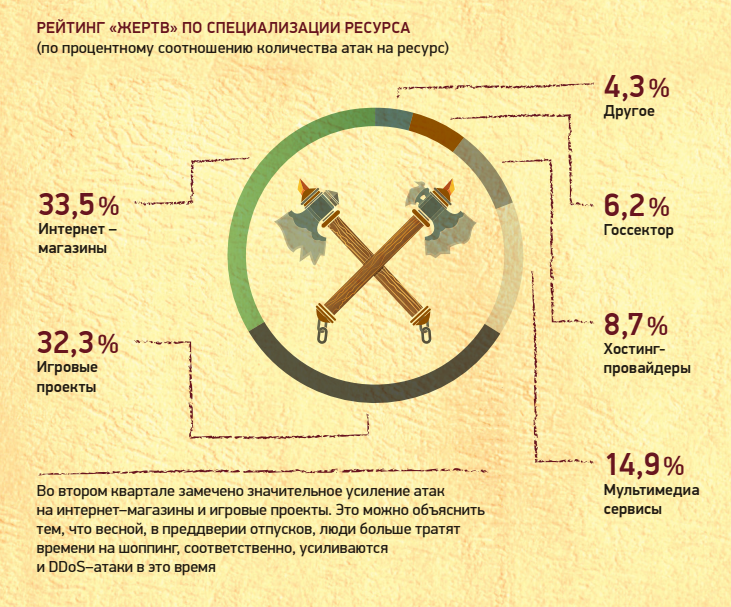
According to DDoS-GUARD , in the second quarter of 2016, a significant increase in attacks on online stores and game projects was observed. Servers of popular online games are hackers' favorite target.
DDoS attacks become more complex and sophisticated. The decrease in peak speeds of DDoS attacks, noted in 2015, was offset by an increase in their complexity. The increase in the technical complexity of attacks makes DDoS protection a classic example of “competition of armor and projectile”, so companies need to regularly update their protection system, experts say. Hackers combine different approaches, simultaneously resorting to DDoS attacks and attacks against application vulnerabilities. In 84% of cases, a DDoS attack is accompanied by attempts at hacking the site.
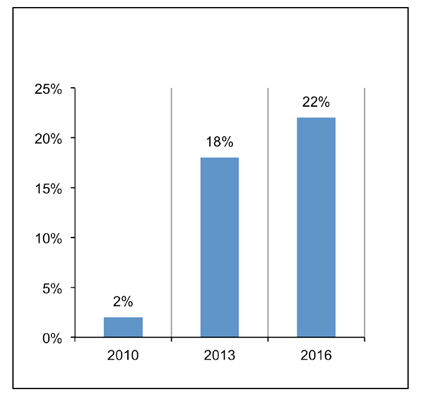
In the world of DDoS attacks, they are increasingly becoming the main cause of unplanned downtime in the data center (data from the Ponemon Institute , 2016).
In addition, if earlier attackers, as a rule, were limited to one type of DDoS, then today attacks are becoming complex, they can be directed to several network layers and infrastructure elements at once. Attacks on the application layer (L7), which often accompany DDoS attacks on the data link layer (L2), have become frequent. At the same time, hackers use intelligent automated tools. You can counter this in many ways.
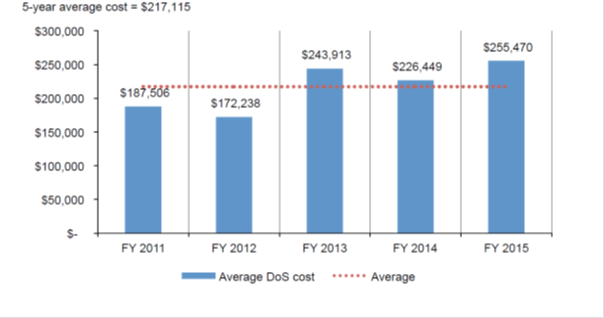
Change in the average cost of DDoS attacks (data from the Ponemon Institute, 2016).
One of the trends is attacks such as Amplification. A request is sent to the server containing the vulnerability, which is replicated several times by this server and sent to the victim's web resource. DNS, NTP, SSDP servers and others can be used as servers that are unwillingly involved in such attacks.
In Amplification attacks, botnets are rarely used to generate the first wave of garbage traffic. Usually, servers are rented for these purposes, or someone else’s hacked ones are used. Amplification attacks can be followed by an attack on an application (L7).

Organizing an Amplification type of attack is inexpensive; an attacker only has to generate requests at a speed of several Gbit / s and send them to a server with a vulnerability that will increase this speed by several orders of magnitude (data from Qrator Labs).
The actual cost of the attacker on the infrastructure necessary to organize an attack is several dozen times less than the victim company needs to neutralize such an attack on its own.
The DD4BC approach (combining attacks from various classes) is also gaining popularity. Following a stopped DDoS attack, an attempt to hack the site is likely to be made, and vice versa.
In addition, hackers use Internet scanning tools in search of resources with known vulnerabilities. Today, almost every site costs daily testing bot. Any resource, including a little-known and practically not visited, can be hacked by automated tools.
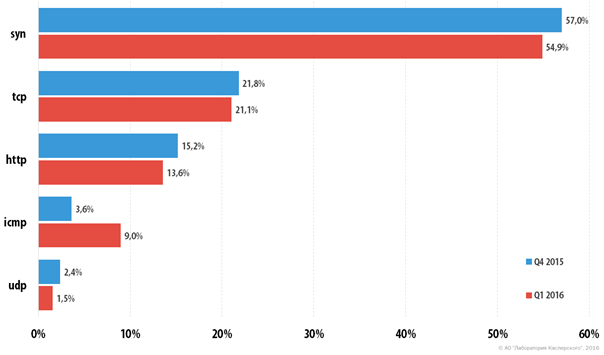
Distribution of DDoS attacks by type ( according to Kaspersky Lab ).
According to Wallarm, 31% of sites contain critical vulnerabilities. Such a site can be hacked even by a highly qualified specialist. The number of attacks on cloud infrastructures (AWS, Azure, etc.) is increasing. Attackers use frequent errors in the administration of cloud resources.
An increasing number of companies from various industries are switching their sites to secure data transmission using the HTTPS protocol. Following this, hackers pay more attention to attacks on applications running on this protocol. The overall increase in the number of DDoSs and the steady annual growth of encrypted traffic (in 2015, it grew about two times in the world) suggests that in 2016 the number of DDoS attacks on HTTPS services will increase, respectively.
According to DDoS-GUARD , in the second quarter of 2016, the maximum level of spurious traffic via UDP was 217.7 Gbit / s, which is 71% higher than in the first quarter of 2016. The strongest TCP DDoS attack reached 119, 8 Gbit / s, which is 49% more powerful than the first quarter. The average power of all attacks also increased - by 10% - and amounted to 1.15 Gbit / s.

Distribution of attacks by protocol types according to DDoS-GUARD for the second quarter of 2016.
If we talk about packet and volumetric attacks, then their volume during the reporting period increased 12 times and amounted to an average of 450,603 packets per second. Trends of the spring-summer season:
1) Multivector, i.e. attack on several protocols of one Internet resource at once,
2) the combination of low-power long-term flood with short-term "needle" attacks of large volume,
3) the use of social networks to generate parasitic traffic.
The number of incidents related to attacks on network infrastructure (DNS servers, as well as attacks related to BGP errors) will also increase in the next few years.
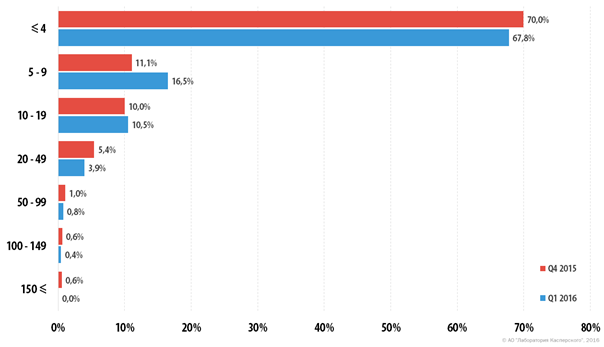
Distribution of DDoS attacks by duration according to Kaspersky Lab . About 70% of attacks accounted for short-term actions lasting 4 hours or less. At the same time, the maximum attack duration was significantly reduced.
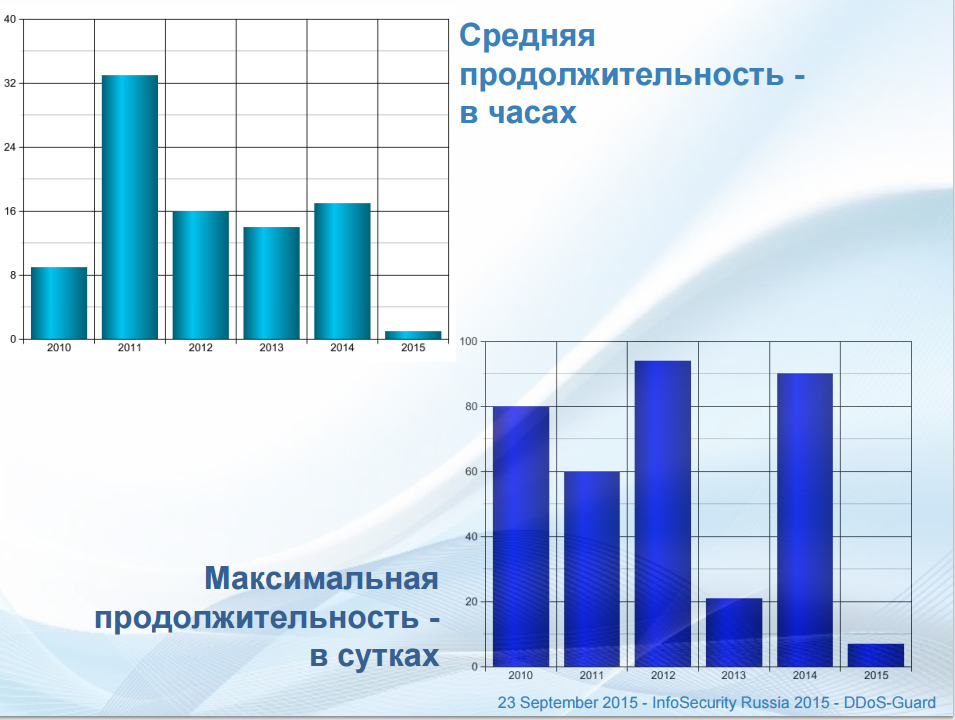
Change the average and maximum duration of attacks according to DDoS-GUARD .
According to Qrator Labs, in 2016, 5-10% of autonomous systems of Internet access providers will experience problems with the availability of their services. The number of significant BGP incidents leading to the unavailability of hundreds and even thousands of networks will also increase.
In the future, the Internet of Things (IoT) will pose a serious threat. All devices connected to the Internet can potentially become part of the infrastructure of attackers and be involved in DDoS-attacks.
When building a network security system, it is important to take into account modern threats and especially targeted and DDoS attacks. Many web resource owners are familiar with DDoS attacks firsthand, invest a lot of money in hosting and protecting their services from DDoS, and have achieved good results in repelling such attacks. In the case of attacks on the data link layer, companies usually rely on the protection provided by the provider. For virtualized servers, essentially the same protection rules apply as for physical ones. Local solutions are often used to protect against attacks on IT infrastructure.
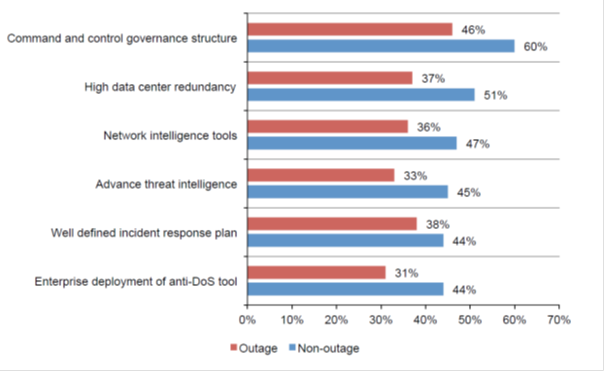
Preventive measures against DDoS in data centers and their results (red - unplanned downtime as a result of the attack, blue - avoided downtime (data from the Ponemon Institute , 2016). The most common measures cover the management level, include backup tools, intelligent analytical tools and Means for combating threats include an incident response plan and deployment of DoS protection.
Meanwhile, the means providing only protection against DDoS, today are insufficient. To build protection against DDoS should be immediately at all levels. Companies with an integrated approach to the organization of a system to counter attacks of increased complexity succeed in fairly successfully neutralizing these risks.
For example, to ensure the availability of the site at the level of 95-99.5%, you can pass all its traffic through the traffic clearing network, provide resource protection at the transport and network levels, where filtering and analysis of incoming traffic, blocking IP addresses, and generating reports occur about incidents.
Thus, only the simultaneous use of different types of protection (including protection against DDoS and attacks on applications, as well as BGP monitoring tools) can effectively resist DDoS. Protect yourself from security threats with a combination of integrated solutions.
Protection against DDoS attacks at the application level requires maximum expertise and speed of response to changes in the attack vector, for which automated systems are used, including those based on machine learning algorithms. To counter the complex, complex DDoS attacks and hacks, you need to use professional solutions.
If the owner of the data center does not have sufficient experience and special technical means, a DDoS attack can cause the inaccessibility of its network devices and IT infrastructure of its clients. The introduction of protection against DDoS-attacks in the data center is a necessary measure to ensure stable and reliable operation of applications and customer resources.
The attempts to independently cope with the attacks of the link level (L2) are gradually disappearing. After all, for this it is necessary to organize and maintain an expensive communication channel and distributed infrastructure (in several data centers). Therefore, companies prefer to rely on their Internet providers or start using professional DDoS counteraction services that can handle multi-vector attacks in real time.
Providers, as a rule, have sufficient capabilities and qualifications not only to ensure the security of their own services, but also to offer various solutions for protecting customer data, providing secure access and storing information.
The range of security services offered by Russian providers today is quite wide. Moreover, protection against DDoS-attacks is one of the most common services along with services such as firewall, encryption of the access channel (VPN).
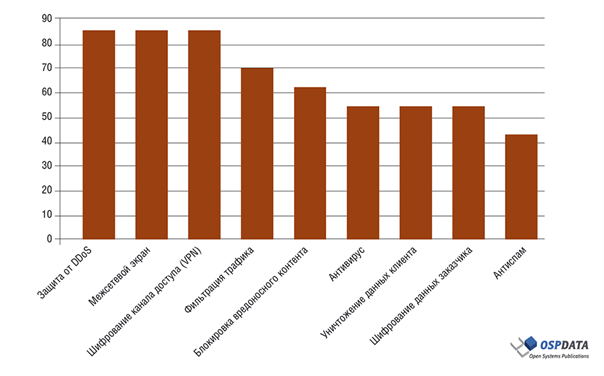
According to a survey of Russian providers (21 companies) conducted by OSP Data in 2015, 85% of them in one form or another provide customers with the service of protection from DDoS.
Analytics and protection against DDoS attacks is a popular service that provides sufficiently effective protection of the physical and virtual servers ( VPS / VDS ) placed in the data centers of the provider, especially since it is inexpensive . For this, providers and hosters use modern partner solutions. Network traffic analysis is performed 24/7, and protection allows stably withstanding powerful attacks - up to 1500 Gbit / s.

DDoS attacks are exposed to Internet projects and sites around the world. So in 2015, Wallarm detected more than 100 million attacks on its clients' web resources. Often such attacks are ordered by competitors. Another reason for organizing attacks is extortion through blackmail.

According to Qrator Labs, in 2015 the increase in the number of attacks in Russia was 100%.
Meanwhile, according to Qrator , in 2015 in Russia the number of DDoS attacks doubled compared with 2014. In 84% of cases, there is an alternation of DDoS attacks and site hacking attempts. Similar incidents have become frequent in the world. Solar JSOC experts attribute the increase in the number of DDoS attacks during the whole of 2015, primarily to the competitive struggle that has intensified by the end of the year.
')

Increase in the frequency of DDoS attacks in the world (data from the Ponemon Institute , 2016).
The target of such attacks are a variety of organizations.
After analyzing the statistical data for the 2nd quarter of 2016, the specialists of the DDoS-GUARD security provider came to a different conclusion : the activity of hackers has decreased significantly, but they have become tougher to act. DDoS attacks were recorded at 57% less than in the previous quarter - only 12,583. But the quality of attacks, power and complexity increased markedly. Based on this, it can be assumed that in the spring and in the beginning of summer most DDoS attacks were organized and carried out by professional hackers.
Who is attacked?
According to DDoS-GUARD , in the second quarter of 2016 compared to the previous quarter, attacks from China and Russia became slightly smaller, but the three leaders remained the same:
China - 41%
Russia - 30%
United States - 29%
For companies from the banking, telecommunications and government sectors, countering DDoS attacks remains a hot issue. The main target of the attackers is e-commerce companies, banks, social networks and even game resources . Also in 2015, among the most frequent goals were travel companies and real estate agencies. According to 42Future, 25% of the largest retailers have come across DDoS over the past year. The number of attacks on retailer sites increased by about 70% compared with 2014.
Growth in the average number of DDoS attacks on sites of various industries in 2015
| Amplified DDoS | All ddos | |
| Online stores | 25% | 70% |
| Social networks | 73% | 159% |
| Coupons | -25% | -ten% |
| Forex | -53% | -62% |
| Payment systems | 74% | 37% |
| Games | 42% | 110% |
| Trading platforms | -15% | -18% |
| Banks | 121% | 61% |
| mass media | -29% | 17% |
| Content aggregators | -43% | -28% |
| Promotional sites: | ||
| Real estate agency | 113% | 144% |
| Advertising agencies | -40% | -sixteen% |
| Microfinance | -thirty% | -36% |
| Travel Agencies | -one% | 145% |
| Taxi | 116% | 108% |
| The medicine | -20% | -54% |
| Remaining promotional sites | -58% | -34% |
All over the world, these attacks lead to serious material damage.

The average damage from a single DDoS attack in various industries, thousand dollars (data from the Ponemon Institute , 2016).
Qrator Labs identifies the following categories of target resources for targeted attacks:
1. E-commerce, and above all online retailers. Fraud with bonus points, hunting for user bases.
2. Payment systems and aggregators, financial brokers and other financial institutions. Attempt to access the database with the ability to change balances.
3. Game industry. Frode with the internal economy of games, the collapse of source codes, etc.
4. Advertising networks. Fraud with the internal balances of accounts and fraud with the number of hits.
5 MASS MEDIA. Violation of the availability and performance of resources.
At the same time, hacking of web applications often becomes a stepping stone to access to the company's internal infrastructure.

The most serious types of financial damage to companies from DDoS attacks are loss of profits, violations in the robot, reduced user productivity, technical support problems, damage or damage to IT resources (data from HPE (red) and Emerson Network Power (blue), 2016) .
The target of the attackers may be computing resources, which they later use for further DDoS attacks, as a proxy server, mining cryptocurrency, etc.

According to DDoS-GUARD , in the second quarter of 2016, a significant increase in attacks on online stores and game projects was observed. Servers of popular online games are hackers' favorite target.
How to attack?
DDoS attacks become more complex and sophisticated. The decrease in peak speeds of DDoS attacks, noted in 2015, was offset by an increase in their complexity. The increase in the technical complexity of attacks makes DDoS protection a classic example of “competition of armor and projectile”, so companies need to regularly update their protection system, experts say. Hackers combine different approaches, simultaneously resorting to DDoS attacks and attacks against application vulnerabilities. In 84% of cases, a DDoS attack is accompanied by attempts at hacking the site.

In the world of DDoS attacks, they are increasingly becoming the main cause of unplanned downtime in the data center (data from the Ponemon Institute , 2016).
In addition, if earlier attackers, as a rule, were limited to one type of DDoS, then today attacks are becoming complex, they can be directed to several network layers and infrastructure elements at once. Attacks on the application layer (L7), which often accompany DDoS attacks on the data link layer (L2), have become frequent. At the same time, hackers use intelligent automated tools. You can counter this in many ways.

Change in the average cost of DDoS attacks (data from the Ponemon Institute, 2016).
One of the trends is attacks such as Amplification. A request is sent to the server containing the vulnerability, which is replicated several times by this server and sent to the victim's web resource. DNS, NTP, SSDP servers and others can be used as servers that are unwillingly involved in such attacks.
In Amplification attacks, botnets are rarely used to generate the first wave of garbage traffic. Usually, servers are rented for these purposes, or someone else’s hacked ones are used. Amplification attacks can be followed by an attack on an application (L7).

Organizing an Amplification type of attack is inexpensive; an attacker only has to generate requests at a speed of several Gbit / s and send them to a server with a vulnerability that will increase this speed by several orders of magnitude (data from Qrator Labs).
The actual cost of the attacker on the infrastructure necessary to organize an attack is several dozen times less than the victim company needs to neutralize such an attack on its own.
The DD4BC approach (combining attacks from various classes) is also gaining popularity. Following a stopped DDoS attack, an attempt to hack the site is likely to be made, and vice versa.
In addition, hackers use Internet scanning tools in search of resources with known vulnerabilities. Today, almost every site costs daily testing bot. Any resource, including a little-known and practically not visited, can be hacked by automated tools.

Distribution of DDoS attacks by type ( according to Kaspersky Lab ).
According to Wallarm, 31% of sites contain critical vulnerabilities. Such a site can be hacked even by a highly qualified specialist. The number of attacks on cloud infrastructures (AWS, Azure, etc.) is increasing. Attackers use frequent errors in the administration of cloud resources.
An increasing number of companies from various industries are switching their sites to secure data transmission using the HTTPS protocol. Following this, hackers pay more attention to attacks on applications running on this protocol. The overall increase in the number of DDoSs and the steady annual growth of encrypted traffic (in 2015, it grew about two times in the world) suggests that in 2016 the number of DDoS attacks on HTTPS services will increase, respectively.
According to DDoS-GUARD , in the second quarter of 2016, the maximum level of spurious traffic via UDP was 217.7 Gbit / s, which is 71% higher than in the first quarter of 2016. The strongest TCP DDoS attack reached 119, 8 Gbit / s, which is 49% more powerful than the first quarter. The average power of all attacks also increased - by 10% - and amounted to 1.15 Gbit / s.

Distribution of attacks by protocol types according to DDoS-GUARD for the second quarter of 2016.
If we talk about packet and volumetric attacks, then their volume during the reporting period increased 12 times and amounted to an average of 450,603 packets per second. Trends of the spring-summer season:
1) Multivector, i.e. attack on several protocols of one Internet resource at once,
2) the combination of low-power long-term flood with short-term "needle" attacks of large volume,
3) the use of social networks to generate parasitic traffic.
The number of incidents related to attacks on network infrastructure (DNS servers, as well as attacks related to BGP errors) will also increase in the next few years.

Distribution of DDoS attacks by duration according to Kaspersky Lab . About 70% of attacks accounted for short-term actions lasting 4 hours or less. At the same time, the maximum attack duration was significantly reduced.

Change the average and maximum duration of attacks according to DDoS-GUARD .
According to Qrator Labs, in 2016, 5-10% of autonomous systems of Internet access providers will experience problems with the availability of their services. The number of significant BGP incidents leading to the unavailability of hundreds and even thousands of networks will also increase.
In the future, the Internet of Things (IoT) will pose a serious threat. All devices connected to the Internet can potentially become part of the infrastructure of attackers and be involved in DDoS-attacks.
How to protect yourself?
When building a network security system, it is important to take into account modern threats and especially targeted and DDoS attacks. Many web resource owners are familiar with DDoS attacks firsthand, invest a lot of money in hosting and protecting their services from DDoS, and have achieved good results in repelling such attacks. In the case of attacks on the data link layer, companies usually rely on the protection provided by the provider. For virtualized servers, essentially the same protection rules apply as for physical ones. Local solutions are often used to protect against attacks on IT infrastructure.

Preventive measures against DDoS in data centers and their results (red - unplanned downtime as a result of the attack, blue - avoided downtime (data from the Ponemon Institute , 2016). The most common measures cover the management level, include backup tools, intelligent analytical tools and Means for combating threats include an incident response plan and deployment of DoS protection.
Meanwhile, the means providing only protection against DDoS, today are insufficient. To build protection against DDoS should be immediately at all levels. Companies with an integrated approach to the organization of a system to counter attacks of increased complexity succeed in fairly successfully neutralizing these risks.
For example, to ensure the availability of the site at the level of 95-99.5%, you can pass all its traffic through the traffic clearing network, provide resource protection at the transport and network levels, where filtering and analysis of incoming traffic, blocking IP addresses, and generating reports occur about incidents.
Thus, only the simultaneous use of different types of protection (including protection against DDoS and attacks on applications, as well as BGP monitoring tools) can effectively resist DDoS. Protect yourself from security threats with a combination of integrated solutions.
Protection against DDoS attacks at the application level requires maximum expertise and speed of response to changes in the attack vector, for which automated systems are used, including those based on machine learning algorithms. To counter the complex, complex DDoS attacks and hacks, you need to use professional solutions.
If the owner of the data center does not have sufficient experience and special technical means, a DDoS attack can cause the inaccessibility of its network devices and IT infrastructure of its clients. The introduction of protection against DDoS-attacks in the data center is a necessary measure to ensure stable and reliable operation of applications and customer resources.
Conclusion
The attempts to independently cope with the attacks of the link level (L2) are gradually disappearing. After all, for this it is necessary to organize and maintain an expensive communication channel and distributed infrastructure (in several data centers). Therefore, companies prefer to rely on their Internet providers or start using professional DDoS counteraction services that can handle multi-vector attacks in real time.
Providers, as a rule, have sufficient capabilities and qualifications not only to ensure the security of their own services, but also to offer various solutions for protecting customer data, providing secure access and storing information.
The range of security services offered by Russian providers today is quite wide. Moreover, protection against DDoS-attacks is one of the most common services along with services such as firewall, encryption of the access channel (VPN).

According to a survey of Russian providers (21 companies) conducted by OSP Data in 2015, 85% of them in one form or another provide customers with the service of protection from DDoS.
Analytics and protection against DDoS attacks is a popular service that provides sufficiently effective protection of the physical and virtual servers ( VPS / VDS ) placed in the data centers of the provider, especially since it is inexpensive . For this, providers and hosters use modern partner solutions. Network traffic analysis is performed 24/7, and protection allows stably withstanding powerful attacks - up to 1500 Gbit / s.
Source: https://habr.com/ru/post/308764/
All Articles