Why shadow copies do not save most encryptors

There are not many ways to recover files that are encrypted as a result of an attack by the coder, but without paying a ransom for them. If we are lucky, then there may be some free tools to restore them, but a more realistic option is to restore your files from your backups. However, not everyone has backup copies of their files, although Windows offers a very useful feature, known as Shadow Copy , which, in brief, is a backup of your files. Cyber criminals have learned about it for a long time, and therefore a few months after encryption attacks became popular, the first thing they do when they infect your computer is to remove a shadow copy of your files before encrypting your information.
There are a number of technologies that can be used to stop cipher attackers: some of them are almost useless, such as signatures or heuristics (this is the first thing the malware authors check before their “release”), others can sometimes be more effective, but even All these techniques do not guarantee that you will be protected from all such attacks.
')
More than 2 years ago, PandaLabs used a simple but quite effective approach in the anti-virus lab: if a process tries to remove shadow copies, then most likely (but not always, by the way), we are dealing with malware, and most likely with cipher clerk. Nowadays, most families of cryptographers delete shadow copies , since if this is not done, people will not pay the ransom, since they can restore their files for free. Consider how many infections were stopped in our laboratory due to this approach. It is logical to assume that this number should grow exponentially, because the number of attacks by cryptographers using this technique is also growing rapidly. Here, for example, the number of attacks that we have blocked in the last 12 months using our approach:
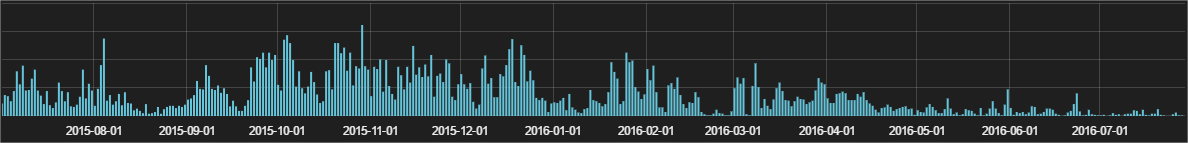
But in the diagram we see the exact opposite of what was expected. How is this possible? In fact, this “phenomenon” has a very simple explanation: we use this approach as a “last resort”, when no other safety precautions could detect anything suspicious, and therefore this rule is triggered, which blocks the cipherteader's attack. We also use this approach for internal purposes, as a result of which we can analyze in more detail those attacks that were blocked at the “last turn”, and then improve all previous levels of security. We also use this approach to assess how well or poorly we stop coders: in other words, the lower the values, the better our core technologies work. So, as you can see, the efficiency of our work increases.
Article author: Louis Corrons
Original article: Tales from Ransomwhere: Shadow Copies
Source: https://habr.com/ru/post/308732/
All Articles