Why do you need SSL security certificates in 3CX Phone System
Despite its fantastic capabilities, the Internet is a rather insecure place. This is due to the fact that without the use of special methods, we have a rather vague idea of who we still communicate with. Besides the fact that some organization or person tells us about itself, we have no opportunity to confirm the veracity of these words. And here SSL certificates help us.
SSL certificates “for dummies”
The SSL certificate is the “ID” of the resource we are visiting. If the name of the resource (as a rule, the domain name of the web site) does not match the certificate issued for this name, there are good reasons to suspect that the “king is not real”. Imagine that the attackers registered a domain name, very similar to your bank's FQDN, and copied the original credit card data entry interface. If you do not use the certificate (as it often was before), you will very easily, quickly and quietly give your money to criminals.
A similar situation can occur with the 3CX system. Without a reliable “identity card” server attackers can lure the credentials of the administrator or extension numbers, and then tell a huge amount. Therefore, starting with 3CX v15, the use of SSL security certificates becomes mandatory.
When you connect to the 3CX interface by entering the server URL (for example, company.3cx.eu), you can always make sure that you are logged in to your server. This shows the certificate in the Issued to: field. It shows the FQDN of the server. An SSL certificate can be issued not only for a specific host name (company.3cx.eu), but also for the entire top-level domain (* .3cx.eu). This certificate covers all nodes in the 3cx.eu domain, but costs a bit more (called wildcard certificate).
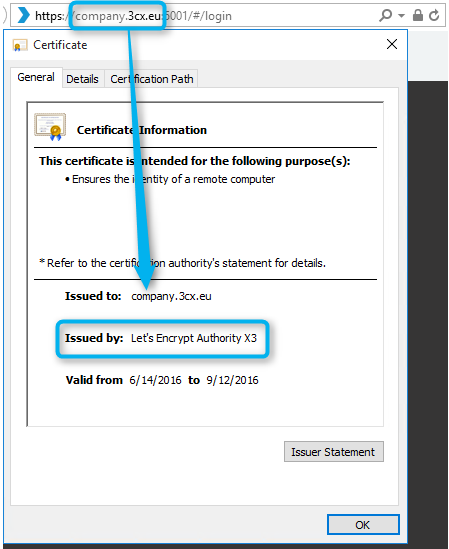
The whole essence of resource certification is contained in the Issued by line : The information in this line is the main difference between the so-called. a self-signed (“self-appointed”) certificate and a certificate issued by a public, trusted and respected certification body. It can be Let's Encrypt, GoDaddy, VeriSign, GeoTrust, etc. Using a self-signed certificate, you show that you trust yourself, but this does not mean that someone else will be ready to trust you. For example, a self-signed certificate for the www.bank-of-igor.com domain will not cause any trust - who will vouch for the people behind this bank? Almost distrust looks like this browser warning.

Get SSL certificate
But what to do so that other people (or devices) start trusting me? How to confirm that 3CX administrators, 3CX software clients and hardware IP phones are actually connecting to a trusted system? All you have to do is contact the certification authority (“the Ministry of the Interior”), which is responsible for checking your system in various ways. After verification, he issues her a certificate. Since a serious certification authority is trusted by everyone, there is no reason not to trust its certificates.
How to start obtaining a trusted certificate?
If you submit a public certificate (extension .crt, but may have several extensions) as your house, visible to everyone, then the key to the certificate (extension .key) is the key to your house, allowing you to enter it. In computer terms, the key allows you to encrypt and decrypt the traffic between you and the server, while ensuring the authenticity of the server.
By preparing a certificate request, you first generate a secret key (which can be password protected) for your certificate. However, there is one problem. The key to the apartment should always be kept only with you - it can not be transferred to third parties. After all, it does not cost the employees of these organizations to use the key for criminal purposes. Therefore, the process of obtaining a certificate provides another link - a special temporary certificate request (certificate signing request, extension .csr), which is generated based on your private key. It is this request, and not the key itself, that you pass to the certification body.
The certificate request contains information about your company and the domain name for which you want to issue a certificate. Then you send the CSR request to the certification authority. The certification authority certifies your “decency” as stated and sends you back the generated SSL certificate. Also, the certification body ensures that only you, the owner of the key to the certificate, have the right to this certificate and to the resource for which it is issued.
Both the private key and public certificate are stored on the 3CX web server.
I just want to test 3CX
But what if you only want to test 3CX, without wasting time getting a certificate to the server? You can quickly generate a self-signed SSL certificate. It is enough to specify your FQDN name and the certificate will be ready. However, note that this configuration is not supported by 3CX in the future. In addition, you will not be able to perform automatic remote configuration of supported IP phones - they only support trusted certificates.
useful links
- Free trusted SSL certificates are issued by the company Let's Encrypt for 90 days
- A utility for generating a secret key and a request certificate signing request from 3CX
- Resource for free self-signed key generation
- Using trusted certificates for your FQDN on the 3CX server
')
Source: https://habr.com/ru/post/308258/
All Articles