Cisco and Fortinet confirmed the presence of vulnerabilities published by The Shadow Brokers hackers

At the end of last week (August 13), the network reported that the cyber grouping The Shadow Brokers had uploaded an archive of data stolen from another hacker group Equation Group. Many observers and security experts associate the latter with the NSA, in particular, it is assumed that it was their representatives who worked on the most well-known cyber-weapons - including the Stuxnet worms, Flame, Duqu and others.
As stated, among the programs stolen from the Equation Group were vulnerabilities for Cisco, Juniper and Fortinet products, as well as several Chinese manufacturers of network equipment. Now there is evidence that hackers have created exploits for vulnerabilities in the marshutizatorami these vendors. Moreover, Cisco discovered 0-day in its products, for which a security bulletin appeared only on August 17.
')
What happened
The Equation Group is associated with penetrations into the computer networks of state institutions, telecommunications companies and other structures in different countries - for example, Kaspersky Lab in 2015 published information about hacker attacks on targets in Russia, Iraq and Iran. In addition, it is believed that this cyber group is closely related to the Stuxnet virus, which was developed by order of the US National Security Agency to combat Iran’s nuclear program.
In turn, hackers from the Shadow Brokers were able to attack the resources of the Equation Group and gain access to "the full state cyber weapon set." The kidnappers published a message stating that they would sell the best of the stolen programs to the buyer who offered the highest price.
In addition to the paid part of the archive, hackers laid out in the free access of its small part. According to Shadow Brokers, if they manage to collect 1 million bitcoins (~ $ 568 million), then some of the stolen spyware will be posted for free download.
Screenshot Shadow Brokers archive
What does Cisco and other vendors
As evidence that the hackers did indeed succeed in stealing the “cyber weapon”, representatives of Shadow Brokers published a code that they claim is intended to bypass the security systems of popular vendors' routers. Experts interviewed by journalists, who familiarized themselves with the presented code, reported that the code is really functional and can solve the problem of manipulating and redirecting traffic as it passes through the router.
According to The Wall Street Journal, the published code snippet is applicable to routers from Cisco, Juniper, and Fortinet, as well as Chinese vendors Shaanxi Networkcloud Information Technology and Beijing Topsec Network Security Technology.
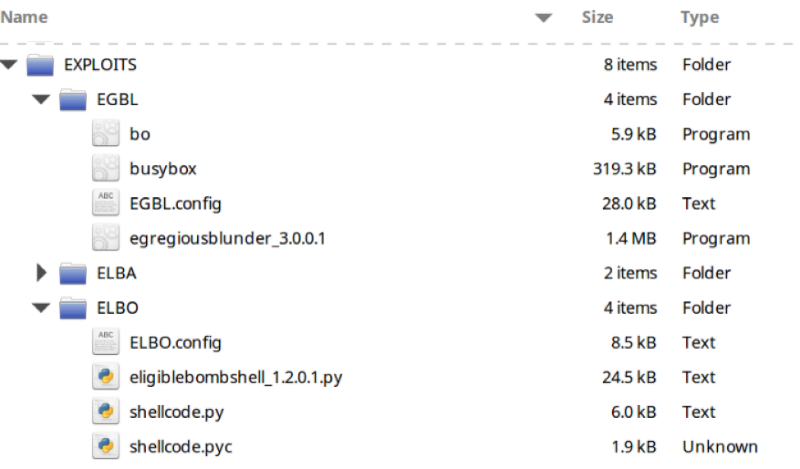
Later, Cisco representatives confirmed that the exploits presented in the stolen archive under the names EPICBANANA, JETPLOW and EXTRABACON exploit vulnerabilities in the company's products. ASA routers, PIX firewalls and Cisco Firewall Services Modules were at risk.
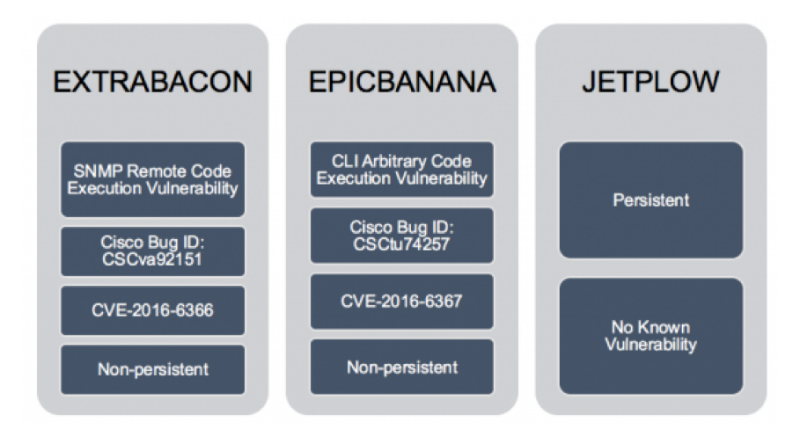
At the same time, if one of the used vulnerabilities ( CVE-2016-6367 ) was eliminated in 2011, the patch for the second 0-day error ( CVE-2016-6366 ) appeared only on August 17. The bug is associated with the implementation of the SNMP protocol and can give an attacking root-rights in the system, which will allow the execution of arbitrary code (RCE).
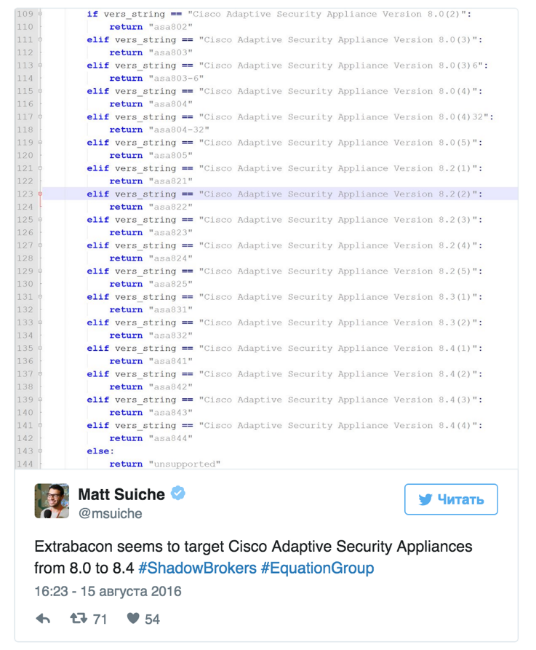
The media reports that the Extrabacon exploit exploits a 0-day-vulnerability, a security bulletin for which was published recently. In the exploit code there is a restriction on its execution in versions from 8.0 (2) to 8.4 (4). As experts of Positive Technologies have found out, on newer versions - for example, 9.2 (2), the script with a certain refinement can successfully work.
Security experts have already tested the performance of the presented exploits and confirmed that they can actually be used to carry out cyber attacks.
How to protect
Since there is not yet a full patch for this vulnerability, Cisco representatives recommend using Snort rules to improve security. In turn, Fortinet released its own security bulletin , and researchers published a utility to check for the presence of a vulnerability in the hardware of this vendor.
Experts at Positive Technologies recommend installing all the latest security updates published by vendors, as well as implement the recommendations contained in the security bulletins. In addition, it is possible to protect against attacks using detected vulnerabilities by using specialized means of protection. For example, the security and compliance monitoring system MaxPatrol 8 successfully detects both of the described vulnerabilities in Cisco equipment.
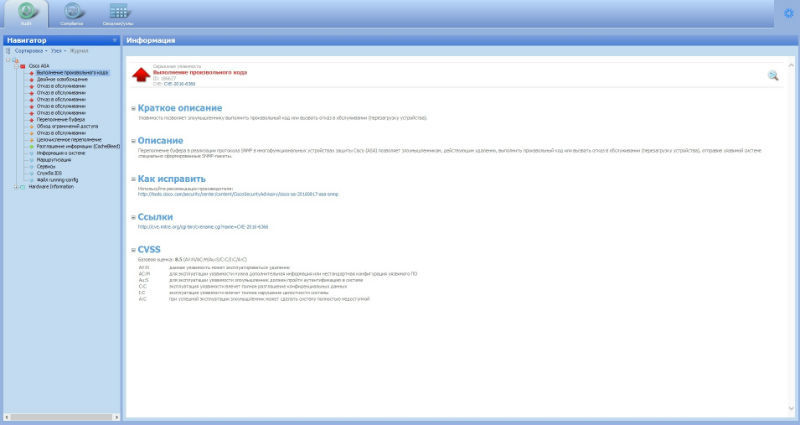
Positive Technologies experts have developed a signature for Suricata IDS, which allows to detect the exploitation of Cisco vulnerabilities and prevent possible consequences. The signature can be found in the official repository twitter.com/AttackDetection/status/766413545672146945 . In addition, all the payloads available for the EPICBANANA exploit were generated and a rule was developed for detecting attacks using it: twitter.com/AttackDetection/status/766695730694291456 .
Source: https://habr.com/ru/post/308064/
All Articles