Rockett Bank jeopardized customer personal data and bank card data
From time to time, I conduct external security audits of IT companies supporting Bug Bounty. According to the Rocketbank page, it can decide on remuneration in cases of detecting serious and publicly undisclosed vulnerabilities.

For the current year, I discovered a significant number of vulnerabilities in the Rocketbank system, including those that allow obtaining personal data of all clients, implement a XSS attack. In this article I will describe the results of the last Rocketbank audit that I conducted.
In the period from 07/31/2016 to 08/03/2016, I conducted a regular security audit of Rocketbank, which resulted in the discovery of the following vulnerabilities:
')
For any operations, Rocketbank generates a receipt page that can be sent to the post office or viewed via a link in the browser. If a receipt for a transfer or replenishment transaction between friends (method / api / v5 / friend_transfers / income), then the name of the POS terminal on the receipt page is generated as follows: “request% NAME OF FRIEND FROM SMARTPHONE CONTACT%”, while the HTML characters in friend's name not screened.
Thus, you can embed the code on the receipt page by simply changing the contact's name to html code that the attacker wants to execute on the receipt page.
Illustrative example of execution:
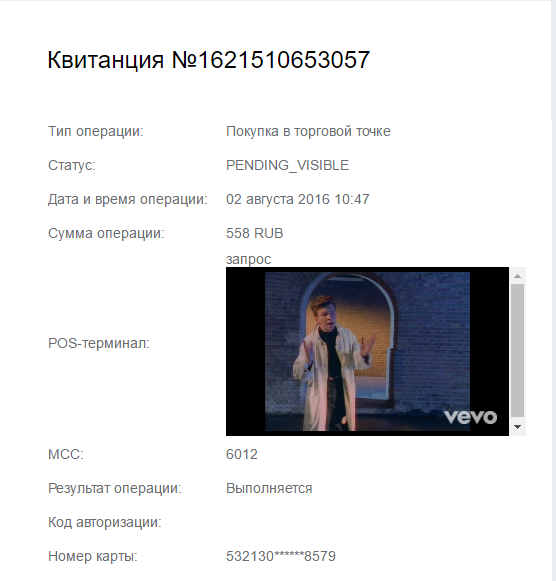
Request:

Answer:
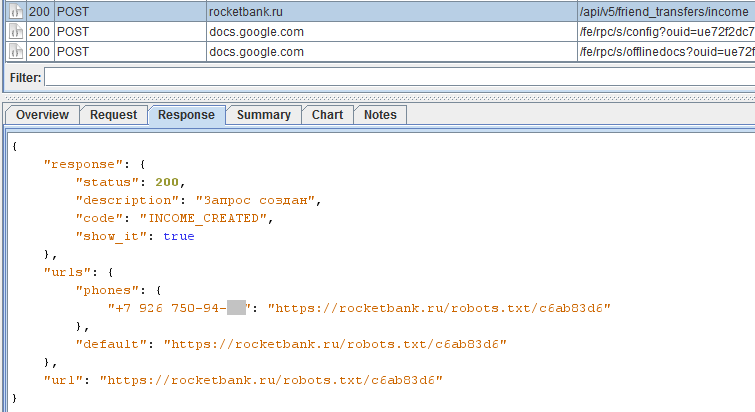
We get a link to the receipt:

The link is a receipt page with JavaScript code that changes the receipt page to the funds transfer page with the interception of bank card data:
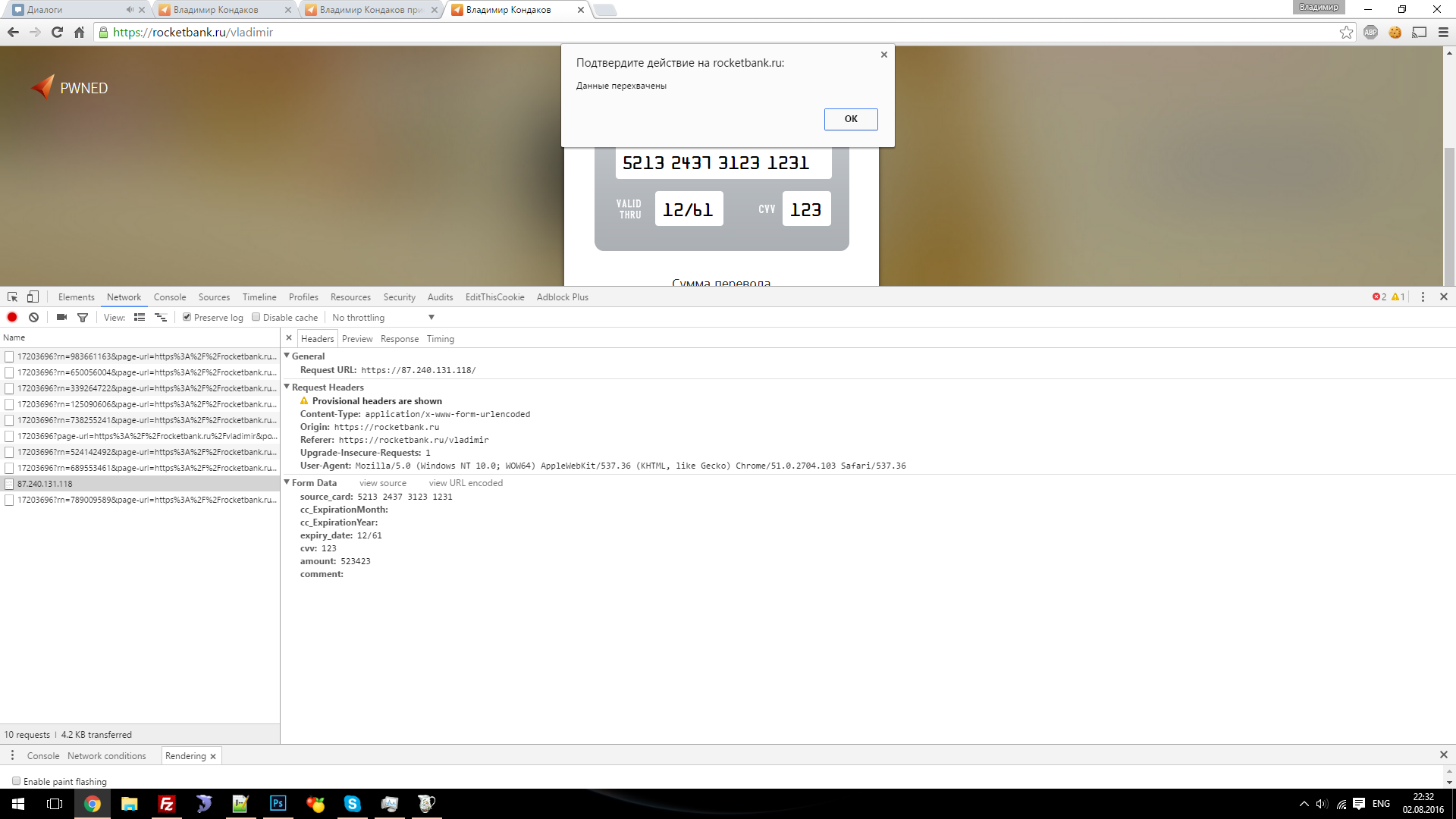
Using this vulnerability, an attacker could, for example, change the receipt page to the money transfer page with the interception of bank card data.
When an application requests invited clients, the / api / v5 / invitations / all method discloses, in addition to the name and surname from the passport, a telephone number and an email address.

Using this vulnerability, an attacker can obtain personal data of the Rocketbank client, which he invited.
Immediately after the audit report was compiled, I sent it to Roketbank: to the security service and technical director Oleg Kozyrev. Vulnerabilities were eliminated within an hour, but no response was received within a week.
Only after I notified Roketbank that I was planning to publish the results, I received adequate feedback from Roketbank, however, Oleg said that they no longer support Bug Bounty:
After a lengthy discussion, the Rocketbank offered a reward, which I was forced to refuse.

For the current year, I discovered a significant number of vulnerabilities in the Rocketbank system, including those that allow obtaining personal data of all clients, implement a XSS attack. In this article I will describe the results of the last Rocketbank audit that I conducted.
In the period from 07/31/2016 to 08/03/2016, I conducted a regular security audit of Rocketbank, which resulted in the discovery of the following vulnerabilities:
')
Crossite scripting
For any operations, Rocketbank generates a receipt page that can be sent to the post office or viewed via a link in the browser. If a receipt for a transfer or replenishment transaction between friends (method / api / v5 / friend_transfers / income), then the name of the POS terminal on the receipt page is generated as follows: “request% NAME OF FRIEND FROM SMARTPHONE CONTACT%”, while the HTML characters in friend's name not screened.
Thus, you can embed the code on the receipt page by simply changing the contact's name to html code that the attacker wants to execute on the receipt page.
Illustrative example of execution:

Example of implementation:
Request:

Answer:

We get a link to the receipt:

The link is a receipt page with JavaScript code that changes the receipt page to the funds transfer page with the interception of bank card data:

Using this vulnerability, an attacker could, for example, change the receipt page to the money transfer page with the interception of bank card data.
Vulnerability to get personal data of invited clients
When an application requests invited clients, the / api / v5 / invitations / all method discloses, in addition to the name and surname from the passport, a telephone number and an email address.
Example of implementation:

Using this vulnerability, an attacker can obtain personal data of the Rocketbank client, which he invited.
Immediately after the audit report was compiled, I sent it to Roketbank: to the security service and technical director Oleg Kozyrev. Vulnerabilities were eliminated within an hour, but no response was received within a week.
Only after I notified Roketbank that I was planning to publish the results, I received adequate feedback from Roketbank, however, Oleg said that they no longer support Bug Bounty:
In addition, I’ll clarify that there’s no “find a bug - we’ll pay” policy. What is written on the site about this is just words that I wrote 3 years ago. After the deal with the Discovery, I do not consider it necessary to continue this practice.However, information on the reward for detecting vulnerabilities is still located on the Rockettbank website.
After a lengthy discussion, the Rocketbank offered a reward, which I was forced to refuse.
Source: https://habr.com/ru/post/307898/
All Articles