Discovered a new hacking mechanism for cloud virtual machines

Cybersecurity experts at Amsterdam Free University have discovered a new mechanism for hacking a cloud-based virtual machine. The mechanism involves several stages. For hacking using the notorious technology Rowhammer.
The first stage is to rent a cloud virtual machine, or several machines, on the same host as the victim.
Cloud virtual machines are used to test the launch of applications, software or Internet pages. At the same time cloud hosting is divided into public, group and private.
Next, you need to find the vulnerable cell "in the neighborhood" with the memory of the victim. After it remains to wait until the deduplication process starts, and expose the cell to the attack of Rowhammer.
Deduplication (elimination of duplicates) is a specialized data array compression method that uses duplicate copies of duplicate data as a compression algorithm. When a duplicate element is detected, it is replaced with a reference to the unique occurrence (or an existing link is redirected to it), and the space occupied by the duplicate is released. Deduplication is widely used in virtualization systems. It allows you to conditionally allocate duplicate data elements of each of the virtual systems into a separate space.
')
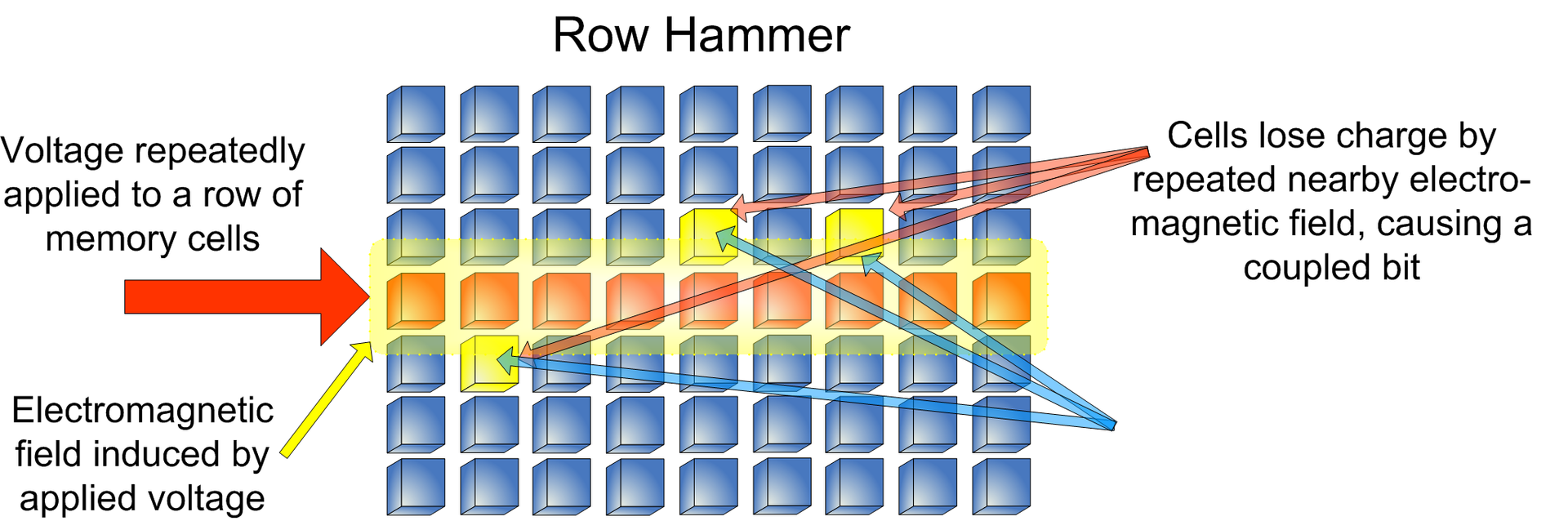
Image website eurosoft-uk.com
When merging copies occurs, the attacker will gain access to the physical DDR-memory of the victim's computer. After that, it can read, copy and even change the contents of the memory cells. For this purpose, just used attack Rowhammer.
Rowhammer was developed in 2014. If hundreds and thousands of times in a fraction of a second to access specific lines of memory (“knocking” them like a hammer, hence the name hammering), then, as a result of certain physical phenomena, this can affect the neighboring memory segment by switching the values of its cells (bits) from zero to one and vice versa.
Having the opportunity to influence the content of memory areas (up to blocked), attackers can carry out attacks that lead to elevation of privileges to administrative ones. And then it becomes possible to launch malicious code or intercept actions of users or programs. A new type of hacking is called Flip Feng Shui (FFS).
Employees of the Amsterdam Free University have tested the technology on virtual cloud machines with Ubuntu and Debian operating systems.
American researchers from the company Third I / O at the Semicon China conference held in China presented a report on the vulnerability of Rowhammer and DDR4 chips. Previously it was believed that DDR3 and DDR4 are not affected by this vulnerability.
But in March 2015, researchers at the Project Zero Google team told us that the problem lies in changing the values of individual data bits (bit flipping) stored in DIMM modules of DDR3 chips.
Before the DDR vulnerability was discovered, hacking virtual cloud machines was limited to viewing and data theft.
Source: https://habr.com/ru/post/307828/
All Articles