Known cyber-grouping Equation Group could undergo large-scale hacking
 A group of hackers called Shadow Brokers has published information in her blog, according to which the compromised cyber grouping of the Equation Group is set for sale at a special auction.
A group of hackers called Shadow Brokers has published information in her blog, according to which the compromised cyber grouping of the Equation Group is set for sale at a special auction.The peculiarity of the potential data breach is that the Equation Group or, in other words, the FiveEyes (Tilded Team), is very likely to be authored by the most well-known types of cyber weapons, including, Stuxnet, Flame, Duqu, Regin, EquationLaser, etc. According to the information which was published by Snowden, FiveEyes is directly related to the special services of the NSA, CIA, GCQH.
In addition to the paid part of the archive with the compromised data, which is put up for auction, the audience is represented and the freely distributed part is in encrypted form. For downloading archive data, a link to file sharing networks is provided. The archive contains eqgrp-auction-file.tar.xz.gpg files, as well as eqgrp-free-file.tar.xz.gpg.
To decrypt the second, you can use the password theequationgroup. Below is the directory tree of this archive.
')

Fig. Directory tree eqgrp-free-file.tar.xz.
A free archive contains a small amount of information that does not directly indicate that the data belongs to the Equation Group.
We auction best files to highest bidder. Auction files better than stuxnet. Auction files The party which sends the most bitcoins to the address: 19BY2XCgbDe6WtTVbTyzM9eR3LYr6VitWK before bidding. Very important !!! When you send it to you. You add OP_Return output. In Op_Return output you put your (bidder) contact info. We suggest using bitmessage or I2P-bote email address. No other information will be disclosed by us publicly. Do not believe unsigned messages. We will contact the winner with decryption instructions. Winner files for public.
Information about the auction.
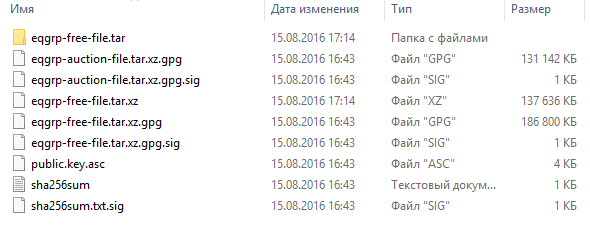
Fig. Directory tree EQGRP-Auction-Files.zip. The archive contains a file with an encrypted archive eqgrp-auction-file.tar.xz.gpg, which can be decrypted after the auction won and receiving the key.
It is difficult to say what important data hackers managed to get as a result of the leak. Anyway, the potential of the Equation Group and its malware is enormous, and the size of the archive is not that big. For comparison, we can cite the case of the compromise of the Hacking Team cyber group, which we wrote about last year. In that case, the archive size was in the hundreds of gigabytes and contained all the achievements of the Hacking Team, as well as the mail correspondence of the group members.
Source: https://habr.com/ru/post/307792/
All Articles