Security Week 32: Sauron project, iOS vulnerability, PLC worm
 Meanwhile, a cozy security digesters one year old. How fast time flies! In the issue for the 32nd week of last year, I wrote about the hole in Android, vulnerabilities in Fiat Chrysler cars and the concept of Do Not Track 2.0. What changed? I still don’t feel a lack of security news, quite the contrary. There are changes for the better, but not everywhere, which can be seen on the example of these three long-standing messages.
Meanwhile, a cozy security digesters one year old. How fast time flies! In the issue for the 32nd week of last year, I wrote about the hole in Android, vulnerabilities in Fiat Chrysler cars and the concept of Do Not Track 2.0. What changed? I still don’t feel a lack of security news, quite the contrary. There are changes for the better, but not everywhere, which can be seen on the example of these three long-standing messages.Stagefright. Since the discovery of the vulnerability, several more media- related issues have been identified, and recently serious holes have been added to them, affecting mainly devices on the Qualcomm platform. Such a big work on the bugs is a good sign, especially since during the year the problem began to be solved by the delivery of patches. Not on all devices, and with varying success with different vendors, but there are positive developments.
Car safety remains a difficult topic. On the one hand, the revelations of the level of last year’s news of a wireless car hacking did not appear, on the other - the absence of loud revelations does not speak about security. Rather, the reason is the closeness of the auto industry with respect to independent researchers. A good story on the topic happened this week: researchers from the University of Birmingham revealed details of the vulnerability of the standard anti-theft system, which has been installed on Volkswagen cars since 1995. Intercepting signals from a wireless keychain of such a system turned out to be quite simple. It is important that all the data were in the hands of researchers already in 2013, but VW slowed down the publication of the report by a lawsuit. They can also be understood, but judging by indirect data, only the public did not know about the vulnerability of the alarm, but the criminals have been using it for a long time. In this situation, the owner of the car is better to know about the potential insecurity of the standard system.
Well, privacy. With privacy did not become better, rather the opposite. Existing systems and associated encryption algorithms are tested for reliability by researchers, plus the entire year there is a discussion about access to encrypted data by government agencies and organizations equal to them. But there are also positive aspects, such as the transition to encrypting WhatsApp and Viber data. Let's go back to the news of today. Absolutely all editions of the digest are available by tag .
')
Project "Sauron" - a new targeted campaign takes into account the mistakes of predecessors
News Research "Laboratories". Symantec research .
Earlier this week, Lab experts and researchers from Symantec independently publish a report on the new APT class attack. We call it ProjectSauron, our colleagues are Strider. "Sauron" uses sufficiently advanced methods of attack, collection and exfiltration of data, although not as steep as, for example, in The Equation . Perhaps the main features of the attack is the maximum confinement for the victim and the maximum difficulty of detection. Malicious components are stored only in RAM, for each victim creates its own set of malware, domains and servers for data output. And for exfiltration, a whole arsenal of tools is used: from standard, but using strong encryption, to operating internal mail servers and outputting data from air-gapped systems using cleverly tagged flash drives. A positive point is the presence of methods of dealing with crowbars and such a classification: the malicious activity was detected with the help of our solution to protect against targeted attacks . More technical details in the detailed “Labs” report in PDF .

A screenshot of our advanced attacker tracker hints that there are a lot of such attacks.
Critical RCE vulnerability closed in iOS 9.3.4
News Advisory on the Apple site.
The winner in the nomination "The shortest news of the week." In the next update of the iOS mobile operating system, Apple closed a dangerous vulnerability that allowed an application to execute code with kernel privileges. Everything! Apple can afford it: the system code is closed, relations with external researchers are also non-public. Even Apple’s recently launched Bug Bounty program is private: as many as two dozen researchers have been invited to the program, they don’t even tell us who it is. By the way, Apple thanks the Chinese team Team Pangu, a group of hackers specializing in jailbreaks, for information about the vulnerability.
Researchers have shown proof of concept worm living in programmable logic controllers.
News Study in PDF .
And here is the compote promised last week - another interesting study from the Blackhat conference. Researcher Maik Brüggemann of OpenSource Security spent quite a lot of time analyzing the interaction of Siemens programmable logic controllers (PLC) with the TIA Portal control console.
Finding holes in the security system, in particular in the methods of checking the integrity of the code and password protection, he showed how you can infect the controllers themselves. This is a key point: if earlier the discussion of the security of industrial systems was built around the protection of control software and systems, now we are talking about a possible compromise of the controllers themselves - devices are relatively simple and therefore not perceived as a threat. But in vain: the demonstration shows, for example, how to establish communication between the worm and the command center outside the network.
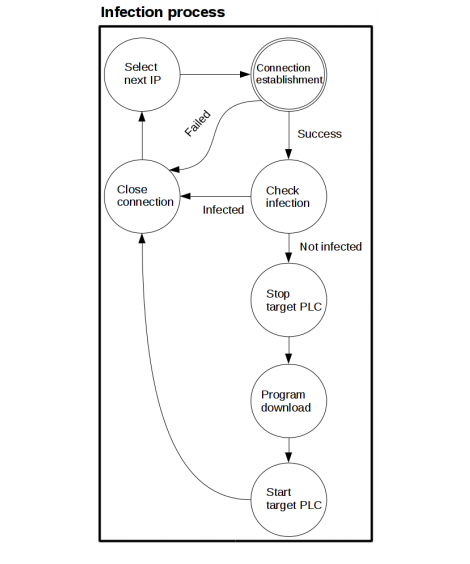
Fortunately, this is still proof of concept, and not a real worm. The iron manufacturer, Siemens, asserts that the demonstration was of a very theoretical nature. In particular, to implement his ideas, the researcher turned off the security systems, which under normal conditions should always be included. Nevertheless, the picture turns out to be beautiful and frightening: in today's production of potentially vulnerable computers, and so dozens, and then it turns out that hundreds. Bruggemann concludes: manufacturers need to change their approach to security. Good, but not concrete: in this case, you can start with monitoring the integrity of the code for the PLC, and preferably not only by the vendor.
What else happened:
Serious vulnerability in TCP protocol implementation in Linux, allowing to intercept traffic.
The authors of Carbanak are possibly involved in the attack on the Oracle POS system.
Microsoft seems to have big problems with the SecureBoot system (and jailbreakers have a holiday).
 Antiquities:
Antiquities:"V-492"
Resident very dangerous virus. It infects COM files when they are executed. The length of the file does not check. It copies itself to the end of the file and changes its first 6 bytes (JMP xx xx zz zz zz).
When activated, it searches for the file C: \ COMMAND.COM and infects it. It then remains resident in memory. To do this, the virus copies itself to the interrupt vector table at 0000: 0200. Periodically erases several sectors with random numbers. Changes int 1Ch and int 21h. Contains the command 'PUSH 100h', therefore it does not apply to computers with an 8086/88 processor.
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 87.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/307662/
All Articles