Random User-Agent - version two
Two years have passed since the first version of this extension for Chromium-based browsers (works in Google Chrome, Yandex.Browser, etc.), the task of which is simple and clear - to hide the real User-Agent. At the moment, this extension works for +6.000 users (which is very modest) , and a few days ago I received a letter in the mail asking for a little refinement. Assessing the state of the code, which no one touched for two years, it was decided to rewrite it from scratch. Four days of work, and voila - we meet a fresh major version, significantly improved and with new functionality.

Under the cut there will be some thoughts about both slightly more anonymous web surfing, and setting up the Google Chrome browser, and why this extension might be useful. Somewhat experienced Anonymous will not find anything interesting in the post for themselves, therefore, both for them and for the most impatient, traditionally - the source code on GitHub and the extension in Google Webstore .
About anonymity
I will not say that it makes sense to let all external network traffic through VPN / OpenVPN / Tor and other encrypted tunnels; I will not say that if competent people with sufficient resources need to grab your ass, most likely they will grab (you don’t use only the mobile Internet in the third world on anonymous SIM cards, constantly moving and looking in network only using telnet via Tor?) .
The anonymity and convenience of surfing the web are increasingly mutually exclusive. 3rd party cookies are very convenient (no need to log in to resources using a single authorization) , but they also allow you to successfully track your movements through other resources. Using proxy / socks gives additional means of hiding the real IP address, but sometimes they are successfully determined by many resources (Avito, Picaba, for example) , and because of their use, access to the resource is closed to you. The use of aggressive AD-blockers is determined by the sites, and they are carefully asked to disable them. Therefore, we have to balance on the edge - convenience, or safety.
Yes, for me, security is synonymous with anonymity. "No, I have nothing to hide, but this is absolutely not your business" (c) habrazhitel.
I use different browsers. At the same time, FireFox, TorBrowser, and Google Chrome are quite often launched (I use it most often) . Different browsers have different sets of plug-ins / proxies, and, accordingly, different settings. Each of them deserves a separate discussion, but now I would like to talk again about Google Chrome. Below I will list the default settings of this browser, which may need to be changed:
- Sync settings are redundant;
- "Settings"> "Advanced synchronization settings"> We mark only "Services", "Extensions", "Settings" and "Bookmarks" (this list can be shortened to "Extensions", "Settings") ;
- We also enable encryption using a code phrase;
- Follow the link and turn off everything;
- Popular search engines track your actions;
- We set as a search engine (it seems to be anonymous)
https://duckduckgo.com?q=%s;
- We set as a search engine (it seems to be anonymous)
- The storage of cookies is permitted for everyone;
- "Settings"> "Content settings"> "Cookies"> "Do not allow sites to save data" + "Block data and cookies from third-party sites";
- When visiting resources where cookies are necessary for functioning, click on the "cookies" in the browser's line> "Show cookies and other data ..."> "Blocked"> Those that need to be stored after closing the browser - mark as "Allow", otherwise, "Delete on Exit";
- From time to time, check the exclusion lists, removing all unnecessary from the allowed ones;
- The maximum storage period for cookies cannot be limited;
- We set a Limit Cookie Lifetime , set a limit of 7 days, for example. Yes, once a week you will have to re-enter your resources, but the tracks will not be relevant for more than a week (unless the track analyzer has good logic) ;
- Launching content plugins (and a flash sieve is one of them) is allowed by default;
- "Settings"> "Content Settings"> "Plugins"> "Refill permission to launch plug-in content";
- Open this link and turn off the "Adobe Flash Player" (if you need to watch online cinema, you will have to temporarily turn the pens back on, but HTML5 players will immediately understand that there is no flash and it will start correctly) ;
- Access to the camera, microphone, etc. is better to disable by default;
- All the same "Settings"> "Content Settings" - independently prohibit access to everything that is not critical right now;
- Be sure to disable "Access to plug-ins outside the test environment" and location;
- Sending "Do Not Track" is disabled;
- I very, very much doubt that anyone follows the rule not to track those who send this header, so decide for yourself whether to put it in Settings> Personal data, or not;
- Passwords and forms are saved;
- "Settings"> "Passwords and forms" - be sure to turn off both checkboxes. To clarify the reason, I think it makes no sense;
- The browser is susceptible to IP address leakage via WebRTC;
- We install the WebRTC Leak Prevent plugin, allow it to work in the "Incognito" mode, specify "Disable non-proxied UDP" in its settings;
- We are checking, for example, on this page ;
- The referer is sent uncontrollably, which allows all resources to determine where you came from;
- We set Referer Control , in the settings we specify "Referer Control status" - "Active", and "Default referer for all other sites" - "Block";
- Some sites (for example, Habrastorage) use the referer check, so the plug-in's work can get a little bit, but you need to overpower it, and learn how to write regular exceptions;
- There is no control over the launch of JS scripts that are engaged in tracking and analytics;
- Favorite ad-blocking plugins are detected by visited resources and close access to content;
- Try to use less popular, but no less effective. Until recently, uBlock was included in this list, but the last time I use is Adguard AdBlocker , as it is still very few people detected and consumes memory several times less than counterparts.
About what extension to use for proxying and where to get proxy lists - you will have to answer yourself. I can only say that it is best to use a chain of proxies, but from this in 9 out of 10 cases, the surfing speed just dies. Public proxy lists are not tenacious at all. Those that were purchased for blood - a little more tenacious, but not significantly. There are not many freebies here, and for comfort it is best to purchase your own proxy server (yes, such services are provided, and quite a few people; when paying, do not use real cards, names, ip-addresses - of course). The fact that all external traffic must first be allowed through tunnels - I don’t remind you, you already know everything.
Basic identification methods
I apologize in advance for the terminology used below. It is not entirely correct, but, as it seems to me, it is simpler to understand.
User identification, the definition that these N requests were fulfilled by him, and not by someone else - is the main enemy of anonymization. Identification methods are divided into at least two large classes - using the client and server sides respectively. On the client side in the classical approach, it might look like this:
- The resource page contains in its body a link to a JS script, for example, google.analytics;
- The browser sends to the server that stores this same JS-script GET request;
- The server responds with the contents of the script;
- The browser executes the received script (loading additional "modules" if necessary) , receives from the browser information about its version, OS, installed plugins, installed fonts, screen resolution, locales, system time, and other tasty information;
- The script checks for the presence of a unique bun, or installs it to track your further movements in the network;
- The script sends the collected data + the name of the bun to itself for storage;
"Well, what of it?" - You ask, and you will be damn right. "Let them collect this data - I do not mind!" - Yes, yes, my friend! And while you think so, let's do some analysis. To visit the sites, you used Google Chrome version 52.0.2743.116 (the current version - you have auto-update enabled) running Windows 10 (the minor version suggests that you may not have installed the latest updates and, as a result, Windows Update is disabled) while in Russia and, presumably, in the city of Moscow (and the time zone corresponds) , from the IP provider "MTC", which has this pool tied to the Lyublinsky district, most likely using a laptop (judging by the screen resolution), and probably interested in buying a new car (because to fl go online drom you were looking for a used Mazda, and it was in Moscow on the site drom, for example, costs that the same analyst). Judging by the time of visits - you did it from the workplace and, probably, in this or neighboring area and work. If your social. the network uses a similar analytics service, then ... So you get it (an example is fictional, but not devoid of the grain of common sense) .
Do you understand why it is quite important to keep track of what scripts your browser launches? "Yes, I generally turn off JS by default!" - Someone will exclaim in the comments, and he will be right - this is more correct. That is more correct, not more convenient. Here, you still need to choose what is more important to you - safety, or comfort. Now 7 out of 10 sites simply do not work as they should without JS, and it is up to you to decide when to switch to telnet and move to a third world country, passing anonymous anonymous SIM cards. Ghostery is good, but even if it would give a 99% guarantee of blocking all analytics - 1% is still the place to be. There can be no universal rule, you just need to be vigilant and think a little bit with your head.
How does server-side authentication happen? Let's remember what http-demons access logs look like:
[meow@hosting /var/log]$ cat somesite.org.access_log | tail -3 10.12.11.254 - - [25/Jul/2016:15:51:16 +0700] "GET / HTTP/1.0" 200 5768 "-" "Mozilla/5.0 (compatible; MJ12bot/v1.4.5; http://www.majestic12.co.uk/bot.php?+)" 10.12.11.254 - - [25/Jul/2016:15:57:38 +0700] "GET / HTTP/1.0" 200 5768 "-" "Mozilla/5.0 (compatible; YandexBot/3.0; +http://yandex.com/bots)" 10.12.11.254 - - [25/Jul/2016:19:19:25 +0700] "GET / HTTP/1.0" 200 5768 "-" "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:30.0) Gecko/20100101 Firefox/30.0" Primitive. By default, the server saves 4 things about you:
- IP address from which the request came;
- The time when he came;
- What page you requested;
- What is your User-Agent?
Having secured the logs by IP, we will get everyone who could have come from your IP (if this is the IP on which NAT is - we will find out which of your neighbor subscribers has been). Grabbing the same User-Agent - we almost certainly get exactly a specific user. Plus, we can look at which pages he went, at what time and sequence, and if there is a debag-log, then it is possible and what data he entered on the site forms, and what kind of buns he has in the browser.
Chef, what to do?
It is possible to avoid 99.8% leaks of information - but this is very inconvenient in terms of usability. If to generalize, then your IP (provider and location) and User-Agent (used software, OS and their versions) can be attributed to the most critical information, since they are the most informative and unique. How to hide the real IP - we have already said. How to hide User-Agent? There are different ways, and the one described below is just one of many. Perhaps, it will seem to you a little more convenient.
With your permission, its main "chips" will be presented in the form of a simple list:
- Open source available on GitHub (I accept pull requests and Issues included) ;
- Replaces the User-Agent field in the HTTP headers of all requests;
- Compact (at the time of writing this post - only 45Kb in a zip archive) ;
- The User-Agent used is randomly generated, similar to certain types of browsers and OS (customizable; one could be used only one specific, but this approach would work only if very many people used this extension - so the user would be "lost" on the heap ) ;
- Automatically replaces User-Agent with a random one after a specified period of time, by pressing a button, or at the start of the browser;
- Able to use the User-Agent specified by the handles, and not use the generated one;
- Settings are synchronized between browsers (configurable) ;
- Includes support for protection from User-Agent detection using JavaScript tools (experimentally) - what was asked for so long (mock runs asynchronously, so it doesn’t hide successfully in all cases; as far as I know, no other extension can do this - correct me, if not right) ;
- Supports the list of exceptions (it is possible to use masks in the addresses) ;
- At the moment, Russian, English and Ukrainian localization;
- Free and without ads;
- WTFPL license;)
What does it look like?
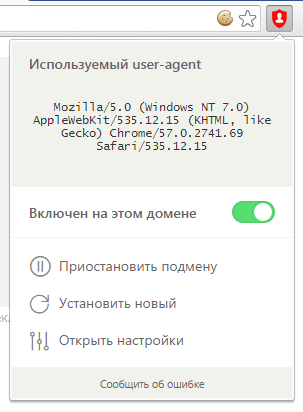
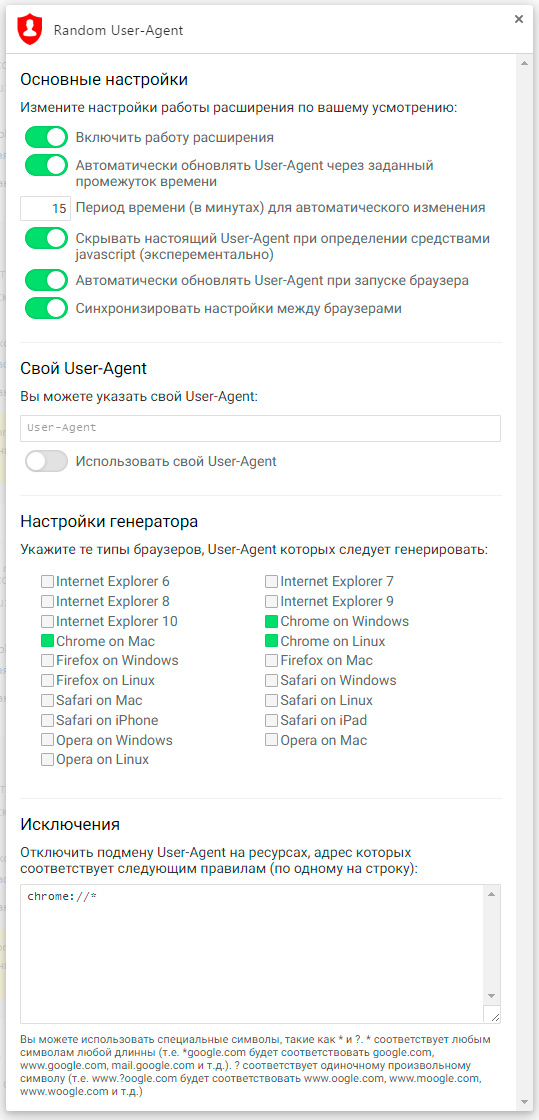
If you have a question, suggestion or bug report, but you can not write about it either in the WebStore or in the comments on the web site - here is a magic link for you . I would also like to write about how the extension itself wrote; how I created an object that supports onGet and onSet events of arbitrary properties and stores its data in the storage itself; how I came to the decision to implement the work of all the components of the extension using my own internal API - but this is a completely different story, and the source code will probably tell it better. I take this opportunity to say that I would be damn grateful in helping to translate the extension into languages other than Russian and English. If there is such a desire to be - just create a Issue in the repository with the theme “I will help with the translation to% name_ of the block name%”, or press the Pull-Request.
You can test both the work of the plugin and your anonymity, for example, through these links . But do not take the results of these tests too seriously.
And, with your permission, I will duplicate the link to the Random User-Agent extension in the WebStore .
Thanks nazarpc for a very quick translation into Ukrainian and pull-request. Straight great!
If you find ochepyatki, grammatical or punctuation errors in the text - write about them in a personal, please.
')
Source: https://habr.com/ru/post/307574/
All Articles