QRLJacking: a new type of attack threatens the security of users of a number of services and instant messengers
QR authentication is not as secure as is commonly believed.

Mohamed Baset (Mohamed Baset) - a specialist in information security, has developed a method of attacking users of instant messengers. This method is based on the use of QR codes. Now QR codes are used for authentication in many applications, including WeChat, Line and WhatsApp. SQRL (Secure QR Logins) was considered a completely safe method, but it looks like it is not.
')
The method shown by Baset includes both technology and social engineering. Such hybrid attack methods are used by attackers quite often. In order to attack the user of the instant messenger, the attacker must in some way force the victim to scan a special QR code. The easiest way to use phishing is here.
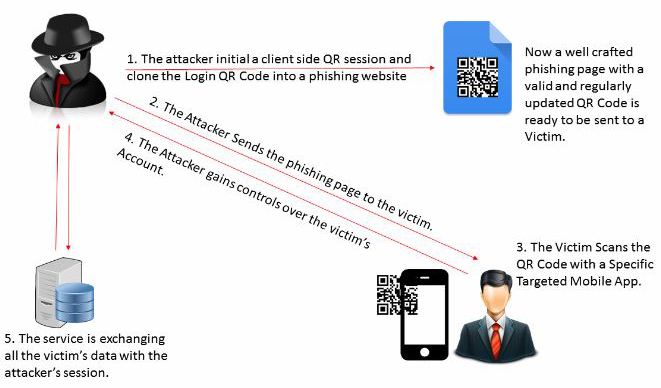
The method consists of the following steps:
1. The attacker initiates a client QR-session and clones the QR-login code to a phishing page;
2. The victim is sent a link to this page. The page looks quite safe;
3. The victim scans the fake QR code, and the application sends a secret token that completes the authentication process;
4. The attacker receives confirmation and can now control the victim’s account.
In order for the method to be more or less effective, the attacker must create a script that clones the temporary QR codes and updates them on the phishing site. The fact is that QR-Login limits the time of validity of QR-codes. The main condition of the attack - the victim and the attacker must be online at the same time.
QRLJacking has already been tested on a number of instant messengers, including QRLJacking on WhatsApp, WeChat, Line, Weibo, QQ Instant Messaging, QQ Mail, Alibaba. All attacks, according to the developer, were completed successfully.

The source code of the proof-of-concepp is published by Basset on GitHub .
In order to test the script in the work, you need to configure the server part :
1. Download "qrHandler.php" on the server. This script converts the string base64 QR-code into a valid image in jpg format. The default image file name is tmp.jpg. It is located in the root folder of the script files and is updated each time a php file is requested. To attract users, you can fake WhatsApp page, you can create a website with some attractive application for messenger users, etc.
2. Update the file "phishing.html", which is the source of the phishing web page.
Client configuration (attacker's browser)
1. Open Firefox
2. Register “about: config” and, of course, agree to be careful;
3. We look for the string “security.csp.enable” and change the value to false. After the script is tested, it is better to return everything back;
4. Install the add-on Greasemonkey , make sure that the file “WhatsAppQRJackingModule.js” is up and running.
5. Now everything is ready. Try opening the “ web.whatsapp.com ” example, waiting for the WhatsApp session to load. Greasemonkey starts working using the WhatsApp module;
6. We send a direct link to the phishing page of the victim.
We look at the result:
According to the developer, the QRLJacking method can be used not only for instant messengers, but also for other services. List of vulnerable resources and services below:
Chats : WhatsApp, WeChat, Line, Weibo, QQ Instant Messaging
Mailers : QQ Mail, Yandex Mail
eCommerce: Alibaba, Aliexpress, Taobao, Tmall, 1688.com, Alimama, Taobao Trips
Online banking: AliPay, Yandex Money, TenPay
Identification services: Yandex Passport (Yandex Mail, Yandex Money, Yandex Maps, Yandex Videos, etc ...)
Mobile Software: AirDroid
Other services: MyDigiPass, Zapper & Zapper WordPress Login by QR Code plugin, Trustly App, Yelophone, Alibaba Yunos

Mohamed Baset (Mohamed Baset) - a specialist in information security, has developed a method of attacking users of instant messengers. This method is based on the use of QR codes. Now QR codes are used for authentication in many applications, including WeChat, Line and WhatsApp. SQRL (Secure QR Logins) was considered a completely safe method, but it looks like it is not.
')
The method shown by Baset includes both technology and social engineering. Such hybrid attack methods are used by attackers quite often. In order to attack the user of the instant messenger, the attacker must in some way force the victim to scan a special QR code. The easiest way to use phishing is here.

The method consists of the following steps:
1. The attacker initiates a client QR-session and clones the QR-login code to a phishing page;
2. The victim is sent a link to this page. The page looks quite safe;
3. The victim scans the fake QR code, and the application sends a secret token that completes the authentication process;
4. The attacker receives confirmation and can now control the victim’s account.
In order for the method to be more or less effective, the attacker must create a script that clones the temporary QR codes and updates them on the phishing site. The fact is that QR-Login limits the time of validity of QR-codes. The main condition of the attack - the victim and the attacker must be online at the same time.
QRLJacking has already been tested on a number of instant messengers, including QRLJacking on WhatsApp, WeChat, Line, Weibo, QQ Instant Messaging, QQ Mail, Alibaba. All attacks, according to the developer, were completed successfully.

The source code of the proof-of-concepp is published by Basset on GitHub .
In order to test the script in the work, you need to configure the server part :
1. Download "qrHandler.php" on the server. This script converts the string base64 QR-code into a valid image in jpg format. The default image file name is tmp.jpg. It is located in the root folder of the script files and is updated each time a php file is requested. To attract users, you can fake WhatsApp page, you can create a website with some attractive application for messenger users, etc.
2. Update the file "phishing.html", which is the source of the phishing web page.
Client configuration (attacker's browser)
1. Open Firefox
2. Register “about: config” and, of course, agree to be careful;
3. We look for the string “security.csp.enable” and change the value to false. After the script is tested, it is better to return everything back;
4. Install the add-on Greasemonkey , make sure that the file “WhatsAppQRJackingModule.js” is up and running.
5. Now everything is ready. Try opening the “ web.whatsapp.com ” example, waiting for the WhatsApp session to load. Greasemonkey starts working using the WhatsApp module;
6. We send a direct link to the phishing page of the victim.
We look at the result:
What resources are vulnerable?
According to the developer, the QRLJacking method can be used not only for instant messengers, but also for other services. List of vulnerable resources and services below:
Chats : WhatsApp, WeChat, Line, Weibo, QQ Instant Messaging
Mailers : QQ Mail, Yandex Mail
eCommerce: Alibaba, Aliexpress, Taobao, Tmall, 1688.com, Alimama, Taobao Trips
Online banking: AliPay, Yandex Money, TenPay
Identification services: Yandex Passport (Yandex Mail, Yandex Money, Yandex Maps, Yandex Videos, etc ...)
Mobile Software: AirDroid
Other services: MyDigiPass, Zapper & Zapper WordPress Login by QR Code plugin, Trustly App, Yelophone, Alibaba Yunos
Source: https://habr.com/ru/post/307538/
All Articles