10 years of online security
Ten years is not a short time, even in a general historical context; during this time very significant changes can occur. For example, 1976 has nothing to do with 1966, and since then, with every new decade, everything has changed in the world. Due to the development of the Internet and the processes of globalization, cultural changes today may not have become so noticeable, but from the point of view of cybersecurity, a lot of time has passed since 2006.

Before the advent of the iPhone, there was still a whole year left, the first 3G networks were just beginning to appear in the world, and there were no mobile applications in their current form. Services for streaming music, publishing photos, social networks - all this was still in its infancy. In 2006, cybersecurity threats were markedly different from modern ones, since the resources available to hackers were very limited.
Today, almost all aspects of our life are somehow connected with the cloud; Almost everything is stored in the cloud - starting with our bank accounts and out-patient cards and ending with even more personal data; while today we are generating significantly more data than ever.
')
The nature of the threats evolved following this explosive growth of useful data. In the early 2000s, in most cases, threats and malicious code presented only minor troubles and were created with the aim of annoying or preventing users from working.
Then, in 2008, the Zeus Trojan Trojan virus appeared, which intercepted bank card details by tracing user-pressed keys and copying the form data sent. Years later, about a hundred people were arrested for stealing a total of over $ 70 million by using this Trojan program.
This is where the formation of a much more professional approach to cybercrime began. Viruses, Trojans and worms began to be created to steal money and critical corporate information. Varieties of the Trojan virus Zeus are rampant to this day, infecting numerous computers. In fact, they played an important role in one of the largest cyber attacks today - the attack against Target in 2013.
Here it is important to remember that as soon as a device connects to the Internet, it immediately becomes vulnerable. And as far as giving new things to the network opportunities, everyone who is involved in this should be aware of the risks involved. Take, for example, connected cars. The presence of Wi-Fi access and on-board entertainment systems that support streaming video, of course, add to the attractiveness of selling cars, but as shown by last year’s events, poorly designed security measures allow intruders to enter.
Every day we see more and more news about large and large-scale data breaches, and in this regard, it is rather curious to see how this changes the attitude of consumers to these leaks. Since 2013, nearly four billion data records have been compromised as a result of leaks in the world, and this news no longer shocks people. At such a scale, almost everything - starting with companies and their employees and ending with ordinary consumers - got used to the idea that leaks are inevitable, and the main question now is when it will break. But in general, the situation is not at all as hopeless as it seems. In the course of our recent study of the Connected Living 2025, we asked the 2000th generation about their opinion on data security issues. Two thirds of them said that they are wary of various threats, and there are much more such respondents than those who are relaxed and do not see particular dangers, or, conversely, are overly suspicious. Thus, the results of the survey indicate that today people are aware of the importance of protecting their data.
If the past ten years have taught us something, it is that the perimeter protection technologies are not able to provide an adequate level of security. No matter how high or strong the wall you build, the enemy will always find a way to bypass it - go on the other side or crawl from the bottom.
Despite the increase in data leakage, companies continue to use firewalls, threat tracking tools and other leak prevention tools as a basis for their security strategies. However, most IT professionals readily admit that in the event of a security perimeter breach, their corporate data and customer information will be at risk.
This does not mean that the perimeter of security no longer matters. This only suggests that perimeter protection should not be the only tool in the arsenal of companies to protect against all sorts of threats. Instead, IT professionals need to accept the fact that leaks are unavoidable, and work to make these leaks safe — by using security measures that are closer to the data and to users, including through encryption technologies and multi-factor authentication.
The development of the following two technologies markedly narrowed the possibilities of cybercriminals. Multifactor authentication technologies have already demonstrated their potential to protect data records, and the standard practice of encryption ensures that in the event of theft or loss of data, attackers cannot use them.
Cybersecurity threats will continue to be a significant problem. But as those who were born after the Internet came to the masses in 1995, we will be able to cope with these threats and openly confront them. In any case, this will definitely have nothing to do with the practice of 2006, when after the theft of 26.5 million data records in the US Department of Defense, the responsible department waited three weeks before generally reporting anything to those whose data were stolen.
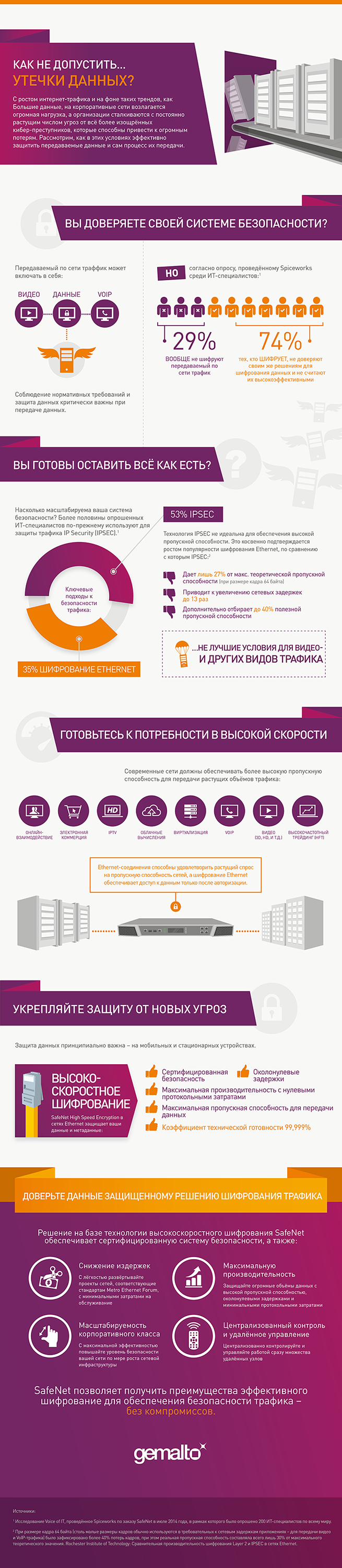
How IT-specialists assess the state of security in their companies and how they see security challenges in the coming years - in our infographics:

Before the advent of the iPhone, there was still a whole year left, the first 3G networks were just beginning to appear in the world, and there were no mobile applications in their current form. Services for streaming music, publishing photos, social networks - all this was still in its infancy. In 2006, cybersecurity threats were markedly different from modern ones, since the resources available to hackers were very limited.
Today, almost all aspects of our life are somehow connected with the cloud; Almost everything is stored in the cloud - starting with our bank accounts and out-patient cards and ending with even more personal data; while today we are generating significantly more data than ever.
')
The evolution of threats
The nature of the threats evolved following this explosive growth of useful data. In the early 2000s, in most cases, threats and malicious code presented only minor troubles and were created with the aim of annoying or preventing users from working.
Then, in 2008, the Zeus Trojan Trojan virus appeared, which intercepted bank card details by tracing user-pressed keys and copying the form data sent. Years later, about a hundred people were arrested for stealing a total of over $ 70 million by using this Trojan program.
This is where the formation of a much more professional approach to cybercrime began. Viruses, Trojans and worms began to be created to steal money and critical corporate information. Varieties of the Trojan virus Zeus are rampant to this day, infecting numerous computers. In fact, they played an important role in one of the largest cyber attacks today - the attack against Target in 2013.
Here it is important to remember that as soon as a device connects to the Internet, it immediately becomes vulnerable. And as far as giving new things to the network opportunities, everyone who is involved in this should be aware of the risks involved. Take, for example, connected cars. The presence of Wi-Fi access and on-board entertainment systems that support streaming video, of course, add to the attractiveness of selling cars, but as shown by last year’s events, poorly designed security measures allow intruders to enter.
Shifts in consumer perception
Every day we see more and more news about large and large-scale data breaches, and in this regard, it is rather curious to see how this changes the attitude of consumers to these leaks. Since 2013, nearly four billion data records have been compromised as a result of leaks in the world, and this news no longer shocks people. At such a scale, almost everything - starting with companies and their employees and ending with ordinary consumers - got used to the idea that leaks are inevitable, and the main question now is when it will break. But in general, the situation is not at all as hopeless as it seems. In the course of our recent study of the Connected Living 2025, we asked the 2000th generation about their opinion on data security issues. Two thirds of them said that they are wary of various threats, and there are much more such respondents than those who are relaxed and do not see particular dangers, or, conversely, are overly suspicious. Thus, the results of the survey indicate that today people are aware of the importance of protecting their data.
Leakage prevention technologies have lost their relevance (as well as the perimeter security concept)
If the past ten years have taught us something, it is that the perimeter protection technologies are not able to provide an adequate level of security. No matter how high or strong the wall you build, the enemy will always find a way to bypass it - go on the other side or crawl from the bottom.
Despite the increase in data leakage, companies continue to use firewalls, threat tracking tools and other leak prevention tools as a basis for their security strategies. However, most IT professionals readily admit that in the event of a security perimeter breach, their corporate data and customer information will be at risk.
This does not mean that the perimeter of security no longer matters. This only suggests that perimeter protection should not be the only tool in the arsenal of companies to protect against all sorts of threats. Instead, IT professionals need to accept the fact that leaks are unavoidable, and work to make these leaks safe — by using security measures that are closer to the data and to users, including through encryption technologies and multi-factor authentication.
Encryption and multifactor authentication as the most effective methods of protection
The development of the following two technologies markedly narrowed the possibilities of cybercriminals. Multifactor authentication technologies have already demonstrated their potential to protect data records, and the standard practice of encryption ensures that in the event of theft or loss of data, attackers cannot use them.
Cybersecurity threats will continue to be a significant problem. But as those who were born after the Internet came to the masses in 1995, we will be able to cope with these threats and openly confront them. In any case, this will definitely have nothing to do with the practice of 2006, when after the theft of 26.5 million data records in the US Department of Defense, the responsible department waited three weeks before generally reporting anything to those whose data were stolen.
Expert survey
How IT-specialists assess the state of security in their companies and how they see security challenges in the coming years - in our infographics:

Source: https://habr.com/ru/post/307532/
All Articles