PosCardStealer: new malware and large-scale attacks threaten PoS systems

A few weeks ago, we (PandaLabs Anti-Virus Lab) reported on an attack where hundreds of restaurants in the United States suffered, in which a malicious program called PunkeyPOS was used. We did not report how PunkeyPOS was discovered: in fact, we are investigating a whole series of PoS attacks, which also affect hundreds of bars, restaurants and shops in the United States. While we were analyzing one of these attacked systems, it was attacked by another cyber gang using PunkeyPOS. In this article we are going to discuss another attack, which we are still exploring. In this case, a PoS malware called PosCardStealer was used.
PosCardStealer: New PoS Attack
The first attack, which we were able to analyze, was September 30, 2015, and it affected 30 PoS systems. The malware was installed using PowerShell, a popular Windows utility. It was used to execute the file (MD5: 0B4F921CF2537FCED9CAACA179F6DFF4), which had a creation date two days earlier (09/28/2015 17:07:59) and was compiled using C ++.
')
The job of the installer is to infect the system with a malware program that is specifically designed for PoS systems. For this, he uses various techniques in the functions of the PoS software installed in the system. In particular, it searches for brain.exe (related to Dinerware ) and scpwin.exe processes, and installs malware as follows, depending on which process it finds:
• brain.exe : in this case, the actual process of the Dinerware program for loading PosCardStealer is performed. To do this, it modifies a pair of Windows registry keys.
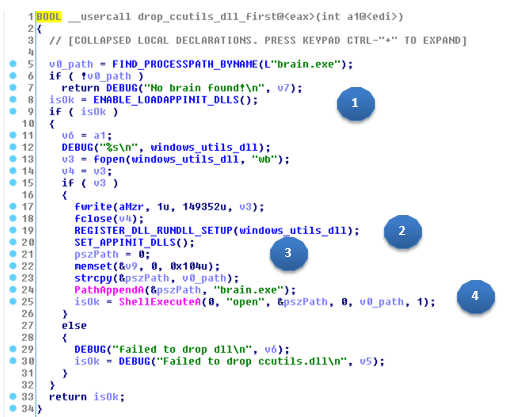
The installer performs the following actions:
1. Enables automatic loading of the DLL, causing ENABLE_LOADAPPINIT_DLLS (0x004017A0), and modifies the following registry key:
SOFTWARE \ Microsoft \ Windows NT \ CurrentVersion \ Windows LoadAppInit_DLLs = 1
2. If the previous key was successfully changed, then it will install PosCardStealer to:
C: \ Windows \ utils.dll
3. After that, it calls SET_APPINIT_DLLS (0x00401850) to add a new DLL path to the registry so that it loads automatically:
SOFTWARE \ Microsoft \ Windows NT \ CurrentVersion \ Windows AppInit_DLLs = C: \ Windows \ utils.dll
4. Finally, he launches the PoS software (“brain.exe”) again, which loads the newly installed DLL.
• scpwin.exe : in this situation it will use a technique known as “DLL hijacking”. After finding scpwin.exe in the attacked system, it will copy “Cdrvhf32.dll” (legitimate DLL) from the Windows system folder to the folder where the same application can be found. It will then modify the copied DLL so that PosCardStealer (utils.dll) can be loaded from there.
In the following screenshot, we can see the pseudocode that is responsible for performing this action:
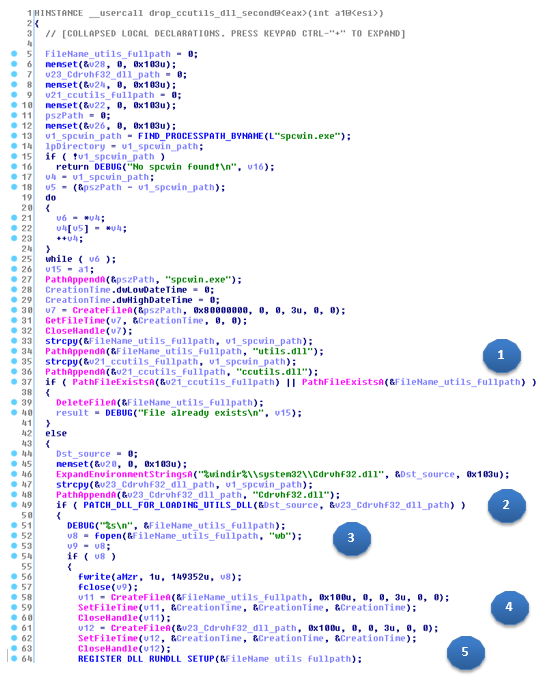
Now the procedure performs the following actions:
1. Verifies that the “utils.dll” or “ccutils.dll” files exist in the folder with the PoS software
2. If these DLLs are not found, then it changes the “% windir% \ system32 \ Cdrvhf32.dll” and copies the “spcwin.exe” folder.
3. If it successfully changed the “Cdrvhf32.dll” library, it will also copy the code of the “utils.dll” malicious library into the “spcwin.exe” folder. The modified library “Cdrvhf32.dll” has the same functions as the original one, but besides this it is also able to execute “additional” code: loading the malicious library “utils.dll”
4. After that, the date of creation / access / modification of the libraries “cdrvhf32.dll” and “utils.dll” will be changed to correspond to the date “spcwin.exe”
5. Finally, it will perform an “export” _Setup @ 16 from the “utils.dll” library from the REGISTER_DLL_RUNDLL_SETUP procedure.
This version of PosCardStealer (MD5: 81060E53D233711507F60C446418AFC6) is compiled in Visual C ++ and has the following internal date: 09/27/2015 12:26:09. All this (plus some other evidence that is available in the PandaLabs anti-virus laboratory) indicates that the analyzed malicious samples were created specifically to attack the victim’s data.
A common feature on all attacked hardware: LogMeIn software was installed everywhere. This software is very popular and can be used for remote access to systems. In the case of PoS systems, it could be used by the same company that provides PoS systems for restaurants to perform tasks of updating, support, etc.
LogMeIn: Remote Attacks
Although the use of LogMeIn could be episodic, in this case, we found out what it could be related to: about a month and a half after this attack, a new attack was carried out using LogMeIn. In this case, not only 30 previously compromised PoS systems were affected, but also hundreds of others. All of them were located in the USA and mostly belonged to bars and restaurants.
In this new attack, criminals used the Multigrain malware, which we analyzed here . The attack began on November 13, 2015 at 22:09 (GMT), and it took the criminals only 10 minutes to infect all the victims. Here is the process that was used to perform the infection:
• Connect to PoS using LogMeIn
• Use LogMeIn to download the executable file (wme.exe, MD5: A0973ADAF99975C1EB12CC1E333D302F, Multigrain option).
• Script execution via LogMeIn. This script calls cmd.exe that performs wme.exe.
14 hours later, an isolated attack on one of the PoS was launched. This attack installed a new version of Multigrain (MD5: A3B944454729EA13AD847D01FFAC556A). Half an hour later (we assume that this time was required to verify that everything is working correctly), the criminals automatically repeated the attack against all their victims, so that all the machines were infected with a new version of the malicious program after only 10 minutes.
These systems have been in a compromised state for months. When the people responsible for the PoS systems realized that they were attacked and cleaned the PoS systems, the hackers could “return” again to where they were thrown from, and with the help of LogMeIn installed a new version of Multigrain (MD5: 4C722EA25EC857E1A7E73DE5886F9299).
It should be clarified that the attack using LogMeIn was not carried out as a result of some kind of vulnerability, but due to the fact that hackers already had hacked computers and they had all the necessary registration data to access the system. We advise LogMeIn users to follow the guidelines published in this document .
Some tips to prevent cyber attacks
This type of attack allows you to steal information from thousands of bank cards in a fairly simple way. PoS systems are critical systems, and they must be protected in case they need to install software for remote access. All available security measures (two-factor authentication, restriction on IP addresses of connected devices, etc.) should be applied. This should be mandatory in order to have full control over all programs that run on these terminals.
Consider that your strength lies in knowing your infrastructure and environment. The best way to ensure complete security in your entire IT park is to use Adaptive Defense . Activate the “Lock” mode to prevent the execution of unknown processes ... This will ensure the protection and security of all information belonging to you and your customers.
Source: https://habr.com/ru/post/307520/
All Articles