IXIA ThreatARMOR: fewer attacks, fewer SIEM alarms, better ROI
We came across a new solution from IXIA - Threat Armor. And we managed to test it and figure out what kind of a “miracle” that appeared at the beginning of this year and has already managed to get a large number of gold awards at various exhibitions in different parts of the world.

First, a little theory. If we talk about the direction of security, then IXIA has long been one of the leaders in this field with its Breaking Point product, which successfully tests the security solutions of any manufacturers. The Breaking Point "invested" knowledge of the ATI team (Application and Threat Intelligence), which for more than ten years has "parsed" attacks and popular applications. Read more about Breaking Point here .
This ATI team monitors the global web for new threats, works in a consortium with security solutions manufacturers, respectively, it allows you to accumulate information about current IS threats and their sources. This knowledge was invested in Threat Armor. The main objective of Threat Armor is to reduce the attack surface by blocking unwanted traffic, and accordingly reduce the load on security devices (FW, WAF, NGFW, IPS, etc.) and thereby reduce the number of SIEM alerts. Threat Armor also analyzes outgoing traffic — for example, whether there are already infected clients or parts of a botnet on the network.
')

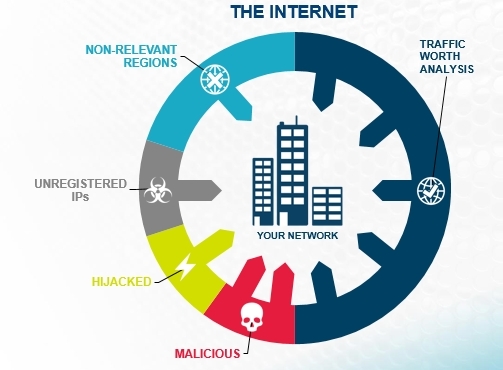
Little of. Threat Armor not only provides information and blocks information security threats, but also provides detailed Rap Sheet for each blocked IP. The relevance of this data is provided by an update from the cloud service of the ATI Research Center, a cloud service that transmits updates every 5 minutes through the management port.
Threat Armor is a hardware access-list that transparently allows traffic at the line speed. Available in two versions - 1 Gbit / s and 10 Gbit / s. In our hands got the first option.
Fault tolerance is provided by redundant power (2 AC power supplies) and internal bypass, which continue to pass traffic even when power is lost on the device.
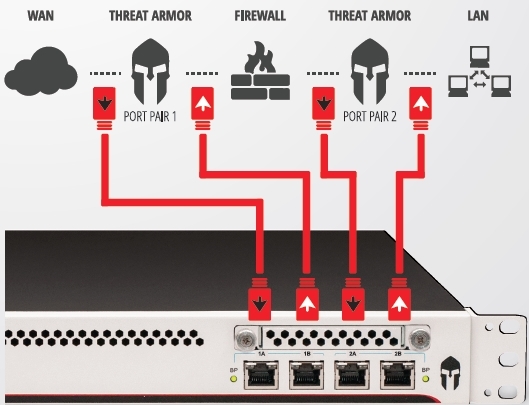
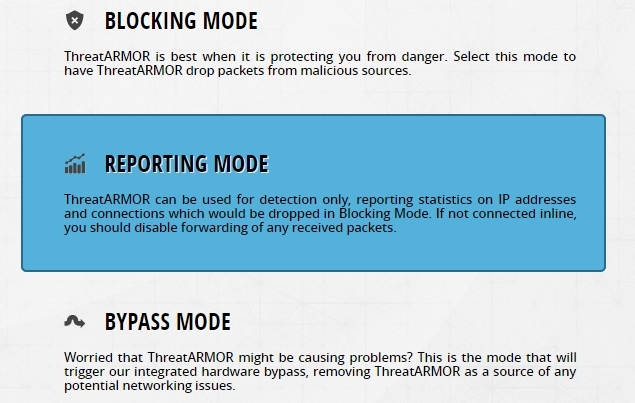
Threat Armor can be enabled in two ways:
- more effective - in-line;
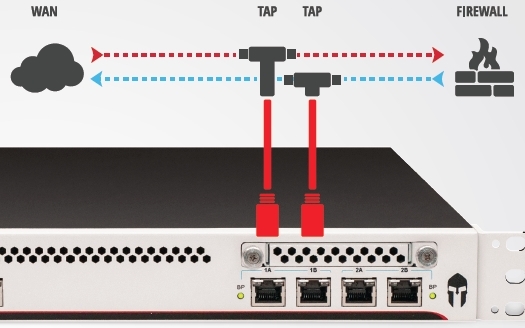
- passive mode - monitoring;
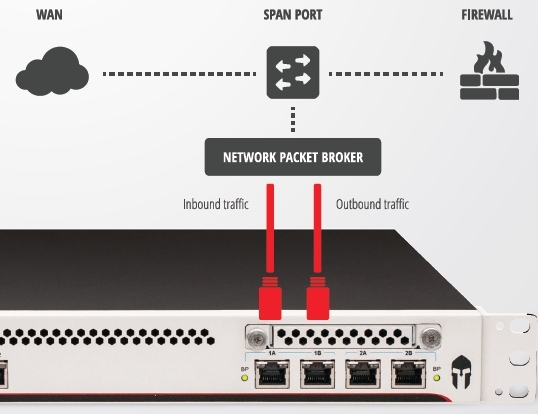
In our case, Threat Armor was turned on in the passive mode, a SPAN port between the local network and a firewall for analyzing incoming traffic.
Power was turned on, IP was configured for management and updates, REPORTING MODE was selected, and the device started working.
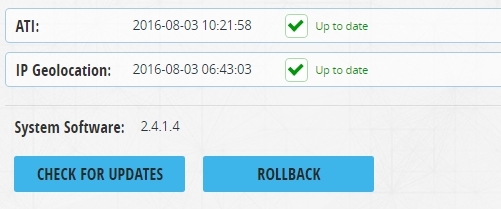
Also an important point is to check whether the updates are catching up.
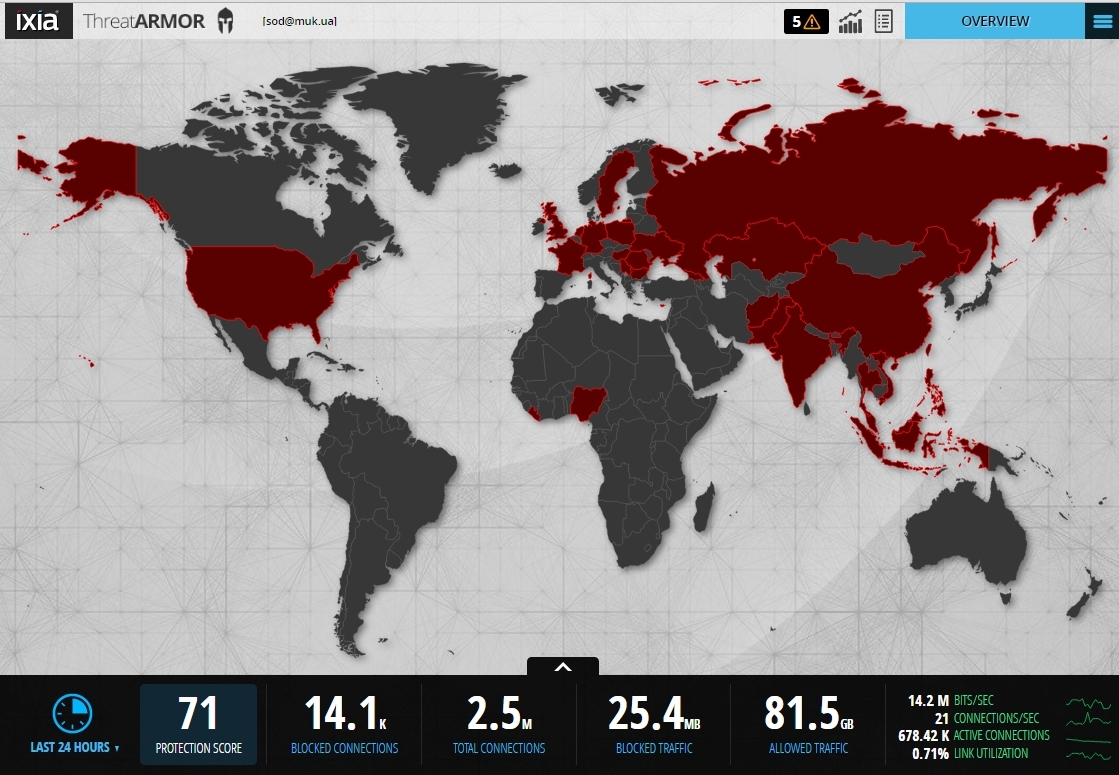
View statistics and reports. Interface of an interactive map of identified threats and general statistics.
Here you can see the statistics for each country, for example, in Ukraine.
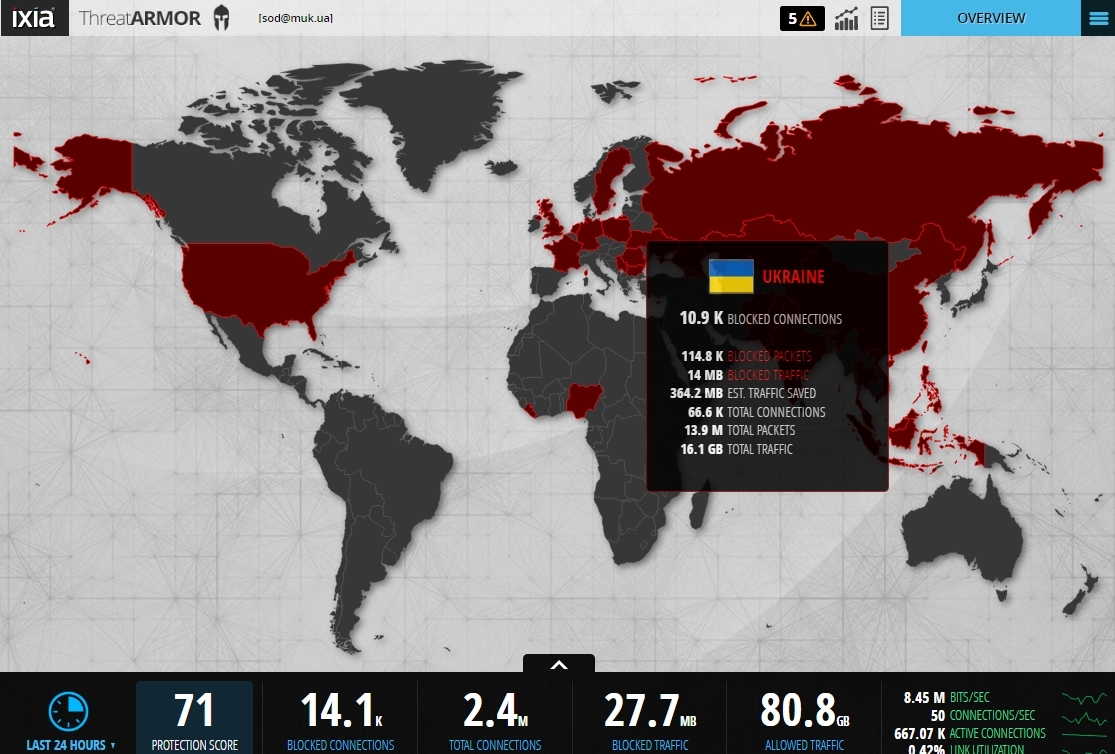
And Dashboard is an interface with a detailed map of identified threats by countries, detailed statistics and countries with which there is almost no traffic. Such countries can be blocked to protect themselves from possible attacks, for example, from DDoS. It is also clear that traffic with IS threats is not such a large amount of the total mass, but the protection ratio (Protection Score), taking into account the independent artificial training of the device, is rather high - 71, which indicates the effectiveness of Threat Armor.
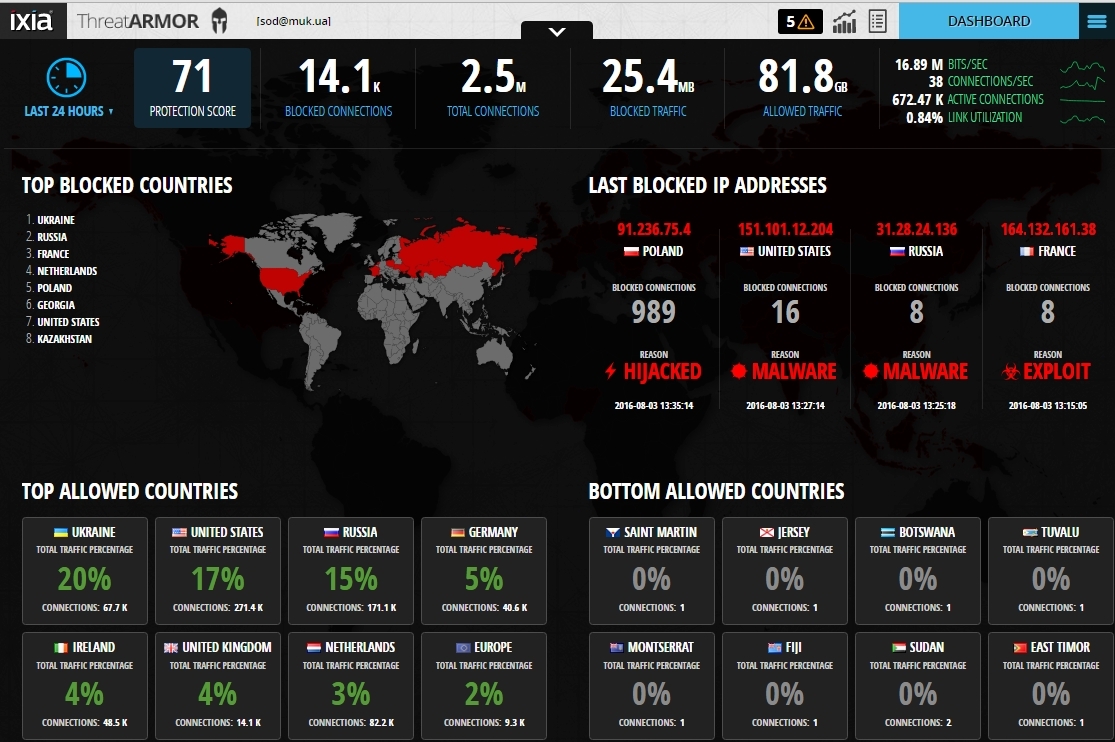
You can block countries directly from the Dashboard,

or from the settings menu, where you can also manually add Black-list and White-list IP addresses.
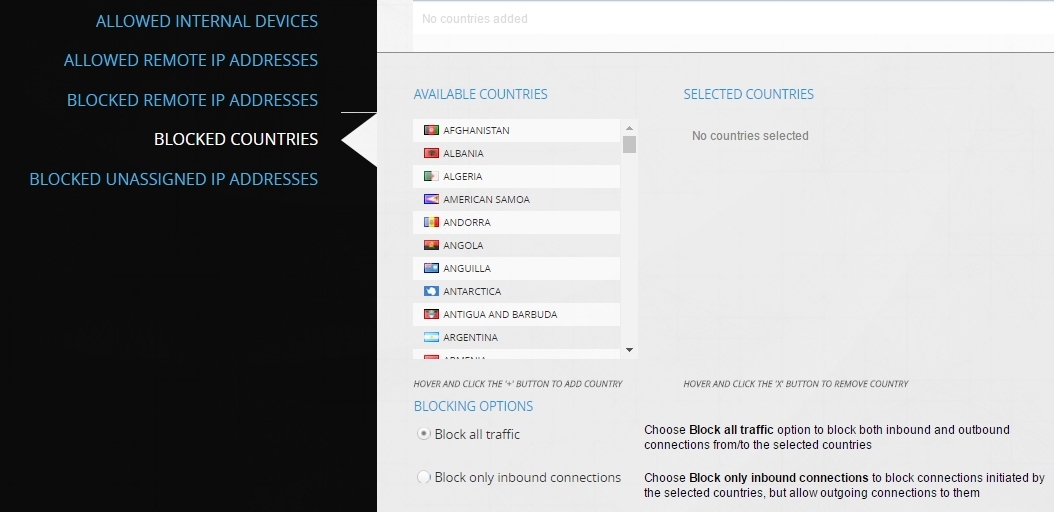
If you select any of the countries, then from the Dashboard you can go to more detailed information on the IP of attackers, sites with malicious code, phishing sites, etc.
On the left side are all addresses - sources of information security threats, on the right - a detailed Rap Sheet.
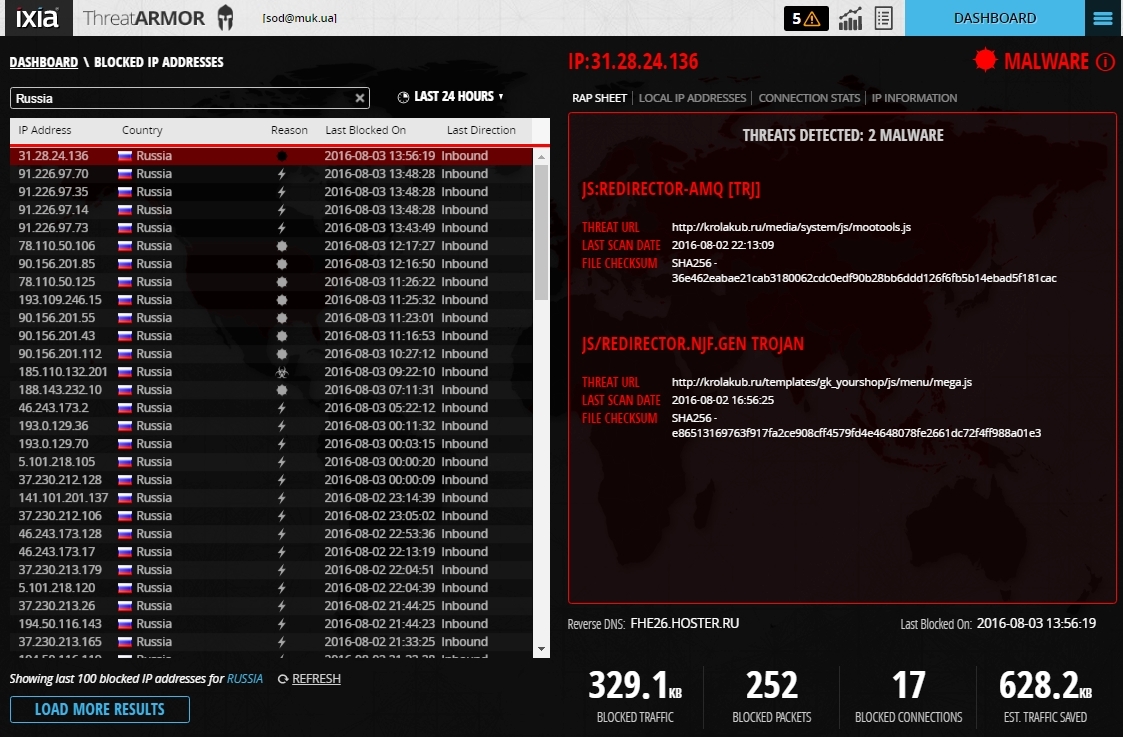
In it you can see detailed information about the threats.

And also what local addresses these attacks were directed to.
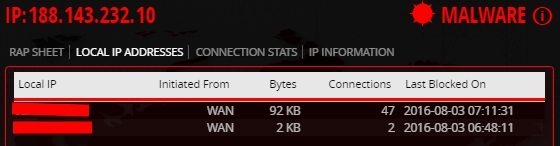
Compound statistics.
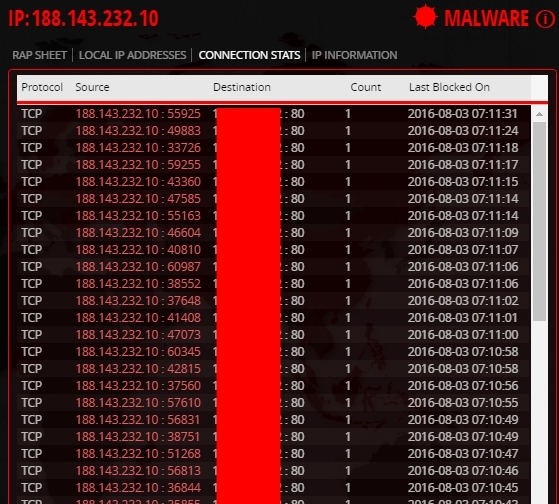
And information about this malicious IP.
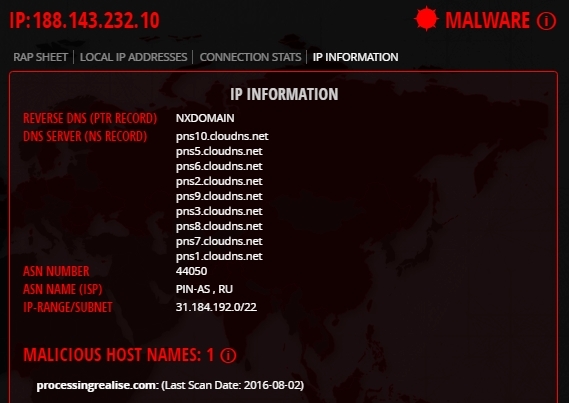
If you look at the attack options, you can see the following.
Web Application Exploit.

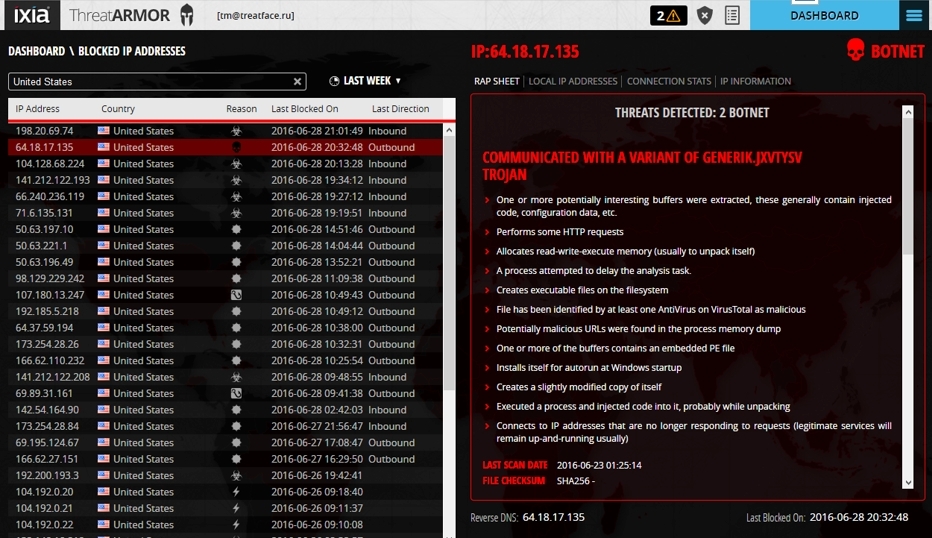
Botnet with a variety of threats / actions.
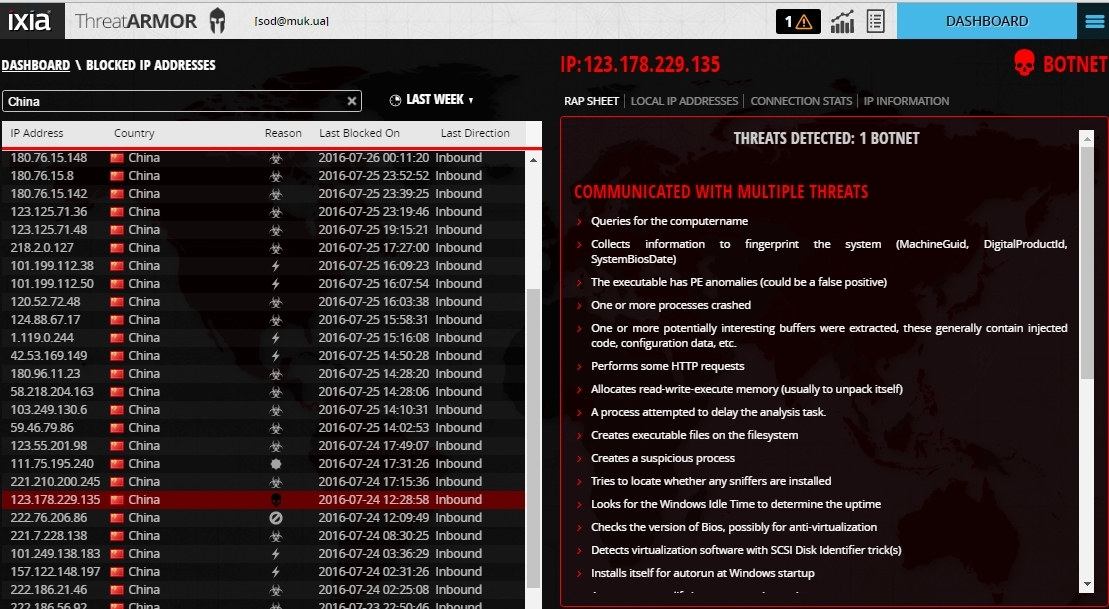
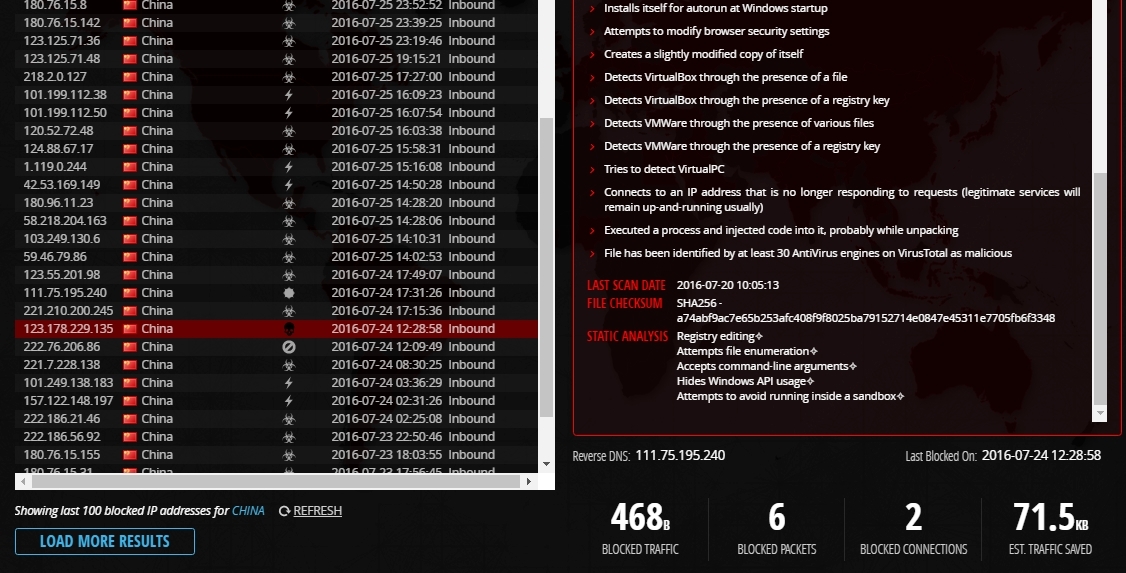
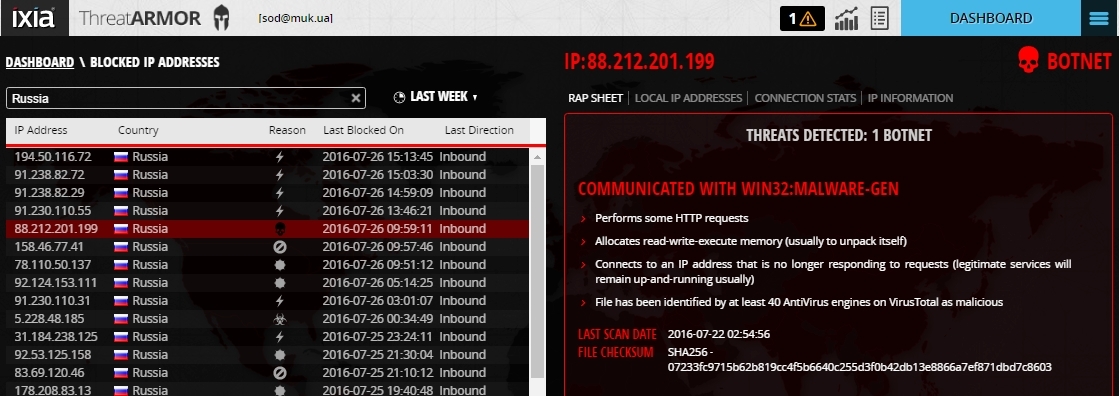
Botnet with an attempt to get infected with a virus.
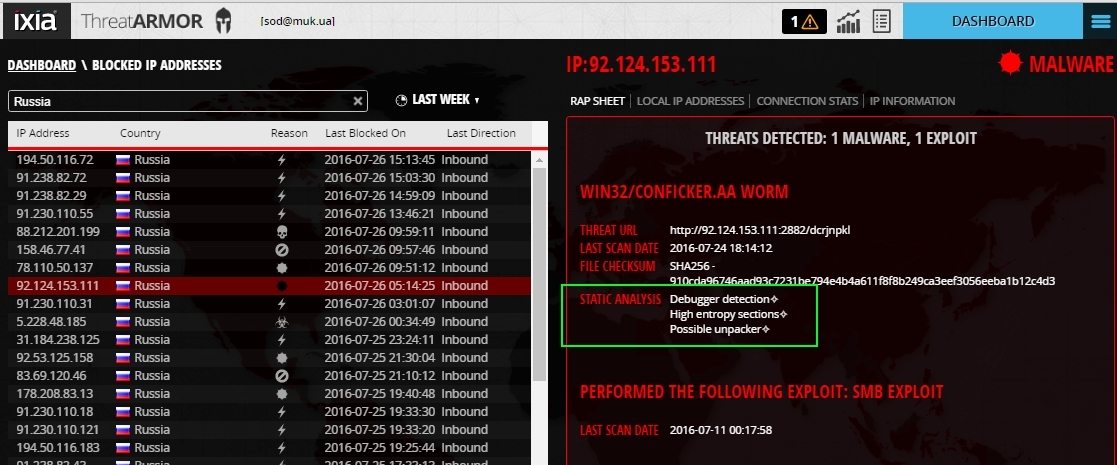
Worm with its description.
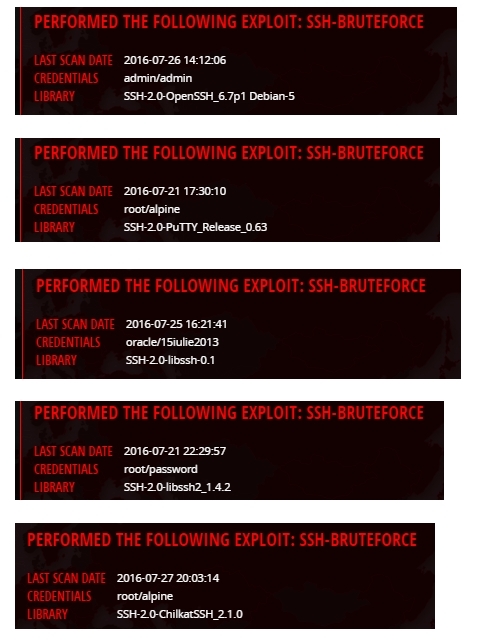
An active brute force attack with a description of the Credentials and the software used.
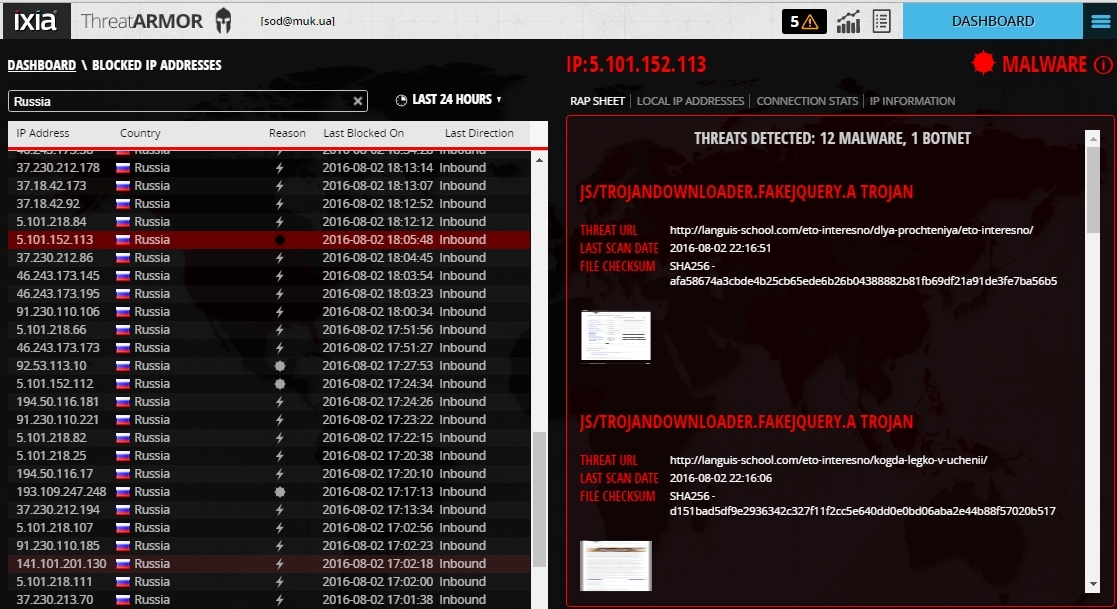
Combined attack with a large number of attacking elements for implementation.
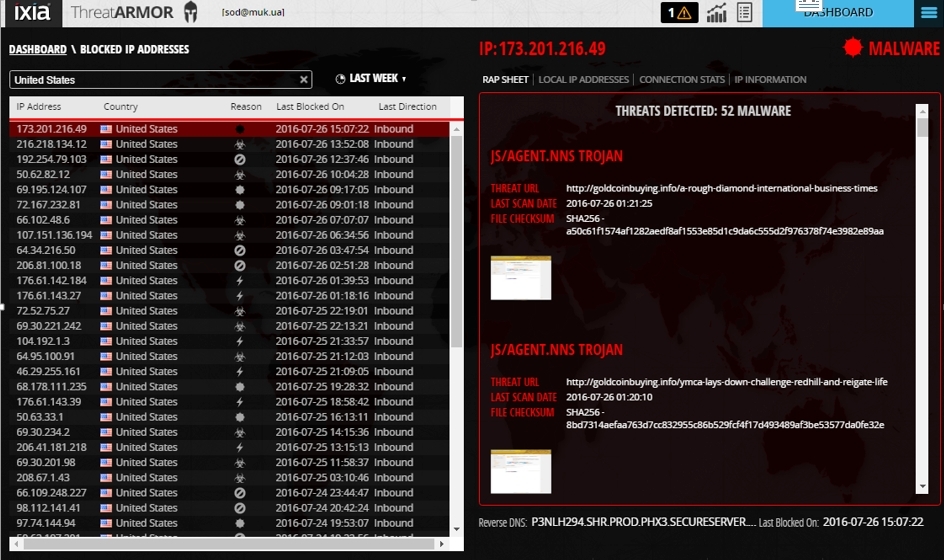
Active attack - botnet through a Trojan program.
Hijacked IP with an explanation - “This particular network range has been hacked. A stolen network range is a network block returned from unused network blocks, often by spammers. The original owner of the unit may have left it blocked for any of the reasons. For more information about these types of IP network ranges, please visit .... "

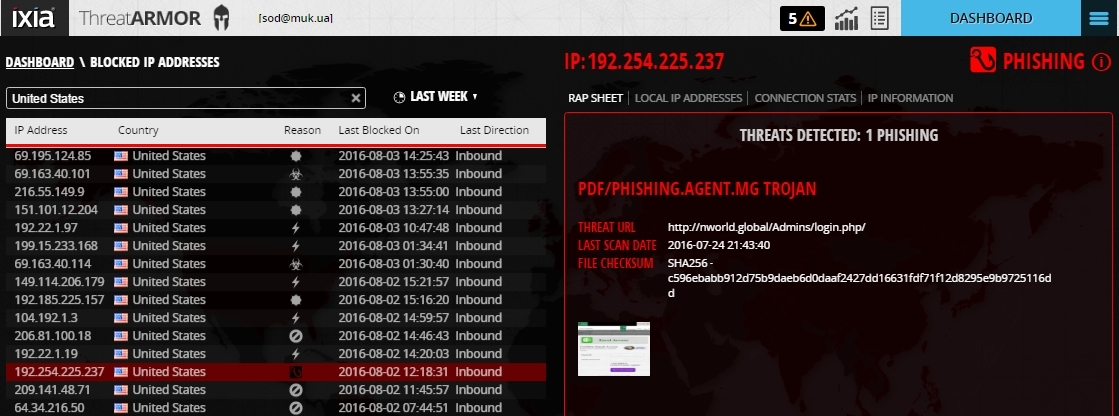
Phishing.
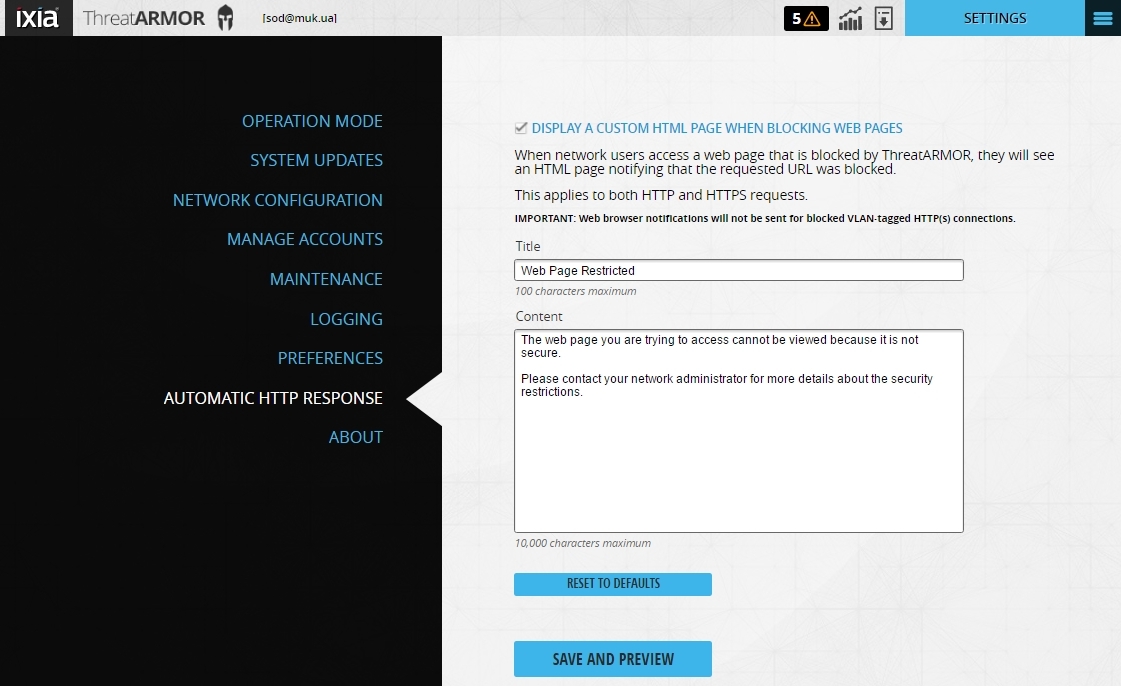
It is possible to configure the access blocking screen for a user who has accessed a resource in the browser that is included in the IXIA ThreatARMOR device’s “forbidden list” of IP addresses, which is generated every 5 minutes from a number of global databases of banned IP addresses owned by hacked resources, spam, etc.).
RESTful API capability
with a detailed description of each request and response.
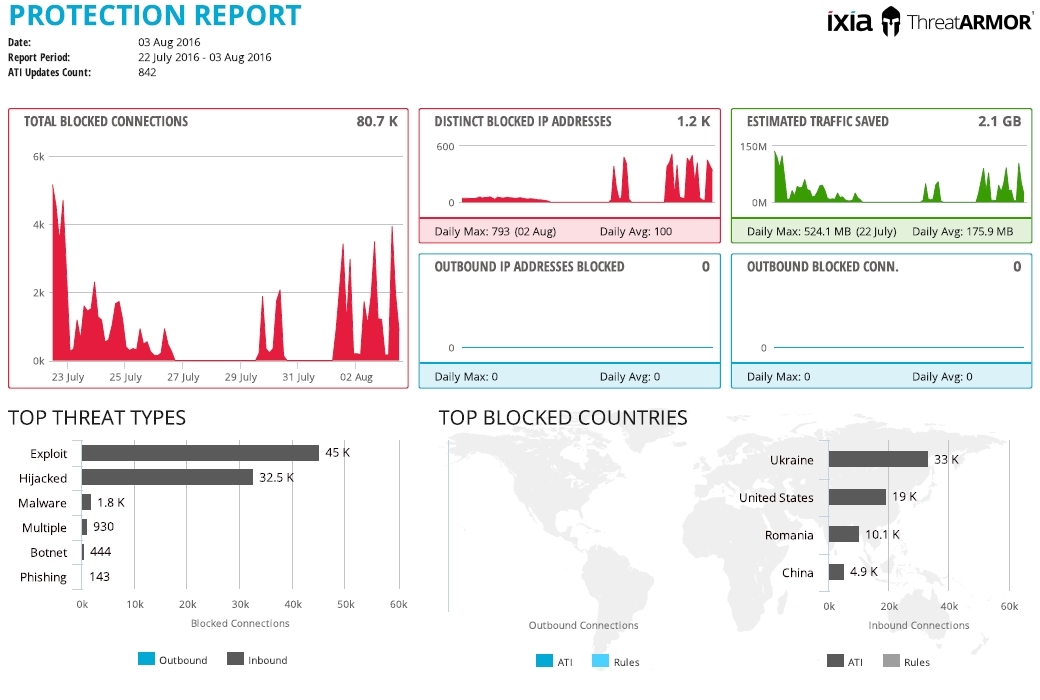
It is possible to generate a weekly report.
As a result, we have an additional level of information security, as well as a number of advantages:
cost reduction - reducing the load on firewalls and IPS, which makes it unnecessary to update perimeter security levels;
saving time - there is no need to update access lists when new “bad” IPs appear;
reduced alert SIEM - saving time and money;
reducing attacks on the network - blocking known attacks and blocking countries with which there are no communications.

First, a little theory. If we talk about the direction of security, then IXIA has long been one of the leaders in this field with its Breaking Point product, which successfully tests the security solutions of any manufacturers. The Breaking Point "invested" knowledge of the ATI team (Application and Threat Intelligence), which for more than ten years has "parsed" attacks and popular applications. Read more about Breaking Point here .
This ATI team monitors the global web for new threats, works in a consortium with security solutions manufacturers, respectively, it allows you to accumulate information about current IS threats and their sources. This knowledge was invested in Threat Armor. The main objective of Threat Armor is to reduce the attack surface by blocking unwanted traffic, and accordingly reduce the load on security devices (FW, WAF, NGFW, IPS, etc.) and thereby reduce the number of SIEM alerts. Threat Armor also analyzes outgoing traffic — for example, whether there are already infected clients or parts of a botnet on the network.
')


Little of. Threat Armor not only provides information and blocks information security threats, but also provides detailed Rap Sheet for each blocked IP. The relevance of this data is provided by an update from the cloud service of the ATI Research Center, a cloud service that transmits updates every 5 minutes through the management port.
Threat Armor is a hardware access-list that transparently allows traffic at the line speed. Available in two versions - 1 Gbit / s and 10 Gbit / s. In our hands got the first option.
Fault tolerance is provided by redundant power (2 AC power supplies) and internal bypass, which continue to pass traffic even when power is lost on the device.
Threat Armor can be enabled in two ways:
- more effective - in-line;

- passive mode - monitoring;


In our case, Threat Armor was turned on in the passive mode, a SPAN port between the local network and a firewall for analyzing incoming traffic.
Power was turned on, IP was configured for management and updates, REPORTING MODE was selected, and the device started working.

Also an important point is to check whether the updates are catching up.

View statistics and reports. Interface of an interactive map of identified threats and general statistics.

Here you can see the statistics for each country, for example, in Ukraine.

And Dashboard is an interface with a detailed map of identified threats by countries, detailed statistics and countries with which there is almost no traffic. Such countries can be blocked to protect themselves from possible attacks, for example, from DDoS. It is also clear that traffic with IS threats is not such a large amount of the total mass, but the protection ratio (Protection Score), taking into account the independent artificial training of the device, is rather high - 71, which indicates the effectiveness of Threat Armor.

You can block countries directly from the Dashboard,

or from the settings menu, where you can also manually add Black-list and White-list IP addresses.

If you select any of the countries, then from the Dashboard you can go to more detailed information on the IP of attackers, sites with malicious code, phishing sites, etc.
On the left side are all addresses - sources of information security threats, on the right - a detailed Rap Sheet.

In it you can see detailed information about the threats.

And also what local addresses these attacks were directed to.

Compound statistics.

And information about this malicious IP.

If you look at the attack options, you can see the following.
Web Application Exploit.

Botnet with a variety of threats / actions.


Botnet with an attempt to get infected with a virus.

Worm with its description.

An active brute force attack with a description of the Credentials and the software used.

Combined attack with a large number of attacking elements for implementation.


Active attack - botnet through a Trojan program.

Hijacked IP with an explanation - “This particular network range has been hacked. A stolen network range is a network block returned from unused network blocks, often by spammers. The original owner of the unit may have left it blocked for any of the reasons. For more information about these types of IP network ranges, please visit .... "

Phishing.

It is possible to configure the access blocking screen for a user who has accessed a resource in the browser that is included in the IXIA ThreatARMOR device’s “forbidden list” of IP addresses, which is generated every 5 minutes from a number of global databases of banned IP addresses owned by hacked resources, spam, etc.).

RESTful API capability


with a detailed description of each request and response.

It is possible to generate a weekly report.

As a result, we have an additional level of information security, as well as a number of advantages:
cost reduction - reducing the load on firewalls and IPS, which makes it unnecessary to update perimeter security levels;
saving time - there is no need to update access lists when new “bad” IPs appear;
reduced alert SIEM - saving time and money;
reducing attacks on the network - blocking known attacks and blocking countries with which there are no communications.
Source: https://habr.com/ru/post/307456/
All Articles