On the hunt for "insects": the program bug bounty in Odnoklassniki
As you know, bug bounty is a reward program for information about security issues in a product. With the help of rewards, the developer encourages him to report vulnerabilities to him, rather than selling information on the black market, and gains time to correct the problem before it becomes known to a wide audience. After all, the more massive and popular product you have, the more there will be those who want to use it for personal gain. For social networks, the presence of gaps in the security system is extremely undesirable, because it undermines the trust of users. And if you want your creation to live long and have a large audience, you need to pay a lot of attention to finding errors and timely correction.
Therefore, a year ago Odnoklassniki also launched such a program. My name is Alexander Svatikova, and as an information security specialist, I’ll tell you about what we’ve encountered and what we managed to achieve during the vulnerability scan program.
Program history
Anyone can participate in our program. The main task is to find and neutralize errors in the field of security and privacy in Odnoklassniki. You can send us your bug reports, and we will definitely study them, fix them and pay rewards. The award is given for reporting an unknown security issue to us at Odnoklassniki. The ideal report is written briefly, in the case, contains a script or a proof of concept and is not copy-paste from vulnerability scanners. Read more about the rules on our page in HackerOne .
A few years ago, we already launched a similar program - users sent their finds by e-mail. The campaign was quite successful, but we faced organizational difficulties, including the delivery of rewards to participants.
Since then, the American startup HackerOne has appeared. This is a platform, a kind of social network, for security professionals with a built-in task tracker and payment platform. This project is designed to bring together software authors and error hunters and takes over the entire organizational part of the process.
The popularity of the platform, you can judge by the list of companies working with HackerOne. As a result, we also decided to move our vulnerability scanner there.
Criminals are not asleep
So, we voluntarily invited a crowd of hackers to look for vulnerabilities in Odnoklassniki. For us, in general, the situation has almost not changed: not only baghunters are constantly attacking us. We constantly struggle with malicious activity, with those who cause damage to our users. But the current situation cannot be called characteristic only for Odnoklassniki, this is how all popular resources live. Hacking accounts, identity theft and spamming is a profitable business. So we can not say that before the launch of Bug Bounty we lived in peace.
Vulnerability Scanning Features
It must be said that technically searching for vulnerabilities for research and criminal purposes is no different. After we settled on HackerOne, the number of specific calls to our resources dramatically increased, indicating the work of automated security testing tools.

Someone launched Acunetix
On the frontends, a surge in the number of errors is periodically recorded, corresponding to fuzzing with millions of stupid queries, but we have not received a single noteworthy auto-generation report from scanners.
We do not provide special conditions for vulnerability seekers. They torture happiness in the usual way; for our security systems, their investigations are no different from attackers of intruders.
The monitoring system also underwent “testing” in the framework of a public search for vulnerabilities and was adequately tested: all successful attacks that somehow affected the infrastructure, such as DOS and SSRF, were identified even before we were sent a corresponding report.
First results
Today, almost a year after the launch of the program, we receive about ten reports a week. And in the first two weeks, we received about 700 (purple graph).
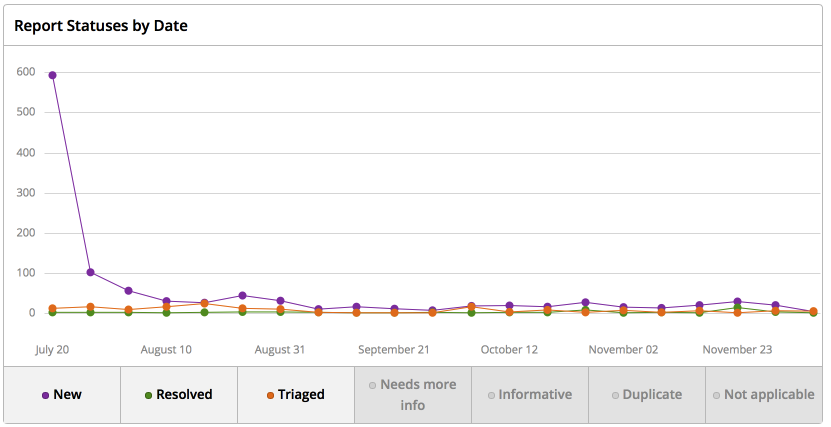
- New - these are new reports sent;
- Triaged - checked by us and queued for correction;
- Resolved - fixed bugs.
By launching the program, we were ready for a splash. We had not only our experience with the bug bounty, but also the experience of Mail.Ru Group, which launched the search for vulnerabilities in 2014. But the response exceeded our expectations and in the first month we barely coped by processing and responding to reports.
It is expected that most of the reports in the first weeks were standard texts about the false positives of popular scanners and did not represent any value or vulnerability.
However, we also received useful data. For the first month of the program, we got tickets for about 50 bugs of varying degrees of criticality.
There was also a funny case: on the eve of the launch of the program, the stored XSS bypassed a two-stage code review process, manual testing and automatic scanning and entered production. We received 11 reports on this bug in a day and a half, a kind of benchmark for a new program.
We also received some interesting reports on vulnerabilities in old unused versions of code, attack scripts on us through bugs in exotic browsers, and even reports on unpublished problems (0day) in the libraries we use.
Labor weekdays for vulnerability hunters
After the first shaft of reports subsided, their number per month became more stable, fluctuating in small limits. A few weeks later, there were far fewer reports of false positives from automated scanners, fewer duplicates. First of all, this is the result of our efforts to correct the detected bugs. But also in Hackerone they are working to discipline hackers, to encourage them to send better reports. We are glad to see the community of bug hunters who explore Odnoklassniki on a regular basis and send us the highest quality and informative reports.
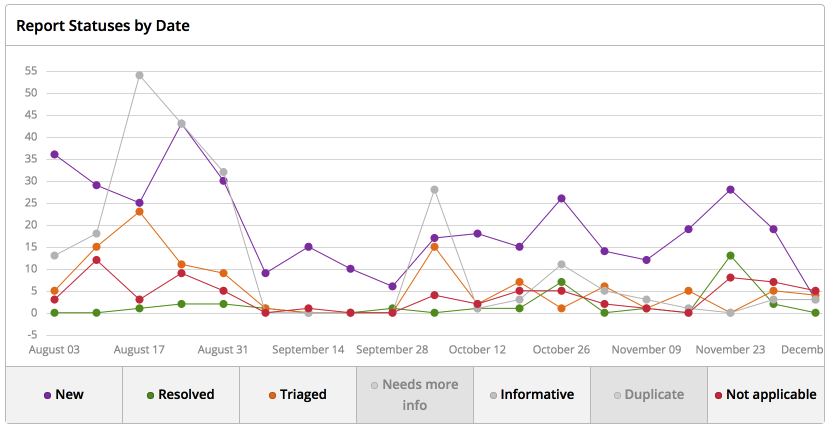
A new bug (New) goes through the verification process: erroneous reports and duplicates are eliminated, the problem is reproduced and analyzed. We estimate the likelihood of operation and possible damage, sometimes we specify additional details for the sender. If the problem is confirmed, the application goes to the status of Triaged and transferred to the developers. The ratio of good and bad reports, as well as the time required for making decisions and corrections, can be estimated on the chart above.
Interesting Entomology
What kind of "insects" found the participants? In addition to the standard set of OWASP Top 10, we received very interesting reports. I will list the most remembered:
- A way to buy Odnoklassniki domestic currency is cheaper than the official rate, made possible due to rounding errors (4lemon)
- csrf tokens in headers by using open redirection (ragnar)
- bypass the same origin policy on the main domain using a vulnerable flash drive on a CDN domain (zoczus)
Results
For the year of work we received from the participants 1328 messages. In total, 143 hackers and 167 real vulnerabilities of different degrees of criticality. Could we have organized an audit of equal size and efficiency within the company? Obviously not. From this I boldly conclude that our venture was a success. If you have questions or want to share your experience - write in the comments!
')
Source: https://habr.com/ru/post/307438/
All Articles