ProjectSauron: cyber spyware hacking into encrypted communication channels of state organizations
ProjectSauron five years disguised as a password filter for Windows systems, while remaining unnoticed
Kaspersky Lab has detected a powerful specialized virus that has been running unnoticed in the networks of various state organizations since 2011. The actions of the virus were aimed at breaking into encrypted communication channels of compromised systems. Information security specialists have identified the presence of this malware in the networks of more than 30 organizations from different countries.
Malware is classified as an Advanced Persistent Threat (APT) cyber espionage software. Only the most complex and long-lasting cyber spyware attacks correspond to this classification. APT malware are also Equation , Regin , Duqu and Careto . ProjectSauron (codename Strider) has long gone unnoticed due to the fact that it was in the system as an executable library loaded into the memory of a domain controller on a network running Microsoft Windows.
The compromised system considered the library a password filter, with the result that ProjectSauron got access to encrypted data in the clear. The developer of this software, according to experts who discovered it, is an unknown cyber grouping, which is responsible for attacks on key state-owned enterprises in different countries (Russia, Iran, Rwanda). According to experts, countries and organizations that have suffered from the virus, much more, what is known is only the tip of the iceberg. The main targets of the attacks were government structures, research centers, centers of the armed forces, telecommunications companies, and financial organizations.
Main features of ProjectSauron:
')
- This is not a simple virus, but a modular platform that is designed for cyber espionage;
- The platform and its modules use advanced encryption algorithms, including RC6, RC5, RC4, AES, Salsa20;
- More than 50 plug-in modules have been developed for the platform, expanding the possibility of a central element;
- The creators of ProjectSauron use this software to steal encryption keys, configuration files and IP addresses of the main servers of the network that are related to the protection of information in an enterprise or organization;
- Criminals can steal data even from networks that are not connected to the Internet. This is done using special USB-carriers. The stolen data is located in a hidden area that is not available to the OS software;
- ProjectSauron has been running since at least 2011.
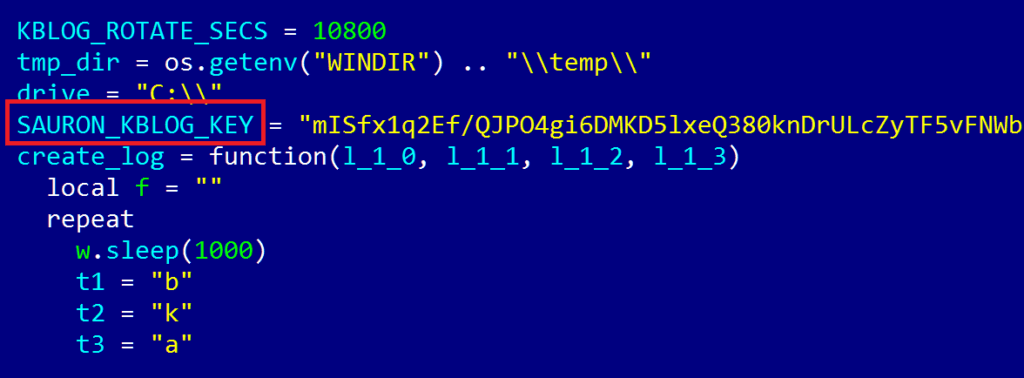
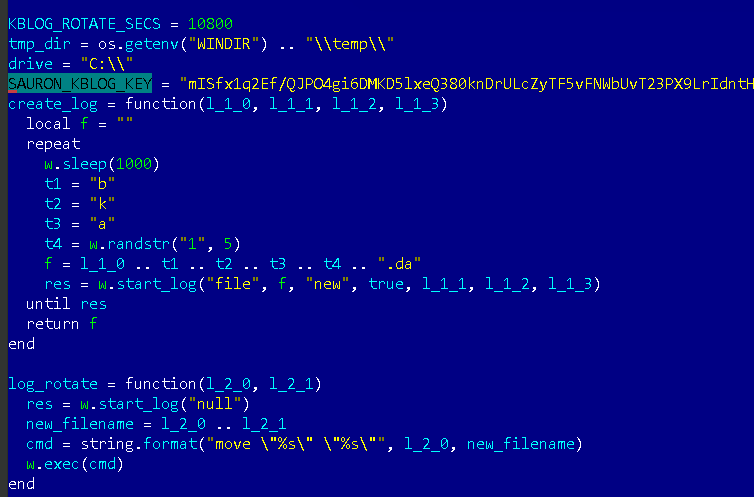
The virus is very difficult to detect. The fact is that the platform is modified for each new attack. Servers, domain names, IP addresses that attackers register for each instance of a modified platform are unique. Unique and plug-ins. They have unique names, file sizes and other characteristics. The timestamps of the modules correspond to the characteristics of the system in which the virus is supposed to work. The modules are designed for a variety of purposes, including theft of documents, keylogging, theft of encryption keys.
In the organization's network, ProjectSauron is also injected differently each time. In some cases, the attackers have changed the scripts that are used by the enterprise network administrators to update the legal software on the computers in the local network. The ProjectSauron bootloader is very small, when installed on a PC, it runs as administrator, connects to a unique IP address and loads the main piece of software. As mentioned above, an extensive network of domains and servers is used to operate the platform and its modules, with each element being used for a specific victim.
Now information security specialists have discovered 28 domains linked to 11 IP addresses in the USA and European countries. Malware has advanced networking communications based on the most common ICMP, UDP, TCP, DNS, SMTP and HTTP protocols. The platform uses the DNS protocol to send real-time data to the remote server in real-time mode.
In order for ProjectSauron to go unnoticed for a long time, its developers have done a lot. This, for example, the use of different command and control servers for different instances of software. Unique domains and IP addresses, the use of different cryptographic algorithms in different cases, working with conventional protocols and message formats. There are no signs of reuse of domains and servers. For each attacked target, a unique algorithm was used, which made it impossible to detect other copies of the software after detecting one of them according to a certain indicator. The only way to identify this software is structural similarity of the code.
First of all, intruders were interested in information that relates to non-standard cryptographic software. Such software is usually created for organizations that need to protect their communication channels, including voice communication, e-mail, document exchange. Known file formats that most interested in the creators of the virus. This is * .txt; *. Doc; *. Docx; *. Ppt; *. Pptx; *. Xls; *. Xlsx; *. Vsd; *. Wab; *. Pdf; *. Dst; *. Ppk; * .rsa; *. rar; *. one; *. rtf; ~ WPL * .tmp; *. FTS; *. rpt; *. conf; *. cfg; *. pk2; *. nct; *. key; * .psw. They are also interested in the following types of information:. * Account. * |. * Acct. * |. * Domain. * |. * Login. * |. * Member. * |. * User. * |. * Name |. * Email |. * _ id | id | uid | mn | mailaddress |. * nick. * | alias | codice | uin | sign-in | strCodUtente |. * pass. * |. * pw | pw. * | additional_info |. * secret . * |. * segreto. *
The virus can steal both documents and intercept keystrokes, search for and send encryption keys to its creators from compromised systems and drives connected to them. It is now known that ProjectSauron is capable of attacking all modern versions of Microsoft Windows. Other types of this software, designed to work in other OS environments, have not yet been discovered.
ProjectSauron, when it enters the system, deploys malicious modules inside the company's cryptographic software catalog and masks its own files among the existing ones. The downloaded virus remained in the system in sleep mode, waiting for the activation command. Subsequently, ProjectSauron was engaged in identifying encryption keys, configuration files and server addresses that encrypt messages between network nodes.
Experts from Kaspersky Lab assume that the cost of preparing cyber spyware of this level is many millions of US dollars. An operation of this level can only be implemented with the active support of a whole state. Most likely, various groups of specialists were involved in the creation of ProjectSauron.
Now, Kaspersky Lab software can detect signs of the presence of ProjectSauron in the system, with detection of samples of this malware as ProjectSauron as HEUR: Trojan.Multi.Remsec.gen.
A full report on the analysis of the virus and its work is available at this link (.pdf) .
Source: https://habr.com/ru/post/307430/
All Articles