Multigrain: Features of PoS Terminal Malware

Multigrain is a malware for PoS terminals that specializes in stealing information from bank cards using RAM-Scraping techniques (it directly accesses RAM from certain processes to obtain information about cards). This has become a very popular method, since international law prohibits storing this information on disk (even temporarily).
Another feature of Multigrain is that it uses DNS calls to communicate with the outside world (and thus it can send stolen information). In this article, we will analyze the malware itself, as well as how it performs its communications.
')
In April of this year, FireEye published an analysis of this malware, and it seems that this was the first time that they discovered the Multigrain variant. In this article, the analysis was related to a sample that was discovered in PandaLabs anti-virus laboratory in November 2015 (MD5: A0973ADAF99975C1EB12CC1E333D302F), and since then we have been able to detect new variants or updates of this malicious program, since fundamentally they worked the same way.
Multigrain in detail: technical analysis
We started analyzing Multigrain, because this code, which shows the characteristics of RAM-Scraping, is typical of PoS malware. We can clearly see this in procedure 00405A10, shown below.

In this procedure, we find typical calls from a process that performs RAM-Scraping in the memory of running processes:
• CreateToolhelp32Snapshot to get the process list pointer;
• Process32FirstW and Process32NextW to get a snapshot of the list of processes after calling the previous API;
• OpenProcess is used later to get a list of memory pages with VirtualQueryEx ;
• Finally, with ReadProcessMemory, you can read the content from previous pages.
Once the buffer is received, using the content from each page, the malware will perform the corresponding "scrapping". To do this, it uses (in the same procedure) the second pseudocode:

If possible TRACKS1 / 2 sequences are detected, associated with the code from the magnetic stripe of a bank card in the buffers from the analyzed memory, the functions sub_406100 and sub_405D10 are called. Now the malware is ready to prepare the data so that it can be stolen later.
This PoS malware is only interested in two processes called “spcwin.exe” and “brain.exe”. If none of them is detected, then the “scrapping” will not be performed.

Data exfiltration
Exfiltration is performed during DNS queries (UDP, port 53) from procedure 00402C40, as shown in the following pseudocode:

Apparently, information leakage is carried out at three different points (two procedures) from the program:

In the first procedure (address 00401DA0), the “install.” Subdomain is used for the stolen information. In the second procedure (address 00402580), the “log.” Subdomain is used for this.
In these exfiltration procedures, we find various references to functions that encode information using "base32". This is due to the fact that in order to steal information from a bank card, it is first encrypted using "base32", and then DNS requests are made in the format: install. <Base32_CCs> .domain
Network information
Apparently, the domain for the sample: dojfgj.com
Whois Information:
Domain Name: DOJFGJ.COM
Registry Domain ID: 1979271903_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.enom.com
Registrar URL: www.enom.com
Updated Date: 2015-11-13T07: 16: 58.00Z
Creation Date: 2015-11-13T15: 16: 00.00Z
Registrar Registration Expiration Date: 2016-11-13T15: 16: 00.00Z
Registrar: ENOM, INC.
Registrar IANA ID: 48
Reseller: NAMECHEAP.COM
Domain Status: ok www.icann.org/epp#ok
Registry Registrant ID:
Registrant Name: WHOISGUARD PROTECTED
Registrant Organization: WHOISGUARD, INC.
Registrant Street: PO BOX 0823-03411
Registrant City: PANAMA
Registrant State / Province: PANAMA
Registrant Postal Code: 00000
Registrant Country: PA
Registrant Phone: +507.8365503
Registrant Phone Ext:
Registrant Fax: +51.17057182
Registrant Fax Ext:
Registrant Email: CC7F8D40E4FA4188AE5EA89A35925E6B.PROTECT@WHOISGUARD.COM
Registry Admin ID:
Admin Name: WHOISGUARD PROTECTED
Admin Organization: WHOISGUARD, INC.
Admin Street: PO BOX 0823-03411
Admin City: PANAMA
Admin State / Province: PANAMA
Admin Postal Code: 00000
Admin Country: PA
Admin Phone: +507.8365503
Admin Phone Ext:
Admin Fax: +51.17057182
Admin Fax Ext:
Admin Email: CC7F8D40E4FA4188AE5EA89A35925E6B.PROTECT@WHOISGUARD.COM
Registry Tech ID:
Tech Name: WHOISGUARD PROTECTED
Tech Organization: WHOISGUARD, INC.
Tech Street: PO BOX 0823-03411
Tech City: PANAMA
Tech State / Province: PANAMA
Tech Postal Code: 00000
Tech Country: PA
Tech Phone: +507.8365503
Tech Phone Ext:
Tech Fax: +51.17057182
Tech Fax Ext:
Tech Email: CC7F8D40E4FA4188AE5EA89A35925E6B.PROTECT@WHOISGUARD.COM
Name Server: NS1.DOJFGJ.COM
Name Server: NS2.DOJFGJ.COM
If we analyze this domain, we can see that it leads to the internal IP address "192.168.0.3". The domain is associated with two DNS servers. To get their current addresses, we need to do a “whois”:
$ whois ns2.dojfgj.com
Server Name: NS1.DOJFGJ.COM
IP Address: 104.156.246.159
The “traceroute” command of this IP address shows us its origin:
$ traceroute 104.156.246.159
traceroute to 104.156.246.159 (104.156.246.159), 30 hops max, 60 byte packets
1 104.131.0.253 (104.131.0.253) 0.423 ms 104.131.0.254 (104.131.0.254) 0.404 ms 0.437 ms
2 162.243.188.229 (162.243.188.229) 0.422 ms 0.394 ms 162.243.188.241 (162.243.188.241) 0.293 ms
3 xe-0-9-0-17.r08.nycmny01.us.bb.gin.ntt.net (129.250.204.113) 3.503 ms 4.078 ms 4.102 ms
4 ae-2.r25.nycmny01.us.bb.gin.ntt.net (129.250.3.97) 1.160 ms ae-3.r25.nycmny01.us.bb.gin.ntt.net (129.250.6.208) 1.226 ms 1.171 ms
5 ae-9.r22.asbnva02.us.bb.gin.ntt.net (129.250.2.149) 6.985 ms 6.926 ms 7.013 ms
6 ae-0.r23.asbnva02.us.bb.gin.ntt.net (129.250.3.85) 6.952 ms 7.091 ms 7.057 ms
7 ae-1.r20.miamfl02.us.bb.gin.ntt.net (129.250.2.87) 42.672 ms 33.314 ms 33.257 ms
8 ae-1.r05.miamfl02.us.bb.gin.ntt.net (129.250.2.185) 35.530 ms 35.327 ms 38.280 ms
9 xe-0-6-0-0.r05.miamfl02.us.ce.gin.ntt.net (129.250.207.174) 32.063 ms 31.912 ms 31.755 ms
ten * * *
11 104.156.246.159.vultr.com (104.156.246.159) 33.398 ms 31.757 ms 32.283 ms
As we can see, it corresponds to an Internet provider in Miami, which manages a range of IP addresses:
NetRange: 104.156.244.0 - 104.156.247.255
CIDR: 104.156.244.0/22
NetName: NET-104-156-244-0-22
NetHandle: NET-104-156-244-0-1
Parent: CHOOPA (NET-104-156-224-0-1)
NetType: Reassigned
OriginAS:
Organization: Vultr Holdings, LLC (VHL-57)
Vitality
In order to remain “robust” in the system (Windows PoS), the malware being analyzed automatically installs itself as a service and selects the name “Windows Module Extension”, as seen in the following screenshot (procedure 00406C20):
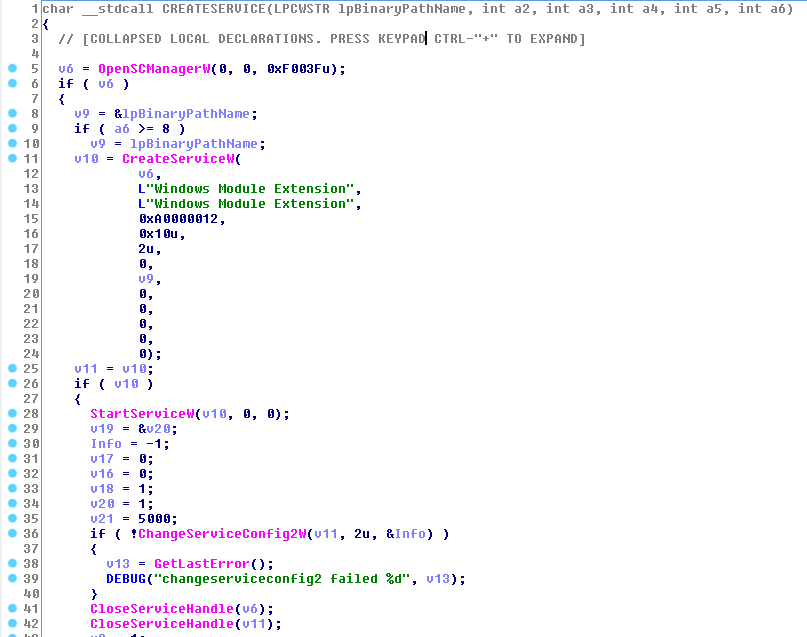
The hacker can make exceptions while he is registering himself as a service: he checks the current region using “ipinfo.io” and depending on the answer the system can register as a service or not. This is especially useful if a hacker, for example, wants to avoid performing an attack on PoS systems in certain countries.
The malicious program accepts "i" as a parameter (from "install"), in this case it sets the "scrapping" process and sends the stolen information.

If this parameter is not specified (“i”), and in the event that the “spcwin.exe” or “brain.exe” processes are not found, the service will not be installed, and in addition to this, the malicious program will be automatically destroyed. Both processes are related to PoS software.
Source: https://habr.com/ru/post/307320/
All Articles