Debian Linux and Tor for a secure deb
On the first day of August, the official blog of the popular Debian Linux distribution got the news that anonymous Tor services are available for some Debian resources. The package, update and security repositories can be downloaded without leaving the Tor network.

The main goal of these innovations is to protect against data leakage, at least - metadata when loading deb packages .
The main distribution servers, Debian and Ubuntu, use plain HTTP and unencrypted network connections. This provides ample opportunities for intercepting traffic on the network, even to amateurs and just curious, but professionals are able to extract from this a lot of useful information. It would seem that if someone traced that the red-eyed type sitting in the metro car opposite, just downloaded and installed new desktop themes? However, if we look more broadly, not only administrators of local authorities will be in sight, but also IT services of financial institutions andhome mail server of the former US Secretary of State of every kind. structures. There are many who want to know what security updates are installed or not yet installed on these systems. Managing the repository through onion services Tor confuses the intruders with all the cards.
This begs the question: what is wrong with HTTPS ? Do not like HTTP, use a much more secure HTTPS protocol, encrypting a web session using SSL / TLS certificates. In addition to the high-risk SSL vulnerabilities coming to light more often than we would like, there are also significant privacy concerns related to the HTTPS solution architecture itself.
')
Using the Hidden Markov Model, a researcher from the University of Cambridge showed that by observing the size of the transmitted data, manipulating it, it is possible to determine to some extent which files are being downloaded or downloaded . On Habré already wrote about the various MiTM attacks associated with HTTPS, in particular, about the Kazakh state. A certificate specially designed for intercepting TLS encrypted traffic . Fortunately, not all web browser development teams appreciated this step positively, in FireFox 48 they refused to add state. Kazakhstan's certificate to the trusted root CA , however, a bad example can be contagious and the danger to ordinary non-sophisticated users is obvious. In addition, it is easy to raise the HTTP (S) mirror of the popular Linux OS repository and use it as you please. For this, a front company and rented hosting for 200 USD will do .
All these troubles are now easy to avoid, because the onionrings of Tor services do not depend on root CA provided by third parties.
Debian repositories hosted on Tor's anonymous proxy network solve another important problem — bypassing restrictions and accessing open source software . At first, she seemed somewhat speculative to me, but just the other day I felt that this was not only a problem of exotic sultanates. This is a 403 error when installing, updating software from Google Play in the Crimea - the result of following the American sanctions "Good Corporation". A quick search on the Internet will tell you how to bypass this byaku using a vpn and proxy server. I wonder how things are for iOS and Windows Phone users in Crimea?
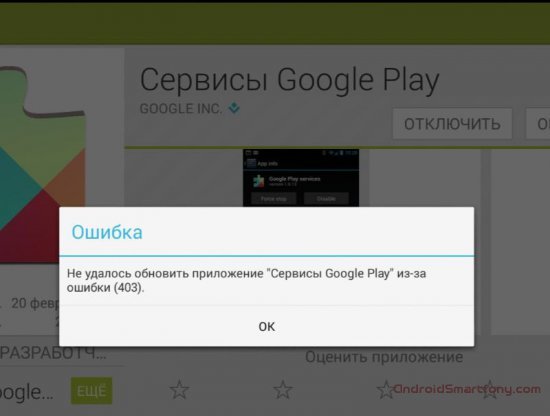
However, the rest of Google’s services in Crimea work well, this suggests that it’s not Sanctions but rather a profanation of them. Of course, you can call installed on an ordinary tablet, Android OS smartphone, free software and Google Play - its repository, you can only with a very big stretch of logic and facts, but in a sense, the indicated problem is present . If your mobile device or PC uses a Debian / Tor bundle, then such sanctions will not affect you.
I would like to hope that the integration of Tor services will become a precedent in other Linux OS, no doubt this is a step in the right direction.
In the simplest case, it suffices to write the paths to the Debian Linux repository configuration files
A more pedantic approach involves writing links.
in a separate
in
Do not forget to add the usual security update configuration if the Tor network is unavailable or unstable.
Write this in the

The main goal of these innovations is to protect against data leakage, at least - metadata when loading deb packages .
The main distribution servers, Debian and Ubuntu, use plain HTTP and unencrypted network connections. This provides ample opportunities for intercepting traffic on the network, even to amateurs and just curious, but professionals are able to extract from this a lot of useful information. It would seem that if someone traced that the red-eyed type sitting in the metro car opposite, just downloaded and installed new desktop themes? However, if we look more broadly, not only administrators of local authorities will be in sight, but also IT services of financial institutions and
This begs the question: what is wrong with HTTPS ? Do not like HTTP, use a much more secure HTTPS protocol, encrypting a web session using SSL / TLS certificates. In addition to the high-risk SSL vulnerabilities coming to light more often than we would like, there are also significant privacy concerns related to the HTTPS solution architecture itself.
')
Using the Hidden Markov Model, a researcher from the University of Cambridge showed that by observing the size of the transmitted data, manipulating it, it is possible to determine to some extent which files are being downloaded or downloaded . On Habré already wrote about the various MiTM attacks associated with HTTPS, in particular, about the Kazakh state. A certificate specially designed for intercepting TLS encrypted traffic . Fortunately, not all web browser development teams appreciated this step positively, in FireFox 48 they refused to add state. Kazakhstan's certificate to the trusted root CA , however, a bad example can be contagious and the danger to ordinary non-sophisticated users is obvious. In addition, it is easy to raise the HTTP (S) mirror of the popular Linux OS repository and use it as you please. For this, a front company and rented hosting for 200 USD will do .
All these troubles are now easy to avoid, because the onion
Debian repositories hosted on Tor's anonymous proxy network solve another important problem — bypassing restrictions and accessing open source software . At first, she seemed somewhat speculative to me, but just the other day I felt that this was not only a problem of exotic sultanates. This is a 403 error when installing, updating software from Google Play in the Crimea - the result of following the American sanctions "Good Corporation". A quick search on the Internet will tell you how to bypass this byaku using a vpn and proxy server. I wonder how things are for iOS and Windows Phone users in Crimea?

However, the rest of Google’s services in Crimea work well, this suggests that it’s not Sanctions but rather a profanation of them. Of course, you can call installed on an ordinary tablet, Android OS smartphone, free software and Google Play - its repository, you can only with a very big stretch of logic and facts, but in a sense, the indicated problem is present . If your mobile device or PC uses a Debian / Tor bundle, then such sanctions will not affect you.
I would like to hope that the integration of Tor services will become a precedent in other Linux OS, no doubt this is a step in the right direction.
Apt setup
In the simplest case, it suffices to write the paths to the Debian Linux repository configuration files
/etc/apt/sources.list with the apt-transport-tor package installed. deb tor+http://vwakviie2ienjx6t.onion/debian jessie main deb tor+http://vwakviie2ienjx6t.onion/debian jessie-updates main deb tor+http://sgvtcaew4bxjd7ln.onion/debian-security jessie/updates main A more pedantic approach involves writing links.
deb tor+http://vwakviie2ienjx6t.onion/debian/ jessie main deb-src tor+http://vwakviie2ienjx6t.onion/debian/ jessie main deb tor+http://vwakviie2ienjx6t.onion/debian/ jessie-updates main deb-src tor+http://vwakviie2ienjx6t.onion/debian/ jessie-updates main deb tor+http://vwakviie2ienjx6t.onion/debian jessie-backports main deb-src tor+http://vwakviie2ienjx6t.onion/debian/ jessie-backports main in a separate
/etc/apt/sources.list.d/00.vwakviie2ienjx6t.onion.list file and the security updates repository. deb tor+http://sgvtcaew4bxjd7ln.onion/ jessie/updates main in
/etc/apt/sources.list.d/00.sgvtcaew4bxjd7ln.onion.listDo not forget to add the usual security update configuration if the Tor network is unavailable or unstable.
deb http://security.debian.org/ jessie/updates main Write this in the
/etc/apt/sources.list.d/99.security.debian.org.list file.Source: https://habr.com/ru/post/307208/
All Articles