HEIST allows you to receive encrypted information in the HTTPS channel in clear text
The HTTPS protocol extension, which protects millions of sites and hundreds of millions of users, is vulnerable to a new type of attack. The exploit allows you to get encrypted email addresses, insurance numbers and other personal data of users. Moreover, the attacker does not need to monitor or control the victim’s Internet connection.
In other words, the exploit does not require the use of the MITM (man-in-the-middle) scheme. Instead, the victim is attacked with the help of an innocent JavaScript file hidden in an advertisement or “stitched” directly into the page of the malicious site. Malicious code after successful execution can request a number of types of pages protected by SSL or TSL protocol and receive the exact size of files with encrypted data, which are transmitted in protected mode. A new type of attack called HEIST (HTTP Encrypted Information can be Stolen Through TCP-Windows).
This attack works due to the fact that the script examines the type of response the framework gives to the client (usually a browser) from which the HTTP request came. Once an attacker receives information about the exact size of the encrypted data, he can use several previously known exploits to obtain test information hidden inside the encrypted file.
')
More specifically, BREACH (Browser Reconnaissance & Exfiltration via Adaptive Compression of Hypertext) and CRIME exploits are used here. BREACH allows you to get test information from a protected file in just 30 seconds. CRIME does not lag behind its fellow. CRIME allows you to select the content of cookies by using multiple requests, observing the values that zlib gives out. The exploit decrypts the value of cookies by 4-6 requests for each base64 byte.
HEIST technology was shown and explained at the Black Hat conference . According to information security experts, HEIST allows you to conduct attacks faster and more efficiently than before. Especially since the MITM scheme is no longer needed. The attackers get the necessary information almost immediately after the victim visits an infected site or a site with infected ads.
Until now, the attacker needed to actively control the traffic from the server to the user. HEIST allows you to remove this restriction. The exploit uses TCP characteristics as a quasi-cryptographic secondary channel to estimate the size of the HTTPS response. TCP splits large transmissions into smaller fragments of a certain size, called frames. In the following, frames are grouped inside “TCP windows”, sent one at a time. TCP sends a new window only after receiving confirmation of receipt of the previous frame group.
HEIST can calculate the number of frames and windows by interacting with a set of recently approved APIs. This is Resource Timing and Fetch. As a result, it turns out to determine the exact size of the HTTPS response. And then, as mentioned above, BREACH and CRIME come into play. At the exit, the attacker gets previously closed information. Experts have already presented the results of their work by Google and Microsoft. So the method presented on Black Hat did not come as a surprise to these companies. An attacker only needs to know the victim's CSRF token, after which the user’s account on a specific site can be compromised.
According to the authors of the work presented on Black Hat, the user can reduce the likelihood of a successful HEIST attack by prohibiting third-party cookies in the browser settings. On the other hand, a number of services simply will not work without third-party cookies.
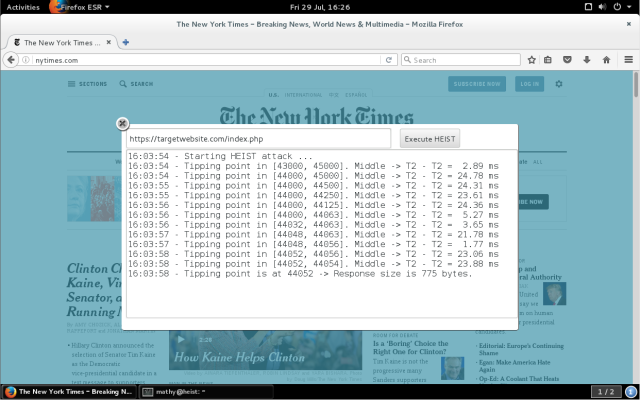
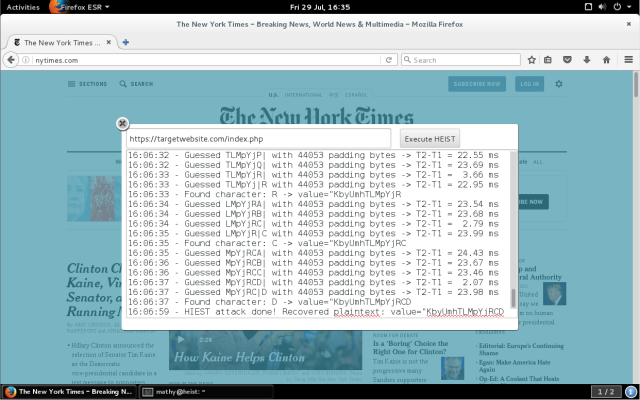
When demonstrating the attack, we were able to measure the size of the encrypted responses for the New York Times, using the site targetwebsite.com.
HEIST is also effective against HTTP / 2, the updated HTTP standard. In some situations, the HTTP / 2 features even increase HEIST performance. In particular, if HTTP / 2 is used, the exploit can simultaneously poll several sources.
Now, according to the authors of the work, the combined attack using BREACH and HEIST is one of the most simple methods of compromising user accounts of various resources.
Our other publications:
Source: https://habr.com/ru/post/307206/
All Articles