Fairy Tales Ransomwhere: Cerber on the rise

Cerber is a relatively new family of cryptographers that has been hard hit in the last few months. In this article we want to look at some of the techniques that are used to infect their victims.
Chapter 2: Cerber
In my first article in this series, I talked about using a Windows utility, known as PowerShell, to infect computers with a cryptographer. This can be done in various ways, but PowerShell was called for a reason: it is really powerful! One of the easiest ways to use it is to download the file (malicious!) And launch it. Of course, before you do this, you need to start PowerShell, which can be done with the help of some script, a macro inside Office documents, or as a “payload” in some exploits. In the case of Cerber, exploit kits are usually used.
')
Thanks to all the information we have, you can easily filter this kind of data. Over the last 3 months, over 3,000 infection attempts were blocked, which used PowerShell to download and download a malware (cryptographer):
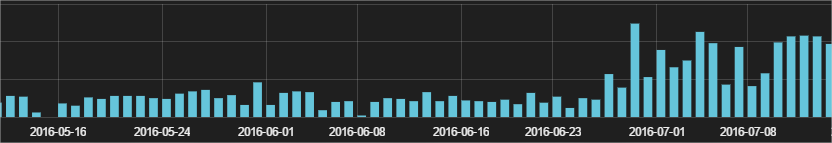
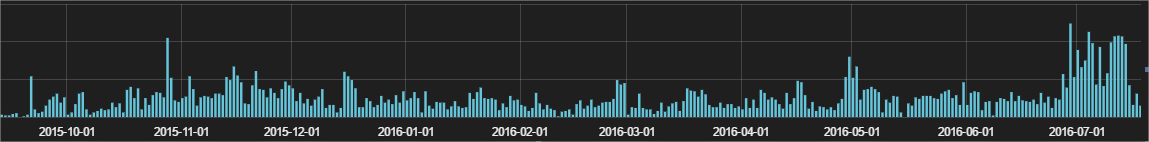
After a quick run, I would like to say that this is Cerber, although there may be different families of cryptographers (since we block all infections, we don’t need to check every binary code, except when it is required for research purposes). Most of these attacks occurred in the first weeks of July. If we go back to October last year, we can see that this is actually the largest wave of infections using this technique in the last 10 months:
Several hashes were randomly selected among the many thousands of hashes that we block, in case you want to play with them in your laboratory and protect your users:
List_Cipher
Another, quite current way today is to execute a malicious program for infecting victims with the help of Cerber - through WMIC, the Windows version of the Windows Management Instrumentation (WMI) for the command line. So far, all the cases that we have observed have occurred through exploits on computers with Internet Explorer. A sample of the malware is downloaded to the computer, and instead of executing it immediately, it uses the WMIC to execute it (thus, an attempt is made to give a legal behavior, since WMIC is a non-malicious program that belongs to the Windows operating system). Over the past 4 weeks, we have blocked more than 3,000 infection attempts using a similar "trick":
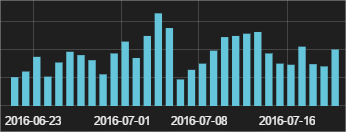
Here is a sample of some encryption hashes using this technique with WMIC, which we stopped for 3 days:
list_coding_2
Stay tuned until the next chapter of Ransomwhere Tales.
Article author: Louis Corrons
Source: https://habr.com/ru/post/307016/
All Articles