Graphic password does not allow the viewer to steal himself.
In this article I will tell about my thesis project on the theme “Iconographic method of user authentication. Is it possible to authenticate so that the person next to you, following your actions, cannot authenticate for you ”. In this publication I will briefly tell you the essence of the project.

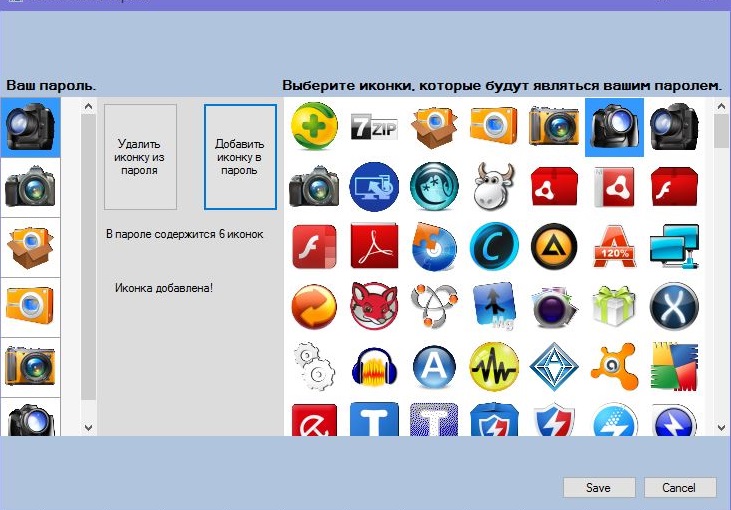
Before authenticating, you must first select a password. The password is selected from a large set of icons and must consist of at least three different icons (hereinafter they will be called password icons). In this example, we selected 6 password icons. We now turn to the authentication itself.
')

Authentication is as follows. The panel randomly houses a common set of icons, among which there will be 3 password icons from the selected password. The user should visually find three password icons, mentally connect them with lines, get a triangle and click the mouse inside this triangle.
Then all the icons are shuffled, some disappear, some new ones appear, as well as new password icons from the selected password (there can be a maximum of 3 password icons on the panel). And the user performs such a procedure several times; if he clicks inside the triangle a specified number of times, the authentication is considered to be passed. If the user at any stage of authentication misses, then authentication is considered not passed and you need to go through all the steps again.
Immediately there are several questions:
We will carry out statistical modeling and find out the probability of hitting a mouse click in the password triangle in stage 1 with different aspect ratios.
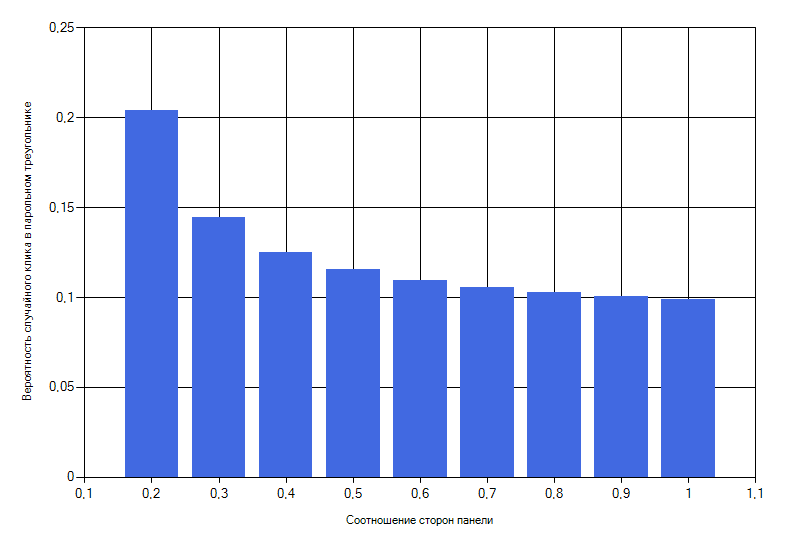
From this histogram, it can be seen that, the more the password panel approaches the square view, the probability of hacking becomes smaller and approximately equal to 10%. Therefore, the most preferred aspect ratio is 1: 1.
The calculations were carried out with a panel width of 5, 15 and 20 cells for icons. However, the results obtained do not practically differ from each other.
But the 10% probability of hitting the password triangle is too high. Therefore, authentication is carried out in several stages and it turns out that at the second stage of authentication, the probability of hacking is approximately equal to 10 ^ -2.
The idea for writing the program was taken from here . Statistical observations were made and the probability of breaking the password triangle was determined.

Formulation of the problem
- Develop a program and implement cryptographic authentication, during the passage of which, an outsider would not be able to repeat it;
- Determine the probability of hacking, such authentication.
Remember password

Before authenticating, you must first select a password. The password is selected from a large set of icons and must consist of at least three different icons (hereinafter they will be called password icons). In this example, we selected 6 password icons. We now turn to the authentication itself.
')
Authentication

Authentication is as follows. The panel randomly houses a common set of icons, among which there will be 3 password icons from the selected password. The user should visually find three password icons, mentally connect them with lines, get a triangle and click the mouse inside this triangle.
Then all the icons are shuffled, some disappear, some new ones appear, as well as new password icons from the selected password (there can be a maximum of 3 password icons on the panel). And the user performs such a procedure several times; if he clicks inside the triangle a specified number of times, the authentication is considered to be passed. If the user at any stage of authentication misses, then authentication is considered not passed and you need to go through all the steps again.
Immediately there are several questions:
- What is the probability of accidentally hitting the password triangle?
- How many authentication steps do I need to get reliable protection?
The probability of hitting a random mouse click in the password triangle
We will carry out statistical modeling and find out the probability of hitting a mouse click in the password triangle in stage 1 with different aspect ratios.

From this histogram, it can be seen that, the more the password panel approaches the square view, the probability of hacking becomes smaller and approximately equal to 10%. Therefore, the most preferred aspect ratio is 1: 1.
The calculations were carried out with a panel width of 5, 15 and 20 cells for icons. However, the results obtained do not practically differ from each other.
But the 10% probability of hitting the password triangle is too high. Therefore, authentication is carried out in several stages and it turns out that at the second stage of authentication, the probability of hacking is approximately equal to 10 ^ -2.
Program settings
- In the program, you can adjust the saturation of the panel with icons, on the one hand 100% saturation makes it difficult to find password icons, on the other hand, when saturation is less than 20%, there is a possibility that a person standing nearby can analyze and understand which icons are password-based. The optimal saturation of the panel with icons is 40-60%;
- For reliable protection, 5 stages of authentication of 10 ^ -5 are sufficient;
- The panel aspect ratio is also adjusted.
Conclusion
- With respect to the sides of the 1: 1 password entry window, the probability of hacking is minimal. However, a change in the ratio of the parties down to 0.8: 1 does not cause a critical increase in the probability of hacking;
- No significant influence of the size of the iconographic panel on the probability of hacking has been identified;
- The degree of filling of the password panel should be in the range from 40 to 60%. The optimal fill value is 50%, which, on the one hand, makes it difficult to disclose the password by an outsider, and on the other hand, does not cause difficulties when searching for password icons;
- Conducting iconographic authentication in 5 stages is enough for reliable protection of most applications. For especially critical applications requiring enhanced security measures, authentication can be performed in 6 or 7 steps.
- The performed computational experiments allow us to conclude that for iconographic authentication carried out in stage 1, the probability of hacking is quite high and amounts to about 0.1 (10%). However, with an increase in the number of stages, the probability of selecting a password decreases exponentially, and, for example, for 5 stages it does not exceed 10 ^ -5.
- With the iconographic method of password protection, the password, as such, is not transmitted over the network, even in encrypted form. Only the coordinates of the mouse click in the password entry window are transmitted over the network, and only the server decides whether this point falls inside the triangle specified by the password icons. Consequently, even complete interception of all information exchanged between the terminal and the server does not provide additional data for cracking the password. In addition, the password is impossible to peep, because, even when standing at the user's shoulder, it is impossible to know which triangle he clicked inside. Consequently, the only possible way to crack the iconographic protection is by accidentally clicking in the password entry window.
List of sources
The idea for writing the program was taken from here . Statistical observations were made and the probability of breaking the password triangle was determined.
Source: https://habr.com/ru/post/306736/
All Articles