Why in Ukraine there are still white hackers
This article will be a response to the recent publication of Vladimir Taratushka.
I had several reasons for writing this article.
The first is to show that there are white hackers in Ukraine. They exist thanks to one of the vulnerability search promotion programs that Privatbank has been conducting .
The next reason is to tell your success story of work with one of the largest banks in Ukraine under this program.
I also want to show the effectiveness of such a program with a real example and encourage those companies that for some reason doubt or don’t see any real advantages in organizing such programs.
And the last reason is to show future and present managers that participation in bug-bounty programs is interesting, ethical and financially beneficial.
I do not consider myself a professional hacker, I do not have a security education profile, I do not have certificates, I have not read the Talmud TCP / IP protocol specifications, and I have not participated in hackathons and other professional hacker competitions. At the same time, I have experience in programming and writing various web services in PHP, Python, and Java. And I roughly understand where programmers usually make mistakes and which aspects of security are ignored when developing web applications. For me, this is enough to successfully find the vulnerabilities of the most critical level.
At the moment, my experience as a receiver is 3 years. That is how much time I take part in the vulnerability search program of PrivatBank.
From the very beginning I kept records of all the vulnerabilities found. I saved in a separate file a detailed description of the vulnerability, mode of reproduction, screenshots of confirmation. The latter help, if for some reason the developers of the bank fail to reproduce the vulnerability, or it turns out to be closed by another update before the start of the check. Some time later, I began to fill in the file the time of application, fix time, the amount of remuneration. Because of this, I have some statistics with which I would like to introduce you today.
')
So, at the moment I have collected statistics on 55 vulnerabilities I have declared, all of which are currently closed.
According to statistics on application status, the picture is as follows:
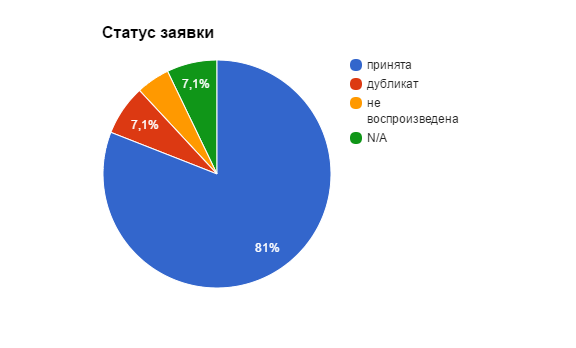
As you can see, most applications are accepted for work. Some vulnerabilities were not reproduced by the developers of the bank due to their complexity or because at the time of how the vulnerability was taken into operation, this service was radically rewritten. There were also duplicates, but as a rule they were simple, easily detectable vulnerabilities. N / A - this means that for some reason I did not save the results for this application. All applications with “accepted” status were eventually closed and rewards were paid for them.
Type of vulnerability / attack classification OWASP:
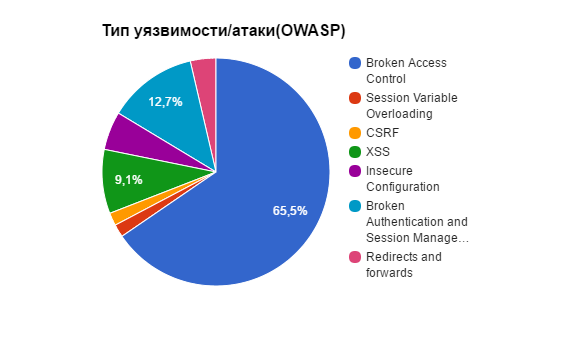 According to the classification of vulnerabilities it can be seen that the most common type is Broken Access Control. These are the vulnerabilities that allow unauthorized access to be obtained by simply iterating through the values that specify the user id or operation. The reason is that such vulnerabilities are the easiest to detect and they are the result of errors in the application architecture. Since a bank is a complex system of numerous internal subsystems interacting with each other, such as back-office, processing, antifraud, this imposes certain difficulties on the implementation of the interaction of the web application with these systems within the framework of the end-user rights of the service. This leads to the emergence of such vulnerabilities as access to statements on the cards of other users, access to private data and, ultimately, access to funds of users.
According to the classification of vulnerabilities it can be seen that the most common type is Broken Access Control. These are the vulnerabilities that allow unauthorized access to be obtained by simply iterating through the values that specify the user id or operation. The reason is that such vulnerabilities are the easiest to detect and they are the result of errors in the application architecture. Since a bank is a complex system of numerous internal subsystems interacting with each other, such as back-office, processing, antifraud, this imposes certain difficulties on the implementation of the interaction of the web application with these systems within the framework of the end-user rights of the service. This leads to the emergence of such vulnerabilities as access to statements on the cards of other users, access to private data and, ultimately, access to funds of users.
It is also certain that the imprint on this rating is put off by my personal preferences and the set of knowledge that I possess and which I use when searching for vulnerabilities.
Type of information received or access in case of exploitation of a vulnerability:
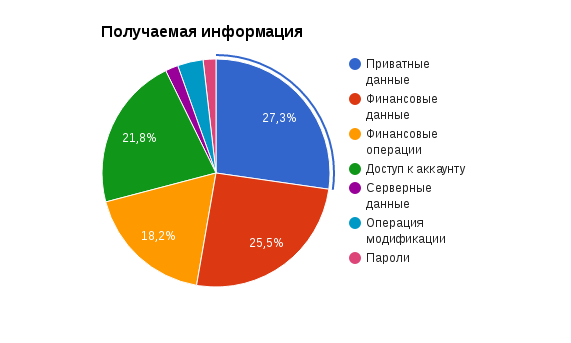
As can be seen from the statistics, most often it was possible to gain access to private data (full name, passport data, card numbers, phone numbers, addresses), financial data (account balance, statement, etc.), accounts in different services (usually due to XSS or Open Redirect) and, which is not unimportant, in 1 of 5 cases access to the financial means of other users.
Fix time This is a conditional value. Since I did not have information about the exact time of closing the vulnerability, I took the time that passed from the moment of filing the application to the notification of the planned payment of remuneration.
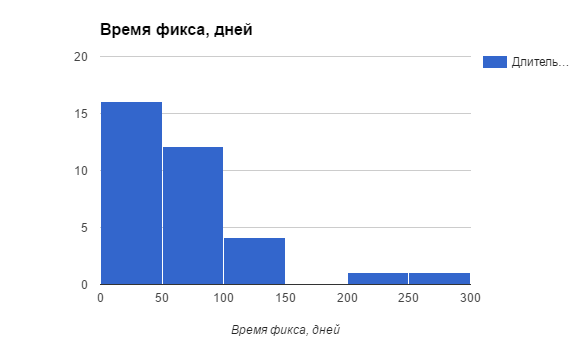
As you can see, most often the alert came within 2 months, but sometimes there was no response for 3-4 months for some vulnerabilities.
And of course, the most interesting moment for researchers is the average amount of remuneration on closed applications. I'll warn you right away that the amount of the remuneration was not tied to the dollar exchange rate until mid-2015, so for some time it decreased in dollar terms due to the rapid growth of the dollar exchange rate to the hryvnia.
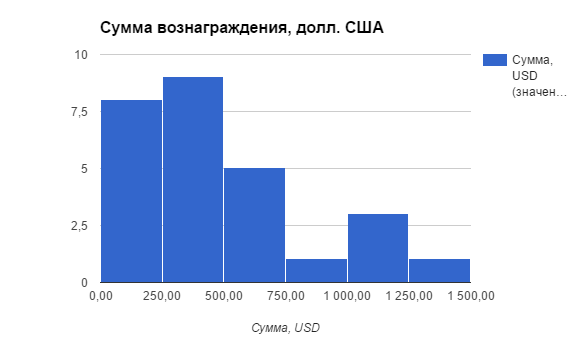
As you can see, most often the amount of remuneration falls in the range of $ 50-500.
Now for some details. Below, I have compiled a long list with a brief description of each vulnerability, so that we can get a rough idea of the criticality of each of them:
Thus, analyzing the criticality of the above vulnerabilities, you can evaluate the effectiveness of this program for the bank.
And finally, I would like to dispel the persistent, but erroneous opinion of many that it is better not to work with PrivatBank, since they can be accused of hacking, as was described in the story with Alexei Mokhov .
The main principle of a white hacker is ethical. The search for vulnerabilities should be conducted exclusively on the accounts and accounts of the “burglars” themselves or their relatives / friends / acquaintances with their personal permission. Also, if the vulnerability was searched for within the framework of the bug-bounty of the program, it should be disclosed only after its closure and only with the permission of the owner of the resource on which it was found. Then all your actions will not be carried out to the detriment of the company and will not violate the law, and therefore there will be no complaints against you, as a researcher.
I had several reasons for writing this article.
The first is to show that there are white hackers in Ukraine. They exist thanks to one of the vulnerability search promotion programs that Privatbank has been conducting .
The next reason is to tell your success story of work with one of the largest banks in Ukraine under this program.
I also want to show the effectiveness of such a program with a real example and encourage those companies that for some reason doubt or don’t see any real advantages in organizing such programs.
And the last reason is to show future and present managers that participation in bug-bounty programs is interesting, ethical and financially beneficial.
I do not consider myself a professional hacker, I do not have a security education profile, I do not have certificates, I have not read the Talmud TCP / IP protocol specifications, and I have not participated in hackathons and other professional hacker competitions. At the same time, I have experience in programming and writing various web services in PHP, Python, and Java. And I roughly understand where programmers usually make mistakes and which aspects of security are ignored when developing web applications. For me, this is enough to successfully find the vulnerabilities of the most critical level.
At the moment, my experience as a receiver is 3 years. That is how much time I take part in the vulnerability search program of PrivatBank.
From the very beginning I kept records of all the vulnerabilities found. I saved in a separate file a detailed description of the vulnerability, mode of reproduction, screenshots of confirmation. The latter help, if for some reason the developers of the bank fail to reproduce the vulnerability, or it turns out to be closed by another update before the start of the check. Some time later, I began to fill in the file the time of application, fix time, the amount of remuneration. Because of this, I have some statistics with which I would like to introduce you today.
')
So, at the moment I have collected statistics on 55 vulnerabilities I have declared, all of which are currently closed.
According to statistics on application status, the picture is as follows:

As you can see, most applications are accepted for work. Some vulnerabilities were not reproduced by the developers of the bank due to their complexity or because at the time of how the vulnerability was taken into operation, this service was radically rewritten. There were also duplicates, but as a rule they were simple, easily detectable vulnerabilities. N / A - this means that for some reason I did not save the results for this application. All applications with “accepted” status were eventually closed and rewards were paid for them.
Type of vulnerability / attack classification OWASP:
 According to the classification of vulnerabilities it can be seen that the most common type is Broken Access Control. These are the vulnerabilities that allow unauthorized access to be obtained by simply iterating through the values that specify the user id or operation. The reason is that such vulnerabilities are the easiest to detect and they are the result of errors in the application architecture. Since a bank is a complex system of numerous internal subsystems interacting with each other, such as back-office, processing, antifraud, this imposes certain difficulties on the implementation of the interaction of the web application with these systems within the framework of the end-user rights of the service. This leads to the emergence of such vulnerabilities as access to statements on the cards of other users, access to private data and, ultimately, access to funds of users.
According to the classification of vulnerabilities it can be seen that the most common type is Broken Access Control. These are the vulnerabilities that allow unauthorized access to be obtained by simply iterating through the values that specify the user id or operation. The reason is that such vulnerabilities are the easiest to detect and they are the result of errors in the application architecture. Since a bank is a complex system of numerous internal subsystems interacting with each other, such as back-office, processing, antifraud, this imposes certain difficulties on the implementation of the interaction of the web application with these systems within the framework of the end-user rights of the service. This leads to the emergence of such vulnerabilities as access to statements on the cards of other users, access to private data and, ultimately, access to funds of users.It is also certain that the imprint on this rating is put off by my personal preferences and the set of knowledge that I possess and which I use when searching for vulnerabilities.
Type of information received or access in case of exploitation of a vulnerability:

As can be seen from the statistics, most often it was possible to gain access to private data (full name, passport data, card numbers, phone numbers, addresses), financial data (account balance, statement, etc.), accounts in different services (usually due to XSS or Open Redirect) and, which is not unimportant, in 1 of 5 cases access to the financial means of other users.
Fix time This is a conditional value. Since I did not have information about the exact time of closing the vulnerability, I took the time that passed from the moment of filing the application to the notification of the planned payment of remuneration.

As you can see, most often the alert came within 2 months, but sometimes there was no response for 3-4 months for some vulnerabilities.
And of course, the most interesting moment for researchers is the average amount of remuneration on closed applications. I'll warn you right away that the amount of the remuneration was not tied to the dollar exchange rate until mid-2015, so for some time it decreased in dollar terms due to the rapid growth of the dollar exchange rate to the hryvnia.

As you can see, most often the amount of remuneration falls in the range of $ 50-500.
Now for some details. Below, I have compiled a long list with a brief description of each vulnerability, so that we can get a rough idea of the criticality of each of them:
Vulnerability Table
| No | Domain | Type of Vulnerability / Attack (OWASP) | Access type | Short description |
|---|---|---|---|---|
| one | privat24.privatbank.ua | Broken access control | Private data | Getting critical data of any card |
| 2 | privat24.privatbank.ua | Broken access control | Private data | Access to user payment archive |
| 3 | privat24.privatbank.ua | Broken access control | Private data | Access to private user data (full name, passport data, the amount of balance and debt) |
| four | privat24.privatbank.ua | Broken access control | Private data | Access to private user data (name, passport data, mother's maiden name) |
| five | privat24.privatbank.ua | Broken access control | Financial data | View statements by card number |
| 6 | privat24.privatbank.ua | Broken access control | Financial operations | Payment sms mailing from someone else's card |
| 7 | liqpay.com | Broken access control | Financial data | Customer Payment Information |
| eight | napi.privatbank.ua | Broken access control | Private data | Receiving critical data of another Internet card |
| 9 | napi.privatbank.ua | Broken access control | Financial data | Buying cars / train tickets on another's card |
| ten | privat24.privatbank.ua | Broken access control | Financial operations | Creating a regular payment on someone else's card |
| eleven | pcalendar.privatbank.ua | Broken access control | Financial operations | Change the status of any regular payment, re-create, even if it was deleted, view data on it |
| 12 | siteheart.com | Session Variable Overloading | Account access | Full access to any siteheart.com account |
| 13 | privat24.privatbank.ua | CSRF | Private data | Connecting your phone to SMS informing about transactions on another card |
| 14 | privat24.privatbank.ua | Broken access control | Financial operations | Creating a regular payment on someone else's card |
| 15 | cards.privatbank.ua | Xss | Account access | Theft of authorized user cookies |
| sixteen | privat24.privatbank.ua | Broken access control | Financial operations | Mass replenishment of mobile phones from someone else’s card |
| 17 | ecommerce.liqpay.com | Broken access control | Financial operations | Payment from someone else’s card when paying for services on the merchant’s website connected to PrivatBank |
| 18 | privat24.privatbank.ua | Broken access control | Private data | Getting phone numbers connected to the SMS notification service for any PrivatBank card |
| nineteen | privat24.privatbank.ua | Broken access control | Private data | View information on utility payments of privat24 clients (full name, residential address, mobile number, debt) |
| 20 | pcalendar.privatbank.ua | Broken access control | Financial data | Balance on any PrivatBank card |
| 21 | pcalendar.privatbank.ua | Broken access control | Financial operations | Creating a regular payment on someone else's card |
| 22 | pcalendar.privatbank.ua | Broken access control | Financial operations | Creating a regular payment on someone else's card |
| 23 | privat24.privatbank.ua | Insecure Configuration | Server data | Directory structure opened |
| 24 | privat24.privatbank.ua | Broken access control | Modification operation | Receiving and changing the Internet limit on any PrivatBank card |
| 25 | privat24.privatbank.ua | Broken access control | Financial data | View statements by card number, there are addresses and gps coordinates of ATMs and self-service terminals used by the client |
| 26 | privat24.privatbank.ua | Insecure Configuration | Financial data | Google checks available |
| 27 | transfers.privatbank.ua | Broken access control | Financial data | Information on private transfers24 (PrivatMoney, Golden Crown, Unistream, Western Union, Contact, Coinstar and Swift) |
| 28 | privat24.privatbank.ua | Broken access control | Financial operations | Creating a regular payment on someone else's card |
| 29 | privat24.privatbank.ua | Broken access control | Private data | View information on utility payments of privat24 clients (full name, residential address, mobile number, debt) |
| thirty | privat24.privatbank.ua | Broken access control | Financial data | Information on applications for a credit rating in UBKI (full name, TIN, date of birth, credit rating, etc.) |
| 31 | client-bank.privatbank.ua | Broken access control | Financial data | Obtaining acquiring statement for any merchant of PrivatBank |
| 32 | client-bank.privatbank.ua | Broken access control | Passwords | Receipt of the password of any merchant registered in privat24 in acquiring. In addition to the password, a card number is available for receiving payments, the client’s name, the client’s website address, ip address, etc. |
| 33 | limit.pb.ua | Broken Authentication and Session Management | Private data | Detailed information on the client (name, card number, phone number, date of birth, residential address, etc.) |
| 34 | privat24.privatbank.ua | Broken access control | Private data | Receipt of the owner’s name, phone number, card validity by card number |
| 35 | socauth.privatbank.ua | Insecure Configuration | Private data | Detailed information on the client (name, card number, phone number, date of birth, residential address, etc.) |
| 36 | privat24.privatbank.ua | Broken Authentication and Session Management | Account access | Repeatedly logging in to private24 by the generated link without entering a static and password password even after the end of the user’s session. |
| 37 | chat.sender.mobi | Xss | Account access | Theft of authorized user cookies |
| 38 | msb.privatbank.ua | Xss | Account access | Theft of authorized user cookies |
| 39 | mypayments.privatbank.ua | Broken Authentication and Session Management | Private data | Detailed information on the client (name, card number, phone number, date of birth, residential address, etc.) |
| 40 | privat24.privatbank.ua | Broken Authentication and Session Management | Financial data | Statements on user cards. |
| 41 | liqpay.com | Broken Authentication and Session Management | Account access | Weak user session protection during authorization via a call to a mobile phone |
| 42 | client-bank.privatbank.ua | Broken access control | Financial data | Statements on any terminal connected to acquiring. |
| 43 | client-bank.privatbank.ua | Broken access control | Financial data | View documents jur. persons created using the document designer |
| 44 | chat.sender.mobi | Xss | Account access | Theft of authorized user cookies |
| 45 | bank24.privatbank.ua | Xss | Account access | Theft of authorized user cookies |
| 46 | blago.privatbank.ua | Broken access control | Financial operations | Vulnerability allows any registered user to replace any other user’s card with their own to receive donations |
| 47 | client-bank.privatbank.ua | Broken access control | Financial data | Information on foreign contracts with foreign partners |
| 48 | client-bank.privatbank.ua | Broken access control | Private data | Information about users who have access to the specified account, namely the login (sometimes it is a phone number), name, email. |
| 49 | privat24.privatbank.ua | Broken access control | Modification operation | Mass change (at least reduction) of credit limits on PrivatBank customer cards |
| 50 | nkk.privatbank.ua | Broken access control | Private data | Access to information that the client fills in when applying for a loan |
| 51 | privat24.privatbank.ua | Redirects and forwards | Account access | Access to a user account through a token received through Open Redirect |
| 52 | client-bank.privatbank.ua | Broken Authentication and Session Management | Account access | Access to a user account through a token obtained through the referer on the statistics website |
| 53 | client-bank.privatbank.ua | Redirects and forwards | Account access | Access user account via phishing using Open Redirect |
| 54 | client-bank.privatbank.ua | Broken Authentication and Session Management | Account access | Access to a user account through a token obtained through the referer on the statistics website |
| 55 | client-bank.privatbank.ua | Broken access control | Financial data | Access to contracts with foreign partners clients |
Thus, analyzing the criticality of the above vulnerabilities, you can evaluate the effectiveness of this program for the bank.
And finally, I would like to dispel the persistent, but erroneous opinion of many that it is better not to work with PrivatBank, since they can be accused of hacking, as was described in the story with Alexei Mokhov .
The main principle of a white hacker is ethical. The search for vulnerabilities should be conducted exclusively on the accounts and accounts of the “burglars” themselves or their relatives / friends / acquaintances with their personal permission. Also, if the vulnerability was searched for within the framework of the bug-bounty of the program, it should be disclosed only after its closure and only with the permission of the owner of the resource on which it was found. Then all your actions will not be carried out to the detriment of the company and will not violate the law, and therefore there will be no complaints against you, as a researcher.
Source: https://habr.com/ru/post/306694/
All Articles