New firmware for iPhone?
Here you will not believe. I come late from work, connect my phone to my laptop and what do I see?
And I see a warning by the ITUN that a new firmware for my device is ready for Apple ...
Here I sit and think ... stitch or not?
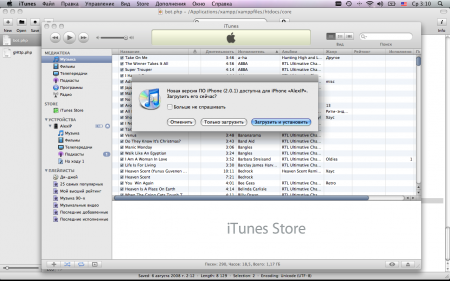
And I see a warning by the ITUN that a new firmware for my device is ready for Apple ...
Here I sit and think ... stitch or not?

')
Source: https://habr.com/ru/post/30663/
All Articles