World of Warcraft: one line of code to lose everything

Imagine the situation: in the game, a character who introduced himself as a member of one of the popular and famous guilds, comes up to you and promises rare cool elements, rare animals (on which you can travel) weapons, etc. Most likely such a Persian has neither rare elements nor special codes for them. As a result, the victim does not receive the correct code or any rare item. The attacker was able to convince the unsuspecting player to enter just one command in the dialog box.
/run RemoveExtraSpaces=RunScript The WoW interface (for example, the menu bar, the chat window, and other 2D graphic elements) and also add-ons are written in the Lua language. Both sides of the string are RemoveExtraSpaces and also RunScript are legal functions and are part of the WoW Lua API. But the introduction of this line of code in the dialog box changes the behavior of the WoW interface.
')
What does this team really do?
/run - a command to interpret the following text as a Lua script.RemoveExtraSpaces is a built-in function that removes unwanted spaces from text.RunScript is a function that executes text as Lua code (similar to the /run command)Why is this dangerous?
The RemoveExtraSpaces function is called every time a player receives a new message. The
/run command above replaces the RemoveExtraSpaces function with a RemoveExtraSpaces function that originally exists in the software. After the original function is rewritten, each new chat message is interpreted as Lua code and immediately executed. The script is as follows.A reckless player enters a maliciously crafted line of code in his dialog box because he was convinced by the words of the attacker. But instead of receiving rare items, he becomes a victim.
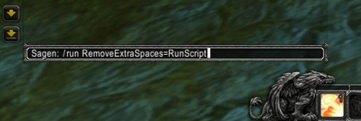
Unsuspecting player is about to send a malicious code line.
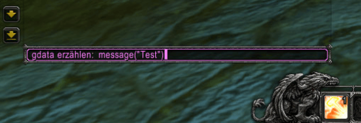
The attacker sends a chat message to the victim
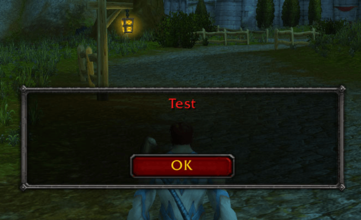
The received message is interpreted as Lua code and then executed.
What has been shown above is a fairly harmless example of this vulnerability, proof of concept. But actually - this means that the attacker can now remotely control the victim's interface. This is very similar to the behavior of Trojans, who pretend to be something useful and then perform their malicious function. In the real case, instead of creating messages with the text “Test”, the attackers launch another script, an example of which will be given below.
Temporarily hide and save a command
After the victim has opened the backdoor to his interface, the attacker sends the following message:
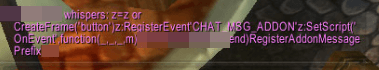
The attacker establishes a new data channel
In case the command was executed, the message that is shown above will not be visible to the victim, but will be executed immediately. The fact that the chat feature is no longer working may seem suspicious and the victim may try to restart the game. The attacker acts quickly enough to solve this problem. By sending the command shown above, which establishes a new communication channel, they again restore normal chat operation without arousing suspicion.
In order to understand the purpose of this command, you need to know that WoW has the ability to communicate using a hidden channel (locally and remotely). This channel is established through the use of “CHAT_MSG_ADDON” events.

The script creates a frame (line 2) to which you can set various properties. The script logs CHAT_MSG_ADDON events with a specific prefix (lines 6 and 25). Only those who know the selected prefix can secretly control the victim's interface. It's like a password for backdoor.
Each time a hijacked interface receives a CHAT_MSG_ADDON event with a secret prefix, the code will run silently and without the knowledge of the victim.
Conclusion: until the attacker decides to show you what is happening, you, unfortunately, will not know about it.
Even though we are talking about add-ons that can communicate through a covert channel, the victim does not need to have add-ons in order for the attack to succeed.
What harm can be done?
Since the attacker will have full access to the victim’s interface, he can gather complete information about him. But the burglar will not be able to collect any detailed information about other players. In WoW, players have the opportunity to share / sell items to each other. If the attacker knows the location of the victim’s character and is within reach, he can open the trade window remotely and transfer gold, objects and everything that can be transferred to him. Virtually rob the victim.
The described scenario demonstrates a social attack along with a technical one. Now a hacker can send a convincing message to friends, colleagues and other players with whom the character communicates with the help of the victim, thereby increasing the number of captured characters.
How can you protect yourself?
The answer is simple and obvious: you do not need to enter this kind of command or any other command that will be offered even to you by a long-standing friend.
In this example, we talked about the attacking character in the game, who belonged to the popular guild. But in fact he did not belong to this guild. He chose a famous guild and copied the name, replacing “L” with “I”. You may already be familiar with this method of phishing attacks.
In addition, be careful when downloading add-ons use protected and popular websites, save your add-ons so that they can be replaced at any time. It is possible that some of these updates may already contain malicious code. A similar problem was noticed in 2014, when the so-called “ElvUI Backdoor” was discovered in one of the add-ons.
The glitch itself can only be fixed by Blizzard. They must ensure that such a function cannot be rewritten in the future. Blizzard has already released a pre-release for the upcoming Legion expansion. In this supplement, they took into account the scenario discussed here and added a warning before sending a message that contains a malicious character.
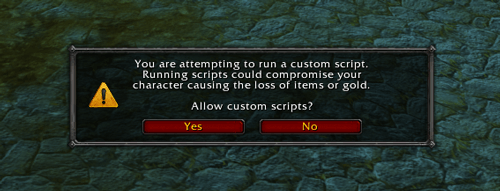
Selecting “Yes” disables the message permanently, even a restart will not return it - for this reason the issue cannot be considered resolved. To reactivate this message, you must manually delete one line of code in the config file.
Code to be removed:
SET AllowDangerousScripts "1"File: c
onfig-cache.wtfPath:
World of Warcraft\WTF\Account\\Source: https://habr.com/ru/post/306618/
All Articles