Destroy SSD in 7 seconds: tactical protection of information from unauthorized access
"Any value is controlled only by one who is able to destroy it"
- Dune, Frank Herbert
In the second year of uni, my classmate got a job as an assistant administrator. A month later, in the cafeteria, he (I was and three other groupmates) boasted that he wrote a software program that allowed him to download files from the Internet through a corporate account (let me remind you that in those days one mp3 swung an hour). Another classmate for pivas told it already in his company of friends, and those without his knowledge decided to play tricks. Databases with phone numbers, addresses, traffic police and others have long walked along, the town is small. Call:
- Yevgeny, good afternoon, this is Sergeant Ivanov, a department of the Federal Service for Investigation of Information Crimes. Do you have an illegal use of official position, when you can come to us to testify?
The guy did not appear in the university about a week, and he crushed his hard disk and RAM into a crumb.
')
Surely everyone who reads these lines wondered how and how to chop up your hard drive if they came to it (the effect of an elusive Joe). Someone left it in the form of a mental plan, and someone got their hands on weapons by technical means (for example, hard, the disk was previously pulled out of the system unit, and a nearby Bulgarian).
Protection against unauthorized access is not only software, but also hardcore. There are all sorts of situations, and protecting information comes at the cost of her life. “So do not you get to anyone!” Or “Ultima ratio regum” (the last argument of the kings).
Today - a report from the laboratory for the rapid destruction of information. (Thanks to the information security expert Oleg Pozdnyakov from Detector Systems for the right to access.)

Gilfoyle is a schoolboy compared to how critical information is protected in Russia.
I already wrote about how to smudge the magnetic field of the HDD ( hard drive killers. Coercive headshot ). But the SSD has more armor. SSD is tenacious. This is where SSD fed petabytes , he did not choke, but you can feed him himself to a shredder, as they do in Europe and America. Our engineers came up with a more elegant solution. But not at once. At first there was agile agile, several iterations of testing destruction technologies. Before coming to the ideal option of destroying an SSD, there were flames and explosions.
When the saws are knocking on the door, there is no time to hammer in everything with zeros or to unscrew the disk from the body and to push it in the microwave. Although the drill on the desktop will help. The main thing that was always with a charged battery, because the
Several photos and video and test options for destroyers, as well as standards for the protection of information from unauthorized access.
Theory
Guidance document "Protection against unauthorized access to information." Terms and definitions .
American national standard DoD 5220.22-M
It is based on one of the oldest algorithms for guaranteed destruction of information. DoD 5220.22-M was adopted in 1995 for use in the US Army. By the way, it was from here that the abbreviation DoD - the Department of Defense (Ministry of Defense) - took the title of the standard.
The DoD 5220.22-M standard involves making three recording passes on top of the deleted information and one verification cycle. In the first of them, randomly selected characters are stored in each byte of each sector. The second pass is recording the inverted data. That is, units are written instead of all zeros and vice versa. And finally, the third cycle is another entry of a random sequence of characters.
This approach is a good defense against people who do not have special tools. Nevertheless, in many cases, its application will not be enough. This is recognized by the US Army, whose headquarters prohibits the use of DoD 5220.22-M to delete information with the “Top Secret” stamp.
pcsupport.about.com/od/termsd/g/dod-5220-22-M.htm
The DoD 5220.22-M standard involves making three recording passes on top of the deleted information and one verification cycle. In the first of them, randomly selected characters are stored in each byte of each sector. The second pass is recording the inverted data. That is, units are written instead of all zeros and vice versa. And finally, the third cycle is another entry of a random sequence of characters.
This approach is a good defense against people who do not have special tools. Nevertheless, in many cases, its application will not be enough. This is recognized by the US Army, whose headquarters prohibits the use of DoD 5220.22-M to delete information with the “Top Secret” stamp.
pcsupport.about.com/od/termsd/g/dod-5220-22-M.htm
German national standard VSITR
This standard was developed in 1999 by the organization Bundesamt fuer Sicherheit in der Information-stechnik, performing in Germany many of the duties of our former FAPSI. Compared to the US DoD 5220.22-M, it is more reliable. This is achieved through the implementation of seven recording cycles over the destroyed information. True, there is no originality in it. The first cycle is the recording of all logical zeros (0x00), the second - ones (0xFF). The next four passes repeat the first two. And on the seventh, the last “lap”, the value 0xAA is recorded.
Naturally, this algorithm of guaranteed destruction of information takes longer than the US DoD 5220.22-M. And although it is better in terms of reliability, it does not guarantee the absolute impossibility of data recovery.
Naturally, this algorithm of guaranteed destruction of information takes longer than the US DoD 5220.22-M. And although it is better in terms of reliability, it does not guarantee the absolute impossibility of data recovery.
Russian national standard GOST R50739-95
This standard, as its name implies, was developed in 1995. It is based on the “softest” algorithm, which, although it protects against data recovery using ordinary programs, provides absolutely no protection against special tools. The standard provides two options for data destruction. The first one is for computer systems from the 6th to the 4th grade of protection. It provides for writing logical zeros to each byte of each sector. The second option is used for computer systems from the 3rd to the 1st class of protection. In this case, randomly selected characters are written instead of zeros.
GOST P 50739-95 Computing facilities. Protection against unauthorized access to information. General technical requirements
GOST P 50739-95 Computing facilities. Protection against unauthorized access to information. General technical requirements
Hardware data destruction
According to the Pentagon, software does not guarantee absolutely reliable data deletion. Therefore, the position of NTSC-TG-025 determines that when deleting information from the Secret or Topsecret category, it is necessary to use powerful devices for demagnetization and heating of the hard disk to a temperature of more than 700 ° C.
NSA
NSA / CSS Storage Device Declassification Manual (NSA / CSS SDDM)
But doing so in Europe:

Russia, 2016
Laboratory for the destruction of information. SSD shredder test samples.Hotter
The first hypothesis is to burn.

It was hypothesized that instead of an oven and microwave, which “warms up” in a few minutes, the termite will cope in a few seconds. We made several test samples, even showed at the exhibition.

Self-igniting SSD drives. Click, and the termite inside fuses everything into glass. But not everything was so simple in practice.

"Drops of molten silicon." Termite burning temperature - 1300 degrees.

Two glasses of termite, please. With myself.

Term-stuffed drive.

Tests of termites.
At the site:
We dig into what remains:
The termite version was rejected due to the risk of uncontrollable effects of accidental operation - too much noise-light-sound effects. As well as the risk of damage to nearby equipment.
Solid flame
There were also ideas to use a solid flame , and there were also connections with the SHS laboratory ( self-propagating high-temperature synthesis ).
Here's what it looks like. Handsomely.
Although if you make the basis of the boards of such a material or housing for drives. But so far it has remained at the level of the idea.
A little louder
DISCLAIMER. For the explosions, they used the usual New Year's petard, which is sold in any fireworks store.

Tested on a conventional flash drive, tightly screwed into caprolon.



Experts found the damage to the chip insufficient . Plus the risk of unauthorized tripping, for example, on an airplane.
Sun into the outlet (outdated technology)
Marketers came up with the idea of how to push the unreliable equipment to other people. Here, they say, let's connect 220 volts directly, and we will burn everything in a second. But no. Burn the wiring, and the chip remains intact. Yet the market still come across such solutions. (Again “Peal”?)
They tried this solution in the laboratory, tested it and found it completely unreliable.

But since electricity is the most affordable, quiet and odorless, we decided to use it, but with a qualitatively different method. Thus was born the most optimal solution at the moment - Impulse-SSD .
Lightning chain

Here is a demonstration of the work of the Impuls-SSD Killer , voltage is 20,000 volts.
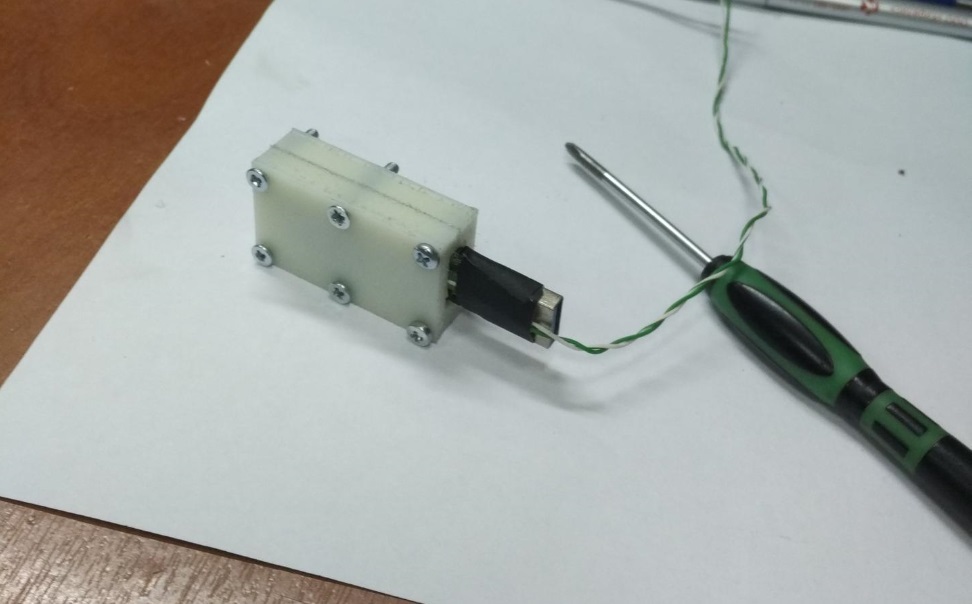
The device is designed for emergency erasure of information from a solid-state single board SSD carrier of 2.5 ”form factor.

Appearance - the usual five-inch slot, with a hole for a standard SSD drive.
The final task of the device is to produce an unrecoverable and complete erasure of the information recorded on the NAND-flash SSD chip in the shortest time possible.
The performance of the disk after erasing is irretrievably lost and the disk must be replaced.
When the device is activated (erasing data), a specific electric field is generated in the device's chamber, which leads to the destruction of the structure of the NAND-flash memory chips.
Erase time up to 2 seconds.
A side effect is the allowable partial cracking of the microcircuit cases.
An ordinary SSD should be stripped from the aluminum case so that it does not shield our lightning.
The SSD drive is placed in the device's camera, connected to the server (disk controller) using an interface cable - extension cable. The interface of the disk does not matter. At the same time, speed and functionality of the disks are fully preserved. Before being placed in the device, the external case should be removed from the disk, that is, the disk board itself should be placed in the device without a protective casing. This operation may be performed by medium-level IT personnel familiar with the instruction.

Knitting "red buttons" to destroy information.
Peripherals allow remote (including wireless) control of the device, organization of perimeter protection of the computer case, premises.
Local device activation - wired buttons up to 300m.
Remote activation - a radio channel (range 40, 1000m), a GSM controller with the additional possibility of receiving feedback on the activation and status of the device.

Blocks radio channel short and medium range.
Perimeter protection - mechanical, reed sensors, security control - contactless keys.
I wasn’t allowed to climb inside the device, only “motors” showed.

Such simple motors provide sweep across the entire area of the SSD drive.
Protection from the fool and cleaners
When all hard drives can be destroyed at the touch of a button, it’s worth thinking “fool-proof” protection. Our engineers have proposed a solution - a kind of “pressure pattern” (such as the cunning knock on the door: pam-pababampamp-pam-pam). But once the "fool" managed to circumvent the protection from himself and he decided to fight with a colleague. There was an activation of the destruction of disks. At first they wanted to blame the spontaneous operation of the device, but there are logs. When the logs were raised, there was an obvious triggering of the radio launch and our hero confessed to bypass the defenses.
Conclusion
“We are increasingly turning to the company for destruction systems on solid-state media. SSD media, apparently becoming cheaper, more often used in the assembly of workstations and servers. I am an expert in the information security market for 5 (10 years), during which time I have rechecked several dozen variants of destroyers and boldly declare that Ipulse-SSD provides the maximum destruction of carriers from all existing options. It does not use sub solders, pyrotechnics and other, to put it mildly, charlatan ways to destroy information. ”
- Oleg Pozdnyakov
“Never trust a computer that you cannot throw out the window.”
- Steve Wozniak
When all measures to ensure the protection of the perimeter failed, the last argument of the kings remains. It is important that it works guaranteed (especially in situations with power cuts and radio broadcast jamming) and precisely when ordered (and not arbitrarily). It follows from this that it is worth checking the reliability of the destruction system several times in the “training alert” mode and not to trust the “marketing assurances”.
PS
Again I want to remind you about “Genius”:
Pps
Somehow it happened that my classmate was forgotten to say that he was pinned over him. He learned only a year later. But this year he lived as a saint, he even passed his tests on time.
Source: https://habr.com/ru/post/306520/
All Articles