Safety of railways from open sources

Introduction
Good day, dear reader. Surely there were situations when you were somewhere out of the house outside the city limits. One of the possible means of transportation is a train, and sometimes it turns out that you can get to your destination with the help of it as quickly as possible than by plane.
At the very beginning I want to make some important clarifications. The potential attack vectors, which will be considered in Section 4, are determined only on the basis of information from open sources. In addition, this article considers the situation as a whole on the railways of different countries of the world without being tied to a specific country. However, in particular, we clarified some data on the attack vectors proposed in the article by our Russian colleagues from the Russian Railways Cybersecurity Center: work is underway to eliminate possible attack vectors, and for some problems partially eliminated. It is also worth noting that the author is not able to give a full technical opinion on the safety of high-speed trains due to the lack of access to the system and the possibility of conducting full-fledged practical experiments on the railway.
')
This article will provide an overview of some of the safety systems that can be used on modern high-speed trains. The number of such platforms is growing, they are becoming increasingly difficult. At the same time, they are based on well-known technologies, including Ethernet, CAN, RS-485. Increasingly, various PLC and industrial computers running Windows / Linux / QNX OS are being used. In addition, the popularity of systems using a radio channel is growing (as an example, GPS / GLONASS, GSM-R, Wi-FI).
In this regard, the question arises - is it safe to create a huge system based on “modules” that are well known to potential intruders?
As an example - potential vulnerabilities in GSM-R. Of course, someone will argue that GSM and GSM-R are different technologies. However, the main difference between the two is that the GSM coverage area is a “circular” area, in the center of which is the base station. The GSM-R standard, in turn, is adapted for railways in such a way that the coverage area extends along the railroad. Another thing is more important: all vulnerabilities present in GSM are also inherent in GSM-R, and this technology is actively used to control the movement of high-speed trains.
The GPS signal can be muted. And it is not so difficult. If you go into the thicket of the forest, it is very likely that the GPS receiver will lose satellites, and you will not even have to do anything. Now imagine a situation where the attacker not only jamming the signal, but also replaces the data so that the receiving party receives completely different coordinates. And the location of the train is only used to calculate the moving blocks.
In modern trains can not do without Wi-Fi. This, of course, is very convenient for passengers, but let's not forget that the IEEE 802.11 standard (in other words, Wi-Fi) is well known to attackers. Next we will talk about the fact that currently Wi-Fi / Ethernet is beginning to dominate when building a TCN. Thus, under the right circumstances, a situation may arise when an attacker, having connected to the Wi-Fi in the car, gets access to other nodes on the MVB / WTB bus. And in some cases, these nodes have very good production capacity. Interpretation of the mentioned abbreviations will be given in section 1.1.
Another one of the possible attack vectors is attacks on computers, to which various mobile diagnostic equipment is connected, “observing” the operation of all parts of the rolling stock. And because it seems not a very good idea after each trip to send the train for diagnosis due to incorrect operation of mobile equipment.
In conclusion, I would like to remind you of the introductory part that we should not forget about a possible scenario when the equipment is infected with malware in various ways.
1. General information about modern high-speed trains
This section will describe what technologies are used on modern high-speed trains.
Unfortunately, the author does not have the opportunity to purchase or at least rent for a while to study and search for weak points a full-fledged train. To dive into the safety world of high-speed trains, we will use only open sources and our personal experience in this field. In principle, a potential attacker may be in similar (or even privileged) conditions.
Before the advent of distributed automation systems, satellite systems, logistics was carried out "manually": before sending the train, the dispatcher called the next station and found out whether the haul was free, whether the previous train had passed.

And on the trains of that time there were not many systems interacting with each other, the driver and the dispatcher.
Since then, enough time has passed, much has changed. Let's see how modern railway infrastructure looks today.
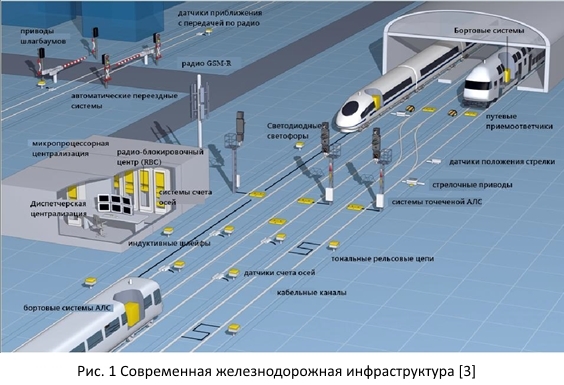
Figure 1 shows the interconnection of various systems. Conventionally, this "diversity" can be divided into several categories:
- Dispatching automation;
- Railway automatics (onboard);
- Railway automation (track).
It should be noted that often onboard and track railway automation is a single software and hardware complex, part of which is located on the train, and the other part - on the railway tracks. Of course, this division is very conditional. In addition, we will be more interested in modern high-speed trains.
1.1. Applicable standards
Let's make a small digression to say a few words about the standards that are applied on the railway.
In 1999, the international standard IEC 61375 was adopted, which is based on the TCN - Train Communication Network. At the time of adoption, TCN consisted of two tires:
- MVB - M ultifunctional V ehicle B us - the on-board network of a rolling stock unit (this could be a wagon, a locomotive);
- WTB - W ire T rain B us is a train network that integrates MVB parts into a single train management system.
In 2014, a new standard was adopted, IEC 61375-2-5, which is intended to replace WTB with ETB - E thernet T rain B ackbone.
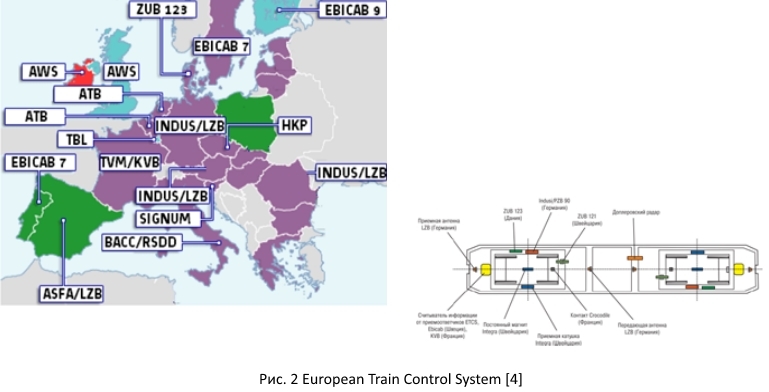
A few words about the prerequisites for creating the ETCS - European Train Control System. In Europe, the railway is popular. But each country has its own standards for railway safety; In addition, there are structural differences in the placement of various sensors that provide similar logical functions. For a painless transition to a new single standard, several levels have been developed.
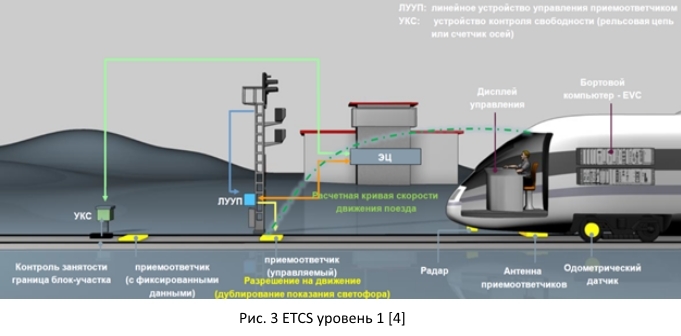
1.1.1. First level ETCS
ETCS first level. At this stage there is no use of a radio channel for running a train. Various systems for monitoring the block occupancy (track circuit or axle counter) are used. The reference points with fixed information or variable information are used to determine the location of the train, the duplication of traffic lights.
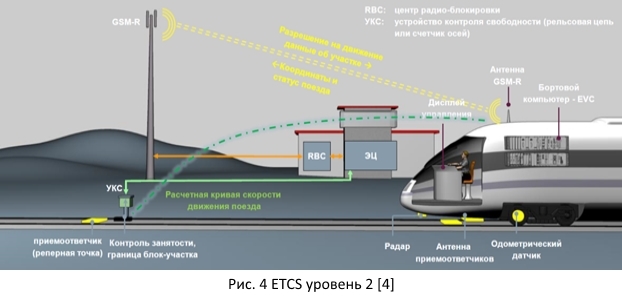
1.1.2. Second level ETCS
ETCS second level. The use of a radio channel for transmitting the coordinates and status of the train, permission to move, data on the upcoming block section. The data are duplicated by the track automation, in particular, on the basis of devices for controlling the workload of the tracks.
1.1.3. Third level ETCS
ETCS level three. The train is fully maintained by radio. Transition from fixed block sections to dynamic. Thus, the distance between trains can be reduced to the necessary and safe, optimal for braking the train.
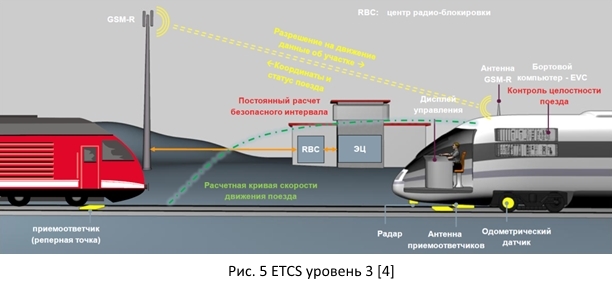
1.2. Modern railway infrastructure
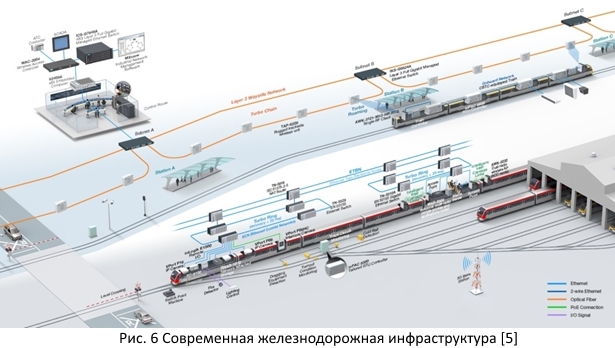
Now consider the modern railway infrastructure. As you can see, a huge number of different technologies will be used to collect and exchange information not only within the train, but also between the train, track automation, railway station and other elements.
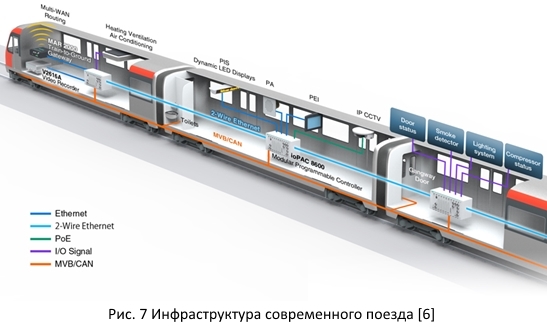
Take a close look at the modern train. This vehicle today is the focus of various subsystems that are responsible both for the safety of the train on the stretch and for providing comfort to passengers.
1.2.1. WTB tire
Within the car, the MVB-bus is laid, and the train is combined into a single WTB-bus. Let us consider in more detail the key functionality of the WTB bus.
The main task is to provide a single information channel between various units of rolling stock.
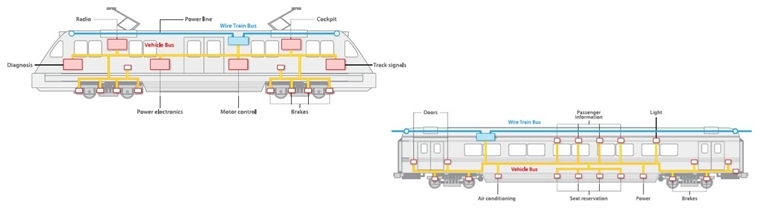
For this, real-time protocols are used. In addition, WTB provides PDM - P rocess Data Distribution, LFLD - Network Management, Network Management, Conformity arrangements. English terms are provided intentionally to avoid distortion.
Main limitations:
- the need for complete redirection of devices (when the car is attached or uncoupled);
- a certain number of cars in the composition (no more than 22).
1.2.2. MVB tire
In turn, the MVB-bus provides the interaction between various sensors, actuators and PLC. The master-slave architecture is used. Moreover, it is allowed to use several “master” devices in the network.
The format of communication is presented in Figure 8.
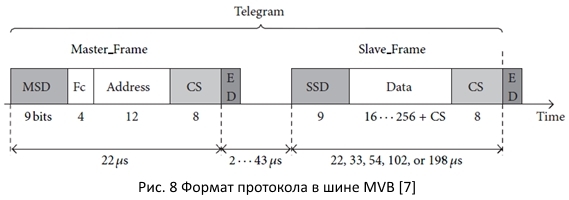
The master sends a request containing the device address and operation code; The slave device - if it receives a request from the master - responds.
1.2.3. Data transmission medium
The following data transmission media can be used to build the MVB / WTB infrastructure:
- ESD ( E lectrical S hort D istance). It provides communication at a distance of about 20 meters, it is often used to connect devices in a single package;
- EMD ( E lectrical M edium D istance). It is used to provide communication at distances of about 200 meters, up to 32 devices can be connected;
- OGF ( O ptical G lass F ibre) - distance of about 2000 meters. The main application is where high noise immunity is required (on locomotives, for example).
1.2.4. Applied equipment
Now I would like to say a few words about the classes of MVB-devices. The simplest can be attributed to the 1st class. Basically, they are designed to connect to sensors and actuators. Higher-end devices have a CPU, they can already be configured and programmed. If you look at the technical description of the presented devices [8], [15], [16], [17], you will see that Intel Atom N450, XScale IX435, ARM 9, Intel Core i7 and similar processors can be used there. The amount of RAM from 512 MB to several GB. Work under known OS (including Windows, Linux, QNX). For some devices it is possible to develop programs in programming languages such as “C” or “Perl”.

Modern train infrastructure involves the use of various multimedia devices (including smartphones or tablets), with which it is possible to connect to the train’s internal network and receive information about departure time, weather forecast and other data relevant to travelers.
2. Modern train infrastructure
Now consider in more detail the possible scheme that can be used on modern trains, as well as various automation systems that are used to ensure the safety and comfort of passengers.
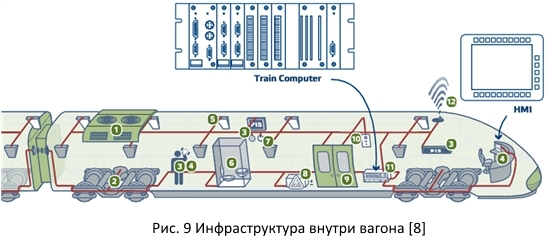
This figure shows one of the real solutions for building an MVB bus offered by the developer. As you can see, a huge number of different devices are connected to the bus, including the HVAC system (1), the functionality for monitoring various parameters of the wheeled cart (2), there are various external communications (12). All this is controlled by the on-board computer (11).
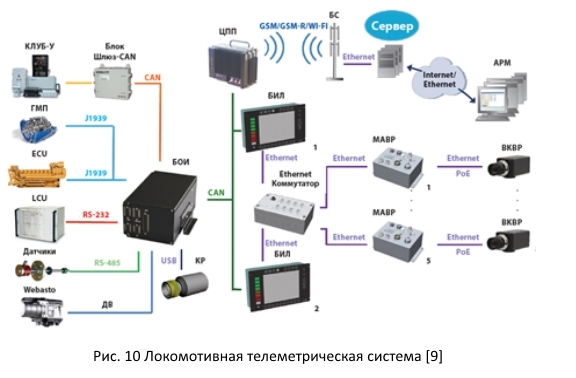
2.1. Locomotive telemetry system
Consider some of the platforms, the description of which was found in open sources. One of them is the Locomotive Telemetric System. As you can see in the diagram, when building this system, widely used protocols are used, including CAN, Ethernet, RS-232, RS-485. Industrial Ethernet switches can be used.
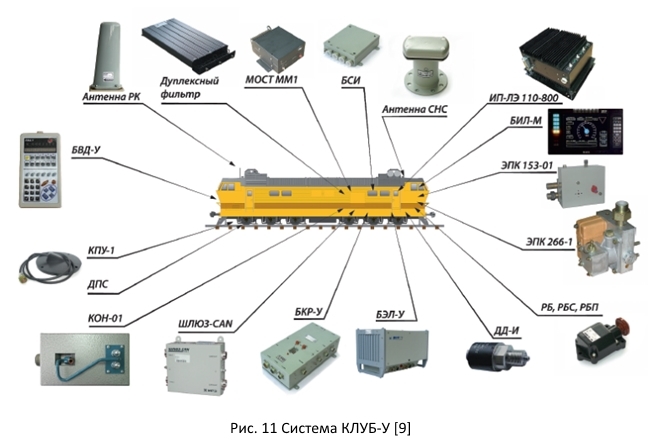
2.1.1. System "CLUB-U"
One of the platforms responsible for safety on the route is the CLUB-U system, consisting of various devices. The main functions performed by this system [18]: elimination of unauthorized movement of the locomotive; comparing the actual speed with the allowable one (if the allowable speed is exceeded, the “Attention” signal is turned on and the voltage is removed from the electromagnet EPK) control of braking before a prohibitive signal of the traffic light; generation of signals for the automatic control system of the ACS brakes; control of the driver's vigilance; registration of motion parameters.
2.1.2. System "ALS"
"ALS" - Automatic Locomotive Alarm. The system includes floor transmitting devices, receiving and deciphering devices on rolling stock, as well as devices that coordinate the work of the ALS with other alarm and blocking components, indicators, sensors and actuators on rolling stock [19]. Included in the CLUB-U system.
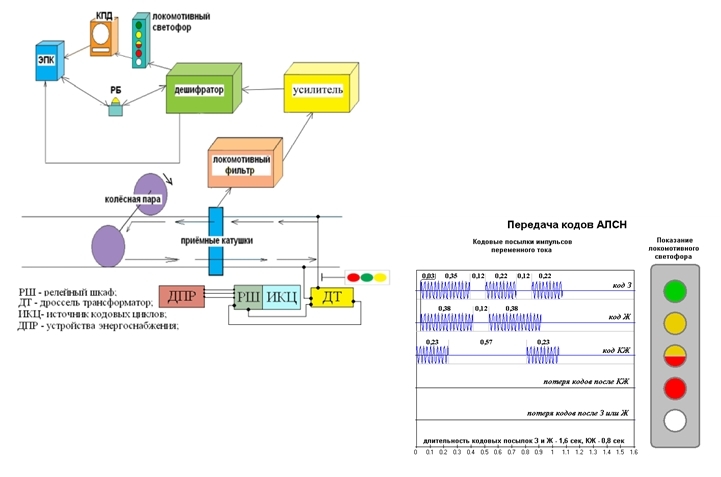
The principle of operation is as follows: track automation via a rail circuit transmits a signal at a certain frequency about a traffic light signal. The equipment located on the locomotive receives the signal from the track circuit, decodes it and then transmits it to the locomotive traffic light, to the driver’s vigilance control system and another auxiliary option.
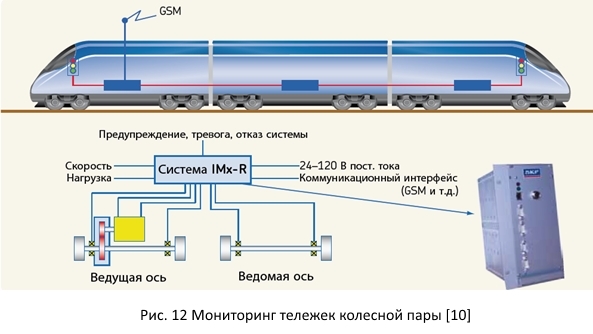
2.2. System "Monitoring trolleys wheelset"
In addition to determining the free block sections before the train, it is necessary to carry out self-diagnostics and train monitoring. In particular, the system should monitor the condition of wheelsets. It is responsible for measuring speed, vibration and other parameters of wheelsets, and, in the event of a deviation from the norm, it generates messages, which may result in a referral to diagnostic services after arriving at the end station.
2.3. Passenger accounting system
Electronic tickets and electronic check-in for a train - this can surprise few people. But high-speed trains in their arsenal certainly have a system of accounting and analysis of passenger traffic.
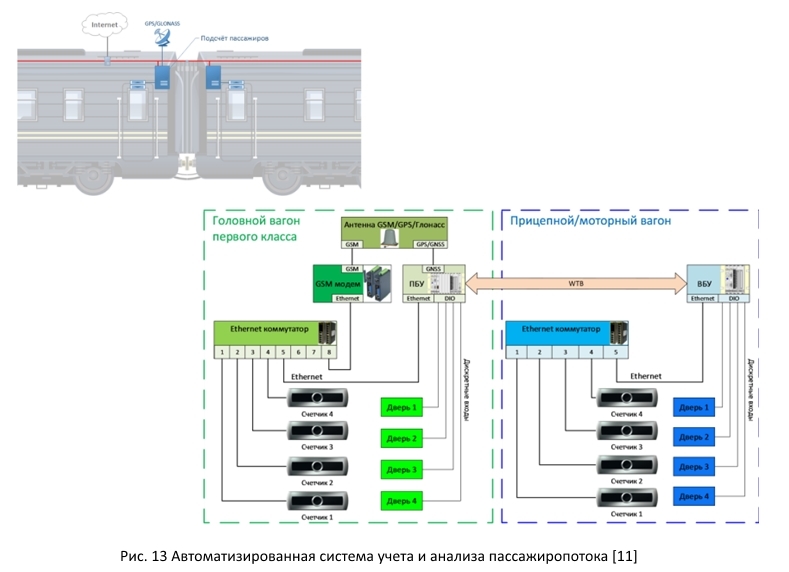
As can be seen in Figure 13, Ethernet switches are used to implement this scheme. In addition, the counters are located next to the door, where an attacker can access them and connect to an Ethernet network.
2.4. Interval motion control system
To increase the carrying capacity of the hauls, a transition is carried out from the fixed block sections to the moving block sections.
Movement along fixed block-sections implies the passage of a train to the next block-section only if it is completely free. In turn, the moving block sections reduce the distance between the trains to the minimum distance that is necessary to safely stop the train going behind.
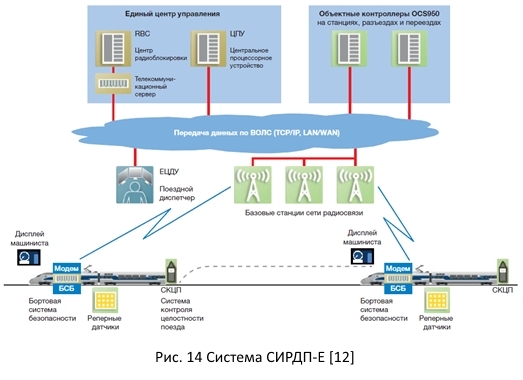
Movable block sections can be implemented on the basis of an interval control system based on a radio channel. This solution allows to increase the carrying capacity of the haul, but it also requires strengthening security measures to avoid train collisions and other emergencies.
2.5. Diagnostic equipment
Do not forget about the various diagnostic systems, some of which are presented in the mobile version.

This equipment can be operated as part of test equipment (CPS) of complex locomotive safety devices CLUB-U. It can simulate the activation signals of the locomotive control devices, the signals of the speed sensors, the system of the telemetry driver’s vigilance monitoring system, the ALS signals.
3. High-speed train "Sapsan"
Above was a small list of various systems that can be used on trains. In particular, in Russia there is only one high-speed train, the Sapsan, built on the basis of the German ICE. (Intercity-Express) [20]
In Figure 16, you can see the functional diagram of the Sapsan train control system. And, as already mentioned, it consists of MVB modules, which are combined into a WTB train bus.
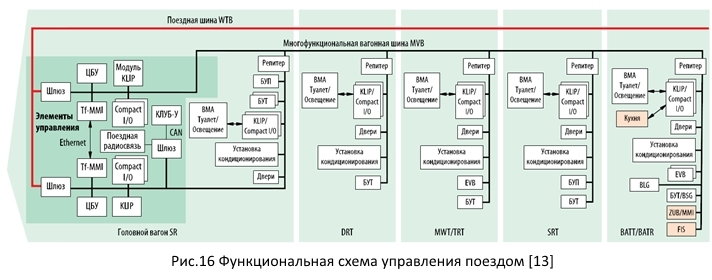
The train system is based on SIBAS 32.
The SIBAS system itself was developed for rail transport in 1983 by the German company Siemens. In 1992, SIBAS16 was upgraded to SIBAS32, which is currently used in such trains as the Sapsan and Lastochka.
In 2008, the system was upgraded to SIBAS PN, and it is expected that the first train running this system will be launched in 2016. The main difference between the SIBAS 32 and SIBAS PN is that the SIBAS32 was based on the Intel 386/486 CPU using the closed OS SIBAS OS, while the SIBAS PN is based on the Power PC and the Intel Atom CPU. Simatic Step 7 is used as the development environment.
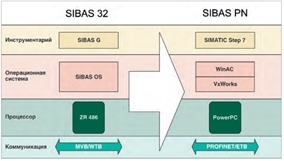
The main properties of SIBAS PN are modularity, compliance with industry standards, automatic addressing, software independence from the hardware platform, and the possibility of registering and monitoring via the WEB interface.
Also, there is independence from the hardware platform, which is achieved through the use of hard real-time OS VxWorks and WinAC. I want to immediately emphasize that VxWorks has a number of known vulnerabilities, and up to version 6 uses a single address space. As practice shows, many modern devices use old versions of this operating system, which can negatively affect information security.
4. Possible attack vectors
Having considered the "stuffing" of the modern train, it is time to talk about possible attack vectors.
4.1. Impact on radio signals (GSM-R, GPS)
So, what we have in the "arsenal". As it was said above, GSM-R is used for running the train and transmitting telemetry. Through this communication channel, data about the coordinates of the train, its speed are transmitted, receiving information related to the movable block sections. Now imagine a situation in which the train receives information that the next few hauls are free, but in fact, the train "catches the next turn" ahead of the train, as In the control room there is incorrect data on the location of the leading train. Such an attack scenario cannot be called “fantastic” due to the fact that there are no fundamental differences between GSM and GSM-R. As already mentioned, the main difference between these two standards is the coverage area. For GSM, it is represented as a circular area in the center of which the base station is located; for GSM-R, it extends along the railway. In addition, according to [4] the requirements that are put forward to GSM-R when building ETCS, double overlapping of each segment should be ensured, and, in the event of a radio communication failure, the train should switch to protection mode up to emergency braking.
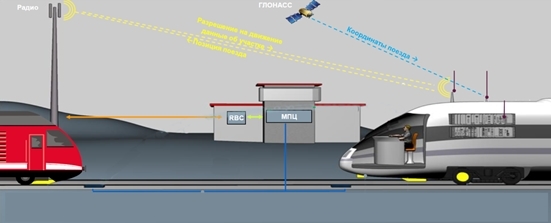
We have already described a situation in which a train collision may occur due to the fact that the control tower receives incorrect data on the location of the train. One way to find out current coordinates is to use GPS. But this technology has some drawbacks. First, the signal itself is rather weak: go to a dense thicket of the forest or move away from the window, and your device will “lose” the satellites with high probability. Another, more important point is that the signal itself can be changed, as a result of which the on-board automation of the train can calculate that it is in a different place. In fairness it should be noted that to determine the location of the train is used not only GPS / GLONASS.
4.2. Impact on track automation
Another possible attack vector can be a different effect on track automation, interacting with the train. As an example, it is potentially possible to connect to the ALS “track system” and gain access to making changes to the code pulses.
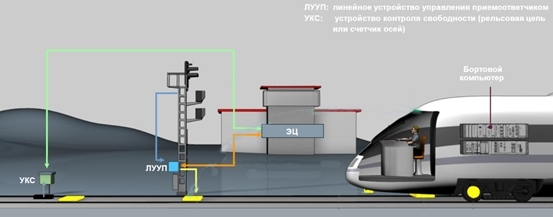
As a result, a signal will be generated prohibiting passage to the next block section. This can lead to a false stop of the rolling stock. The railroad is not a freeway, where, if one lane is occupied, everything is calm, slowly moving into the next lane. On railways, the schedule of trains is quite tight, especially in busy areas, and an unforeseen train stop can create a “transport” collapse. In some European countries, up to 100% of the ticket price is refunded if the train is more than 5 minutes late. [14]
4.3. Connecting to an Ethernet / Wi-Fi network
Since modern trains use technologies such as Ethernet and / or Wi-Fi, which are very familiar to attackers, one should not exclude the option of connecting to Ethernet or Wi-Fi and the possibility of reconfiguring various nodes based on the unsafe SNMP v1 protocol. In addition, let's not forget that the attacker has a direct opportunity to connect to the train infrastructure if the passenger traffic analysis system is used and thus potentially gain access to any network device.
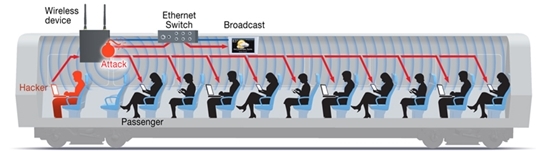
To reduce the risk of such attacks - it is necessary at least to carry out network segmentation. As mentioned earlier, some nodes are characterized by high productive capacity. In addition, as already noted, the transition from the "zoo systems" to some unified and "unified" systems based on the x86 / ARM architecture using known operating systems (Linux / Windows / QNX), which, in turn, have vulnerabilities. Unfortunately, the latest equipment and patches covering the vulnerabilities found are not always applied to industrial equipment in operation.
4.4. Impact on train automation systems through diagnostic equipment
Another scenario could be the situation when an attack occurs on a computer that interacts with various diagnostic equipment that later connects to automation systems installed on the train.
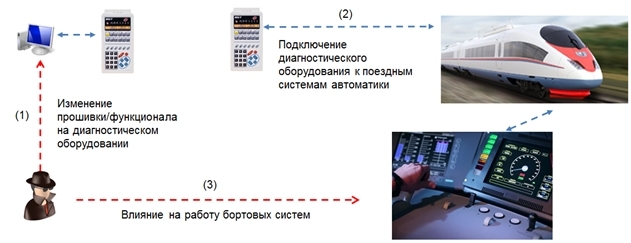
As practice shows, there are no absolutely isolated systems. We see examples in abundance in the adjacent field - the sphere of various objects of the industrial control system, where there are always ways to "connect from the outside." Thus, it can be assumed that computers, to which various diagnostic equipment is connected, can also be accessed from outside. As a result, a possible infection of the computer with the subsequent change in the configuration of the mobile diagnostic equipment. It is not difficult to guess what the effect will be on the work of the onboard systems of the train.
4.5. Modification of firmware on hardware
Do not forget about the possibility of modifying the firmware along the path of the equipment from the manufacturer to the final customer.
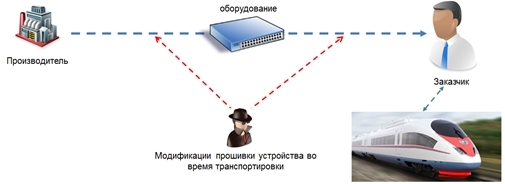
Often, in addition to remote methods of configuring and configuring equipment through special software, the hardware can be directly accessed by connecting via RS-232. Further, the malefactor will take possession of rather ample opportunities for configuring the equipment. Up until the firmware update. As practice shows, there is often no control over the authenticity of firmware equipment. This may result in the attacker replacing the firmware at the lowest level. As a result, according to the behavior, it will not be possible to distinguish good equipment from the infected until the “critical” data packet is received.
Unfortunately, the problem of the integrity and authenticity of the firmware of various equipment is typical for many vendors from different areas.
5. Conclusion
As a conclusion, we summarize the main conclusions reached by us in the course of analyzing the security situation of high-speed trains based on open sources. Thus, the well-known technologies begin to dominate when building a TCN, including Ethernet, Profinet. You can watch the transition from closed architectures to x86-like architecture. There is a transition from proprietary OS to widely known OS. There is an increase in the amount of information transmitted between the train and other systems and the growth of automation systems responsible for the safety and comfort of passengers.
It should be noted that many of the technologies that are used in the modern high-speed train, individually, are already well studied and “broken”. The train is an aggregation of such technologies into a single whole, therefore, to implement various kinds of attacks, attackers will have to “break” several systems at once, taking into account the specifics of the railway. And the question of the safety of high-speed trains remains open.
Bibliography
Here is a small list of open sources from which information was gleaned:
[1] Rail transport
[2] High speed ground transportation
[3] Railway automation "Components and systems of railway automation of the company" Siemens "for railways" space 1520 "
[4] “High-speed rail traffic” A series of lectures by the president of Siemens on Dietrich Möller’s Russia
[5] The Only Full-Range IRIS-Certified Product Portfolio for Railway Communication
[6] Change Rolling Stock
[7] Mo Xia, Kueiming Lo, Shuangjia Shao, and Mian Sun “Formal Modeling and Verification for MVB”
[8] EKE “Technology for smarter trains”
[9] IRZ-Locomotive, Product Catalog 2014
[10] SKF Solutions for High-Speed rail transport.
[11] Automated system for accounting and analysis of passenger traffic
[12] Bombardier, “Products and solutions for railway transport”
[13] Technical features of the high-speed train Velaro Rus
[14] Renfe Memoria social
[15] IGW series Multiple Type Bus Gateway family
[16] Duagon, i101 A8 Based CPU Module
[17] Siemens, On-Board Products and Systems
[18]Description of equipment for integrated locomotive safety devices
[19] Automatic locomotive signaling
[20] German Railways
Source: https://habr.com/ru/post/306182/
All Articles