Is cybercriminal Carbanak group linked to a Russian security company?
Brian Krebs wrote in his blog a voluminous material that shows an interesting look at who and how is associated with the Carbanak group, which sensationally broke into about 100 financial institutions and stole about 1 billion US dollars.
Below is a translation of this article (please write notes in private messages).
The most famous cybercrime group is the Carbanak group. These hackers from Eastern Europe are accused of stealing more than a billion dollars from banks. Today we will look at some compelling evidence pointing to the connection between Carbanak and a Russian security firm claiming to work with some of the biggest cyber security brands.
')
The Carbanak group gets its name from malicious banking software used in countless cyber thefts. This group is perhaps best known for penetrating banking networks using infected Microsoft Office files, then using this access to dispense cash in ATMs. According to estimates by Kaspersky Lab, Carbanak is likely to have stolen more than $ 1 billion, but mainly from Russian banks.
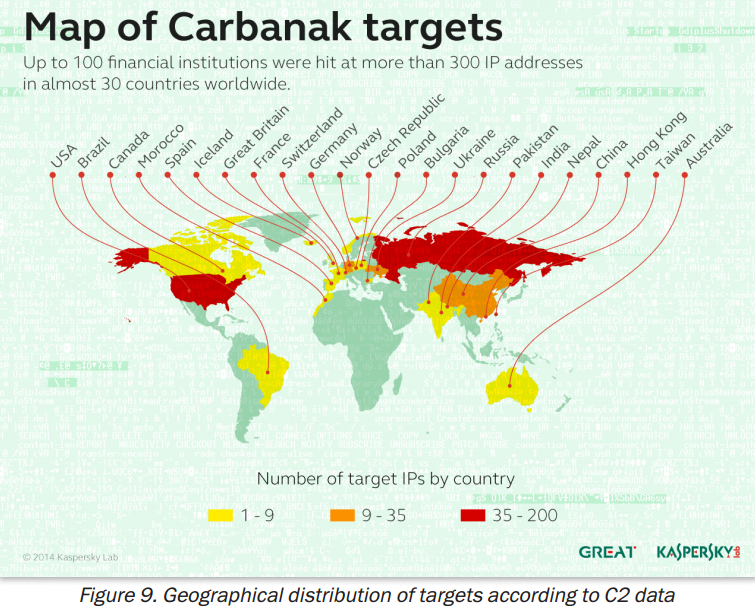
I recently heard from information security researcher Ron Guilmette that he found some interesting similarities in the registration records of websites that were previously responsible for distributing malware used by the Carbanak group.
For example, the weekend-service [dot] com, coral-trevel [dot] com and freemsk-dns [dot] com domains are fixed by several security companies as centers for the distribution of fraudulent Carbanak software. The WHOIS history records for all three domains contain the same telephone and fax number, which is owned by Xicheng Co. in China - 1066569215 and 1066549216, each of which begins with +86 (telephone code of China) or +01 (USA). Each entry also includes the same e-mail: “williamdanielsen@yahoo.com”.
According to ThreatConnect, at least 484 domains have been registered at williamdanielsen@yahoo.com or to one of the 26 email addresses that are associated with the same phone numbers and the Chinese company. "At least 304 of these domains were associated with a malicious plugin that was previously assigned to Carbanak activities," says ThreatConnect.
Let's return to these two phone numbers, 1066569215 and 1066549216. At first glance, they seem to be consistent, but after a closer look it can be seen that they differ slightly in the middle. Among the very few domains registered with these Chinese numbers that were not seen in the launch of malicious programs, there is a website called “cubehost [dot] biz”, which was registered in September 2013 for 28-year-old Artem Tveritinov from the city Perm, Russia.
Cubehost [dot] biz is now inactive site, but it seems that it belongs to the Russian company Infocube. The InfoCube site - infokube.ru - is also registered to Artem Tveritinov. There are dozens of records in the history of WHOIS for infokube.ru, but only the oldest, original record of 2011 contains an email address atveritinov@gmail.com
The same e-mail address was used to register the profile of Artem Tveritinov from Perm on VKontakte .
Mr. Tveritinov is listed as “Chief Executive Officer of InfoKub” in a press release from the Moscow security organization FalconGaze, a company that was partnered with InfoKube in implementing “data protection and personnel monitoring” at a Russian commercial research institute.
By the way, Falcongaze yesterday announced the presence of its technology to intercept Telegram messages, to which Pavel Durov replied that their program is a trojan .
InfoKube's own press releases say that the company is also engaged in developing a “system for protecting information from unauthorized access” for Perm and the Perm Territory, and also participates in a number of consulting projects related to “information security” conducted jointly with the Russian Ministry of Internal Affairs.
The company's website claims that InfoKube collaborates with various security companies, including Symantec and Kaspersky. The latter confirms that InfoKube was a “very insignificant partner” of Kaspersky Lab and mainly participated in the integration of systems. Zyxel reports that he had no partners called InfoKube. According to ESET, “Infokube is not and has never been a partner of ESET in Russia.”
In connection with the findings of Guilmette, I really wanted to ask Mr. Tveritinov how the telephone and fax numbers for the Chinese facility, whose phone number became synonymous with cybercrime, were exactly copied to the WHOIS of Cubehost. I sent inquiries to Mr Tveritinov via e-mail and through his VKontakte page.
I initially received a friendly e-mail reply expressing curiosity about my request, as well as a question about how I discovered his e-mail. In the midst of compiling a more detailed question, I noticed that the VKontakte profile, which Tveritinov regularly maintained from April 2012, is now permanently deleted. The profile page of Artyom and his photos actually disappeared from the screen on my monitor while I was in the process of writing a letter to him on the other.
Shortly after the Tveritinov’s VKontakte page was deleted, I received an e-mail from him. Ignoring my question about the sudden disappearance of a social profile, Tveritinov said that he did not register at cubehost.biz and that his personal information was stolen and used in registration records for cubehost.biz.
“Our company has never done anything illegal, and it carries out all activities in accordance with the legislation of the Russian Federation,” he said via e-mail. - "In addition, it is rather stupid to use our personal data for the registration of domains that will be used for crimes, since [we] are experts in the field of information security."
It turns out that InfoKube / Cubehost also uses a large number of IP addresses managed by St. Petersburg Internet Network LLC (“PIN”), an Internet service provider in St. Petersburg.
For example, many of the aforementioned domain names that cybersecurity firms associate with the spread of Carbanak (for example, freemsk-dns [dot] .com) are posted on Cubehost's Internet addresses. A search of registration records for block 146.185.239.0/24 identifies the physical address in the region of Ras al Khaimah, United Arab Emirates. This region seeks to create a reputation as a tax haven and a place where you can easily create completely anonymous offshore companies. The same RIPE list says that complaints about Internet addresses in this block should be sent to “info@cubehost.biz”.
This PIN hosting provider in St. Petersburg, PIN, has reached a high degree of ill fame and is probably worthy of additional study, considering its reputation as a refuge for all kinds of online scoundrels.
In fact, Doug Madory, director of Internet analysis at Dyn , called the company St. Petersburg Internet Network LLC as “... perhaps the leading applicant for the title“ Mos Eisley Internet ”(referring to a cosmodrome full of alien criminals, in the movie "Star Wars" in 1977).
Madory explains that St. Petersburg Internet Network’s very bad reputation comes from the provider’s predisposition to hide huge pieces of Internet address blocks that don’t actually belong to him, and then this stolen address space is rented to spammers and other Internet attackers.
For its part, Guilmette points to the ten-year significance of another despicable activity that takes place in the Internet address space, apparently belonging to Tveritinov and his company. For example, in 2013, Microsoft seized many domains that were parked there, which were used as control nodes for Citadel malware against online banking, and all of these domains had the same “Xicheng Co.” data in their WHOIS records. In September 2011, the dynamoo.com security blog report marks several domains with this Xicheng Co. WHOIS information that indicates the use of the Sinowal Trojan in online banking thefts was discovered back in 2006.
“If Mr. Tveritinov knew or was directly involved even in a small part of the criminal events within his address space, then the probability that he may also play a role in other additional criminal companies ... including, perhaps, even in cyberbank robberies of Carbanak ... becoming more believable and likely, ”says Guilmette.
It remains unclear to what extent the Carbanak group is still active. Last month, Russian authorities detained 50 people allegedly linked to an organized cybercrime group, whose members hail from Russia, China, Ukraine, and other parts of Europe. The action was announced as the largest retention of financial hackers in Russia.
Let me remind you that this is a translation of the article. Remarks please write in private messages.
Below is a translation of this article (please write notes in private messages).
The most famous cybercrime group is the Carbanak group. These hackers from Eastern Europe are accused of stealing more than a billion dollars from banks. Today we will look at some compelling evidence pointing to the connection between Carbanak and a Russian security firm claiming to work with some of the biggest cyber security brands.
')
The Carbanak group gets its name from malicious banking software used in countless cyber thefts. This group is perhaps best known for penetrating banking networks using infected Microsoft Office files, then using this access to dispense cash in ATMs. According to estimates by Kaspersky Lab, Carbanak is likely to have stolen more than $ 1 billion, but mainly from Russian banks.

I recently heard from information security researcher Ron Guilmette that he found some interesting similarities in the registration records of websites that were previously responsible for distributing malware used by the Carbanak group.
For example, the weekend-service [dot] com, coral-trevel [dot] com and freemsk-dns [dot] com domains are fixed by several security companies as centers for the distribution of fraudulent Carbanak software. The WHOIS history records for all three domains contain the same telephone and fax number, which is owned by Xicheng Co. in China - 1066569215 and 1066549216, each of which begins with +86 (telephone code of China) or +01 (USA). Each entry also includes the same e-mail: “williamdanielsen@yahoo.com”.
According to ThreatConnect, at least 484 domains have been registered at williamdanielsen@yahoo.com or to one of the 26 email addresses that are associated with the same phone numbers and the Chinese company. "At least 304 of these domains were associated with a malicious plugin that was previously assigned to Carbanak activities," says ThreatConnect.
Let's return to these two phone numbers, 1066569215 and 1066549216. At first glance, they seem to be consistent, but after a closer look it can be seen that they differ slightly in the middle. Among the very few domains registered with these Chinese numbers that were not seen in the launch of malicious programs, there is a website called “cubehost [dot] biz”, which was registered in September 2013 for 28-year-old Artem Tveritinov from the city Perm, Russia.
Cubehost [dot] biz is now inactive site, but it seems that it belongs to the Russian company Infocube. The InfoCube site - infokube.ru - is also registered to Artem Tveritinov. There are dozens of records in the history of WHOIS for infokube.ru, but only the oldest, original record of 2011 contains an email address atveritinov@gmail.com
The same e-mail address was used to register the profile of Artem Tveritinov from Perm on VKontakte .
Mr. Tveritinov is listed as “Chief Executive Officer of InfoKub” in a press release from the Moscow security organization FalconGaze, a company that was partnered with InfoKube in implementing “data protection and personnel monitoring” at a Russian commercial research institute.
By the way, Falcongaze yesterday announced the presence of its technology to intercept Telegram messages, to which Pavel Durov replied that their program is a trojan .
InfoKube's own press releases say that the company is also engaged in developing a “system for protecting information from unauthorized access” for Perm and the Perm Territory, and also participates in a number of consulting projects related to “information security” conducted jointly with the Russian Ministry of Internal Affairs.
The company's website claims that InfoKube collaborates with various security companies, including Symantec and Kaspersky. The latter confirms that InfoKube was a “very insignificant partner” of Kaspersky Lab and mainly participated in the integration of systems. Zyxel reports that he had no partners called InfoKube. According to ESET, “Infokube is not and has never been a partner of ESET in Russia.”
In connection with the findings of Guilmette, I really wanted to ask Mr. Tveritinov how the telephone and fax numbers for the Chinese facility, whose phone number became synonymous with cybercrime, were exactly copied to the WHOIS of Cubehost. I sent inquiries to Mr Tveritinov via e-mail and through his VKontakte page.
I initially received a friendly e-mail reply expressing curiosity about my request, as well as a question about how I discovered his e-mail. In the midst of compiling a more detailed question, I noticed that the VKontakte profile, which Tveritinov regularly maintained from April 2012, is now permanently deleted. The profile page of Artyom and his photos actually disappeared from the screen on my monitor while I was in the process of writing a letter to him on the other.
Shortly after the Tveritinov’s VKontakte page was deleted, I received an e-mail from him. Ignoring my question about the sudden disappearance of a social profile, Tveritinov said that he did not register at cubehost.biz and that his personal information was stolen and used in registration records for cubehost.biz.
“Our company has never done anything illegal, and it carries out all activities in accordance with the legislation of the Russian Federation,” he said via e-mail. - "In addition, it is rather stupid to use our personal data for the registration of domains that will be used for crimes, since [we] are experts in the field of information security."
It turns out that InfoKube / Cubehost also uses a large number of IP addresses managed by St. Petersburg Internet Network LLC (“PIN”), an Internet service provider in St. Petersburg.
For example, many of the aforementioned domain names that cybersecurity firms associate with the spread of Carbanak (for example, freemsk-dns [dot] .com) are posted on Cubehost's Internet addresses. A search of registration records for block 146.185.239.0/24 identifies the physical address in the region of Ras al Khaimah, United Arab Emirates. This region seeks to create a reputation as a tax haven and a place where you can easily create completely anonymous offshore companies. The same RIPE list says that complaints about Internet addresses in this block should be sent to “info@cubehost.biz”.
This PIN hosting provider in St. Petersburg, PIN, has reached a high degree of ill fame and is probably worthy of additional study, considering its reputation as a refuge for all kinds of online scoundrels.
In fact, Doug Madory, director of Internet analysis at Dyn , called the company St. Petersburg Internet Network LLC as “... perhaps the leading applicant for the title“ Mos Eisley Internet ”(referring to a cosmodrome full of alien criminals, in the movie "Star Wars" in 1977).
Madory explains that St. Petersburg Internet Network’s very bad reputation comes from the provider’s predisposition to hide huge pieces of Internet address blocks that don’t actually belong to him, and then this stolen address space is rented to spammers and other Internet attackers.
For its part, Guilmette points to the ten-year significance of another despicable activity that takes place in the Internet address space, apparently belonging to Tveritinov and his company. For example, in 2013, Microsoft seized many domains that were parked there, which were used as control nodes for Citadel malware against online banking, and all of these domains had the same “Xicheng Co.” data in their WHOIS records. In September 2011, the dynamoo.com security blog report marks several domains with this Xicheng Co. WHOIS information that indicates the use of the Sinowal Trojan in online banking thefts was discovered back in 2006.
“If Mr. Tveritinov knew or was directly involved even in a small part of the criminal events within his address space, then the probability that he may also play a role in other additional criminal companies ... including, perhaps, even in cyberbank robberies of Carbanak ... becoming more believable and likely, ”says Guilmette.
It remains unclear to what extent the Carbanak group is still active. Last month, Russian authorities detained 50 people allegedly linked to an organized cybercrime group, whose members hail from Russia, China, Ukraine, and other parts of Europe. The action was announced as the largest retention of financial hackers in Russia.
Let me remind you that this is a translation of the article. Remarks please write in private messages.
Source: https://habr.com/ru/post/305998/
All Articles