How do FortiASIC processors work?
As a world leader in high-performance information security solutions, in terms of performance, Fortinet relies on the FortiOS operating system in conjunction with FortiASIC , which is a specialized chipset, processors accelerating content analysis and processing network traffic of its own design. In this article, the work of these processors will be described in detail. We will explain how they speed up packet processing / analysis.
')
FortiASIC
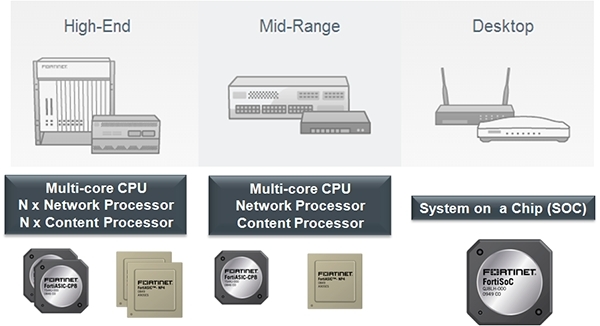
Most FortiGate models have FortiASIC (Application Specific Integrated Circuit) hardware acceleration to handle traffic and reduce latency, which offloads the main processor (CPU).
- Network processors (NPs) - for processing network traffic
- Content processors (CPs) - for security features
- System-on-a-Chip Processor (SOC2) - for joint operation of security features and traffic processing
For performance, Fortinet divides its FortiGate line into three categories:
- Entry Level (Desktop)
- Mid-Range
- High-End
In each of the categories, different CPUs and FortiASICs are used, as well as a different number of them.
Network processors
NP network processors operate at the interface level to speed up traffic by offloading traffic from the main processor. Current models contain NP4 and NP6. Older FortiGate models include NP1 (also known as FortiAccel or FA2) and NP2.
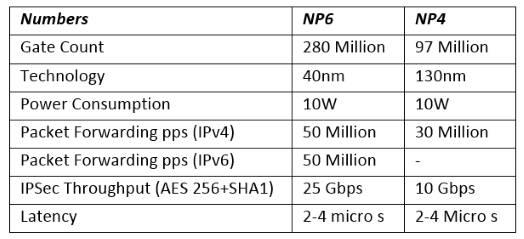
At the moment, NP6 processors are the latest development and can offload the following traffic and services:
- IPv4 and IPv6 traffic, NAT64 and NAT46 traffic
- Link aggregation (LAG) (IEEE 802.3ad) traffic
- TCP, UDP, ICMP and SCTP
- IPsec VPN traffic, as well as IPsec encryption / decryption (including SHA2-256 and SHA 2-512)
- Unencrypted IPsec traffic
- IPS based on anomalies, checksum offload and packet fragmentation
- SIT and IPv6 Tuning session
- Multicast traffic (including Multicast inside IPsec)
- CAPWAP traffic
- Shaping traffic and queuing by priority
- Syn proxying
- Traffic passing through the Inter-VDOM link
- IPS
- Application Control
- CASI
- Flow-based antivirus
- Flow-based web filtering
NP does not support downloading modified content at the application level, which means that sessions are not unloaded if the following security features are enabled in the policy:
- proxy-based virus scanning
- proxy-based web filtering
- DNS filtering
- DLP
- Anti-Spam
- VoIP
- ICAP
- Web Application Firewall
- Proxy options
Content processors
CP content processors operate at the system level with tasks defined by the CPU. New FortiGate models (2000E, 2500E, 6040E) contain CP9. The older versions are CP4, CP5, CP6, and the current FortiGate models use the CP8.
CP8 can unload the following tasks:
- Flow-based inspection IPS, Application Control, Cloud Access Security Inspection (CASI), Web Filtering, DLP, and Antivirus
- High performance VPN bulk data engine
- IPsec and SSL / TLS protocol processor
- DES / 3DES / AES in accordance with FIPS46-3 / FIPS81 / FIPS197
- ARC4 in compliance with RC4
- MD5 / SHA-1 / SHA256 with RFC1321 and FIPS180
- HMAC in accordance with RFC2104 / 2403/2404 and FIPS198
- Key Exchange Processor support high performance IKE and RSA computation
- Public key exponentiation engine with hardware CRT support
- Primarily checking for RSA key generation
- Handshake accelerator with automatic key material generation
- Random Number generator compliance with ANSI X9.31
- Sub public key engine (PKCE) to support up to 4096 bit operation directly
- Message authentication module offers high performance cryptographic engine for calculating SHA256 / SHA1 / MD5 data bytes (used by many applications)
- PCI express Gen 2 four lanes interface
- Cascade Interface for chip expansion
System-on-a-Chip Processor
SOC processors are used in the lower Entry Level category (Desktop). The purpose of the SoC-architecture is to combine several processors in a single chip, simplifying the overall hardware design. SOC combines CP, NP, RISC-based CPU processors.
Currently, SOC version 2 is relevant, which offloads the traffic described in the NP and CP section.
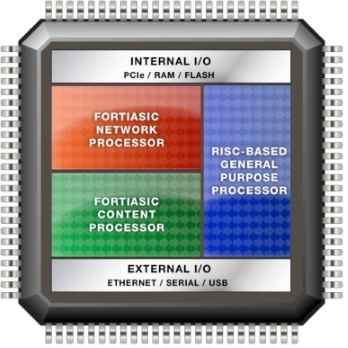
SOC Architecture
Offloading
The process of unloading the session occurs in several stages. The first batch of each new session always goes to the CPU. If the NP supports the requested security features that must be performed, the CPU sends out instructions to the NP that it can handle this session. All subsequent packets for the “fast path” session are redirected to NP. Finally, after the last TCP packet, “FIN” (finish) or “RST” (reset) NP returns the session to the CPU to close the session. Otherwise, if the NP does not support the requested security functions that are required to be processed, all packets in this session should work out the CPU.

Package Path in Session Unloading

The path of the first packet in the unloaded session

Path of subsequent packets in an unloaded session
FortiGate High-End models with two or more NP6s are physically connected together through an Integrated Switch Fabric (ISF), which allows communication between all interfaces and NP6 processors, bypassing the central processor. Thus, traffic is unloaded, even if the input and output port belongs to more than one NP processor.
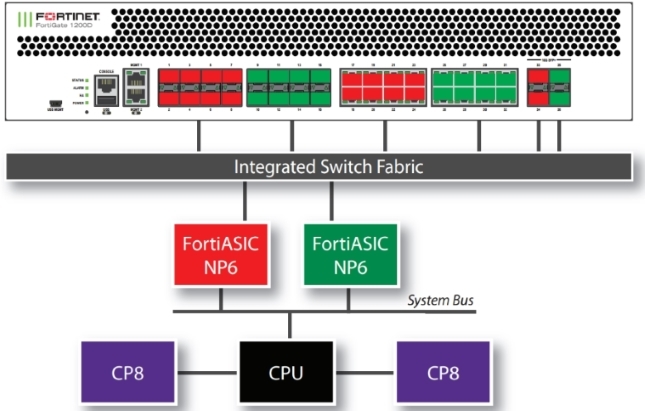
Integrated switch fabric
NTurbo-acceleration
The NTurbo acceleration functionality allows you to offload UTM / NGFW sessions that pass through the NP processor.
Thanks to NTurbo, a special “data channel” is created to redirect traffic from NP to IPS and back. Unloading Steps:
1.NP accepts the packet and performs the required actions;
1.1If the packet is encrypted, the packet is transmitted to the CP by the processor;
1.2Decoding with CP;
1.3CP transmits NP data to the processor;
2. For flow-based UTM / NGFW inspections, NP creates a data transmission channel with an IPS engine (worked out on the CPU) and transmits data to it;
3.IPS-engine transfers the data inspection task to the CP for its acceleration;
4.CP returns the IPS data to the engine;
5.IPS-engine returns NP data to the processor;
6.If the data has been decrypted, it is transmitted to the CP for encryption;
7. Produce encryption using CP;
8.CP transfers NP data to the processor;
9.NP processor transmits a packet of CPU.
NTurbo support NP4 and NP6.
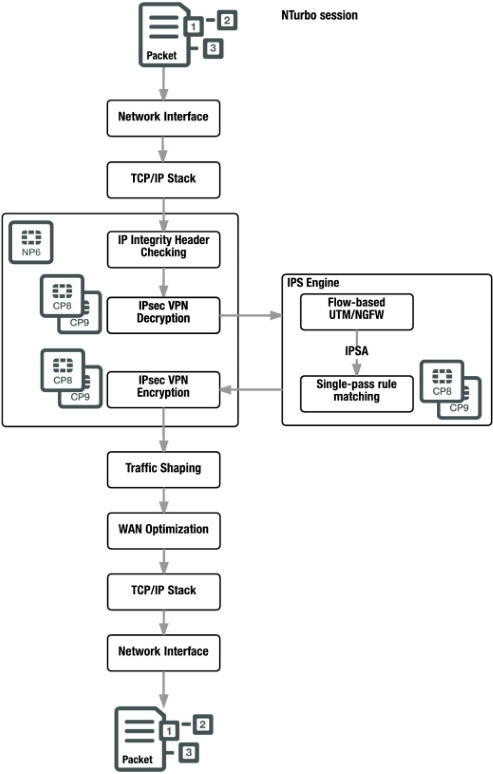
NTurbo session with IPSA offload
IPSA acceleration
IPSA technology offloads “pattern matching” extensions for flow-based UTM / NGFW checks, the technology is available in NTurbo and standard firewall sessions. IPSA support CP7, CP8 and CP9.
IPsec Encryption / Decryption
If the IPsec tunnel uses encryption and hashing algorithms supported by the NP network processor, then IPsec user data processing can be unloaded to improve performance. In this case, the NP will only decrypt the traffic, and the CP will encrypt.

IPsec Encryption / Decryption
Accelerated Flow-based and Proxy-based Inspection with CP
Flow-based UTM / NGFW Inspection identifies and blocks real-time security threats by sampling packets in a session using a single-pass architecture that includes Direct Filter Approach (DFA) pattern matching to identify possible attacks or threats.
Before testing, the IPS engine can be applied using a series of decoders to determine the appropriate security modules that will be used depending on the packet protocol and policy settings. In addition, SSL packets will also be decrypted. SSL decryptions are unloaded and accelerated by the CP8 or CP9 processors.
The use of security modules (IPS, Application Control, CASI, flow-based Web Filtering, flow-based DLP filtering) occurs simultaneously in a single approach and is accelerated by the CP8 and CP9 processors. CASI signatures are applied in the Application Control portion of the check. Flow-based Antivirus caches files during protocol decoding, and then scans them. If it was an SSL packet, at the end of the check it is encrypted and, accordingly, the CP8 and CP9 processors speed up the process.
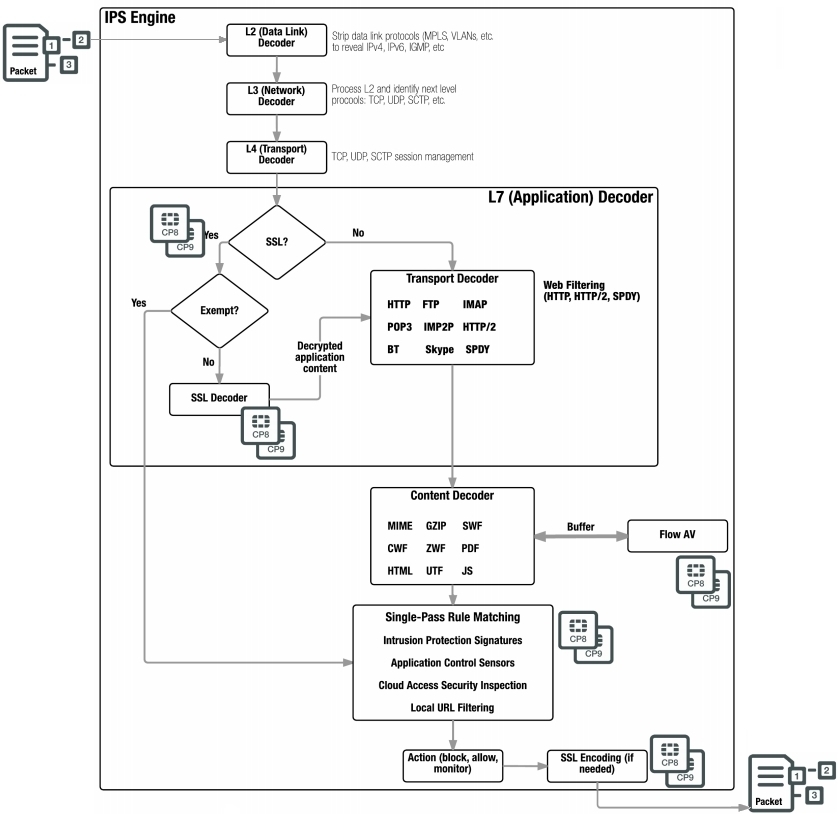
Stages of flow-based inspection
Proxy-based UTM / NGFW inspection retrieves and caches files for further verification.
Initially, packets get into the IPS engine and pass flow-based inspection with security functions that work only in this mode (single-pass IPS, Application Control and CASI) and, accordingly, traffic is accelerated using CP8 and CP9. After that, the packets go to the FortiOS Proxy-server to check the security function in proxy-based mode. First, the proxy detects the SSL traffic. SSL packets will be decrypted using CP8 or CP9 and sent back to the IPS engine to re-examine the flow-based security functions (single-pass IPS, Application Control and CASI) of the decrypted traffic. Then the traffic goes to the Proxy-server, where proxy-based security features are used. The inspection takes place in the following order:
• VoIP inspection
• DLP
• AntiSpam
• Web Filtering
• Antivirus
• ICAP
After checking the decryption, the SSL traffic is encrypted. If no threat is found, the proxy server sends the file to its destination. If the threat is found, the proxy server can block the file and in response send a message about the reason for blocking.

Proxy-based inspection steps

')
FortiASIC
Most FortiGate models have FortiASIC (Application Specific Integrated Circuit) hardware acceleration to handle traffic and reduce latency, which offloads the main processor (CPU).
- Network processors (NPs) - for processing network traffic
- Content processors (CPs) - for security features
- System-on-a-Chip Processor (SOC2) - for joint operation of security features and traffic processing
For performance, Fortinet divides its FortiGate line into three categories:
- Entry Level (Desktop)
- Mid-Range
- High-End
In each of the categories, different CPUs and FortiASICs are used, as well as a different number of them.
Network processors
NP network processors operate at the interface level to speed up traffic by offloading traffic from the main processor. Current models contain NP4 and NP6. Older FortiGate models include NP1 (also known as FortiAccel or FA2) and NP2.

At the moment, NP6 processors are the latest development and can offload the following traffic and services:
- IPv4 and IPv6 traffic, NAT64 and NAT46 traffic
- Link aggregation (LAG) (IEEE 802.3ad) traffic
- TCP, UDP, ICMP and SCTP
- IPsec VPN traffic, as well as IPsec encryption / decryption (including SHA2-256 and SHA 2-512)
- Unencrypted IPsec traffic
- IPS based on anomalies, checksum offload and packet fragmentation
- SIT and IPv6 Tuning session
- Multicast traffic (including Multicast inside IPsec)
- CAPWAP traffic
- Shaping traffic and queuing by priority
- Syn proxying
- Traffic passing through the Inter-VDOM link
- IPS
- Application Control
- CASI
- Flow-based antivirus
- Flow-based web filtering
NP does not support downloading modified content at the application level, which means that sessions are not unloaded if the following security features are enabled in the policy:
- proxy-based virus scanning
- proxy-based web filtering
- DNS filtering
- DLP
- Anti-Spam
- VoIP
- ICAP
- Web Application Firewall
- Proxy options
Content processors
CP content processors operate at the system level with tasks defined by the CPU. New FortiGate models (2000E, 2500E, 6040E) contain CP9. The older versions are CP4, CP5, CP6, and the current FortiGate models use the CP8.
CP8 can unload the following tasks:
- Flow-based inspection IPS, Application Control, Cloud Access Security Inspection (CASI), Web Filtering, DLP, and Antivirus
- High performance VPN bulk data engine
- IPsec and SSL / TLS protocol processor
- DES / 3DES / AES in accordance with FIPS46-3 / FIPS81 / FIPS197
- ARC4 in compliance with RC4
- MD5 / SHA-1 / SHA256 with RFC1321 and FIPS180
- HMAC in accordance with RFC2104 / 2403/2404 and FIPS198
- Key Exchange Processor support high performance IKE and RSA computation
- Public key exponentiation engine with hardware CRT support
- Primarily checking for RSA key generation
- Handshake accelerator with automatic key material generation
- Random Number generator compliance with ANSI X9.31
- Sub public key engine (PKCE) to support up to 4096 bit operation directly
- Message authentication module offers high performance cryptographic engine for calculating SHA256 / SHA1 / MD5 data bytes (used by many applications)
- PCI express Gen 2 four lanes interface
- Cascade Interface for chip expansion
System-on-a-Chip Processor
SOC processors are used in the lower Entry Level category (Desktop). The purpose of the SoC-architecture is to combine several processors in a single chip, simplifying the overall hardware design. SOC combines CP, NP, RISC-based CPU processors.
Currently, SOC version 2 is relevant, which offloads the traffic described in the NP and CP section.

SOC Architecture
Offloading
The process of unloading the session occurs in several stages. The first batch of each new session always goes to the CPU. If the NP supports the requested security features that must be performed, the CPU sends out instructions to the NP that it can handle this session. All subsequent packets for the “fast path” session are redirected to NP. Finally, after the last TCP packet, “FIN” (finish) or “RST” (reset) NP returns the session to the CPU to close the session. Otherwise, if the NP does not support the requested security functions that are required to be processed, all packets in this session should work out the CPU.

Package Path in Session Unloading

The path of the first packet in the unloaded session

Path of subsequent packets in an unloaded session
FortiGate High-End models with two or more NP6s are physically connected together through an Integrated Switch Fabric (ISF), which allows communication between all interfaces and NP6 processors, bypassing the central processor. Thus, traffic is unloaded, even if the input and output port belongs to more than one NP processor.

Integrated switch fabric
NTurbo-acceleration
The NTurbo acceleration functionality allows you to offload UTM / NGFW sessions that pass through the NP processor.
Thanks to NTurbo, a special “data channel” is created to redirect traffic from NP to IPS and back. Unloading Steps:
1.NP accepts the packet and performs the required actions;
1.1If the packet is encrypted, the packet is transmitted to the CP by the processor;
1.2Decoding with CP;
1.3CP transmits NP data to the processor;
2. For flow-based UTM / NGFW inspections, NP creates a data transmission channel with an IPS engine (worked out on the CPU) and transmits data to it;
3.IPS-engine transfers the data inspection task to the CP for its acceleration;
4.CP returns the IPS data to the engine;
5.IPS-engine returns NP data to the processor;
6.If the data has been decrypted, it is transmitted to the CP for encryption;
7. Produce encryption using CP;
8.CP transfers NP data to the processor;
9.NP processor transmits a packet of CPU.
NTurbo support NP4 and NP6.

NTurbo session with IPSA offload
IPSA acceleration
IPSA technology offloads “pattern matching” extensions for flow-based UTM / NGFW checks, the technology is available in NTurbo and standard firewall sessions. IPSA support CP7, CP8 and CP9.
IPsec Encryption / Decryption
If the IPsec tunnel uses encryption and hashing algorithms supported by the NP network processor, then IPsec user data processing can be unloaded to improve performance. In this case, the NP will only decrypt the traffic, and the CP will encrypt.

IPsec Encryption / Decryption
Accelerated Flow-based and Proxy-based Inspection with CP
Flow-based UTM / NGFW Inspection identifies and blocks real-time security threats by sampling packets in a session using a single-pass architecture that includes Direct Filter Approach (DFA) pattern matching to identify possible attacks or threats.
Before testing, the IPS engine can be applied using a series of decoders to determine the appropriate security modules that will be used depending on the packet protocol and policy settings. In addition, SSL packets will also be decrypted. SSL decryptions are unloaded and accelerated by the CP8 or CP9 processors.
The use of security modules (IPS, Application Control, CASI, flow-based Web Filtering, flow-based DLP filtering) occurs simultaneously in a single approach and is accelerated by the CP8 and CP9 processors. CASI signatures are applied in the Application Control portion of the check. Flow-based Antivirus caches files during protocol decoding, and then scans them. If it was an SSL packet, at the end of the check it is encrypted and, accordingly, the CP8 and CP9 processors speed up the process.

Stages of flow-based inspection
Proxy-based UTM / NGFW inspection retrieves and caches files for further verification.
Initially, packets get into the IPS engine and pass flow-based inspection with security functions that work only in this mode (single-pass IPS, Application Control and CASI) and, accordingly, traffic is accelerated using CP8 and CP9. After that, the packets go to the FortiOS Proxy-server to check the security function in proxy-based mode. First, the proxy detects the SSL traffic. SSL packets will be decrypted using CP8 or CP9 and sent back to the IPS engine to re-examine the flow-based security functions (single-pass IPS, Application Control and CASI) of the decrypted traffic. Then the traffic goes to the Proxy-server, where proxy-based security features are used. The inspection takes place in the following order:
• VoIP inspection
• DLP
• AntiSpam
• Web Filtering
• Antivirus
• ICAP
After checking the decryption, the SSL traffic is encrypted. If no threat is found, the proxy server sends the file to its destination. If the threat is found, the proxy server can block the file and in response send a message about the reason for blocking.

Proxy-based inspection steps
Source: https://habr.com/ru/post/305954/
All Articles