Lenovo will fix a 0day ThinkPwn vulnerability in the firmware of its computers
Lenovo has expanded its security notice LEN-8324 on the ThinkPwn vulnerability with a list of the computers it affects, and also announced update dates for fixing it. We previously wrote about this 0day LPE vulnerability, which is present in one of the drivers for UEFI firmware of Lenovo computers, and also indicated that computers from other manufacturers, such as Dell and Hewlett Packard, are also vulnerable. The vulnerability allows a logged in attacker with administrator rights to execute an arbitrary SMM code in it, and also use this method to bypass the hardware protection from modifying the SPI-flash memory of the chip.

According to Lenovo, ThinkPwn is the least relevant for desktop and desktop all-in-one (monoblocks) series of computers, it is about IdeaCentre, Lenovo (B, D, E, G, H, M), Lenovo QITIAN, etc. On the other hand The most susceptible to ThinkPwn was the ThinkPad series of notebooks and some IdeaPad models. For some ThinkStation computers, the vulnerability is also relevant.
')
From Lenovo’s advisory, it can be seen that for many models, research on their vulnerability to ThinkPwn is still ongoing, especially with the ThinkServer server computer series. The vulnerability of almost all models of this series is still under study.
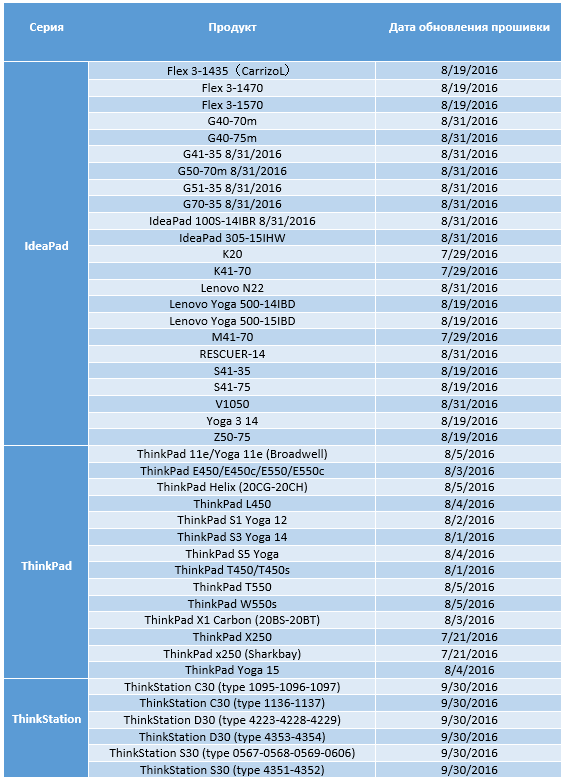
The table below shows the models of computers for which an update has already been announced.
Updates are also expected for the following computers (status pending):
We recommend that users update their computers immediately after the update.

be secure.

According to Lenovo, ThinkPwn is the least relevant for desktop and desktop all-in-one (monoblocks) series of computers, it is about IdeaCentre, Lenovo (B, D, E, G, H, M), Lenovo QITIAN, etc. On the other hand The most susceptible to ThinkPwn was the ThinkPad series of notebooks and some IdeaPad models. For some ThinkStation computers, the vulnerability is also relevant.
')
From Lenovo’s advisory, it can be seen that for many models, research on their vulnerability to ThinkPwn is still ongoing, especially with the ThinkServer server computer series. The vulnerability of almost all models of this series is still under study.
The table below shows the models of computers for which an update has already been announced.

Updates are also expected for the following computers (status pending):
- System x series: Flex System x240 M5, Flex System x280 X6, Flex System x480 X6, Flex System x880, Flex System x880 X6, NeXtScale nx360 M5, System x3500 M5, System x3550 M5, System x3650 M5, System x3850 X6, System x3950 X6.
- ThinkPad: ThinkPad 10 (Ella-2), ThinkPad 11e, ThinkPad 11e / Yoga 11e (20ED-20EE), ThinkPad E455 / E555, ThinkPad E465 / E565, ThinkPad Edge E145, ThinkPad Edge E440 / E540, ThinkPad Edge E445 / E545, ThinkPad Edge E455 / E555, ThinkPad Edge S430, ThinkPad Helix (3xxx), ThinkPad L430, ThinkPad L440 / L540, ThinkPad L530, ThinkPad S1 Yoga (20FS-20FT), ThinkPad S3-S440, ThinkPad S430, etc.
We recommend that users update their computers immediately after the update.

be secure.
Source: https://habr.com/ru/post/305844/
All Articles