Security Week 28: Pokémon Privacy, Critical Online Infrastructure, Post-Quantum Cryptography in Chrome
 How, and then Pokemon ?! And what to do: one of the main criteria for selecting meaningful security news for me is still their popularity at Threatpost. The method is not perfect, but fairly objective. If there is some strange garbage in the top, there is a reason to figure out how it happened, like for example it came out with the news about malicious code in PNG metadata in the 2014 top . As a rule, the explanation of such incidents is not in the technical features of the threat, but in how people perceive safety. And this is also interesting.
How, and then Pokemon ?! And what to do: one of the main criteria for selecting meaningful security news for me is still their popularity at Threatpost. The method is not perfect, but fairly objective. If there is some strange garbage in the top, there is a reason to figure out how it happened, like for example it came out with the news about malicious code in PNG metadata in the 2014 top . As a rule, the explanation of such incidents is not in the technical features of the threat, but in how people perceive safety. And this is also interesting.The news about malicious applications masquerading as Pokémon Go is generally 100% about perception
However, there were problems in the authentic application. Researcher Adam Reeve found that when registering an account in a game, users are required to give full access to their Google account. That is, the game developer, Niantic Labs, is able to read all mail correspondence, send letters on behalf of the player, can download all documents from Google Drive, watch search and navigation history, and much more. It is noteworthy that at the time of this discovery an alternative method of registration, not through Google, simply did not work.
All editions of the digest are available by tag .
However, it immediately became clear that access can be canceled, and this will not affect the performance of the game. But the user must do it himself. Obviously, the developers made a mistake, which they later admitted , promising to fix everything. Google also had to ruin the privacy ruins: they will have to cancel privileges for already registered users, as the vendor himself apparently cannot.
')
Not one pokemon was hurt. This whole story proves once again: for most users, to put it mildly, privacy matters are indifferent. Otherwise, the brilliant start of the first truly popular game with augmented reality would be thwarted. But no. And most importantly, it is useless to blame the players, if such blunders allow much more knowledgeable developers. Developing unsafe, behaving unsafe is easy. The converse is much more complicated. I think that this problem should be solved not at the level of legislation (as it was done, for example, in a rather stupid law about tracking cookies ), but at the level of technology. The need to work with people (training in safe development practices, methods of protecting privacy), however, does not cancel.
91% of online components available in industrial systems are vulnerable
News Research "Laboratories".
On the Internet you can find anything, just need to know where to look. Laboratories experts used tools available to everyone, such as the specialized Shodan search engine , to calculate the number of specialized ACS devices available from the network. Automated control systems are a very broad term, combining both individual solar controllers and control systems for large and critical facilities. They have one thing in common: shining controllers on the Internet is not the best idea, and in most cases (when this is not a honeypot, of course ) this is an indicator of an incorrect system configuration.
Having prepared a rather long list of criteria by which systems of automated control systems can be identified, experts found more than 220 thousand such devices on 188 thousand hosts. By country, they are divided as follows:

Further study of these devices showed that the absolute majority of them are subject to attacks to a varying degree. The most frequently encountered criterion is the dependence of devices on data transmission protocols unprotected by their nature. That is, if the system is controlled remotely, it is possible to intercept traffic with minimal effort. 6.3% of hosts detected systems with more serious vulnerabilities. Most of all, Sunny WebBox controllers (solar control) were found, which are known to contain tightly wired access passwords.
The main reason for such security failures is the security through obscurity approach common in industrial systems: when it is calculated that it is not known which controllers and protocols are used, access to them is limited, and the systems themselves are difficult to analyze even for those who own documentation . Actually, the study shows how bad this approach is.
First, the overwhelming majority of information in the study (the vulnerable hosts themselves, the types and characteristics of the vulnerabilities) are obtained from public sources: nothing prevents people with criminal intent from doing the same. Secondly, the use of unprotected communication protocols with the expectation of isolating devices from the Internet can go sideways. An error may occur in the configuration, and in a complex infrastructure one person may be responsible for setting up a critical segment, and another for network security, as a result, the problem crawls out somewhere at the junction of authorities. Thirdly, I will repeat my conclusion from the previous digest : between the “elite” ACS and the “civilian” Internet of things is not such a big difference at the level of hardware and software. The popularity of IoT and the associated increase in the number of attacks sooner or later can bring problems to very, very serious infrastructure facilities.
Google is testing post-quantum cryptography in Chrome
News
The news was sponsored by the US National Security Agency, which issued a communiqué (uii!) Last year, which expressed doubts about the long-term reliability of some encryption methods. I wrote more about this here in this series of digests . In short, progress in the field of quantum cryptography requires the introduction of new standards, for example, RSA with a key length of 3072 bits. That is, on the one hand, there is no progress in creating quantum computers capable of breaking modern robust cryptography, on the other hand, the NSA has doubts. Naturally, all this has generated a lot of controversy and conspiracy theories, and you can read about them in the same issue.
In short, Google seems to know something too. On July 7, they announced the beginning of an experiment with post-quantum cryptography in the Chrome browser. Specifically, in the developer version of the Chrome Canary browser , some users will turn on the encryption system for connecting to Google servers using the new algorithm. The system is built on the basis of scientific work on the implementation of the post-quantum algorithm in the TLS protocol. The algorithm is named symbolically: " New Hope ".
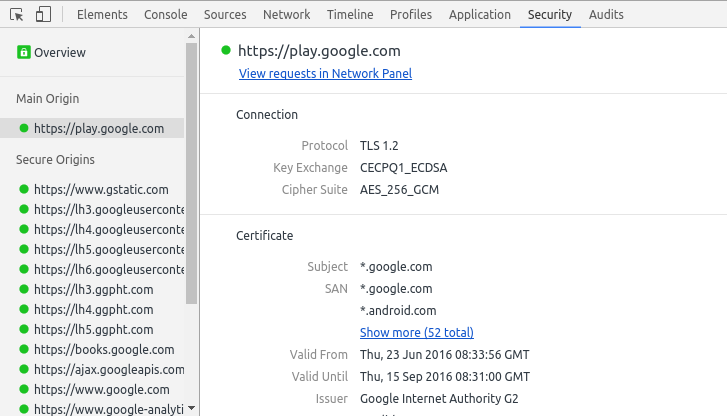
Developers write that the experiment has two goals. First, let the researchers
What else happened:
The original vulnerability in wget (although it would seem, how can you break wget?).
Discussion of the data encryption system in Android continues. A comprehensive assessment of the KeyStore system for storing cryptographic keys was added to the recent description of a specific attack method . General verdict: unreliable.
 Antiquities:
Antiquities:"Hallöchen"
Resident dangerous virus, typically infects .COM and .EXE files (for .COM files it changes the first 6 bytes of the beginning: JMP Loc_Virus; DB (?); DW 5555h). Depending on the “generation” of the virus, it periodically “jokes” with the keyboard: when processing a keyboard interrupt, it substitutes another symbol. Slows down the computer - the delay on int 8. Intercepts int 8, 16h, 21h. It contains the text: "Hallöchen !!!!!!, Here I'm Activate Level 1".
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 69.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/305754/
All Articles