Analysis of obfuscated virus detection by mobile antivirus applications on the Android platform

The UCBS team conducted an independent study in order to test the work of popular anti-virus applications for Android. I shared the results of this study at the phdays VI conference, but I would like to elaborate on the use of obfuscators to bypass the detection mechanisms of viruses.
Obfuscation methods
In the free access there are quite a lot of different obfuscators. Three free ones were chosen for use as part of the study, and another one was written as an addition, performing functions which, in our opinion, were not enough in previous ones.
First, two obfuscators working with the source code were selected - this is Proguard and Alatori.
ProGuard is embedded in the Android application build system - Android Studio and runs along with the application build in “release” mode. Officially, this utility is designed to reduce, optimize and obfuscation code.
ProGuard can rename the names of methods and some classes, and as a unique feature, you can highlight the fact that this obfuscator only removes all debug information (the names of files with the source code of the class and the line numbers in the code).
Similar to the considered Proguard, Alatori can rename the names of properties and methods, as well as some class names, and partially removes debugging information — changes the name of the file with the source code without deleting the line numbers. The main difference between Alatori is string encryption (xor algorithm with key 0x20).
Secondly, the obfuscator working with the byte code in the smali format - Adam was considered .
And since the apktool utility easily generates such a bytecode from an apk-file, then obam does not require the source code of this application.
Adam supports 4 methods of obfuscation, by the example of which one can visually examine how the code changes after obfuscation:
1) Adding an additional method to the code of each class.
| IT WAS | BECAME |
| Method Code1 Method Code2 | Method code 1 .method public SparkLog (Ljava / lang / String;) V const-string v0, "SparkLog" invoke-static {v0, p0}, Lcom / lohan / lohanLog; -> Log (Ljava / lang / String; Ljava / lang / String;) V .end method Method Code2 |
2) Changing the names of class methods
| IT WAS | BECAME |
| .method private capitalize (Ljava / lang / String;) Ljava / lang / String; | .method private capitalize abc123 (Ljava / lang / String;) Ljava / lang / String; |
3) Change the flow of execution.
At the beginning of the implementation of each method, a goto statement of unconditional jump to the end of the method is set. After there is an unconditional transition to the beginning, immediately following the transition instruction, where the normal execution of the code will continue.
| IT WAS | BECAME |
| .method private capitalize (Ljava / lang / String;) Ljava / lang / String; Method Code .end method | .method private capitalize (Ljava / lang / String;) Ljava / lang / String; goto: CFGGoto2 : CFGGoto1 Method Code : CFGGoto2 goto: CFGGoto1 .end method |
4) Encryption of lines of code.
All instructions for declaring string variables are replaced with instructions for declaring an encrypted string variable and calling a static method that decodes the string.
| IT WAS | BECAME |
| const-string v5, "http.protocol.content-charset" | const-string v5, " rddz.zbydymyv.myxdoxd-mrkbcod " invoke-static {v5}, Lcom / mzhengDS; -> DecryptString (Ljava / lang / String;) Ljava / lang / String; move-result-object v5 |
Testing antiviruses on obfuscated applications
To test obfuscated applications, it was decided to take one new Trojan (malware.apk application, which includes some dangerous potential) and one known dendroid (known because its signatures are determined by many antiviruses). In addition, testing was also carried out on a modified dendroid - cleaned of garbage in the source code, for example, from unused functions. By the way, even simply removing the garbage, and having reassembled the malicious application, some antiviruses have already ceased to react to it.
The scan results for virustotal are shown in Table 1.
Table 1 - scan results for virustotal
| Clean | Proguard | Alatori | ADAM | |
| Malware.apk | 26 | 17 | ten | 18 |
| Dendroid | 35 | 31 | 24 | 25 |
| Dendroid (modified) | 28 | 28 | 21 | 17 |
The scan results on top mobile anti-virus applications installed on the smartphone are shown in Table 2.
Table 2 - Mobile Antivirus Scan Results
| Clean | Proguard | Alatori | ADAM | |
| Malware.apk | 6 | four | four | 3 |
| Dendroid | 12 | eleven | 9 | eleven |
| Dendroid (modified) | ten | 9 | five | 9 |
In most cases, Alatory showed the best results, presumably due to the function of encrypting lines of code, in addition to scanning obfuscated Malware.apk with mobile antivirus software. In this situation, ADAM did the best job with the task, and Kaspersky, LookOut and AVAST became the three antiviruses that detected the virus.
Reducing the number of detections to three is nice, but we wanted to achieve zero recognition of the obfuscated application (which, by the way, was not possible).
Therefore, another obfuscator was developed, which is able to work with bytecode and combines the best aspects of obfuscators already considered. And due to the fact that he perfectly complemented ADAM with the ability to encrypt the names of packages and classes (using the xor algorithm in Alatori, but this time with a variable key), the obfuscator was called EVA.
Figure 1 shows a fragment of AndroidManifest.xml after obfuscation of EVA, in which all class and package names have been changed (encrypted). After the work of EVA, the obfuscated byte-code needs to be re-compiled with apktool back into the apk-file and re-signed.
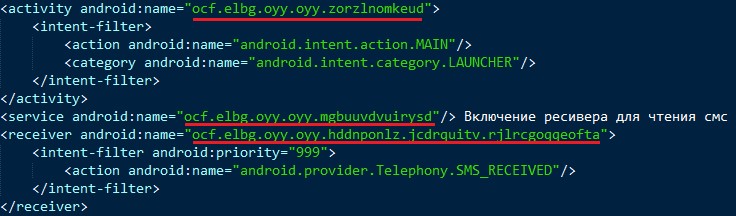
Figure 1 - Fragment of AndroidManifest.xml after EVA obfuscation
The results of scanning applications obfustsii EVA are shown in tables 3 and 4.
Table 3 - scan results for virustotal
| Clean | Eva | |
| Malware.apk | 26 | 3 |
| Dendroid | 35 | 12 |
Table 4 - Mobile Antivirus Scan Results
| Clean | Eva | |
| Malware.apk | 6 | one |
| Dendroid | 12 | eleven |
Thus, EVA showed the best results among obfuscators. For malware.apk, a single detection by mobile antiviruses was achieved, and the only antivirus that detected the virus was AVAST.
But that's not all!
First, simply repacking the application with apktool reduces the number of detections by several times.
Secondly, the combination of different methods and obfuscators greatly improves the results. So, the use of EVA, ADAM and Proguard in any sequence and any number of times allowed reducing the number of virustotal detections to 1. Unfortunately, zero detection was also impossible. But the only antivirus that detected the virus, this time was a certain Ahnlab-V3.
Thirdly, it was noticed that Kaspersky stops responding to the virus after applying any encryption method, although after a while its databases are updated and the detection resumes.
')
Instead of conclusion
Since the application malware.apk in terms of the requested rights on the device was no different from the standard messenger, the popular WhatsApp was taken and obfuscated, which, of course, is not malicious from the beginning.
Messenger obfuscation was carried out in three ways:
1) simple repacking;
2) obfuscation of bytecode using ADAM;
3) Obfuscating bytecode using EVA.
However, when trying to obfuscate the names of classes and packages, the transformation of the application turned out to be too strong and the application crashed.
In addition, due to the fact that WhatsApp checks the checksum of the image, even in the case of successful obfuscation, the application refused to work, offering to reinstall itself.
As a result, obfustsirovanny WhatsApp, in all 3 cases, was identified as malware by two antivirus programs - Avast and Lookout.
Source: https://habr.com/ru/post/305730/
All Articles