Pastilde - open hardware password manager
A lot of notes and discussions are devoted to the difficult issue of safe storage of passwords, an interesting topic and it seems to be relevant for a long time. There are various software solutions for storing passwords, they are often written on Habré (for example, here and here ), but many of them, it seems to us, have the following disadvantages to one degree or another:
- closed code reduces trust and the likelihood of promptly eliminating vulnerabilities
- for auto-fill you need to put additional software
- after entering the master password, the entire database is open and accessible, including for malware, which is especially important on untrusted devices
- the use of mobile applications for storing passwords still implies manual input from the keyboard, for example, when you need to log in to a stationary PC
- autocompletion is impossible in some cases (in bios, console)
We concluded that the most convenient solution would be a simple and inexpensive device that allows hardware to store and enter usernames / passwords on any devices without installing any software.

')
For a start, we, of course, read the entire Internet in order to understand who else had the idea to store and enter passwords in hardware, and how it was implemented. Found options can be divided into the following categories:
- encrypted drives, in fact - just flash drives with a password (for example, such ). You can safely store documents, but we are not talking about automatic password input.
- devices with biometric identification ( example ). Biometric identification looks attractive, but it is less versatile than a character password (for example, if you need to remotely give someone access to the device, fingerprint transmission will become a real problem), and additional sensors increase the cost of the product. In the case of compromising difficult to quickly change prints
- software password managers with a hardware token-key, which gives access to the database ( for example ) have the same drawbacks as key-token-based software managers
- devices for entering 1-4 passwords and their generation ( example , example ). The closest solutions. Among the shortcomings, a limited number of stored passwords should be noted, as well as the management of only buttons on the device, which is not always convenient.
None of the devices found fully corresponded to our idea. We were delighted - and let's think further.
Idea
Not so long ago, we began to use KeePass for corporate tasks of storing passwords instead of paper, browsers and biological memory. Fully satisfied with the convenience and versatility of this product, we decided to adapt it for the tasks of hardware password storage, porting to the microcontroller.
However, a huge number of questions remained. How to choose the desired entry in the database on the device? How to show the user what record is selected? Should I place buttons on the device? Screen? How is it supposed to connect to a computer? To the tablet? To the phone?
The screen was abandoned immediately. If the user already needs to enter a password - most likely, he already has a screen. As for connection methods, we decided not to consider wireless interfaces, due to their potential vulnerability to interception.
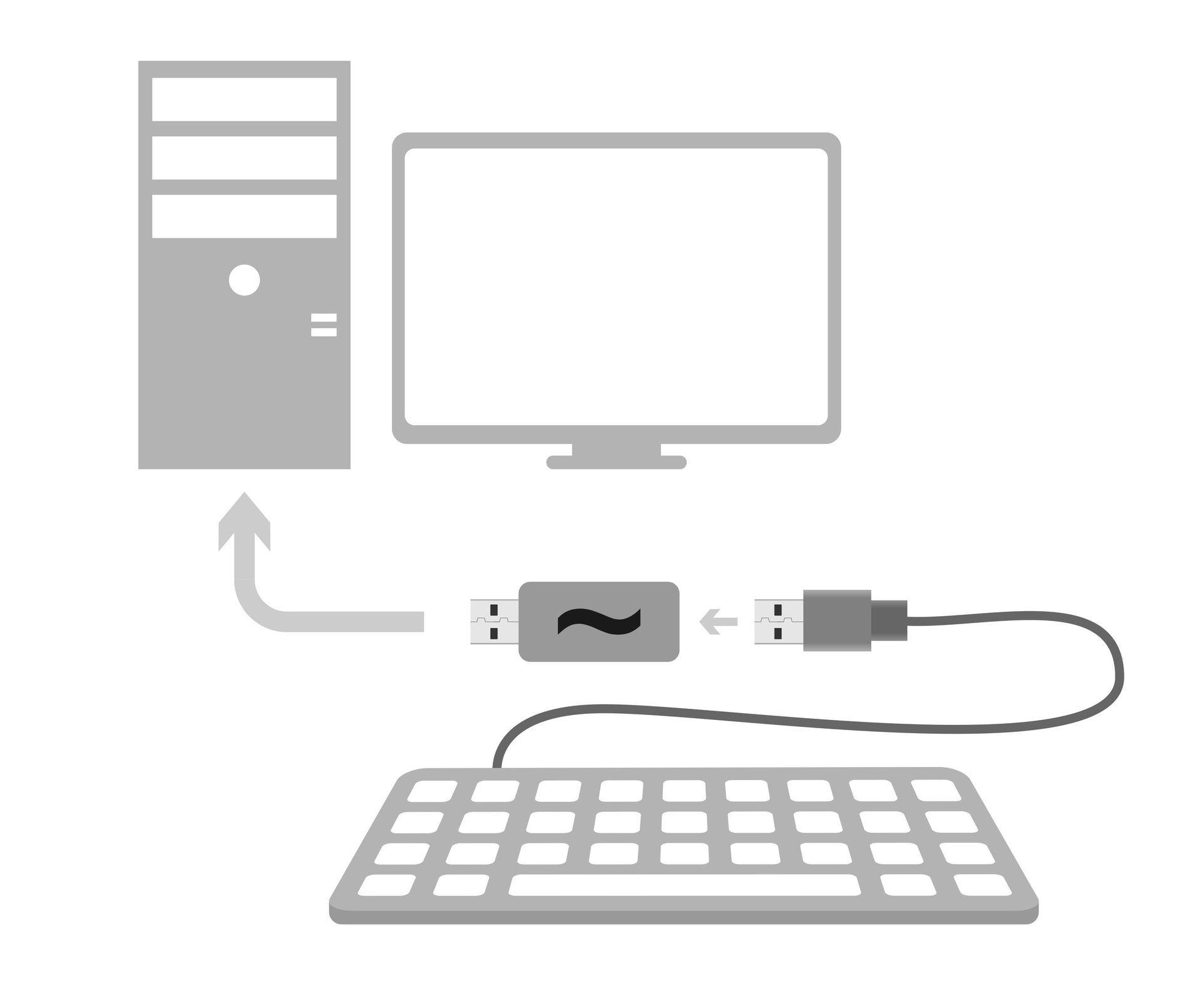
For management, we will use a standard keyboard, and for direct input of saved passwords into forms, we will emulate keyboard commands. “Interception” control will occur when you enter a special key combination. By default, we chose Ctrl + Shift + ~ , because it is convenient for clicking and almost never used. The project was named “Pastilda” (from password, tilda), we associate it with something tasty and sweet, and also help not to forget the main keyboard shortcut for working with the device.
Being in passive mode, Pastilda transmits all messages from the keyboard to the PC without changes, waiting for a special combination to be pressed. After entering the combination, the device enters the active mode. If at this moment the cursor is in the text entry field - it can be the “Login” field, or any other text field - a single-line text menu appears in it.
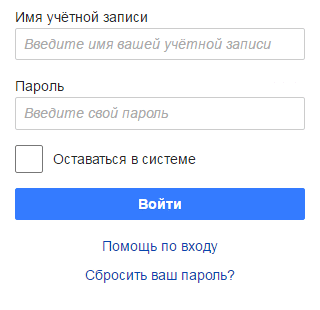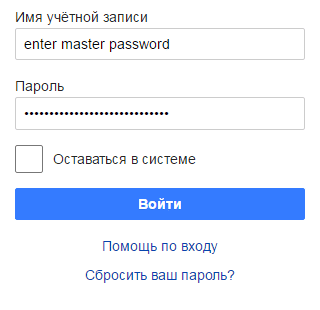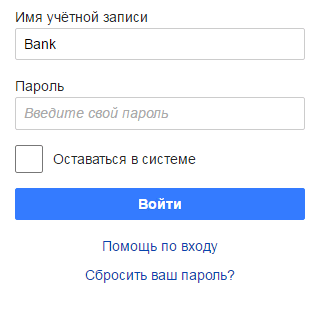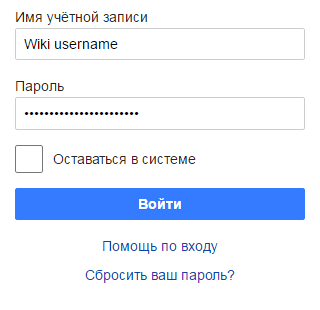
To work with the KeePass database stored in Pastilde’s memory, the user enters a master password, and then selects the name of the account of interest for him with the navigation keys and presses input. Pastilde enters the necessary login and password in the appropriate fields. In this case, the database is decrypted on the device, and the target system does not get access to the master password and to the entire database. The exit from the active mode occurs either automatically, after entering the password, or after pressing the “Shift + Ctrl + ~” combination again. Yes, by the way, you can create your own combinations.
Implementation 0.1
As always, I want to realize a lot of things, but decided to start small. Revision 0.1 is designed to test ideas, ease of use and all kinds of pampering. In the current version, the following minimum functions are scheduled:
- composite USB device (HID + Mass Storage)
- USB host
- work with one base KeePass
- single line menu
- FAT16.
Scheme

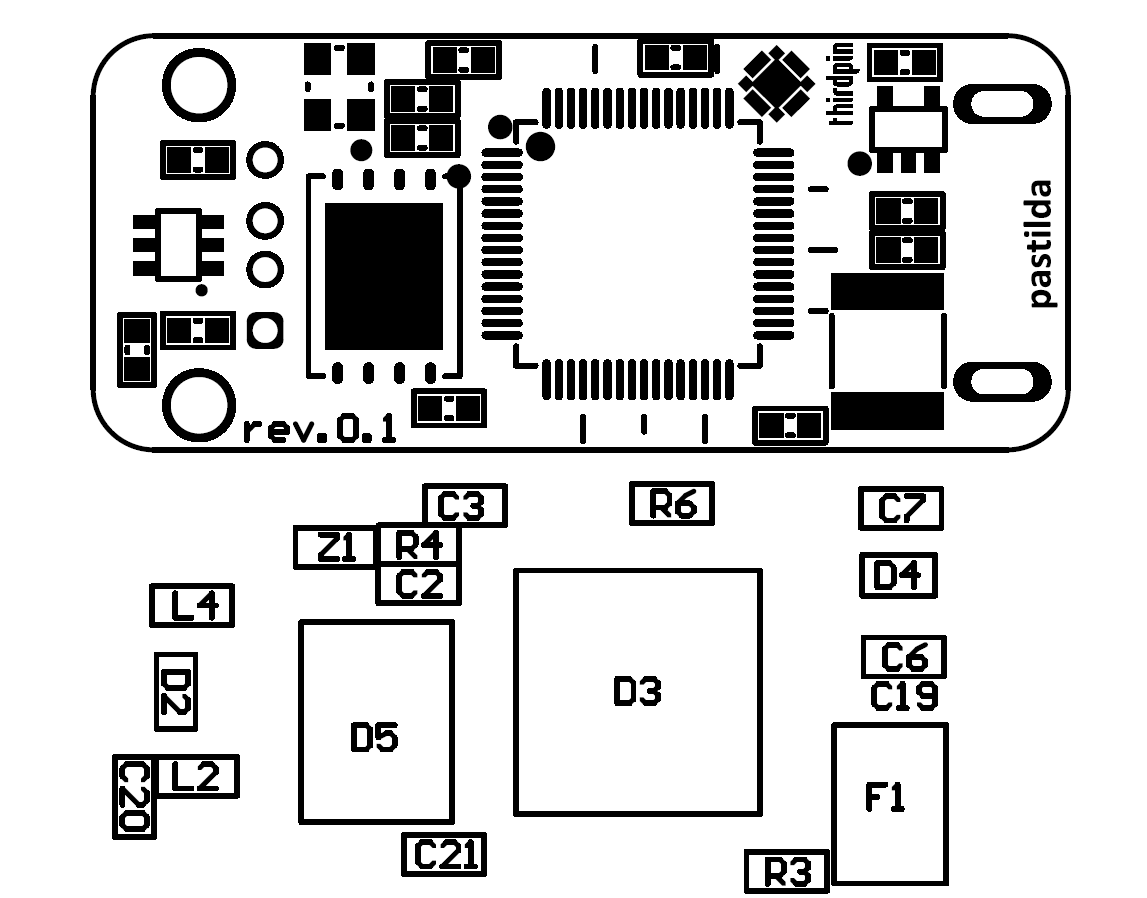
Everything is simple - a Stm32f405 controller, two connectors and a flash drive on the SPI. Just a bit of protection, a SWD connector and, of course, an RGB LED. The choice of components did not cause difficulties - we just love STM
Pay

All components are in conventional enclosures so that the board is cheap and fast to manufacture. Size 40x17 mm, 4 layers. The current version of the board looks like this:

Soft
Currently implemented:
- USB host, in order to recognize the keyboard connected to the device and push messages from it further to the PC
- Composite USB device (msd + hid): in Pastilda mode, the device should be able to be a keyboard, in addition, always be available as an external drive, for easily adding and deleting passwords (By the way, @anaLazareva solved the problem with usb_msc libopencm3.
Waiting for his fate:
- FAT for reading data stored in flash memory, so that we can go through directories and take the desired password
- KeePass decoding, work with records
- menu.
Programmers will write about their harsh everyday life in separate articles.
What's next?
Further more. I want to implement work with any devices that understand the external keyboard. We have already tested the work of our prototype with an Android-smartphone via USB OTG, everything works fine. For the convenience of navigating the menu when using Pastilde with mobile devices, we will make a separate USB-module with a wheel-button.

Another idea is a small flexible-rigid printed circuit board, which is loaded directly into the USB connector, being between the host and device contacts. A hard piece of the board with components is glued onto the device case. Thus, the device will be quite difficult to detect. However, why would we need this? Just an idea.

Pastelda's built-in memory can be used to store data (if speed is not particularly important), and there are options: just a USB drive, which is always visible when the device is connected, or an encrypted drive. KeePass databases, key files, etc. supposed to be stored in this space.
Open all
The code is laid out on github , together with iron. GNU GPL license. Naturally, you can cut something of your own on the basis of this project, such ideas came to our mind:
- kbd + mouse emulation for game cheating
- Stream hardware encryption USB flash.
The main goal of this article is to hear your opinion, feel free to comment!
UPD Jun 27, 2017:
- The Pastilda project repository moved here . The release 1.0 was recently published.
- Latest news on the project can be viewed here .
- And we finally launched the project site !
Source: https://habr.com/ru/post/305594/
All Articles