Everything under control: we protect corporate conversations
Cases for the already familiar GSM / SIP convergence have been repeatedly described in the network and in Habré in particular. In this article we want to tell a little about something else.
We in Tottoli GSM had the opportunity to participate in the project, the essence of which was to deploy a local GSM network in the organization’s territory with access to a public telephone network and integration with the existing PBX.

')
The whole architecture was packed in one OsmoBTS - UmDESK piece of hardware ( MSC / HLR / VLR / AuC / SMSC ). This project is open and very flexible, it allows you to develop your applications and create your services. Well and that is important - the price. The whole software and hardware stack is open source, many articles have been written about it, and there’s no point in retelling the essence.
Our configuration has the following:
The question of the legitimacy of the use of frequencies is decided by the customer, and responsibility lies on his side. However, in order not to attract attention once again, the radio frequency spectrum was scanned to identify free frequencies and determine the ARFCN channels used.
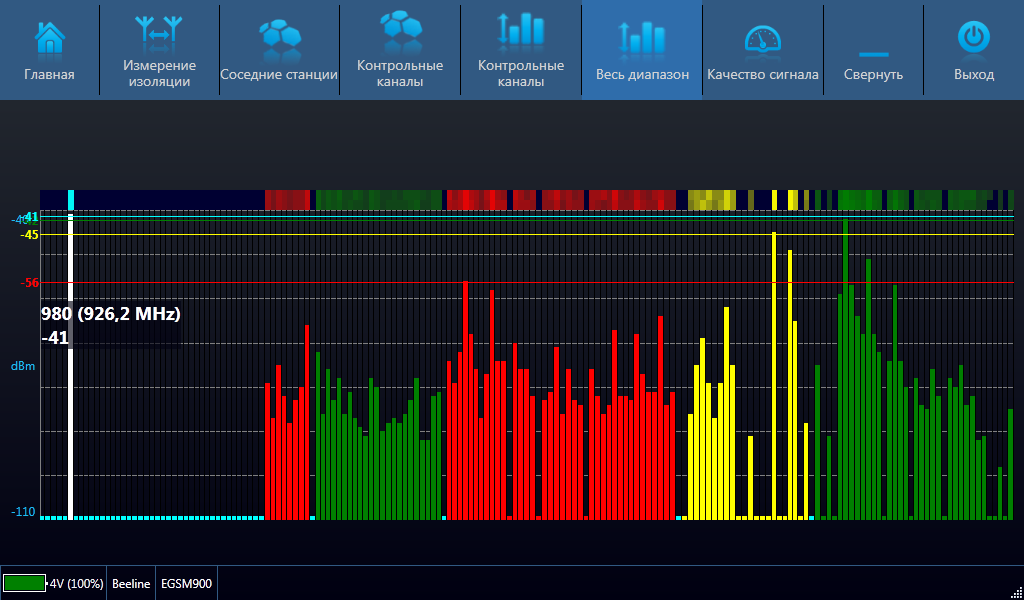
Based on the scan results, two free channels were selected.
We configured OsmoBTS so that the attenuation behind the walls of the organization was maximum, while the signal level in the controlled area was sufficient.
All employees were given SIM-cards with pre-installed profiles ( IMSI / KI / MSISDN ) and specially designed applets. Authentication triplets were whitelisted in HLR / UmDESK. The HLR configuration was made in such a way that any SIM cards could be registered in the local network, but only SIM cards from the HLR white list could make calls. This made it possible to track "guest" telephones at the level of their network, in fact, IMSI-catcher. On the SIM-card, an image of a local network was created, where the only allowed network was a local network. This was achieved by recording the network parameters in the PLMN area , and of course using a special applet. Thus, the employee, getting into the area of the local network, was transferred to it without the possibility of switching to another network (for example, a similar virtual BTS "active interception complex").
For interaction OsmoBTS with iron library libusrp is used. Further, using the oSIP and oRTP libraries, OsmoBTS creates SIP calls, which, in turn, are sent to Asterisk PBX. On the client side is billing and additional services.
1. Employees must be mobile and have access to special services at any time.
2. Employees can use their mobile devices they are used to.
3. All services must be accessible regardless of the operating system of the mobile device.
4. All used traffic from mobile devices must be available to the company's Security Service for analysis.
5. All communications within the network should not fall on the equipment of the host operators.
6. It is necessary to minimize the threat of interception of traffic through the air.
7. The guest subscriber cannot use the communication services of the host operator within the company.
8. The guest subscriber has a controlled ability to use communication services only within the local network.
9. Combine offices located in different countries into a single network.
1. The employee must be able to use the service SIM card outside the local network.
2. An employee must have access to all services outside the local network.
3. In public networks, an employee must change authenticators (IMEI / IMSI).
4. The ability to share sensitive information using instant messages in an encrypted form.
5. The employee’s mobile device must have mechanisms to detect false BTS outside the local network.
6. The employee’s mobile device must detect attacks of active interception complexes.
7. All traffic (GSM / SMS / DATA / USSD) should be available to the company's Security Service for analysis outside the local network.
8. All Internet traffic, both inside the local network and outside the local network, must pass through the customer's APN and be analyzed using DPI.
If this project is of interest, we will describe each item in more detail with pictures and explanations in the following articles of the Tottoli GSM blog.
Everything is under control: we protect corporate conversations. Part 2: Secure Telephone
Everything is under control: we protect corporate conversations. Part 3: Secure SIM Card
We in Tottoli GSM had the opportunity to participate in the project, the essence of which was to deploy a local GSM network in the organization’s territory with access to a public telephone network and integration with the existing PBX.

')
Project Objective:
Maximum reduction of information leakage risks in the GSM network.
The whole architecture was packed in one OsmoBTS - UmDESK piece of hardware ( MSC / HLR / VLR / AuC / SMSC ). This project is open and very flexible, it allows you to develop your applications and create your services. Well and that is important - the price. The whole software and hardware stack is open source, many articles have been written about it, and there’s no point in retelling the essence.
Our configuration has the following:
Radio interface
The question of the legitimacy of the use of frequencies is decided by the customer, and responsibility lies on his side. However, in order not to attract attention once again, the radio frequency spectrum was scanned to identify free frequencies and determine the ARFCN channels used.

Based on the scan results, two free channels were selected.
We configured OsmoBTS so that the attenuation behind the walls of the organization was maximum, while the signal level in the controlled area was sufficient.
Subscriber part
All employees were given SIM-cards with pre-installed profiles ( IMSI / KI / MSISDN ) and specially designed applets. Authentication triplets were whitelisted in HLR / UmDESK. The HLR configuration was made in such a way that any SIM cards could be registered in the local network, but only SIM cards from the HLR white list could make calls. This made it possible to track "guest" telephones at the level of their network, in fact, IMSI-catcher. On the SIM-card, an image of a local network was created, where the only allowed network was a local network. This was achieved by recording the network parameters in the PLMN area , and of course using a special applet. Thus, the employee, getting into the area of the local network, was transferred to it without the possibility of switching to another network (for example, a similar virtual BTS "active interception complex").
SIP PBX
For interaction OsmoBTS with iron library libusrp is used. Further, using the oSIP and oRTP libraries, OsmoBTS creates SIP calls, which, in turn, are sent to Asterisk PBX. On the client side is billing and additional services.

Here are some criteria that have been set by the customer:
1. Employees must be mobile and have access to special services at any time.
2. Employees can use their mobile devices they are used to.
3. All services must be accessible regardless of the operating system of the mobile device.
4. All used traffic from mobile devices must be available to the company's Security Service for analysis.
5. All communications within the network should not fall on the equipment of the host operators.
6. It is necessary to minimize the threat of interception of traffic through the air.
7. The guest subscriber cannot use the communication services of the host operator within the company.
8. The guest subscriber has a controlled ability to use communication services only within the local network.
9. Combine offices located in different countries into a single network.
As often happens, the appetite comes with eating. The customer during the operation offered to implement the following tasks:
1. The employee must be able to use the service SIM card outside the local network.
2. An employee must have access to all services outside the local network.
3. In public networks, an employee must change authenticators (IMEI / IMSI).
4. The ability to share sensitive information using instant messages in an encrypted form.
5. The employee’s mobile device must have mechanisms to detect false BTS outside the local network.
6. The employee’s mobile device must detect attacks of active interception complexes.
7. All traffic (GSM / SMS / DATA / USSD) should be available to the company's Security Service for analysis outside the local network.
8. All Internet traffic, both inside the local network and outside the local network, must pass through the customer's APN and be analyzed using DPI.
If this project is of interest, we will describe each item in more detail with pictures and explanations in the following articles of the Tottoli GSM blog.
Read more:
Everything is under control: we protect corporate conversations. Part 2: Secure Telephone
Everything is under control: we protect corporate conversations. Part 3: Secure SIM Card
Source: https://habr.com/ru/post/305586/
All Articles