5 obvious signs of information leakage in your organization
Nowadays, the business of most organizations is accompanied by the support of complex IT systems and centralized repositories, which in one way or another have already implemented information protection. Working with files in the repository is often inconvenient, so users often copy files from IT systems and repositories to their workstation or external media. In this case, the copied data is stored in unprotected unencrypted form. These actions are often justified by the speed of access / processing, convenience, the need to work outside the office, business trips, etc., accompanied by a phrase like “It's easier and more convenient.” Some recent studies have found robust performance:
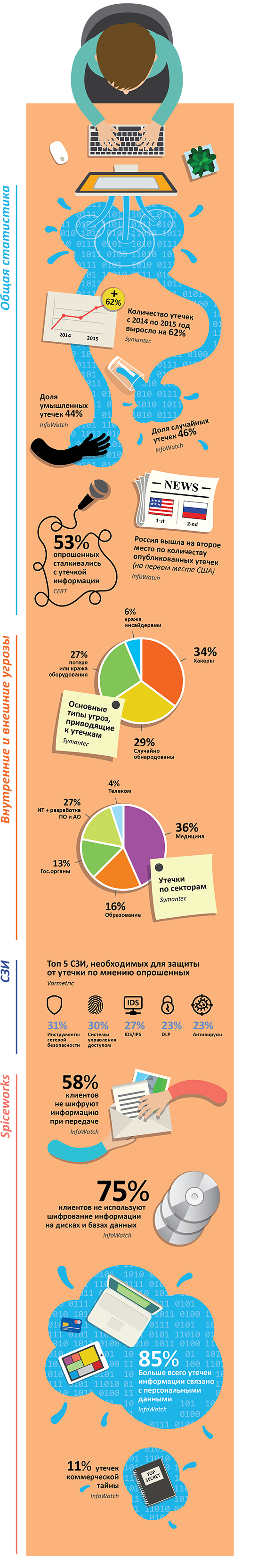
Additional statistical information is presented in the infographic box:
The commonly used security measures of centralized systems create a false sense of security, because at first glance only trusted people can get access to information carriers on workstations and laptops, but in reality this is not the case.
Access to information on disks of workstations, servers or laptops can be carried out in the following situations:
It is fairly easy to access unprotected data in such situations, but it is very difficult to detect data leakage due to them. For example, when you send a "tightly" hung computer for repair to a service center, there is a significant risk of unauthorized access to confidential information. Such information leakage may never show up.
Another common misconception is that laptops store information, the loss of which cannot harm the company, because copies of the files are in the centralized file storage. In order to refute this judgment, it is enough to imagine the possible consequences of information leakage from the lost laptop of the company's general director:
')
According to the specialists of Aladdin RD, there are very specific signs and situations that clearly indicate the presence of potential problems with the leakage of confidential information in the organization.
If a company detects one or more of the following signs, the risks of leakage of sensitive or confidential information increase substantially. This circumstance should serve as a certain “ring” for the information security service. Of course, the traditional method of solving such potential problems is monitoring information leaks through the DLP (Data Leak Prevention) system. However, such systems require impressive financial costs for their implementation and further maintenance. An alternative approach to solving such problems is to use information encryption on the disks of servers and workstations.
Modern encryption systems are cost-effective and more reliable in the fight against leaks of corporate information. However, to talk about the self-sufficiency of any method is wrong. It is most reliable to use both methods (DLP and encryption) in combination with each other.
The most important and most critical of them are listed below.
Secret Disk Enterprise's corporate system of transparent information encryption allows you to not involve the user in the protection process, thereby reducing the risk of human error and negligence. At the same time, the system guarantees reliable protection of confidential information and providing access to it only to authorized users. The functionality of the encryption system allows to solve the most pressing organizational security problems, including:
Data encryption is the only sensible way to prevent data leaks from lost laptops, mobile computers and external storage media. However, encryption requires not only “mobile” information, stationary workstations and file servers of the company also fall under the risk of leakage of important or business-critical information. Possessing the flexibility of encryption functionality and allowing the security service to provide cryptographic protection for a whole fleet of computer equipment in a modern office, the Secret Disk Enterprise transparent encryption system is an ideal choice combining reliability, simplicity and cost-effectiveness.
- up to 60% of highly critical corporate information is processed and stored locally on the disks of workstations, laptops, in the user's local mailboxes;
- The share of laptops (45% of the total number of computers in the organization) that process and store critical information continues to grow - mobility is becoming the standard for information processing.
Additional statistical information is presented in the infographic box:

The commonly used security measures of centralized systems create a false sense of security, because at first glance only trusted people can get access to information carriers on workstations and laptops, but in reality this is not the case.
Access to information on disks of workstations, servers or laptops can be carried out in the following situations:
- work of the administrator to configure or maintain computer equipment;
- loss of a laptop on which critical information is stored and processed;
- transportation of external media with unprotected critical information;
- repair of computer equipment with removal from the office to the service center;
- the seizure of computer equipment with or without court decisions;
- moving and transportation of computer equipment to another room or new office;
- recycling obsolete, out of order computer equipment.
It is fairly easy to access unprotected data in such situations, but it is very difficult to detect data leakage due to them. For example, when you send a "tightly" hung computer for repair to a service center, there is a significant risk of unauthorized access to confidential information. Such information leakage may never show up.
Another common misconception is that laptops store information, the loss of which cannot harm the company, because copies of the files are in the centralized file storage. In order to refute this judgment, it is enough to imagine the possible consequences of information leakage from the lost laptop of the company's general director:
')
- information on the financial situation of the organization;
- personal data of employees;
- correspondence with customers and other critical data systems CRM-and ERP-systems;
- strategic plans of the organization, analysis of the market and competitive environment, etc.
According to the specialists of Aladdin RD, there are very specific signs and situations that clearly indicate the presence of potential problems with the leakage of confidential information in the organization.
If a company detects one or more of the following signs, the risks of leakage of sensitive or confidential information increase substantially. This circumstance should serve as a certain “ring” for the information security service. Of course, the traditional method of solving such potential problems is monitoring information leaks through the DLP (Data Leak Prevention) system. However, such systems require impressive financial costs for their implementation and further maintenance. An alternative approach to solving such problems is to use information encryption on the disks of servers and workstations.
Modern encryption systems are cost-effective and more reliable in the fight against leaks of corporate information. However, to talk about the self-sufficiency of any method is wrong. It is most reliable to use both methods (DLP and encryption) in combination with each other.
The most important and most critical of them are listed below.
- “Turnover” - personnel rotation, organizational changes or mass layoffs (reductions) of employees. The crisis and difficult economic conditions force the management of most companies to take decisive measures against the staff. In such conditions, the probability of potential leakage increases significantly. Potential danger comes not only from the "affected" employees. Typically, massive layoffs or changes in the organizational structure of the organization reduce the overall level of staff motivation. “Offended” employee, endowed with access to confidential, critical or proprietary information is the weak link in the overall security system. Statistically the most frequent violations of information security of such employees are theft and transfer of information to third parties.
The functions of encrypting information on the disk and controlling copying of protected information to a USB device implemented in the Secret Disk Enterprise system will significantly reduce the risks of leakage during intensive staff rotation in the organization. - Business trips - the working schedule of the organization’s employees involves a large number of business meetings / trips / business trips. A modern “mobile” employee, traveling outside the office on a local or long-distance business trip, is equipped with a variety of electronic means of communication. However, the most popular tool in this situation is a laptop. The vast majority of notebooks, taken out on a business trip, contain service information, trade secrets, confidential information. According to leakage statistics, a laptop, lost or stolen in a public place, is the number one cause in a leak of valuable information.
The encryption functions of the system partition of the hard disk and the encryption of additional partitions implemented in the Secret Disk Enterprise system will make it possible to exclude the possibility of accessing data on a lost or stolen laptop. - Work with contractors or branches - regular external exchange of important and confidential information. Some production processes in the organization are based on the exchange of information with external counterparties. Often this exchange is subject to proprietary and confidential information. Information is transmitted on a variety of flash media, etc. During transport, such information is often lost or even intentionally altered. Access to such information is not controlled by the security service. This type of exchange significantly increases the risk of leakage of important information.
The functions of using cryptocontainers and encrypting virtual external USB disks implemented in the Secret Disk Enterprise system will reliably protect data transmitted to third parties. - Complicated IT infrastructure and several IT administrators. The complexity of the infrastructure and information systems is a very important complicating factor for the information security service. Such infrastructures are often served by several administrators who have equal, maximum access rights to the servers and workstations of the organization. Accordingly, the possibility of uncontrolled access to confidential information indicates the presence of potential leaks of critical and important information. This circumstance is complicated by the traditionally uneasy relationship of management with IT administrators. Obviously, a demotivated or “offended” employee with privileged user rights is a time bomb. The scale of the consequences of leaking critical information in this case can only be guessed.
The functions of using folder encryption in the Secret Disk Enterprise system will “isolate” the system administrator without disrupting the business process of administering the protected system. - Mobile office - a large fleet of laptops used in the company. 45% of customers share of laptops used in modern companies, up to 45% of the total number of computer equipment. Laptops are comfortable and efficient. However, a modern laptop is a closed hardware environment guaranteed by the manufacturer. Employees of IT services in companies do not have the ability to repair and even diagnose problems of the notebook inoperability. In case of breakdown, malfunctions, etc. laptops are transferred to the service center (warranty). Together with the laptop, all confidential information that is on board is forced to be transferred to the service center. Thus, neither the security service, nor the IT service of the company can control the access of employees of the service centers to the information on the disk of the transferred laptop. Obviously, this circumstance is a highly critical problem of leakage of important and confidential information.
The information encrypted by the Secret Disk Enterprise system will not be accessible to service center employees, even if the laptop hangs tight when transferring, the data on the disk will remain encrypted.
Secret Disk Enterprise's corporate system of transparent information encryption allows you to not involve the user in the protection process, thereby reducing the risk of human error and negligence. At the same time, the system guarantees reliable protection of confidential information and providing access to it only to authorized users. The functionality of the encryption system allows to solve the most pressing organizational security problems, including:
- guaranteed prevention of information leaks from laptops, workstations and servers of the company;
- restriction of privileged users access to confidential information (protection from the administrator);
- differentiation of access rights to protected information;
- information security in exchange with third parties or branches of the organization;
- protection of personal data and trade secrets;
- prompt termination of access of a certain employee to information on his workstation;
- protection of information from unlawful or undesirable seizure by third-party organizations and services.
Data encryption is the only sensible way to prevent data leaks from lost laptops, mobile computers and external storage media. However, encryption requires not only “mobile” information, stationary workstations and file servers of the company also fall under the risk of leakage of important or business-critical information. Possessing the flexibility of encryption functionality and allowing the security service to provide cryptographic protection for a whole fleet of computer equipment in a modern office, the Secret Disk Enterprise transparent encryption system is an ideal choice combining reliability, simplicity and cost-effectiveness.
Source: https://habr.com/ru/post/305494/
All Articles