We attack SS7: security analysis of cellular operators in 2015
Interception of mobile phone conversations is considered to be a difficult task. However, not only the special services own this art: a middle level hacker can attack subscribers if he is familiar with the structure of signaling networks. The good old SS7 vulnerabilities allow you to eavesdrop on phone conversations, locate callers, intercept SMS, and disconnect your phone from the network.
In 2015, Positive Technologies experts carried out 16 projects to analyze the security of SS7 networks of leading mobile operators in the EMEA and APAC regions. The results of the eight most informative projects fell into our statistics. In this article, we will look at the level of security of subscribers of cellular networks, as well as all industrial and IoT devices, from ATMs to GSM pressure monitoring systems on a gas pipeline, which are also subscribers of cellular networks. The report describes the main problems detected and their solutions.
')
Preamble: Hello from the 70s
Developed forty years ago, the SS7 system (SS-7) has certain disadvantages in terms of security (for example, there is no encryption and authentication of service messages). For a long time, this posed no danger to either the subscribers or the operator: the SS7 network was a closed system in which only fixed-line operators were connected. However, as time goes on, the network has evolved to support the needs of mobile communications and the provision of additional services. In the early 2000s, the SIGTRAN specification was proposed, allowing SS7 service information to be transmitted over IP networks. Signal network has ceased to be isolated.
Of course, it’s impossible to get directly into the signaling network; you will need an SS7 gateway. But to ensure access to it is not so difficult. You can get a carrier license in a country where it is overlooked, or you can get access on the black market from the current operator. There are ways to get into the network through hacked camera equipment, GGSN or femtocell. If there is a technical company operator among the members of the hacker group, he can perform a series of attacks using a set of legitimate commands or connect his equipment to SS7.
Attacks via SS7 can be carried out from anywhere on the planet, which makes this method one of the most promising for an intruder. The attacker does not need to physically be close to the subscriber, as is the case with a fake base station, so it is almost impossible to calculate it. High qualification is also not required: many ready-made applications for working with SS7 are available on the network. At the same time, operators cannot block commands from individual nodes, since this has a negative impact on the entire service and violates the principles of roaming.
For the first time, SS7 vulnerabilities were publicly demonstrated in 2008: a German researcher Tobias Engel showed the technique of spying on subscribers of mobile networks. In 2014, experts from Positive Technologies made a presentation on “How to eavesdrop on a person on the other side of the globe” and presented a detailed report “Vulnerabilities of mobile communication networks based on SS7”. In 2015, SR Labs on the Australian program “60 minutes”, being in Germany, intercepted the SMS correspondence of the Australian senator Nick Xenophon and the British journalist, and then watched the movements of the senator on a business trip to Tokyo.
Overall results
For reasons of confidentiality, we do not disclose the names of the companies that participated in our research. We only note that half of the SS7 networks studied belong to the largest mobile operators with more than 40 million subscribers.

Volume of subscriber base of operators
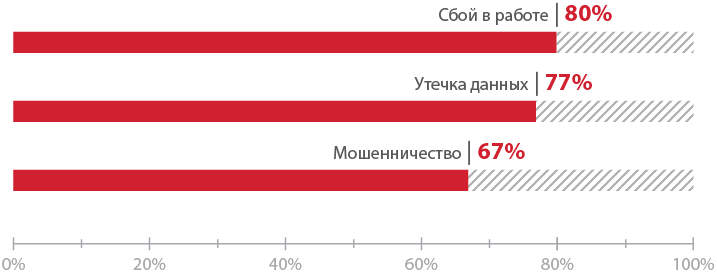
The final security level of the SS7 networks of all the studied mobile operators was extremely low. In 2015, attacks related to data leakage of subscribers (77% of successful attempts), network disruptions (80%) and fraudulent activities (67%) could have been implemented against telecom operators and their SS7 networks.
Incoming SMS messages could be intercepted in the networks of all study participants. Nine out of ten attacks (89%) reached the goal, and this is a very bad result. Judge for yourself: SMS messages are often used in two-factor authentication systems and for recovering passwords from various Internet services. Interception of messages was performed by the UpdateLocation method. The attacker registers the victim's subscriber in the fake network, after which all incoming SMS messages arrive at the address specified by him.

The proportion of successful attacks in order to obtain sensitive information
Unauthorized balance inquiry was also possible almost everywhere (92% of attacks). For this attack, the ProcessUnstructuredSS-Request message is used, in the body of which the corresponding USSD command is transmitted.
Voice calls were protected a little better: only half of the attacks with the aim of listening to incoming and outgoing calls were crowned with success. But this is a huge risk for subscribers. To intercept incoming calls, a roaming number substitution technique was used. Listening of outgoing calls was carried out by the InsertSubscriberData method. Then, in either case, traffic was redirected to another switch.

Subscriber location methods (share of successful attacks)
Determine the physical location of the subscriber happened in all networks except one. The main methods are SendRoutingInfo and ProvideSubscriberInfo, the latter giving the result with every second attack (53%).
The most valuable subscriber information is IMSI. This identifier is needed for most attacks. The easiest way was to get it using the SendRoutingInfo method.

Methods of stealing subscriber information (share of successful attacks)
Another method of determining IMSI - SendRoutingInfoForSM - was effective in 70% of cases. This message is used in the incoming SMS message to request route information and localize the recipient subscriber. It was possible to find out the subscriber ID using the SendIMSI command, but with a lower probability (25%).
Fraud
In each of the systems were identified deficiencies that allow to implement any fraudulent actions by an external offender. Examples of such actions include call forwarding, transfer of funds from the subscriber’s account, changing the subscriber’s profile.

Fraud: the proportion of successful attacks
Most of the attacks to redirect incoming calls were successful (94%). This confirms the existence of significant problems in SS7 networks related to the architecture of protocols and systems.
The outgoing call was redirected only in 45% of cases. For redirection, the InsertSubscriberData method was used.
Attacks to redirect incoming calls were carried out using two techniques - roaming number substitution and call forwarding manipulation. The roaming number is changed at the moment of an incoming call to the attacked subscriber, who must be registered in the fake network. In response to the roaming number request, the attacker sends the number to redirect the call. The fee for the established connection will fall on the operator.
Manipulation with redirection - unauthorized installation of unconditional redirection. All incoming calls for the subscriber will be redirected to the specified number. You have to pay for calls to the subscriber.

Incoming call redirection methods (shares of successful attacks)
Subscriber profile change was possible in every second attack carried out by the InsertSubscriberData method (54%). The attacker has the ability to change the subscriber profile in such a way that outgoing calls will be bypassed by the charging system. This attack can be used in fraud schemes for generating traffic to paid numbers and expensive destinations at the expense of the operator.
DoS attack on the subscriber
To make the subscriber equipment (phone, modem, GSM alarm or sensor) inaccessible for incoming transactions, an attacker can carry out targeted attacks on subscribers of the mobile network. Most of the SS7 networks we studied are vulnerable to DoS attacks (80% were successful).
In all cases, the UpdateLocation method was used; to attack you need to know the subscriber's IMSI. An UpdateLocation message is sent to the operator’s network informing the HLR that the subscriber has registered (on a fake network). After that, incoming calls to the subscriber are routed to the address specified during the attack.
Causes of problems
Most attacks on SS7 networks were possible due to the lack of verification of the real location of the subscriber. On the second and third places in the list of reasons - the inability to verify the identity of the network subscriber and the lack of filtering unused signal messages. Fourth position - SMS Home Routing configuration errors.

Average number of successful attacks on a single SS7 network (depending on the deficiency)
What can be done
Most of the flaws that determine the location of the subscriber and steal data can be eliminated by changing the configuration of network equipment. At a minimum, it is necessary to prohibit the processing of AnyTimeInterrogation and SendIMSI messages on the HLR.
Architectural problems of protocols and systems are solved by blocking unwanted messages. First of all, you should pay attention to SendRoutingInfoForSM, SendIMSI, SendRoutungInfoForLCS, SendRoutingInfo. Filtering will help avoid risks associated with denial of service, intercepting SMS messages, forwarding calls, listening to calls, changing the subscriber profile.
However, not all specified SS7 network messages can be dangerous. It is necessary to implement filtering in such a way that only unwanted messages used in attacks are cut off. To this end, it is recommended to introduce additional means of protection, for example, intrusion detection systems. Such systems do not affect network traffic, but they allow identifying the actions of the offender and determining the necessary settings for filtering messages.
The full version of the study: www.ptsecurity.ru/research/analytics .
Authors : Dmitry Kurbatov, Sergey Puzankov, Telecommunication Systems Security Department, Positive Technologies
Source: https://habr.com/ru/post/305472/
All Articles